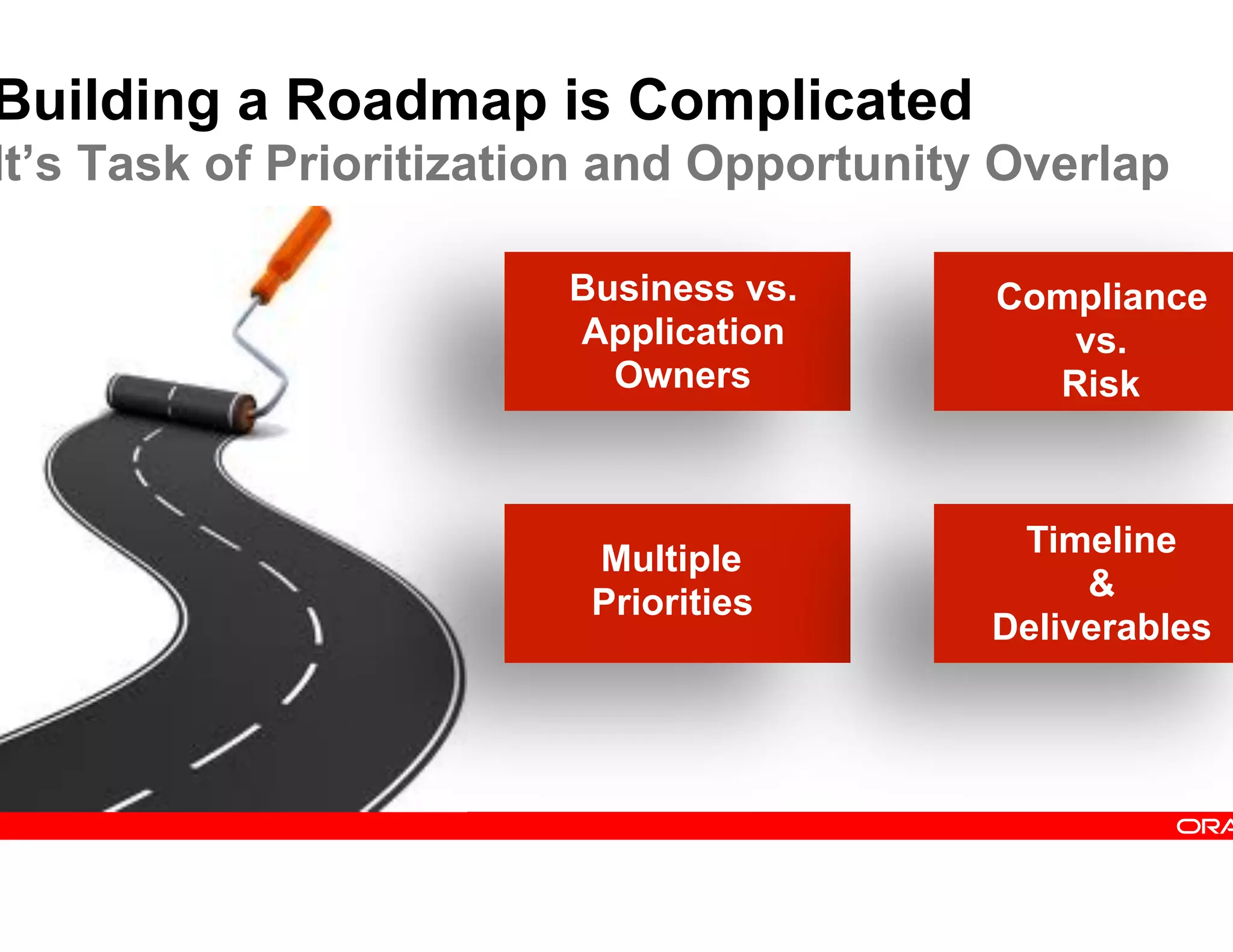
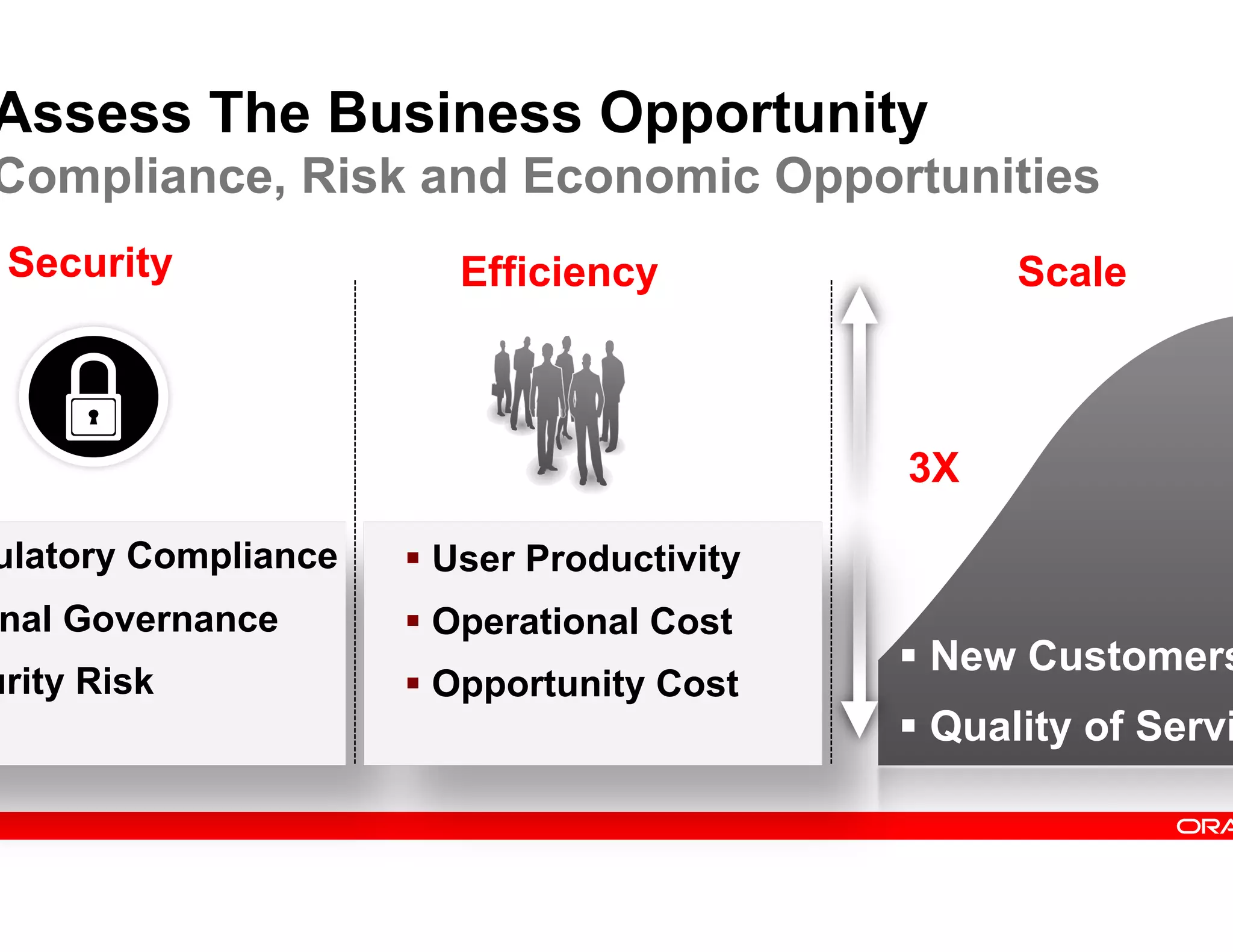
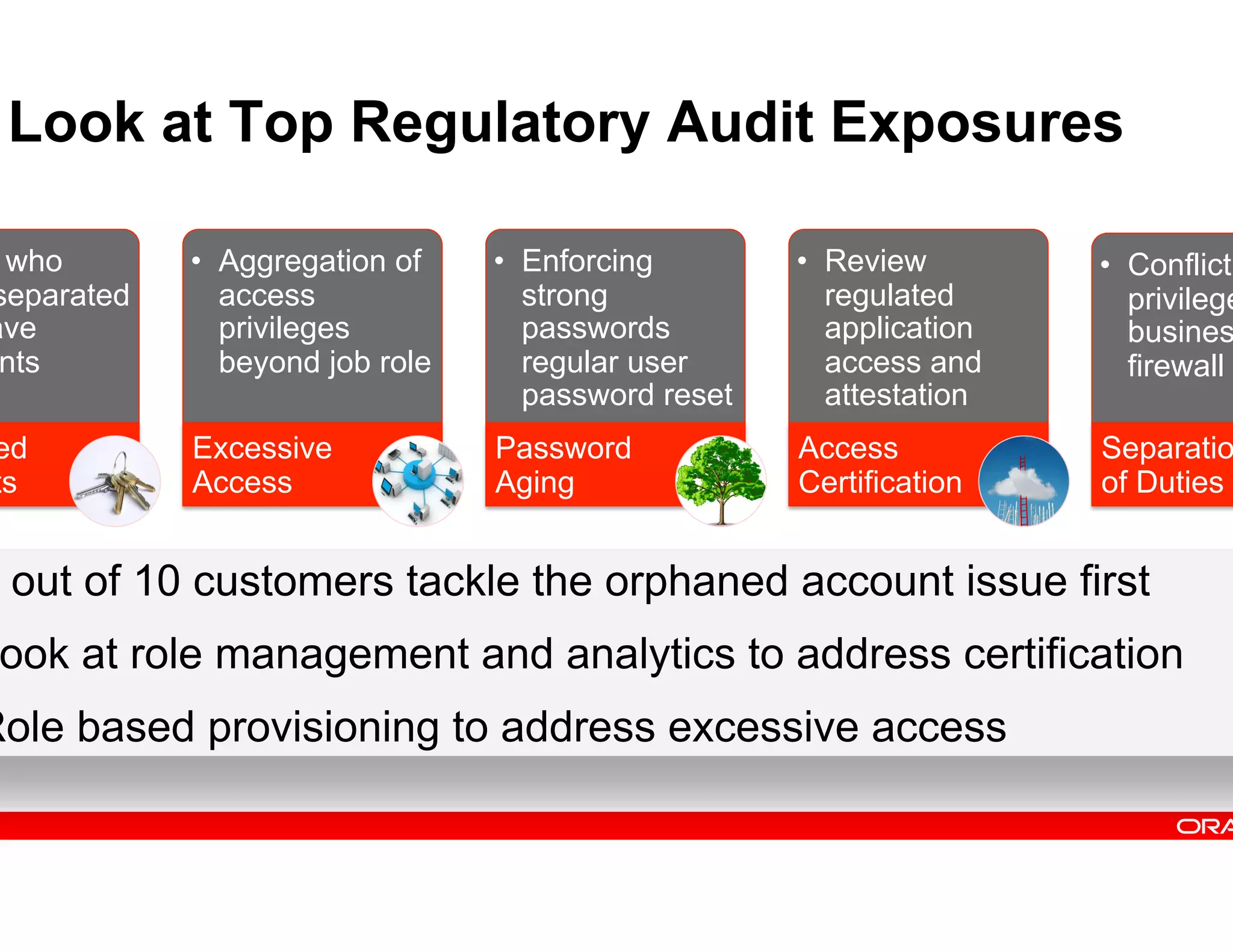
