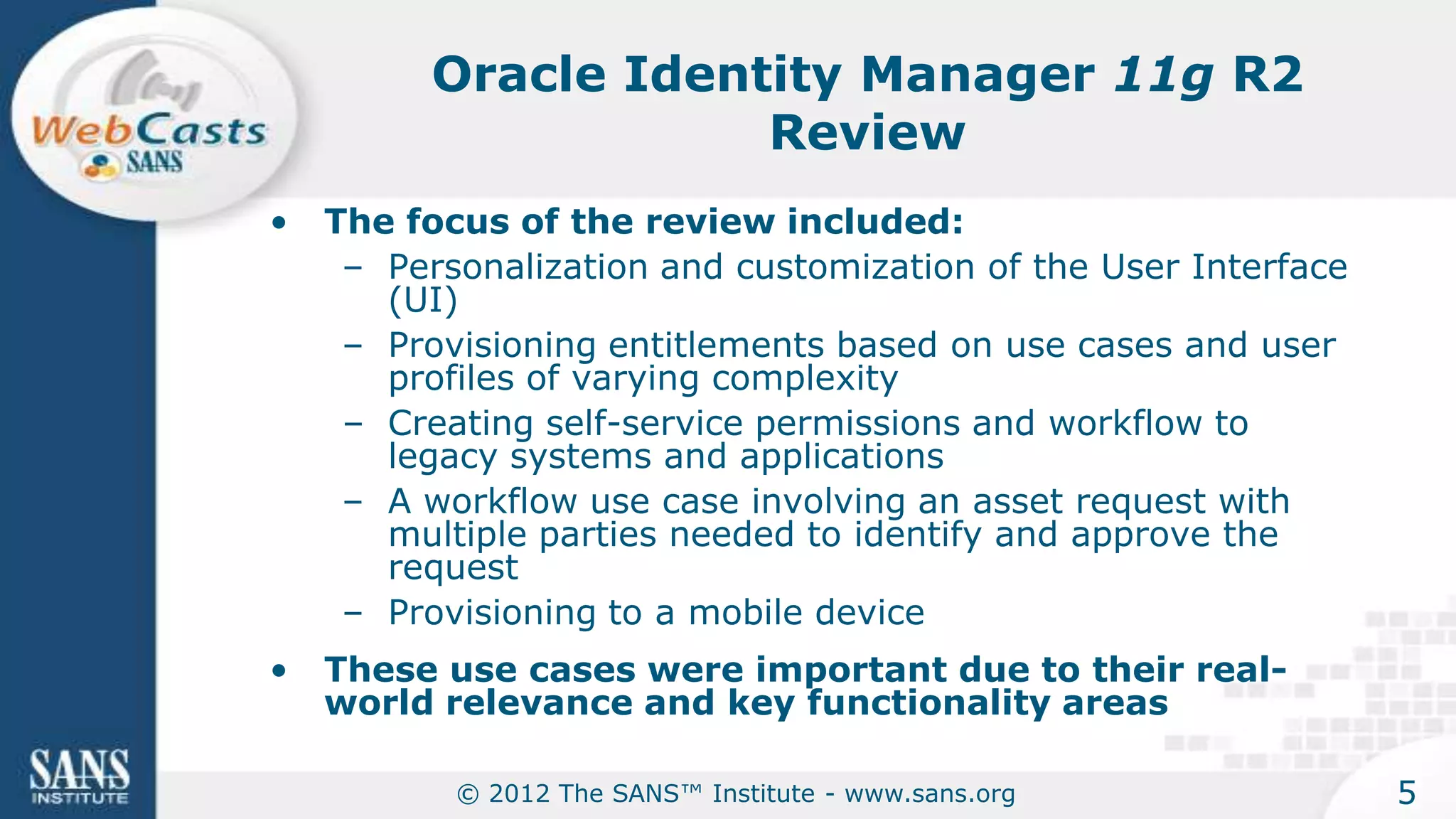
