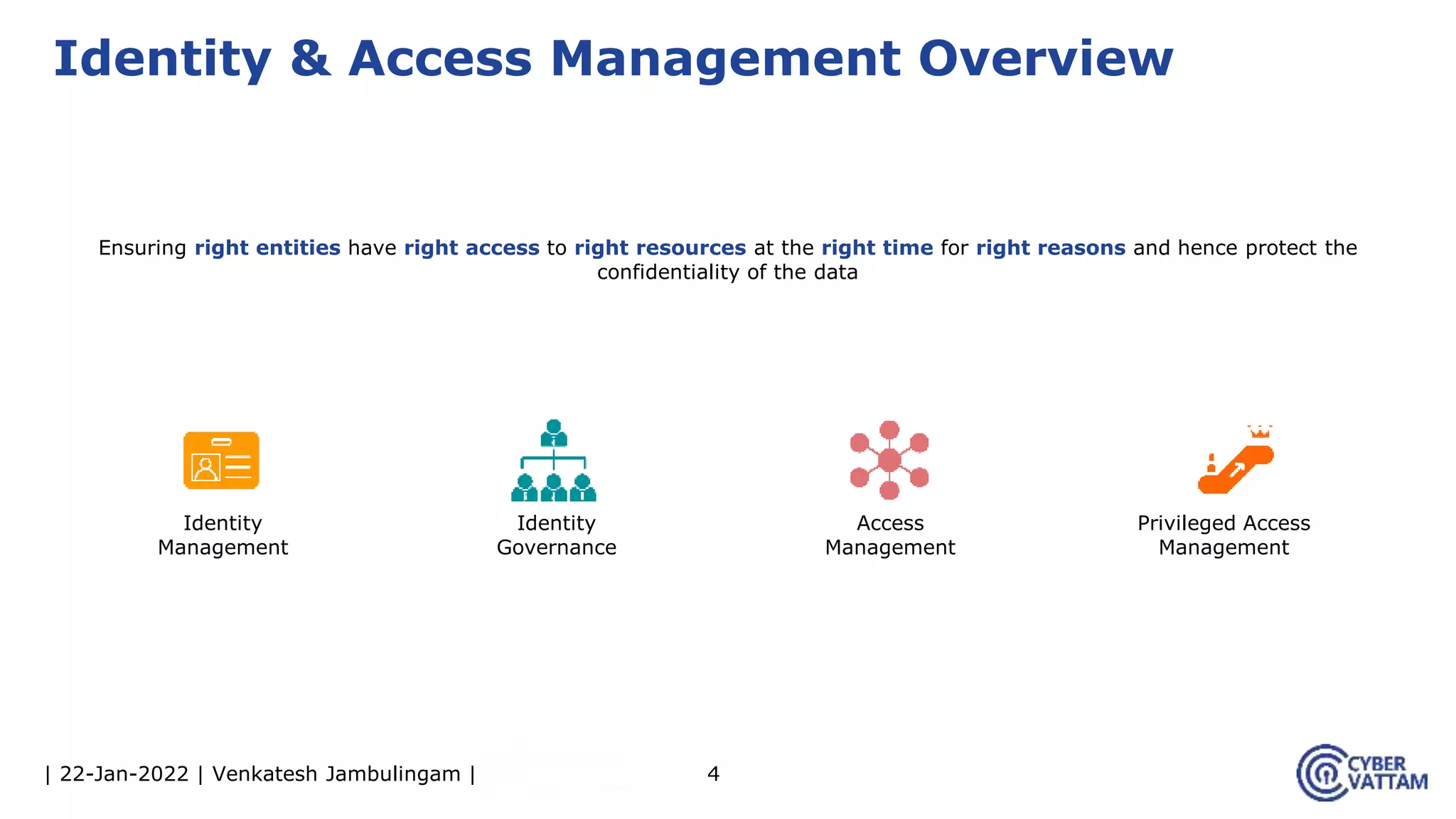
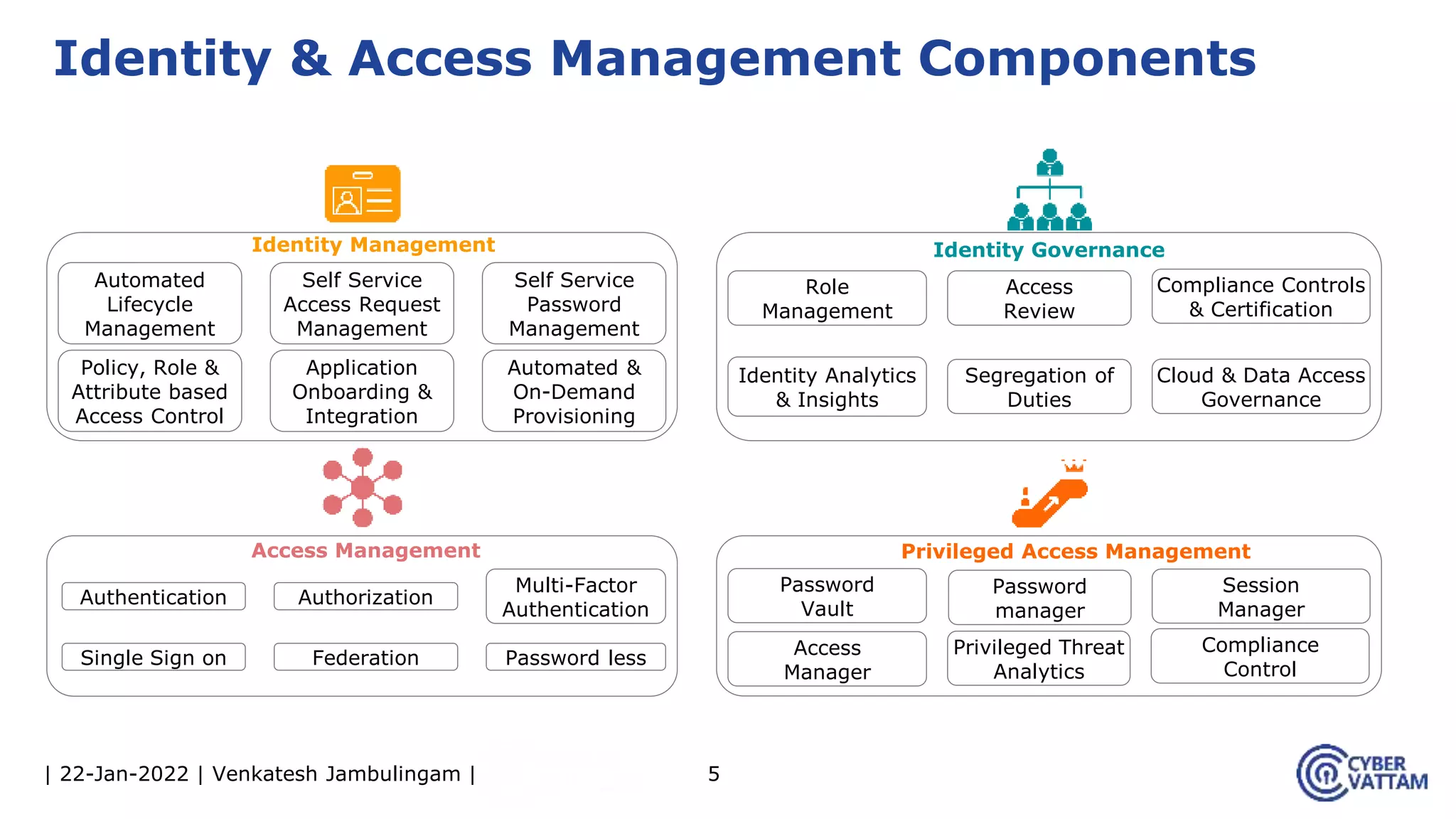
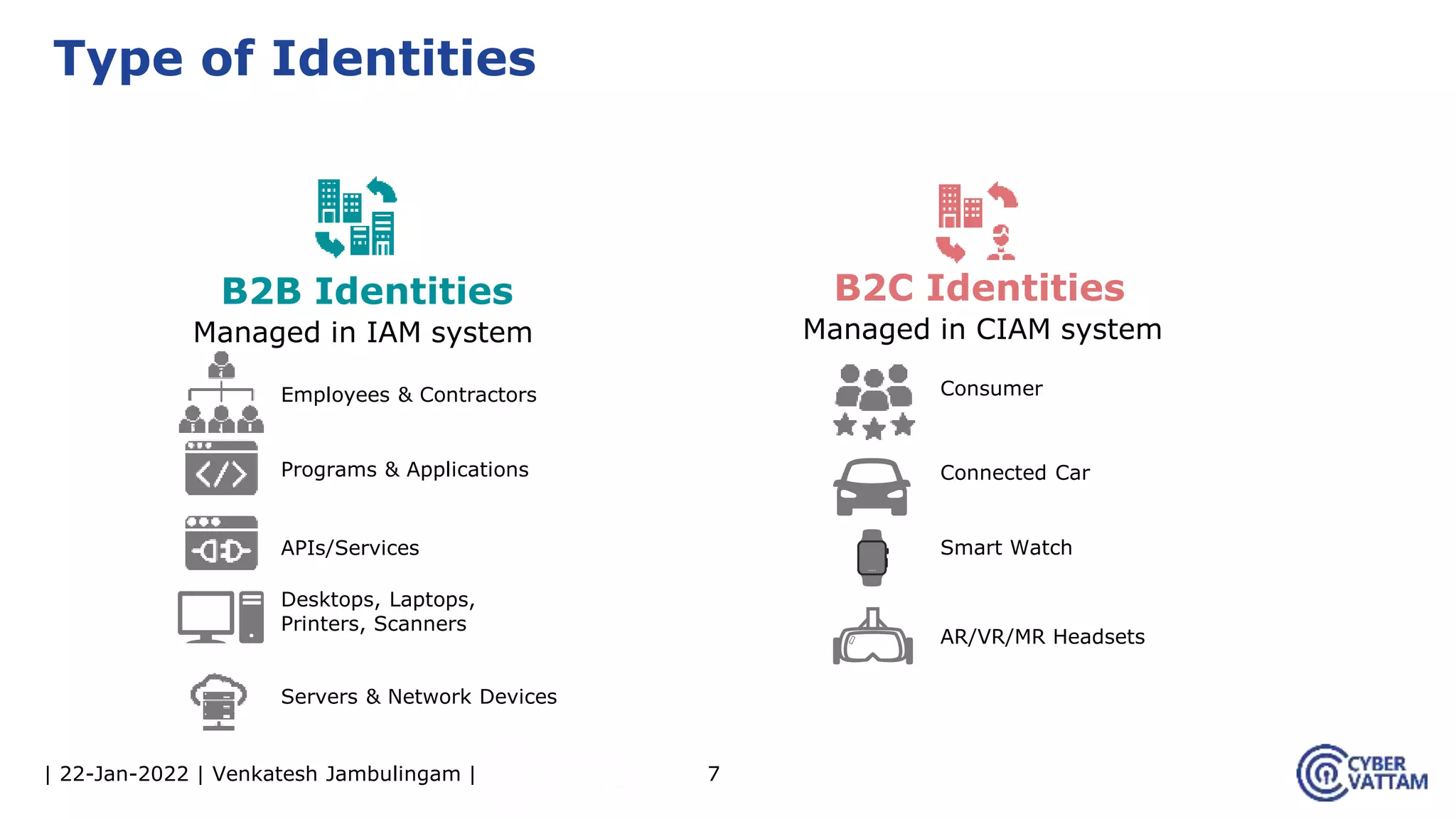