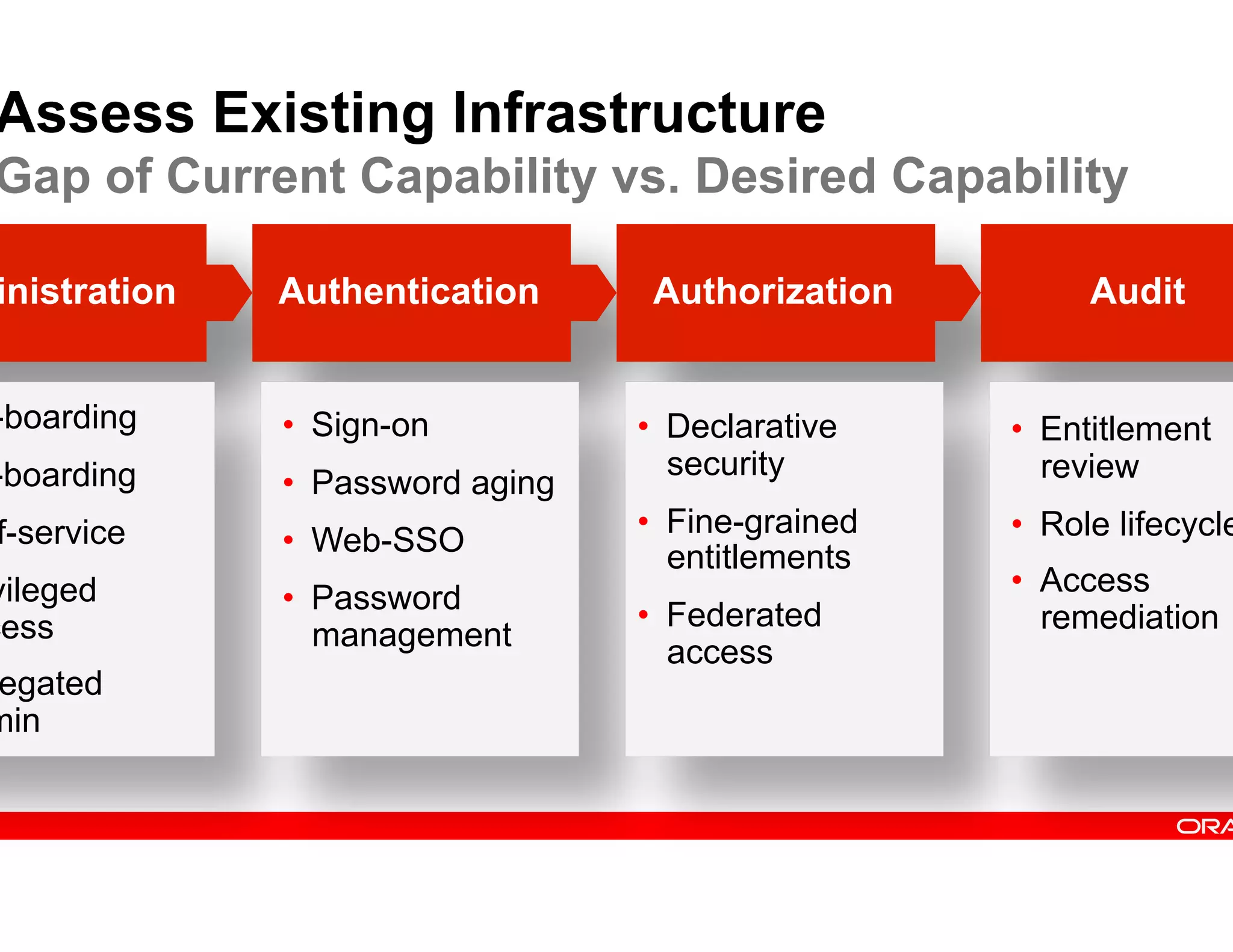
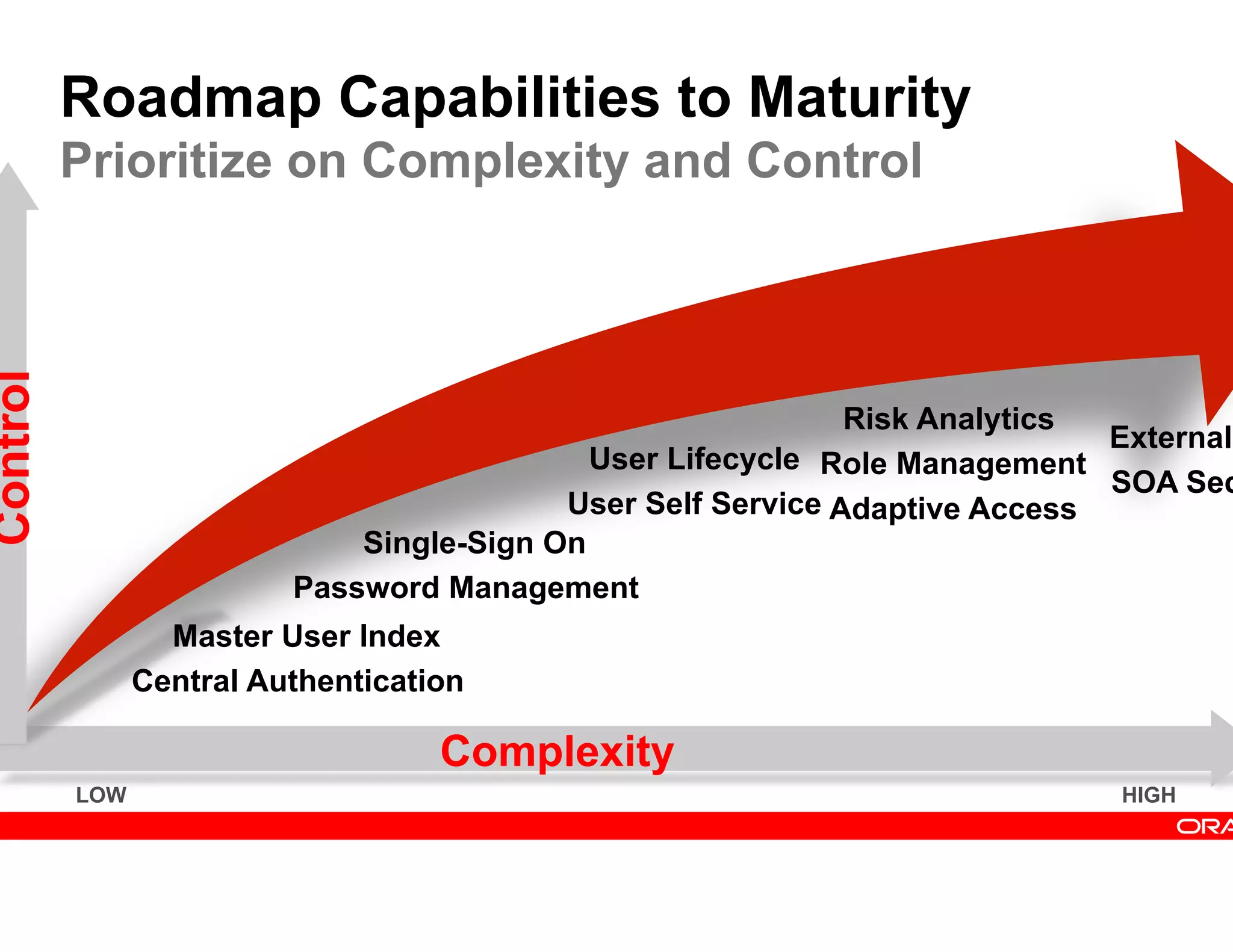
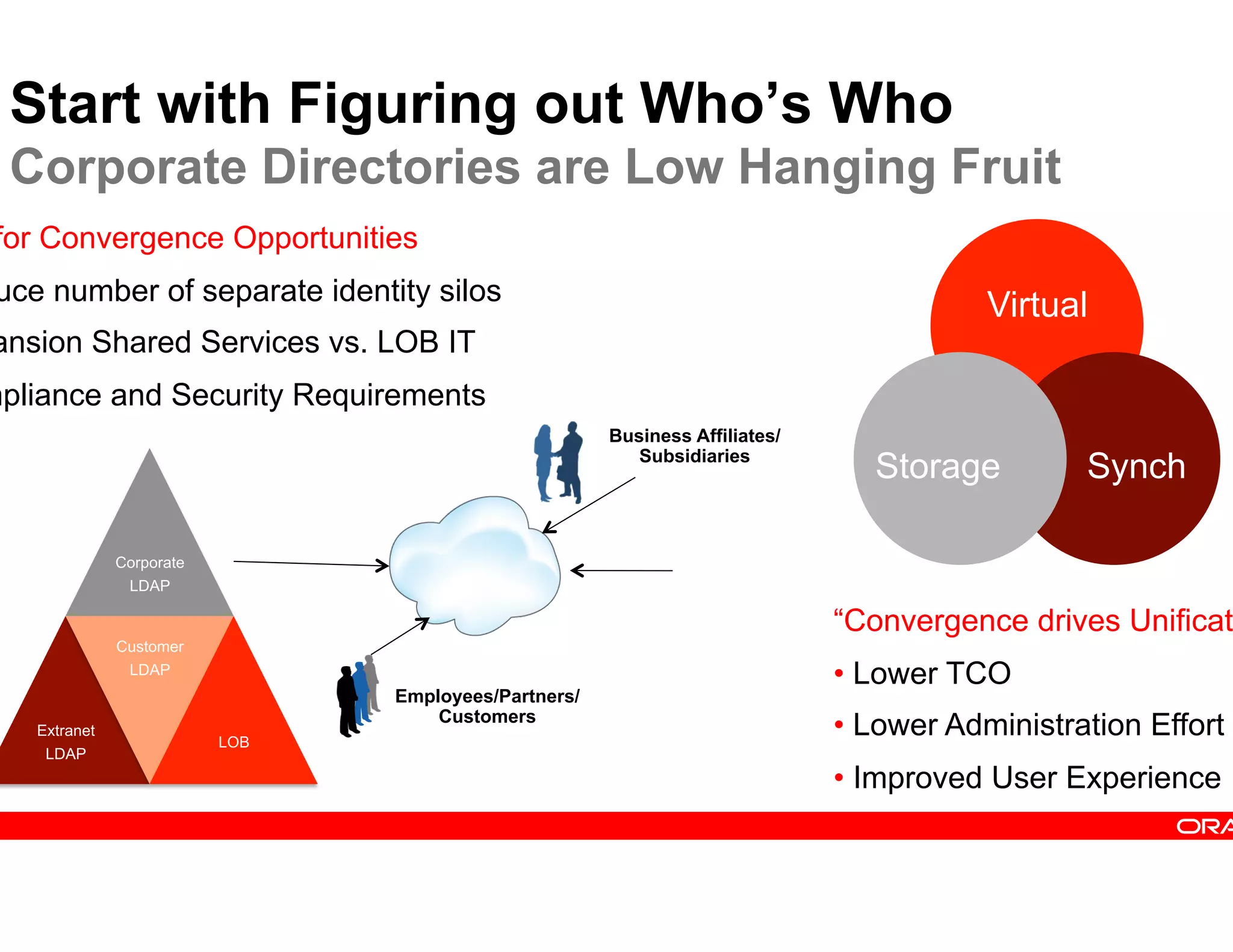