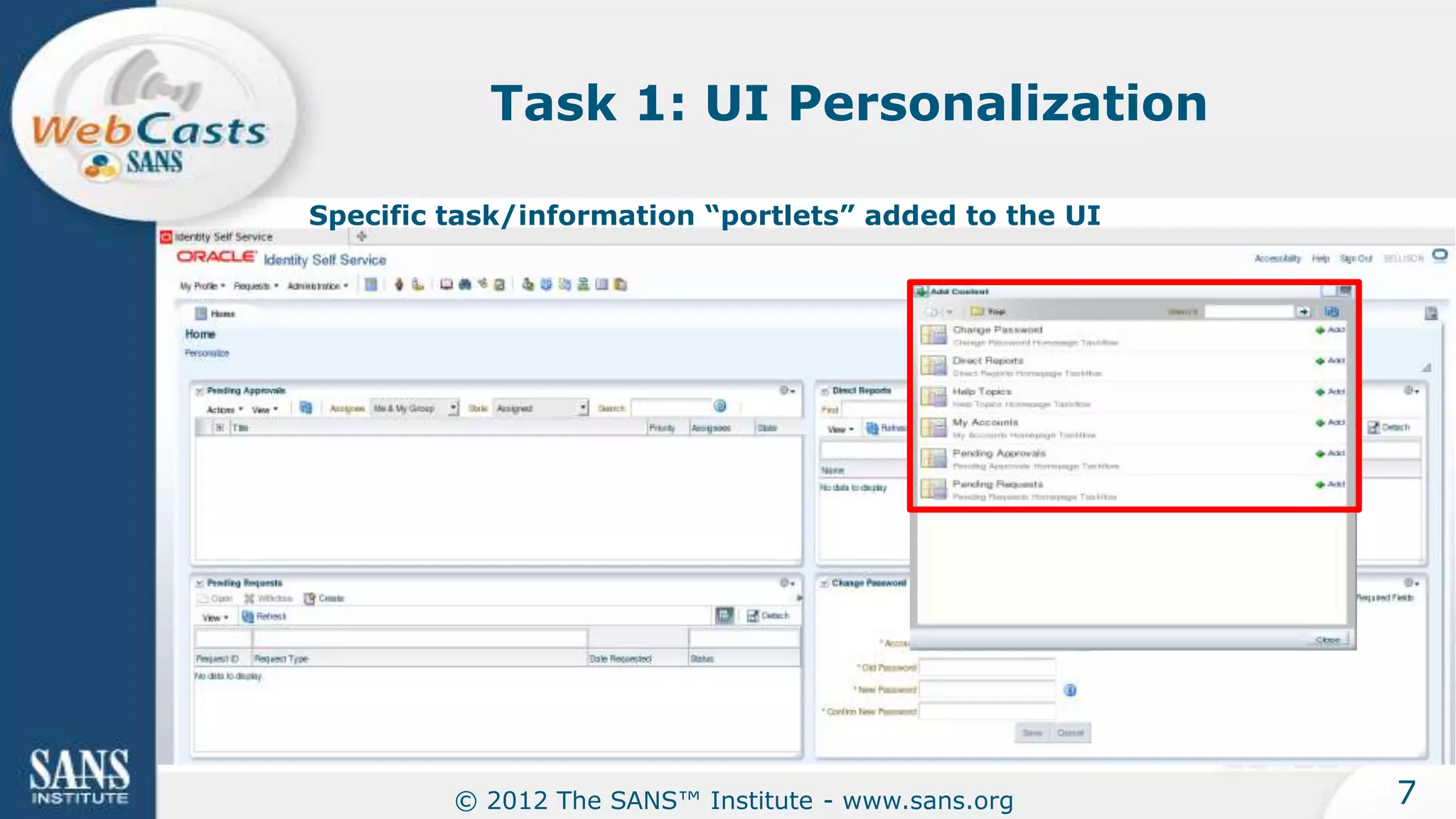