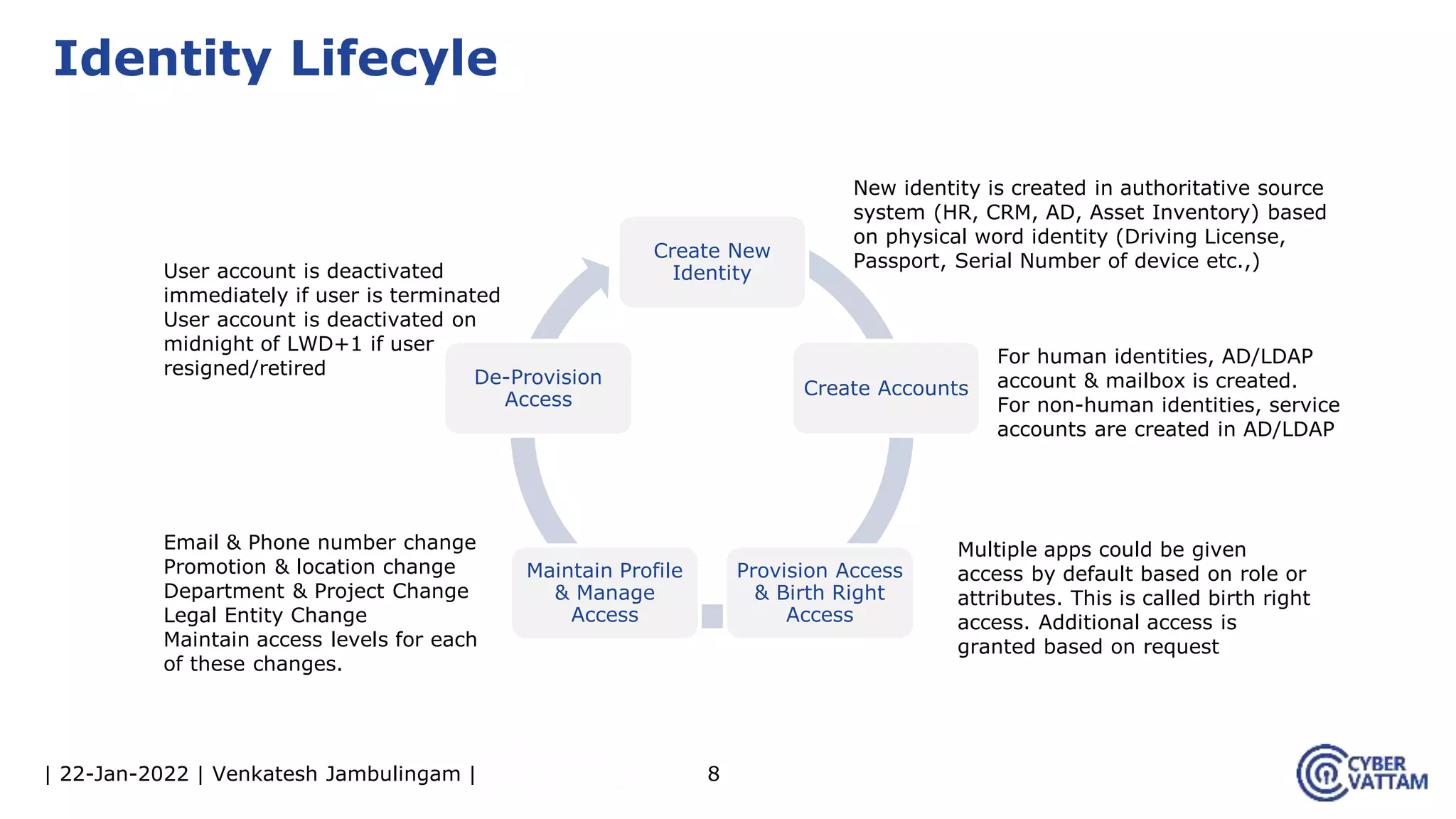
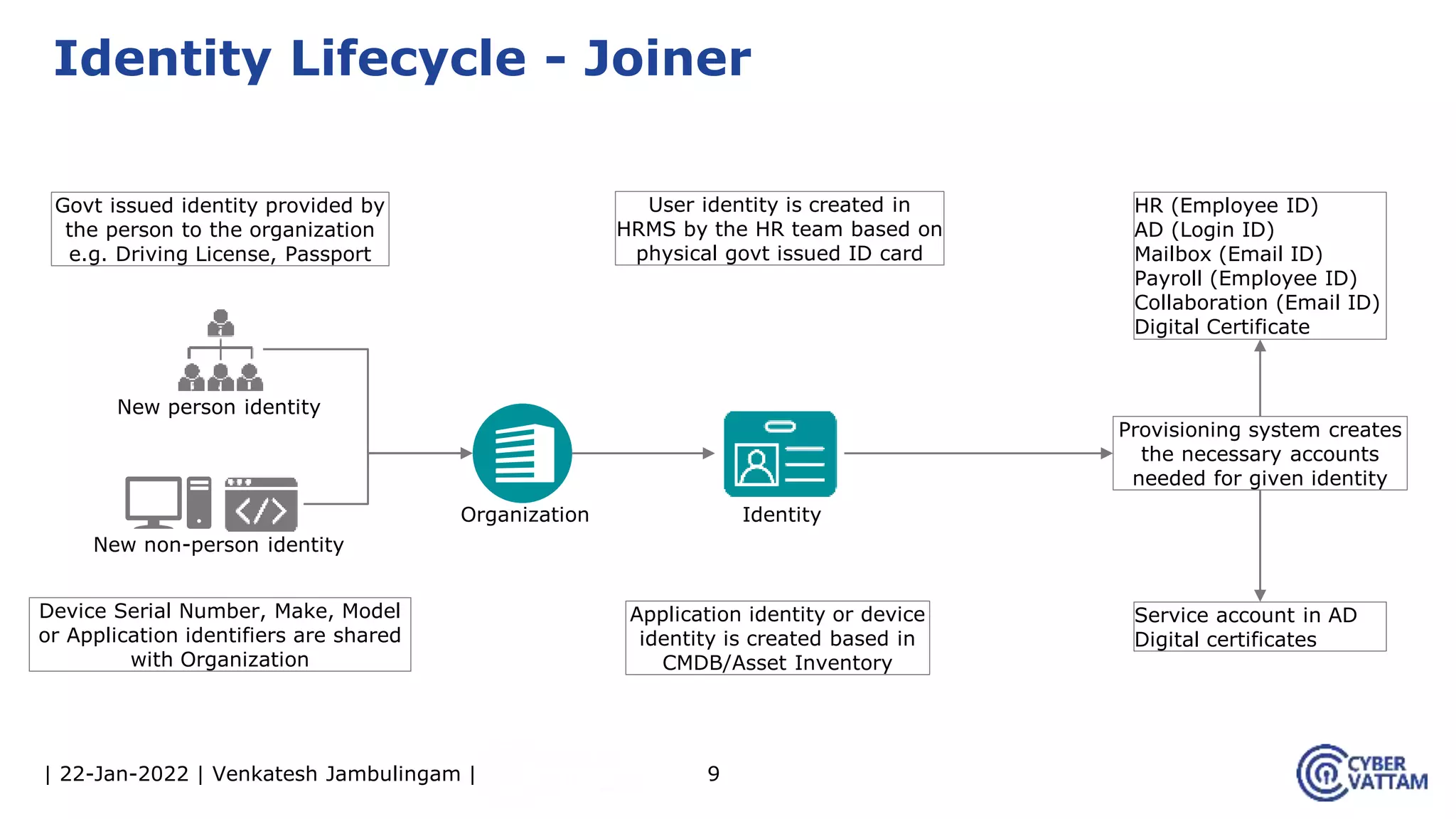
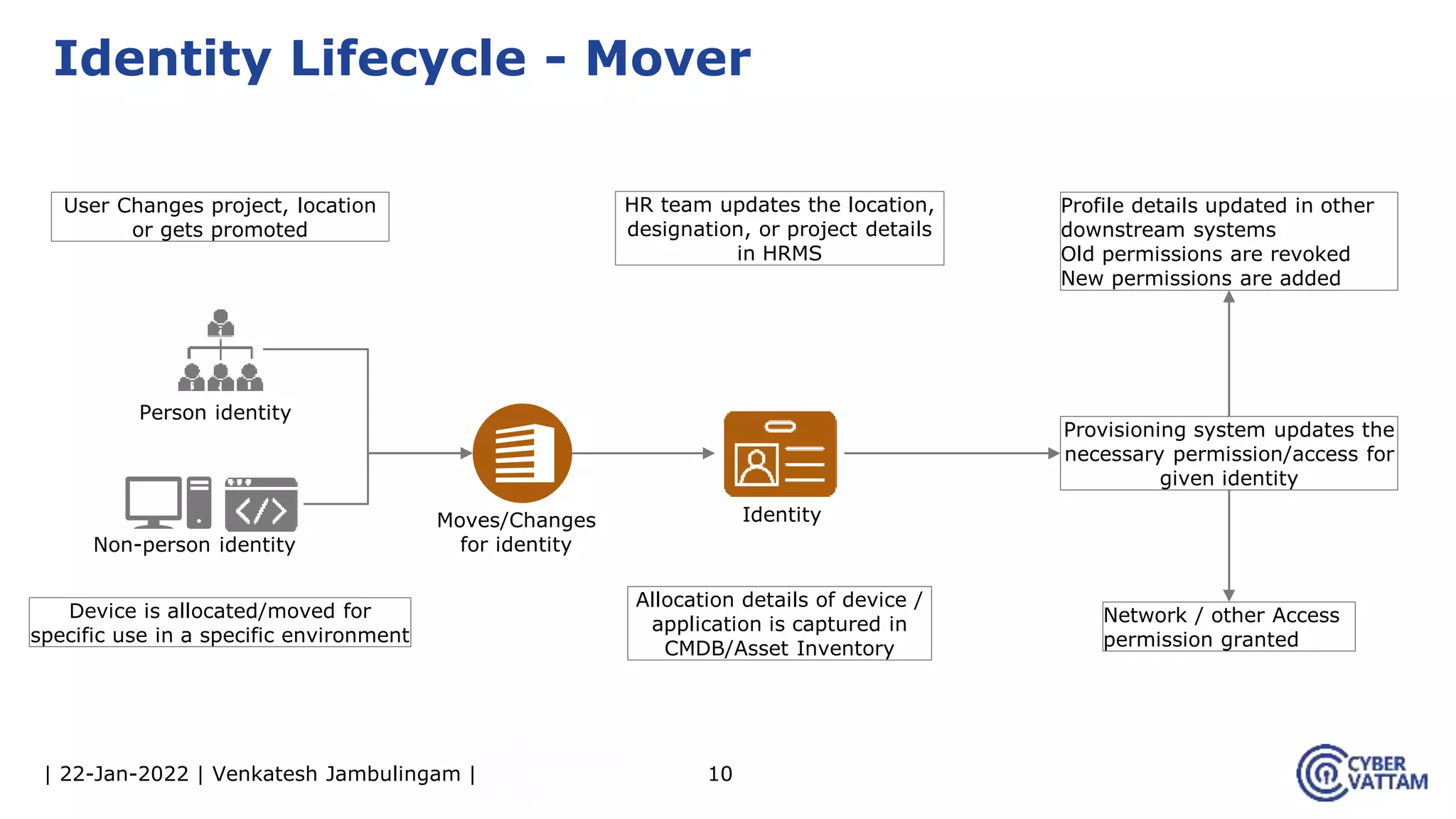
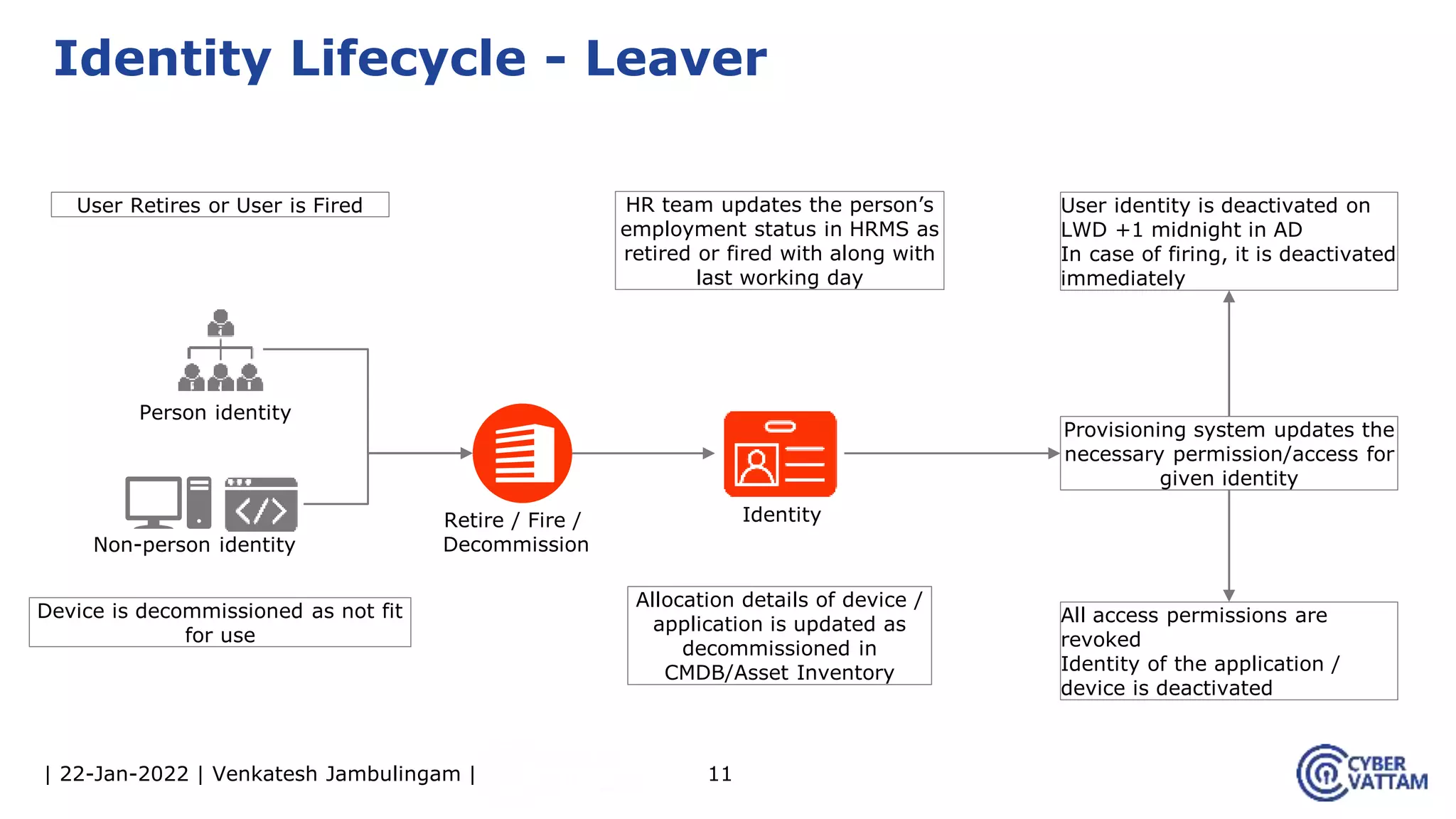
