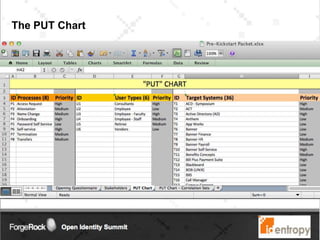
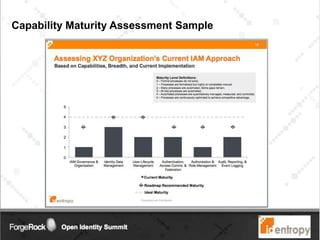
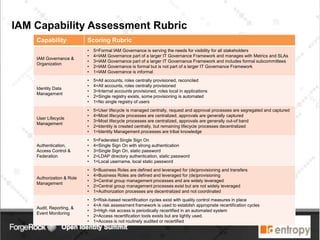
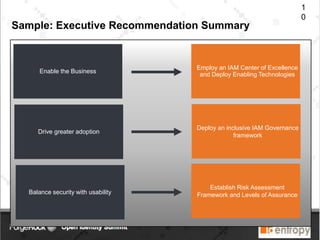
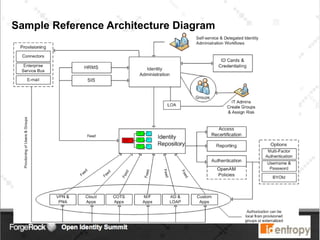
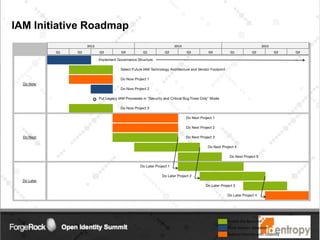
Identropy's professional services practice focuses on Identity and Access Management (IAM) through a structured plan-build-run approach, providing a DIY kit for IAM roadmaps. The IAM kickstart program includes a seven-step methodology designed to assess current capabilities, create strategies, and establish implementation roadmaps for organizations. Key deliverables include an IAM capability benchmark, architecture recommendations, and a detailed initiative roadmap to enhance IAM governance and effectiveness.