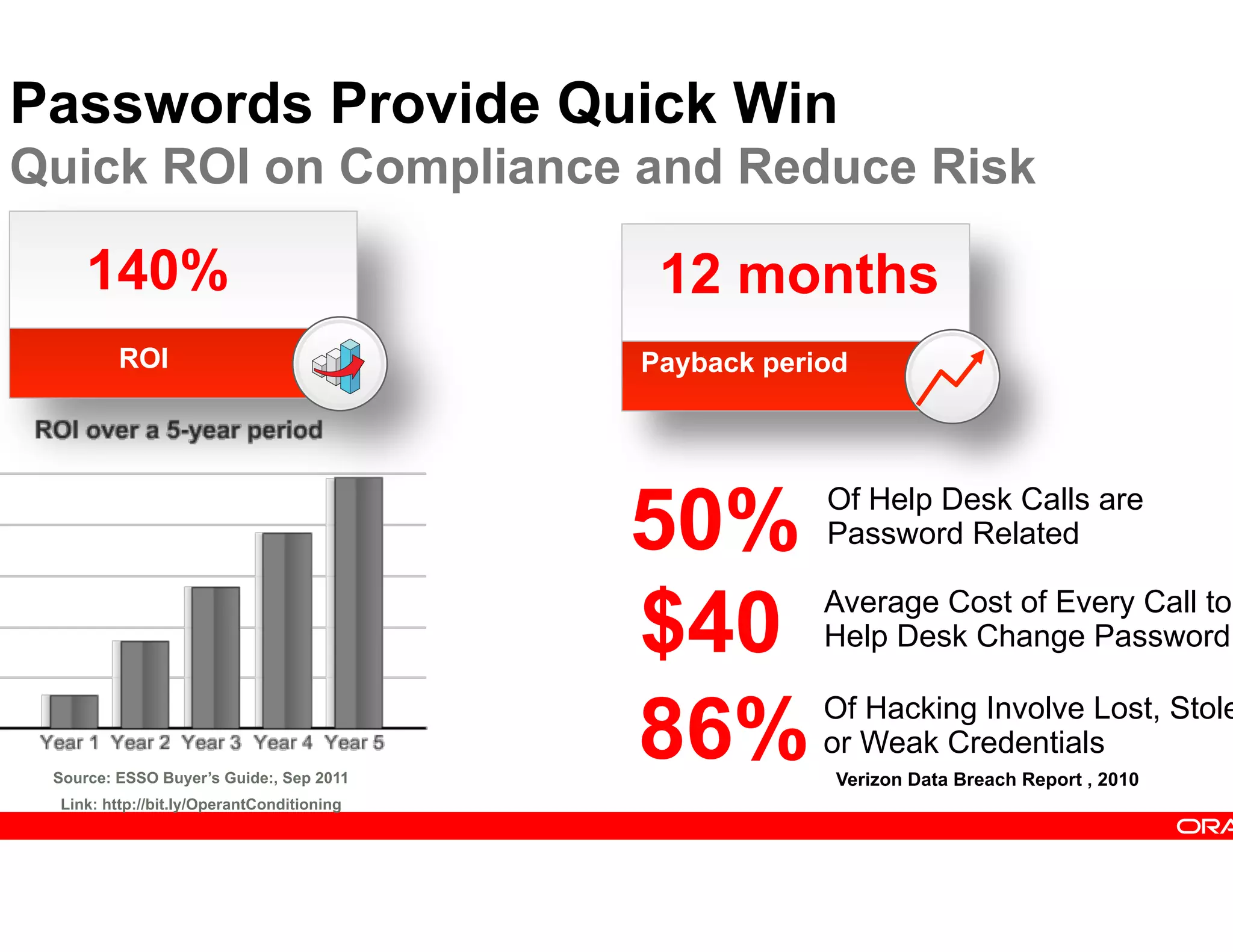
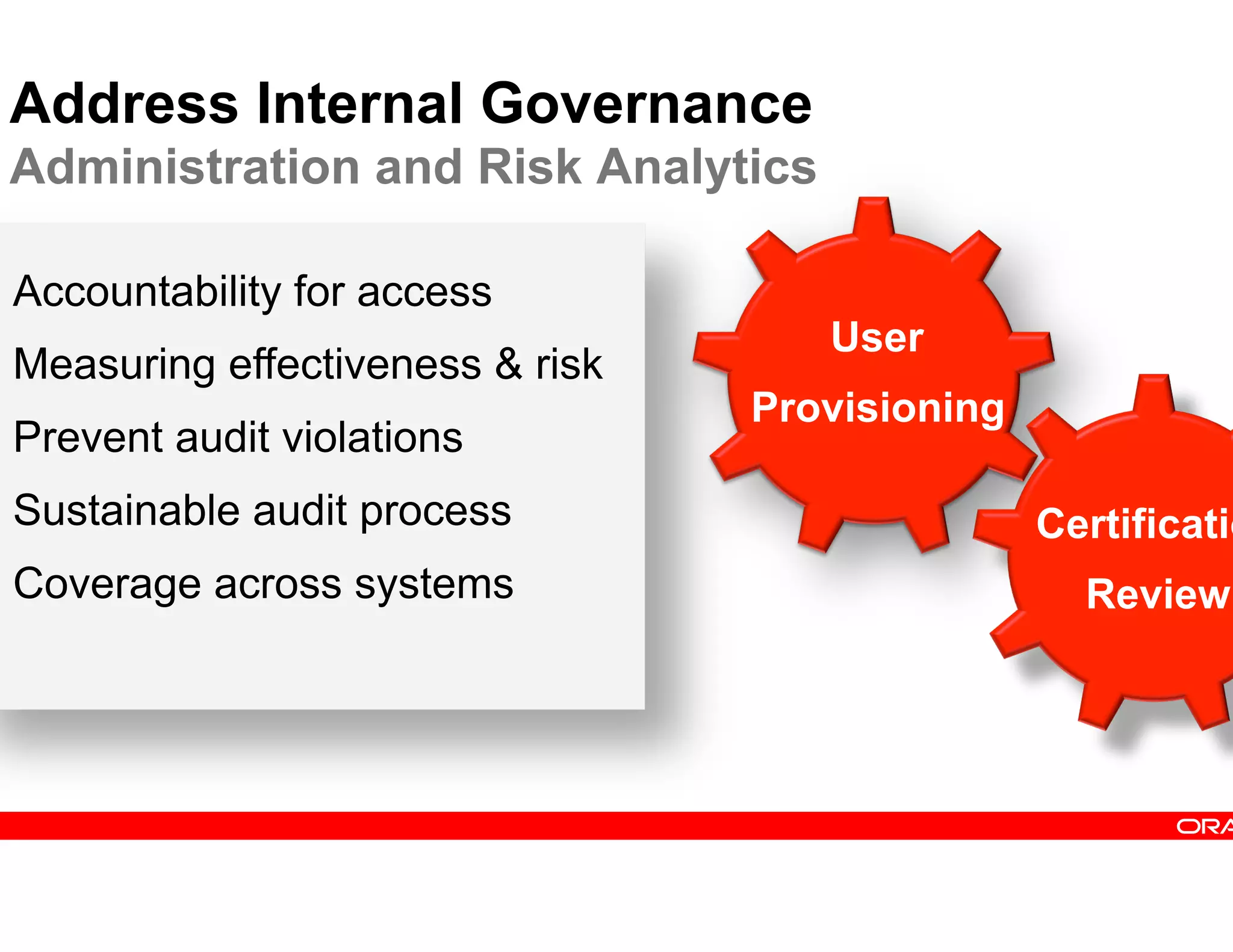
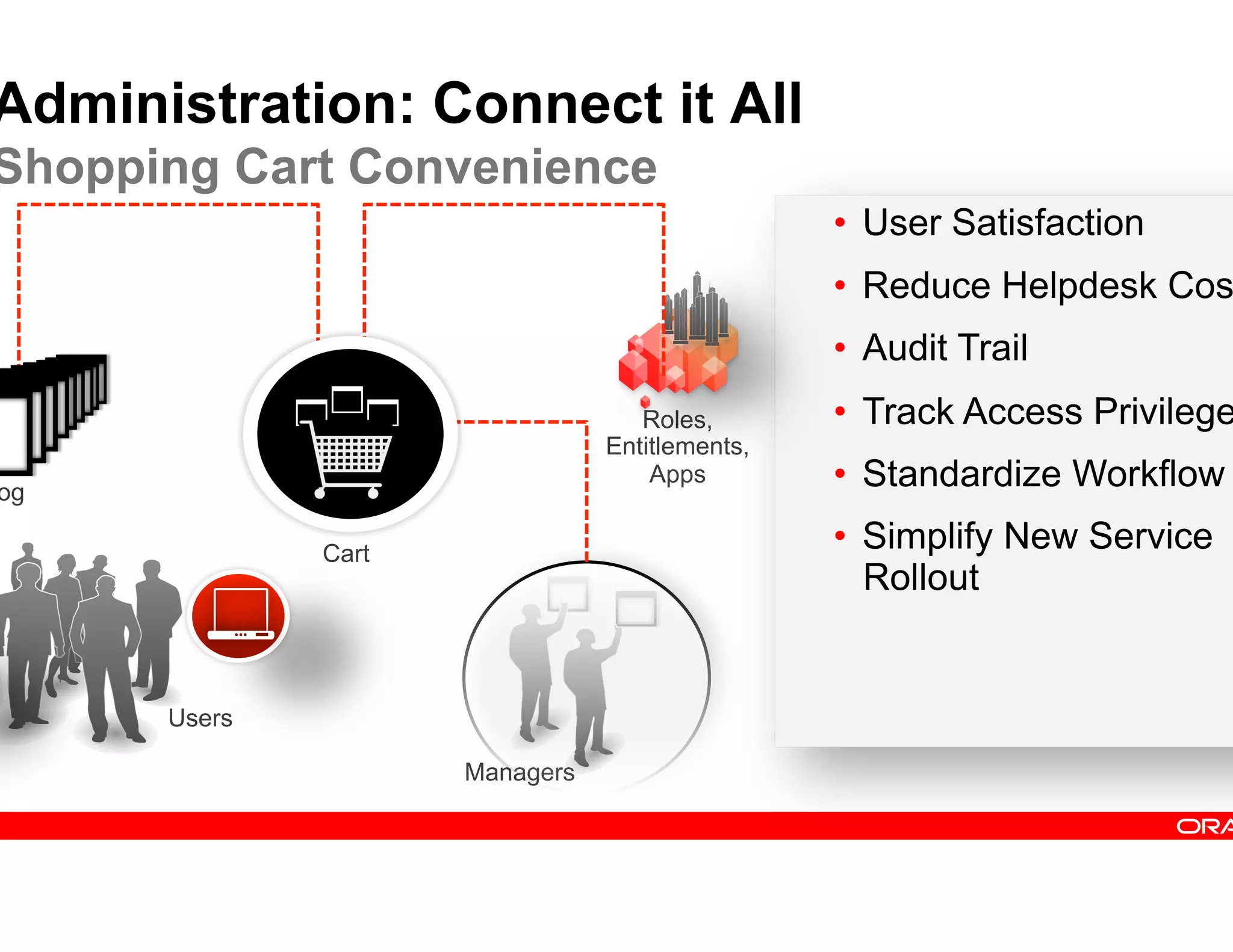