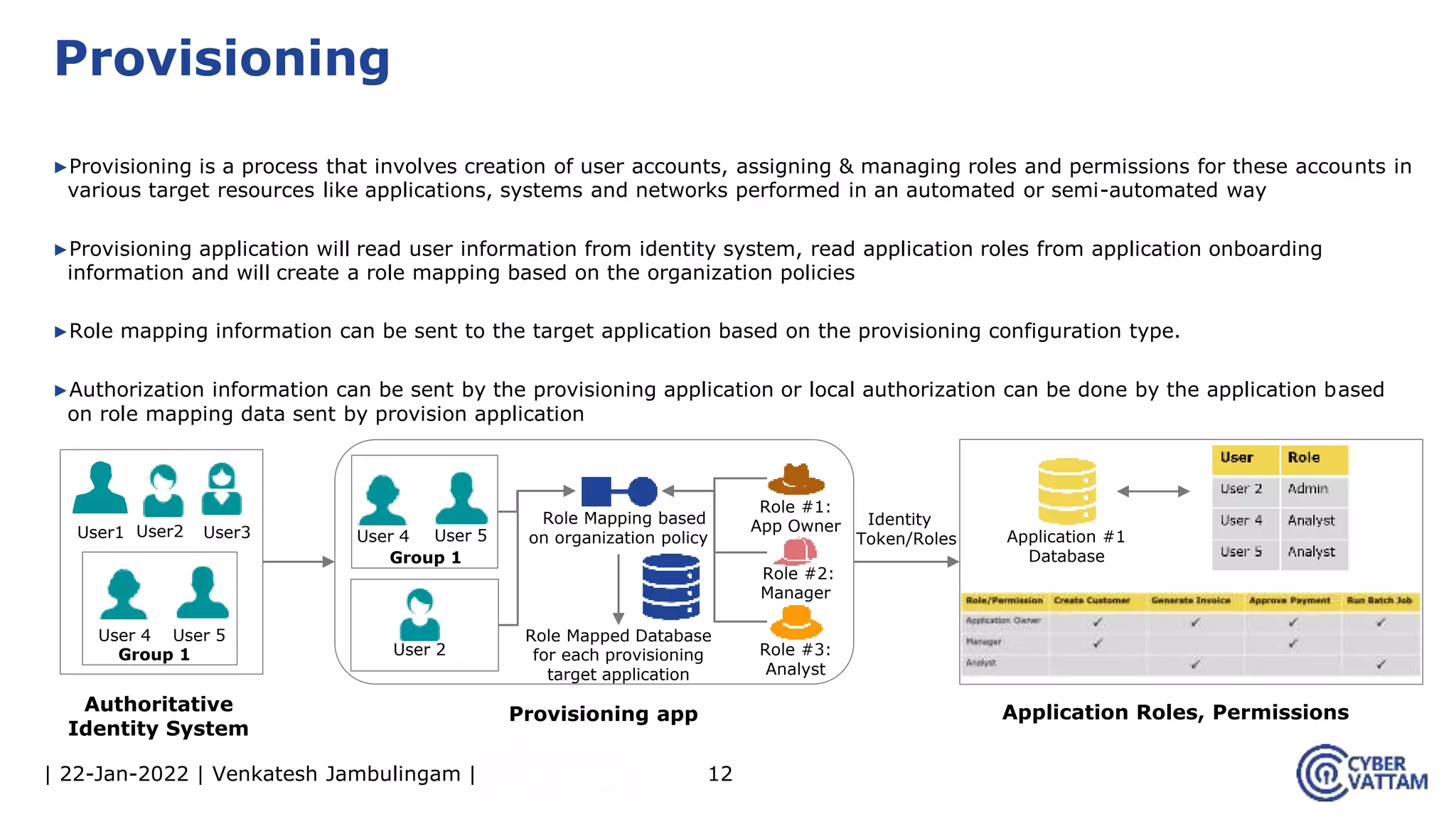
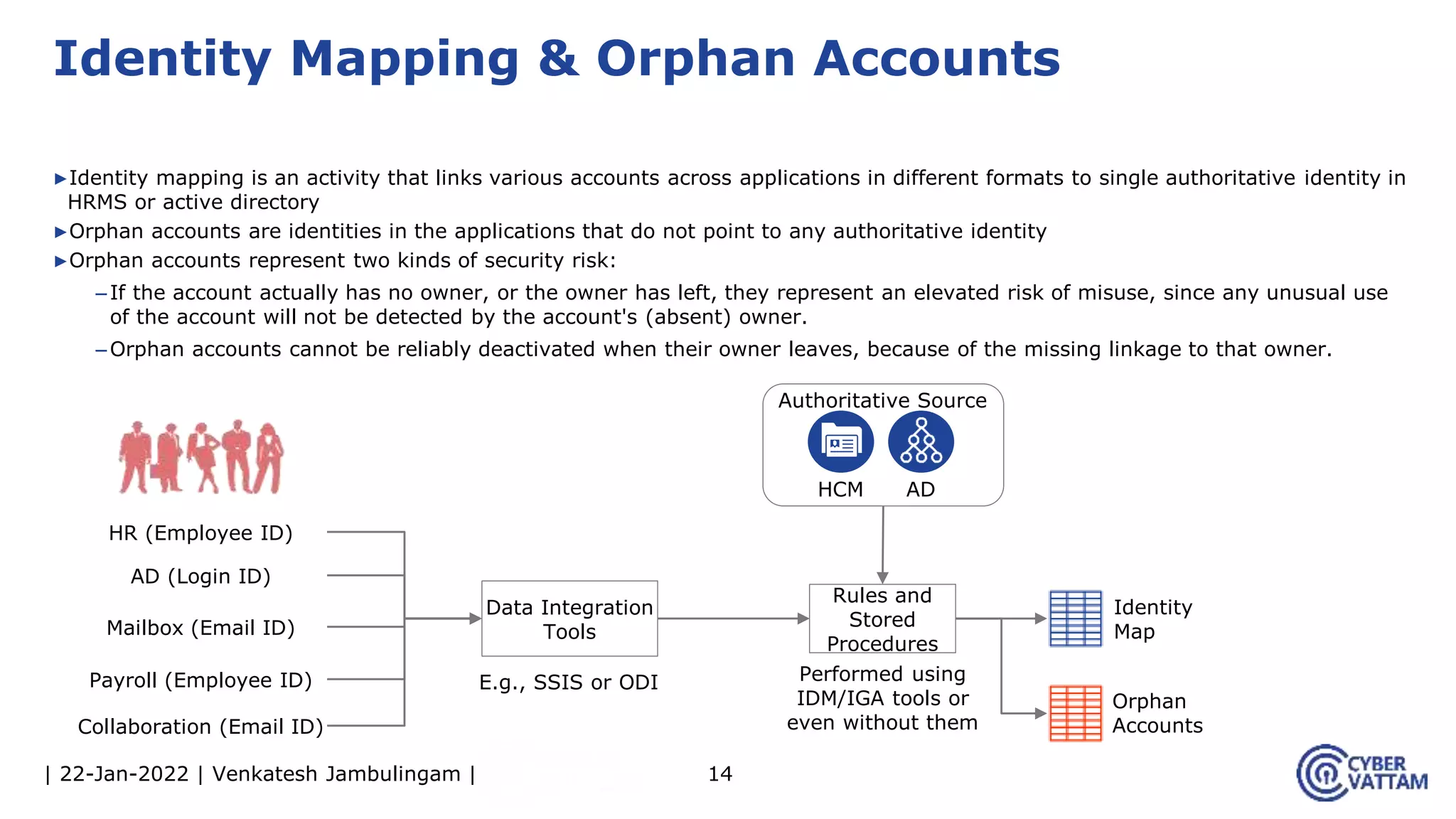
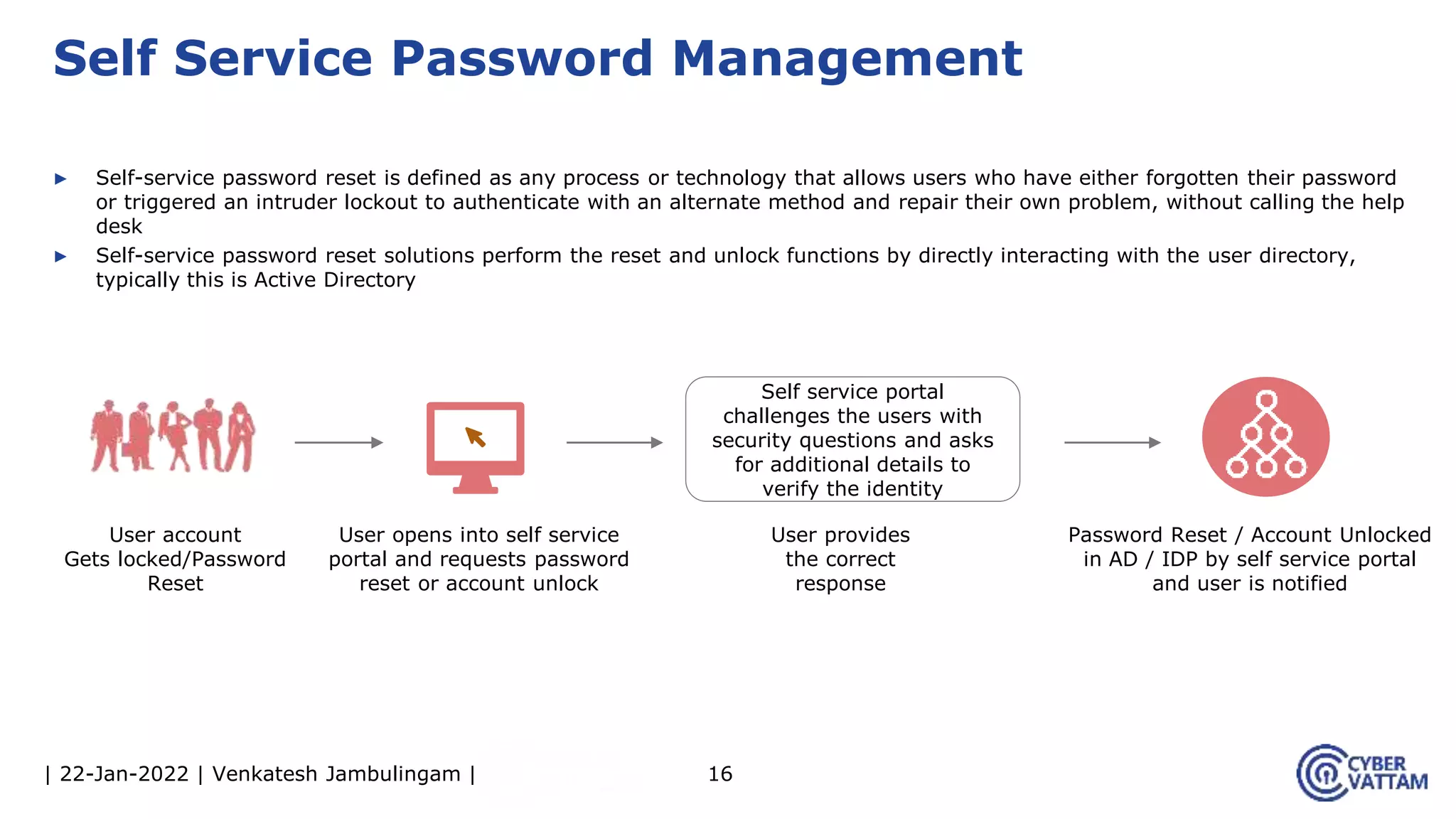