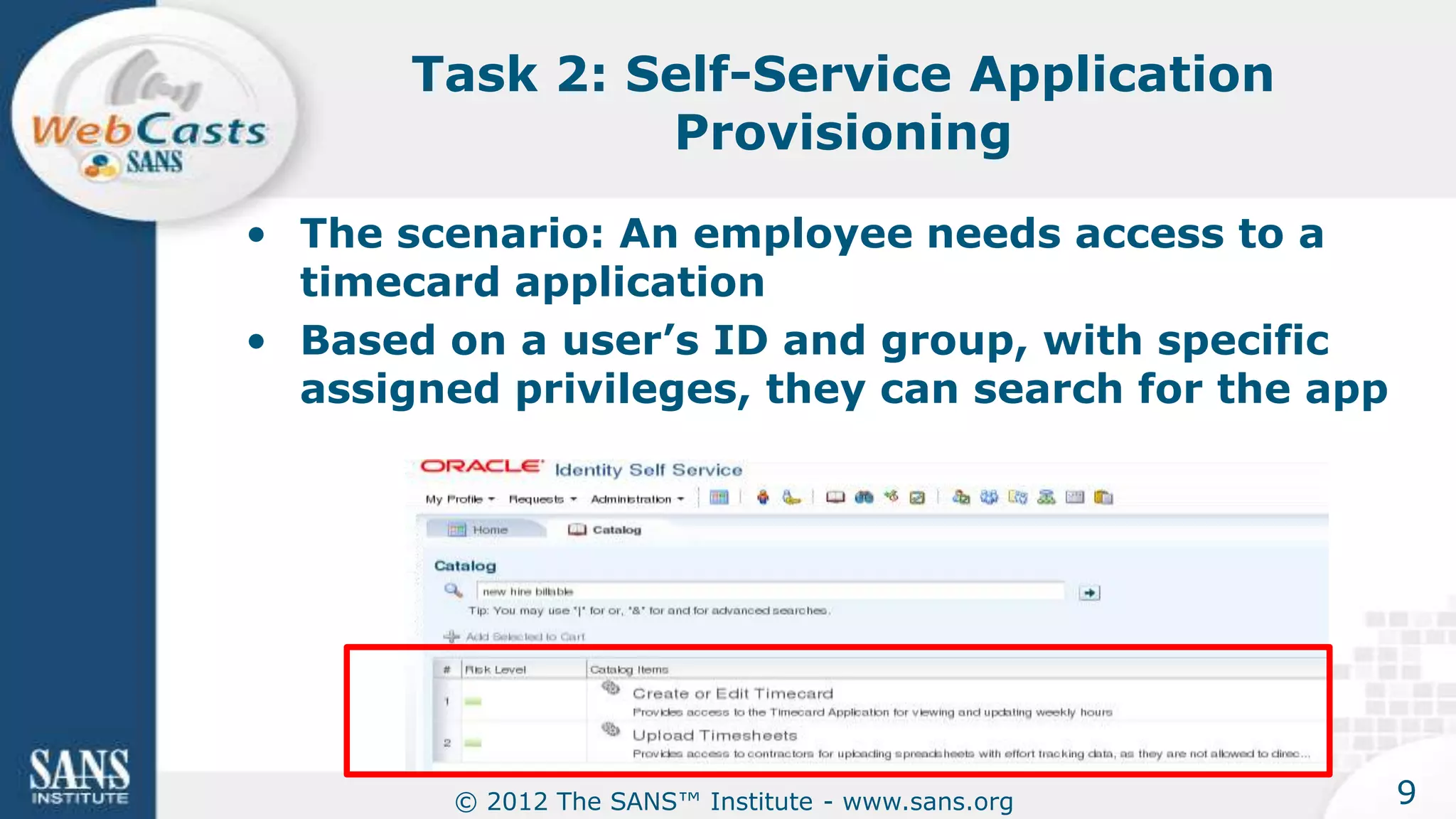