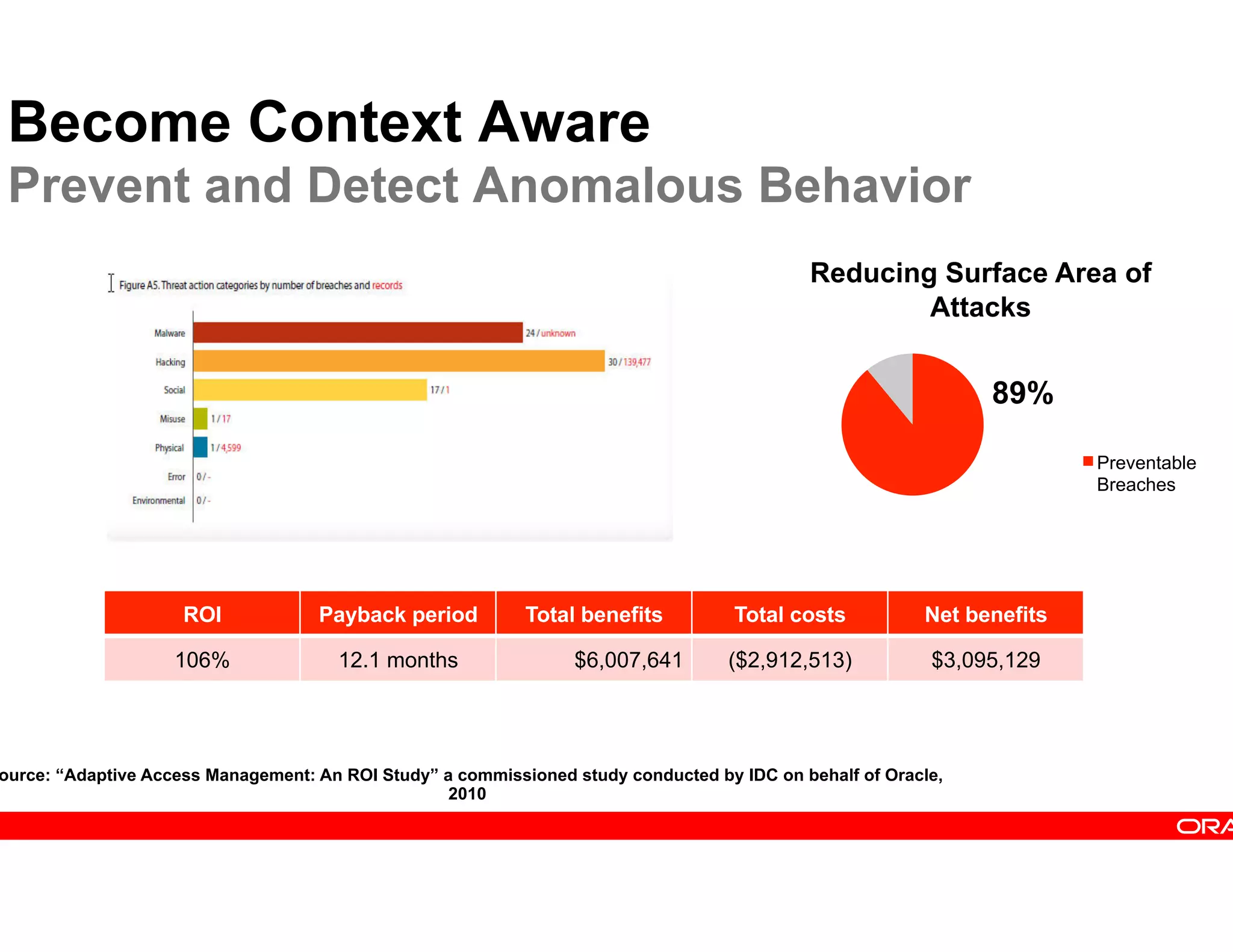
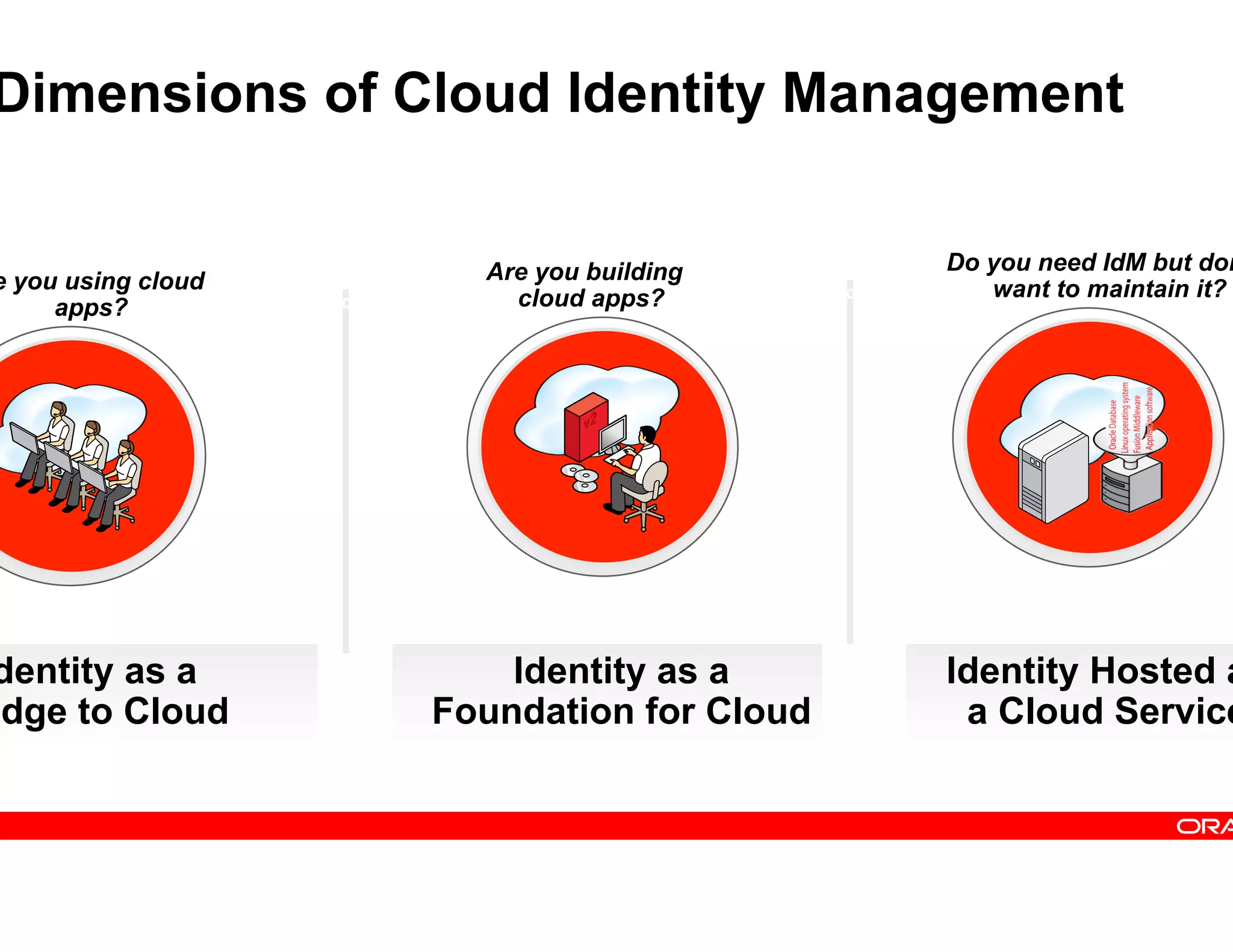
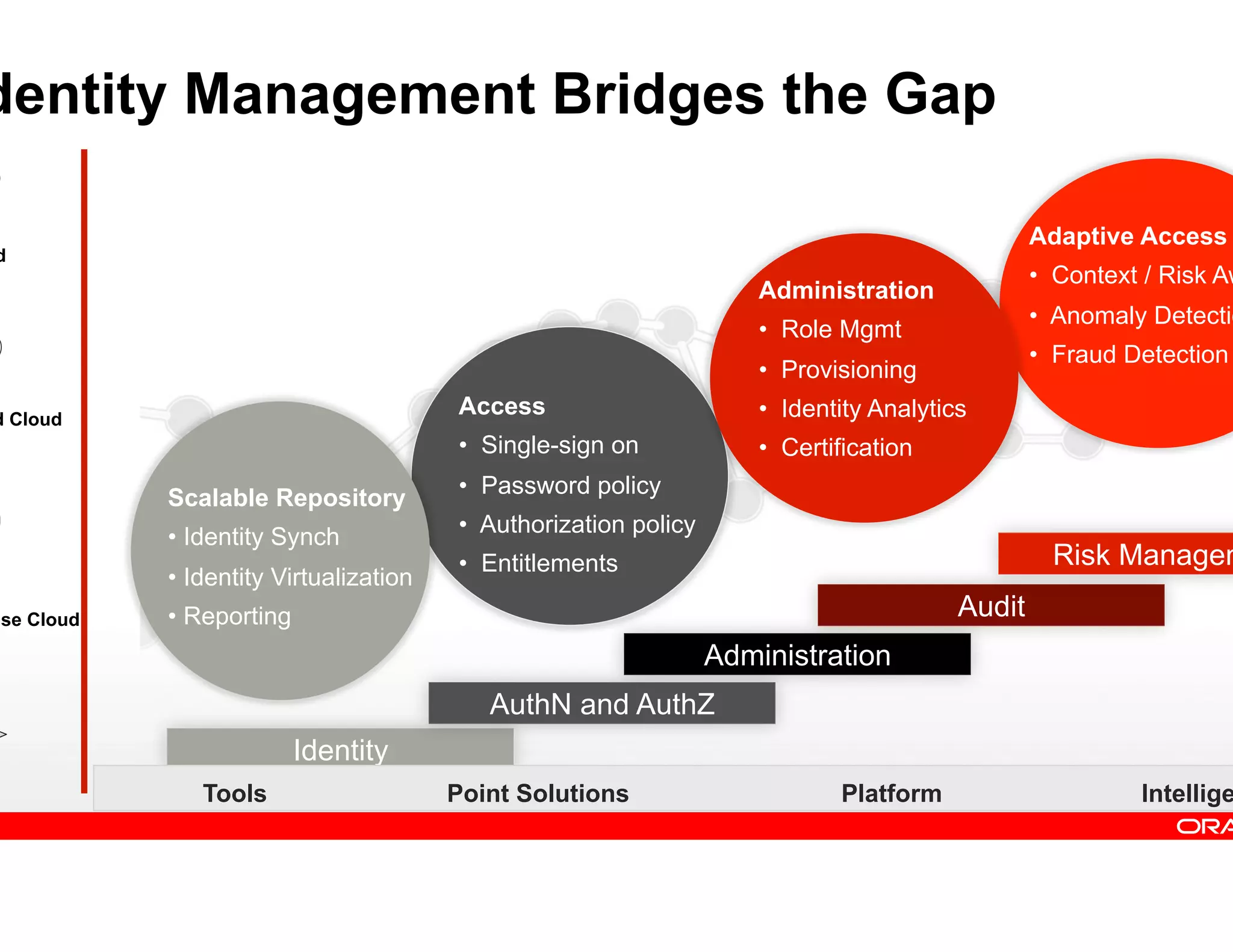
This document provides guidance on building a comprehensive identity roadmap. It recommends prioritizing initiatives based on complexity and assessing the existing identity infrastructure. Quick wins can be found in addressing orphaned accounts, role management, and implementing single sign-on and password management. The roadmap should plan for increasing maturity through user lifecycle management, role-based access controls, and risk analytics. It also suggests considering identity as a service hosted in the cloud.