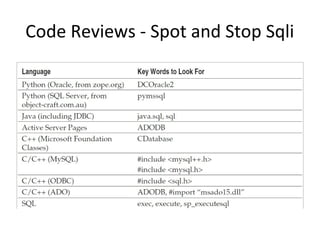
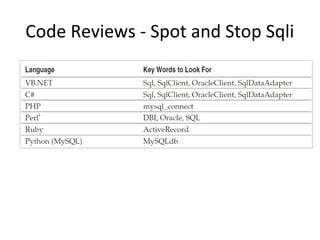
The document presents a comprehensive overview of SQL injection (SQLi) vulnerabilities, exploitation techniques, and prevention strategies. It discusses the implications of inadequate security measures, the persistence of legacy code issues, and suggests various tools and methods to counter SQLi attacks. Furthermore, it emphasizes the importance of proper input validation, parameterized queries, and ongoing audits to secure databases against SQLi.




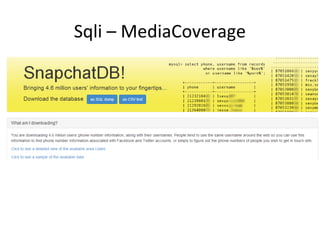






















![Blacklist Filter Evasion
';exec xP_cMdsheLL 'dir';-';ex/**/ec xp_cmds/**/hell 'dir';-- [old versions]
';exec/**/xp_cmdshell/**/'dir';-';Declare @cmd as varchar(3000);Set @cmd =
'x'+'p'+'_'+'c'+'m'+'d'+'s'+'h'+'e'+'l'+'l'+'/**/'+''''+'d'+'i'+'r'+'''';e
xec(@cmd);--](https://image.slidesharecdn.com/sqli-140129101620-phpapp02/85/Devouring-Security-Sqli-Exploitation-and-Prevention-34-320.jpg)






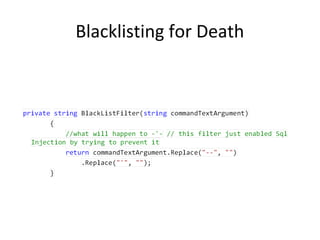





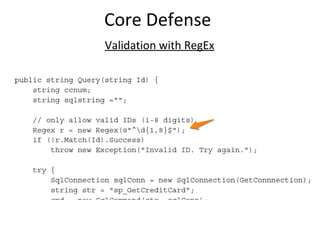
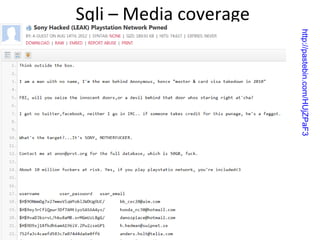
![Core Defense
CREATE PROCEDURE dbo.doQuery (@id NCHAR(4))
AS
DECLARE @query NCHAR(64)
IF RTRIM(@id) LIKE '[0-9][0-9][0-9][0-9]'
BEGIN
SELECT @query = 'select ccnum from cust where id = ''' + @id + ''''
EXEC @query
END
RETURN
-- Or, better yet, force an interger parameter
CREATE PROCEDURE dbo.doQuery(@id smallint)](https://image.slidesharecdn.com/sqli-140129101620-phpapp02/85/Devouring-Security-Sqli-Exploitation-and-Prevention-48-320.jpg)
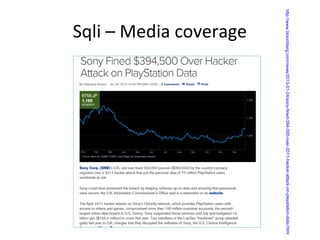
![Core Defense
Parametrization a.k.a prepared statements
[refer to your framework for support]](https://image.slidesharecdn.com/sqli-140129101620-phpapp02/85/Devouring-Security-Sqli-Exploitation-and-Prevention-49-320.jpg)