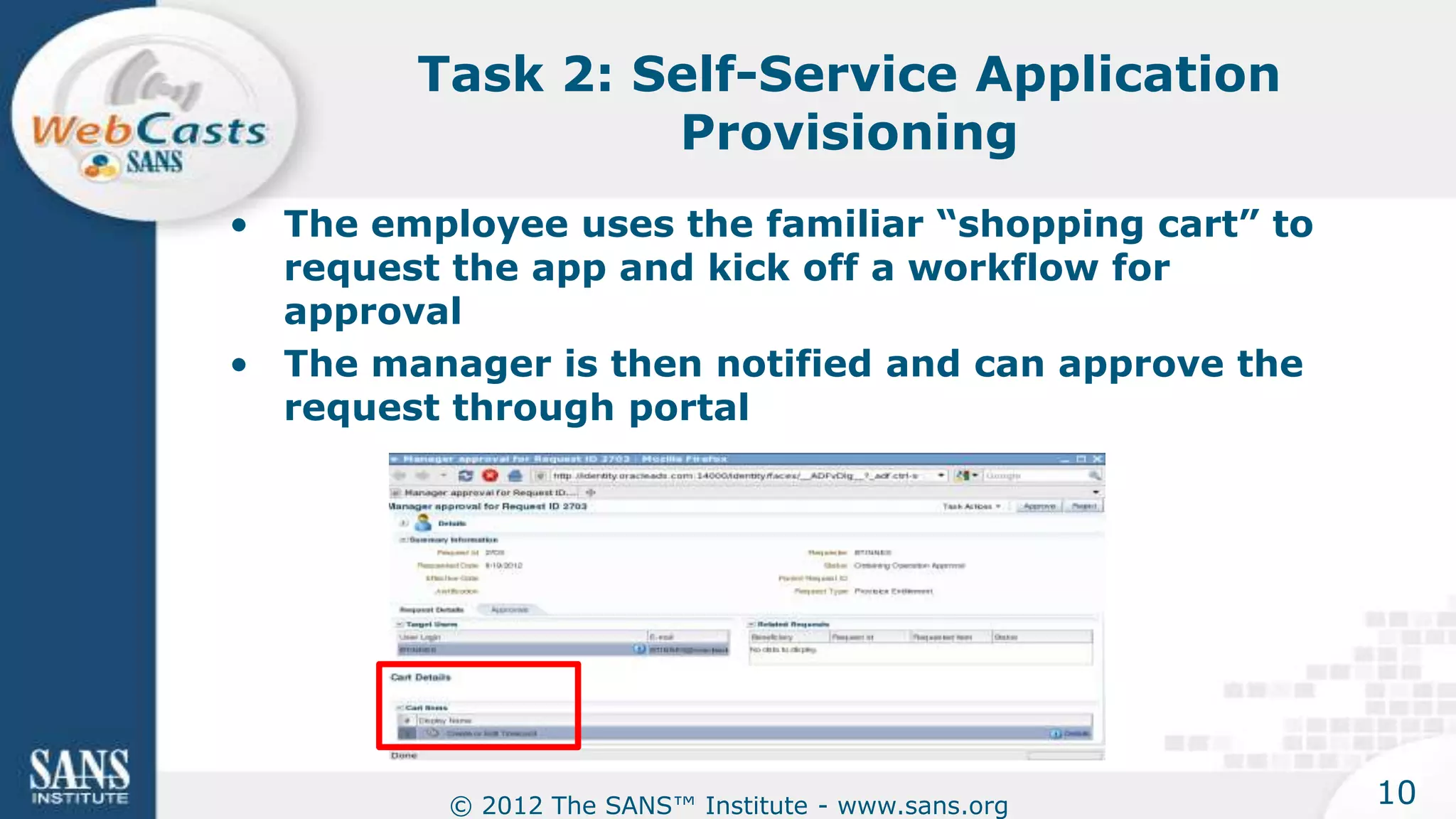
