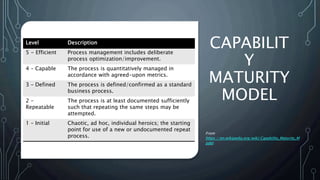
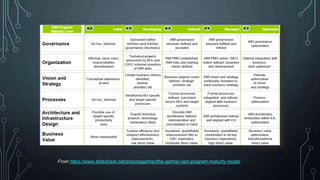
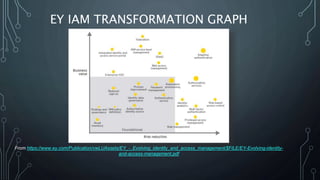
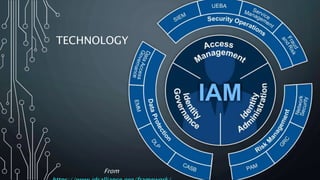
This document outlines the maturity models for Identity and Access Management (IAM), detailing the progression through five levels from chaotic initial processes to efficient, optimized management. It emphasizes the importance of strategic planning, stakeholder engagement, and process documentation as key steps in advancing IAM maturity. Additionally, it provides resources and next steps for organizations to assess and improve their IAM practices.