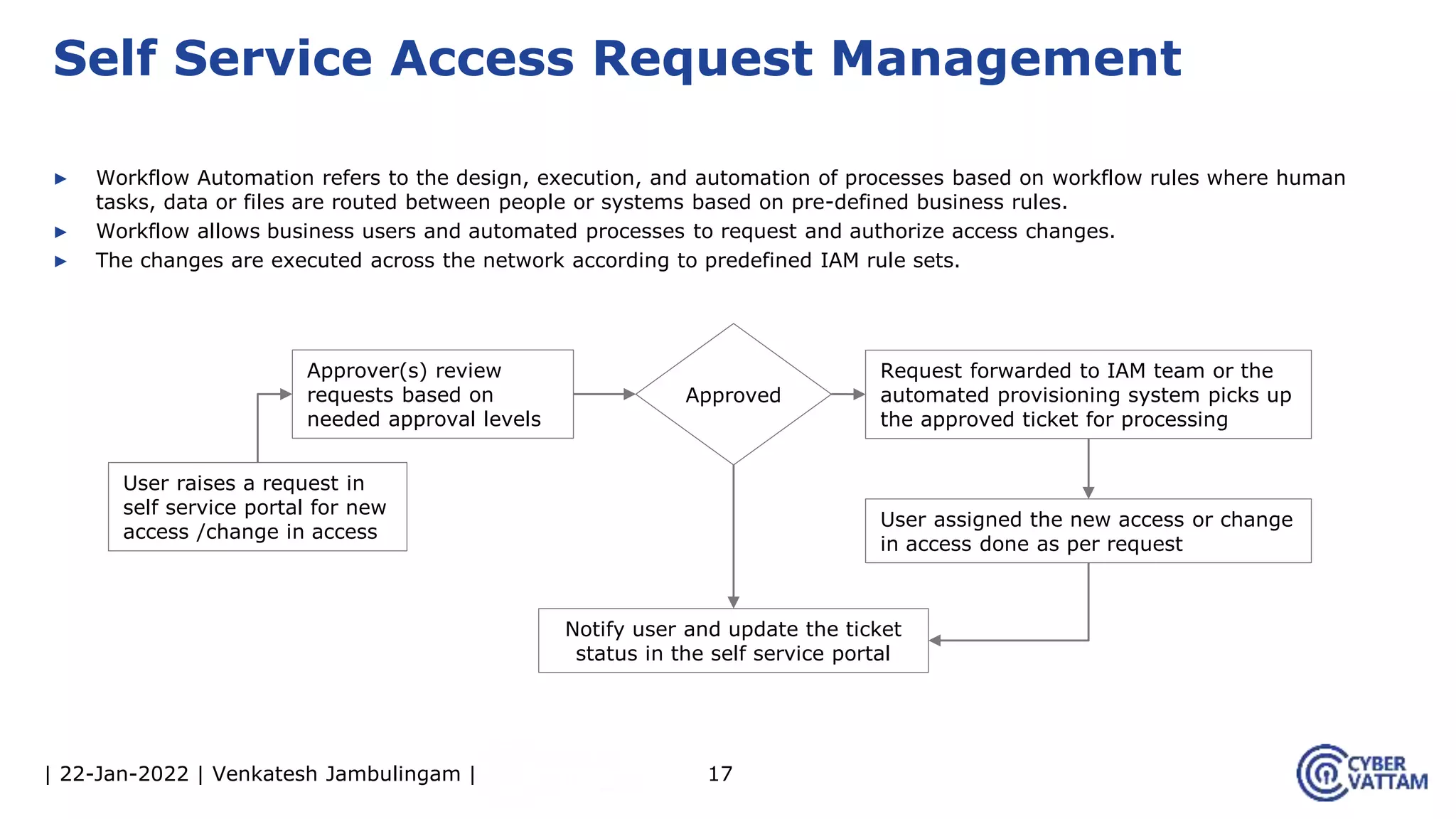
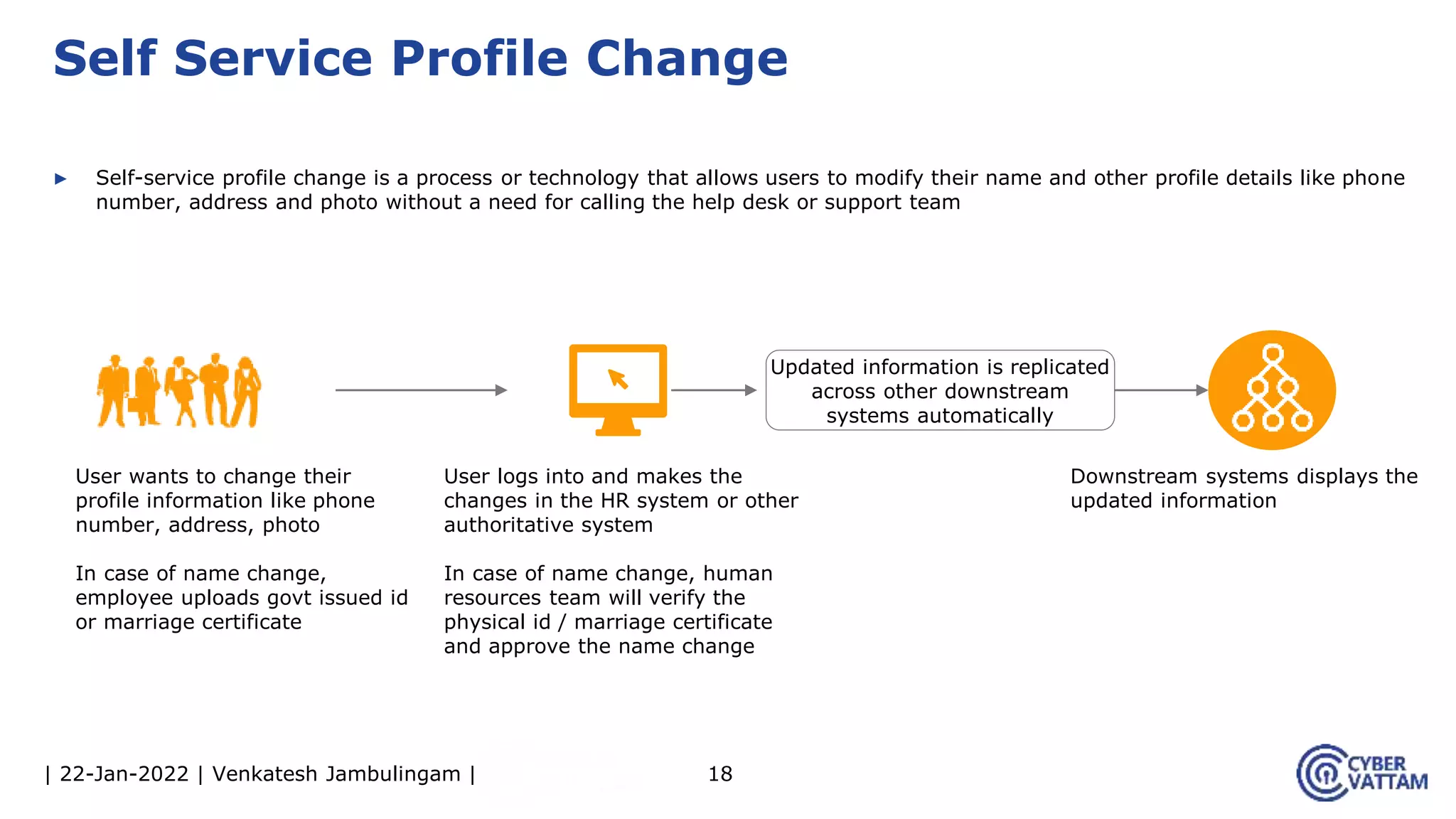
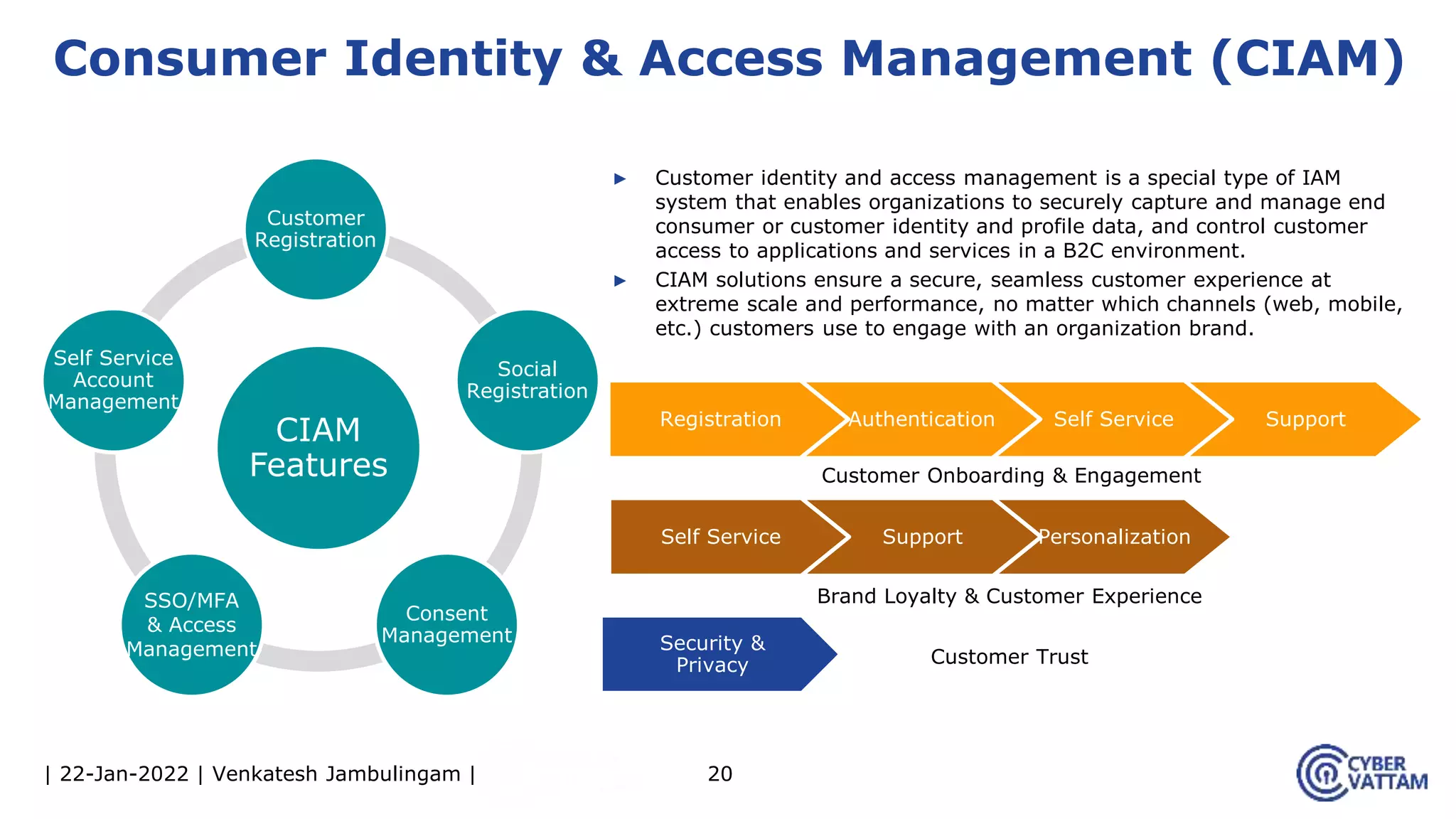
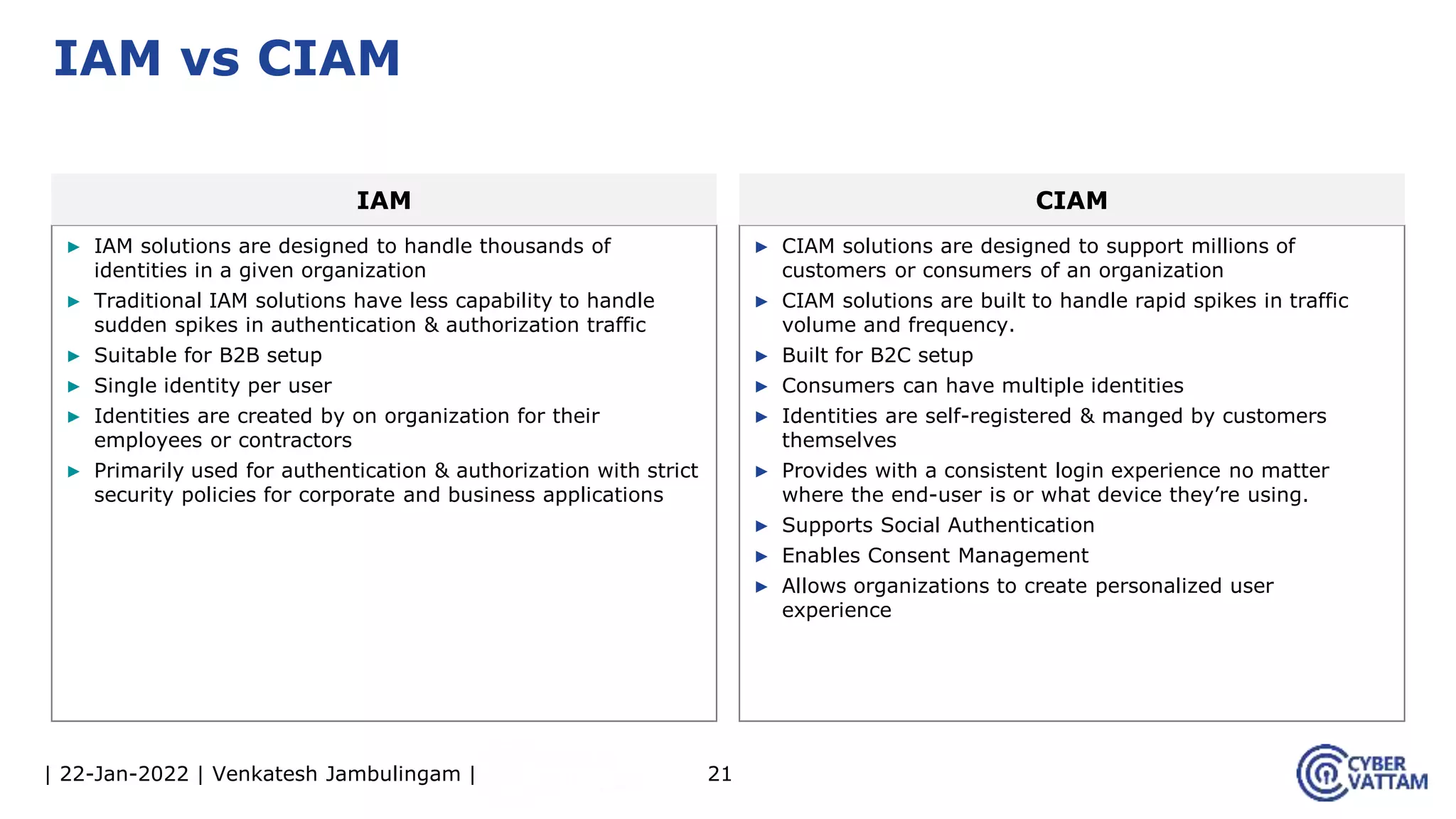
The document provides an overview of identity and access management (IAM), detailing the processes involved in identity lifecycle management, including creation, maintenance, and de-provisioning of identities. It emphasizes the importance of ensuring authorized access to resources through various components like self-service management, provisioning, and identity analytics. Additionally, it contrasts traditional IAM approaches with consumer identity and access management (CIAM), highlighting differences in user management and intended application environments.