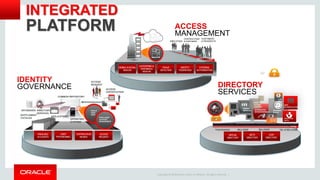
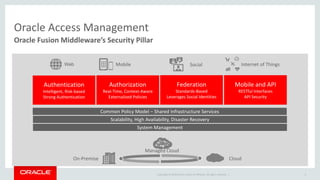
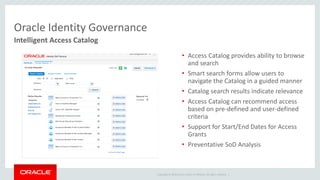
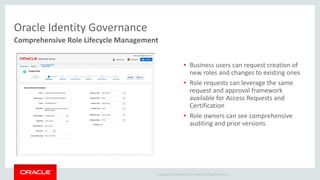
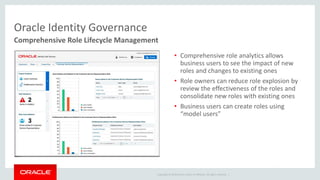
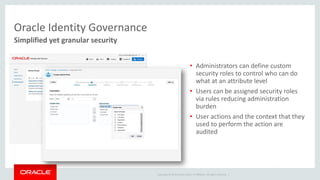
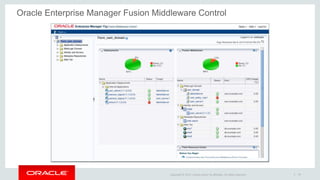
The document discusses Oracle Identity and Access Management solutions. It provides an overview of Oracle's offerings for authentication, authorization, federation, mobile security, access management, identity governance, privileged access management, and directory services. Key capabilities mentioned include single sign-on, adaptive access and fraud prevention, identity federation, role-based access control, and support for cloud, mobile, and on-premise deployments at large scale.