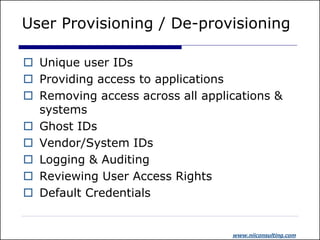
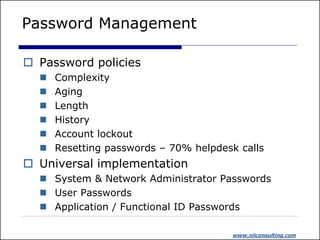
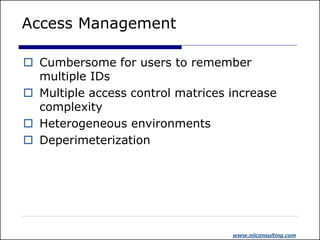
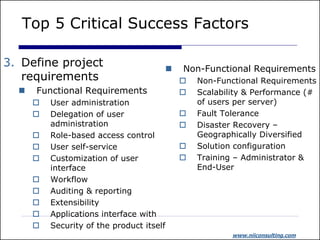
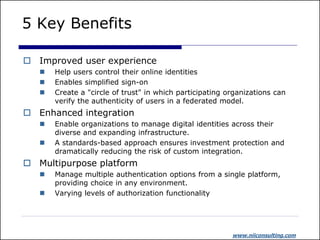
The document discusses identity and access management (IAM). It outlines common IAM problems like weak passwords, password sharing, and lack of single sign-on. The presentation then discusses how IAM solutions can provide benefits like improved user experience through single sign-on, enhanced integration across systems, centralized administration to reduce costs, and increased security. Critical success factors for IAM projects include identifying business champions, thorough vendor analysis, defining requirements, understanding product features, and ensuring business support.