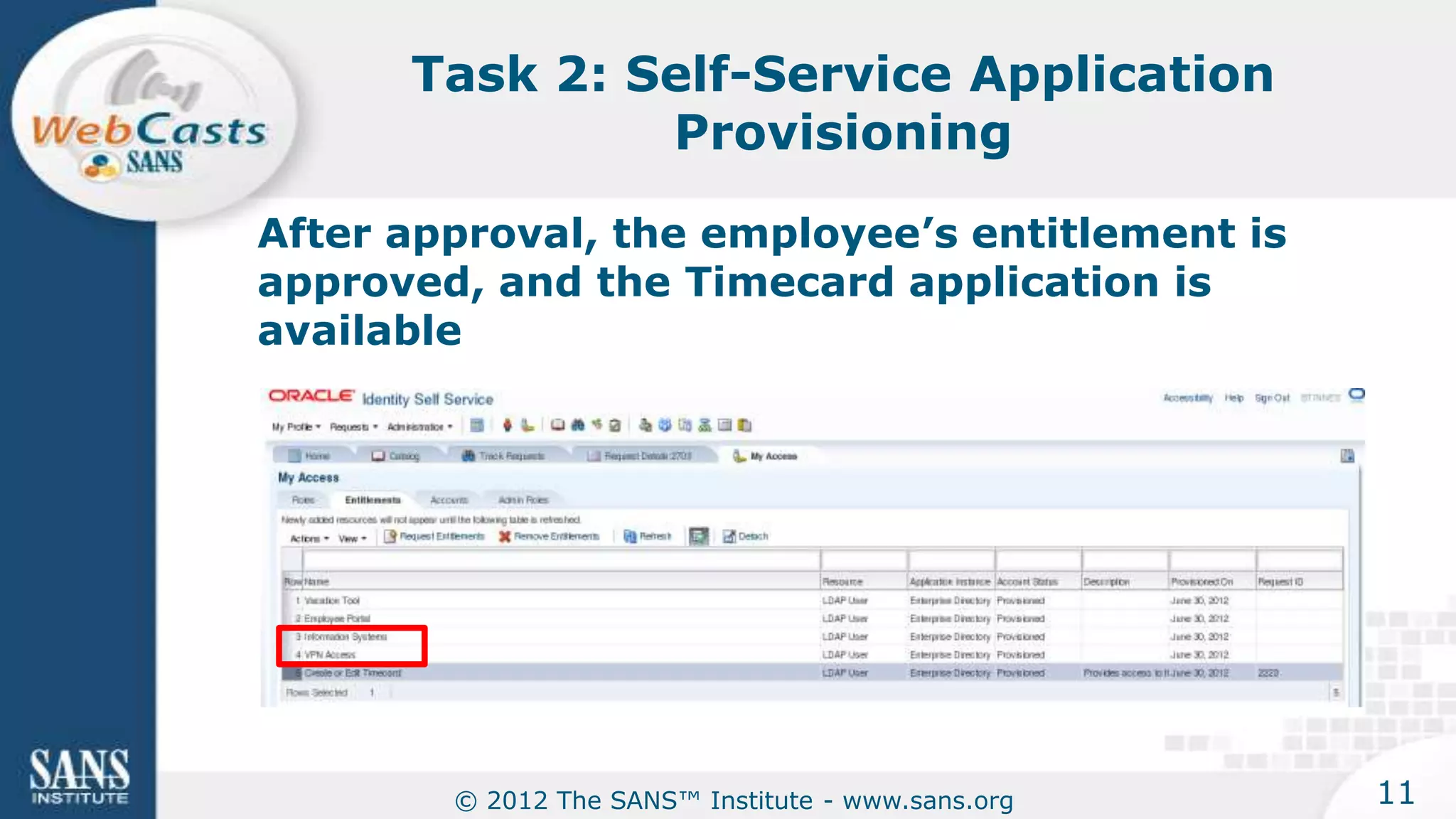
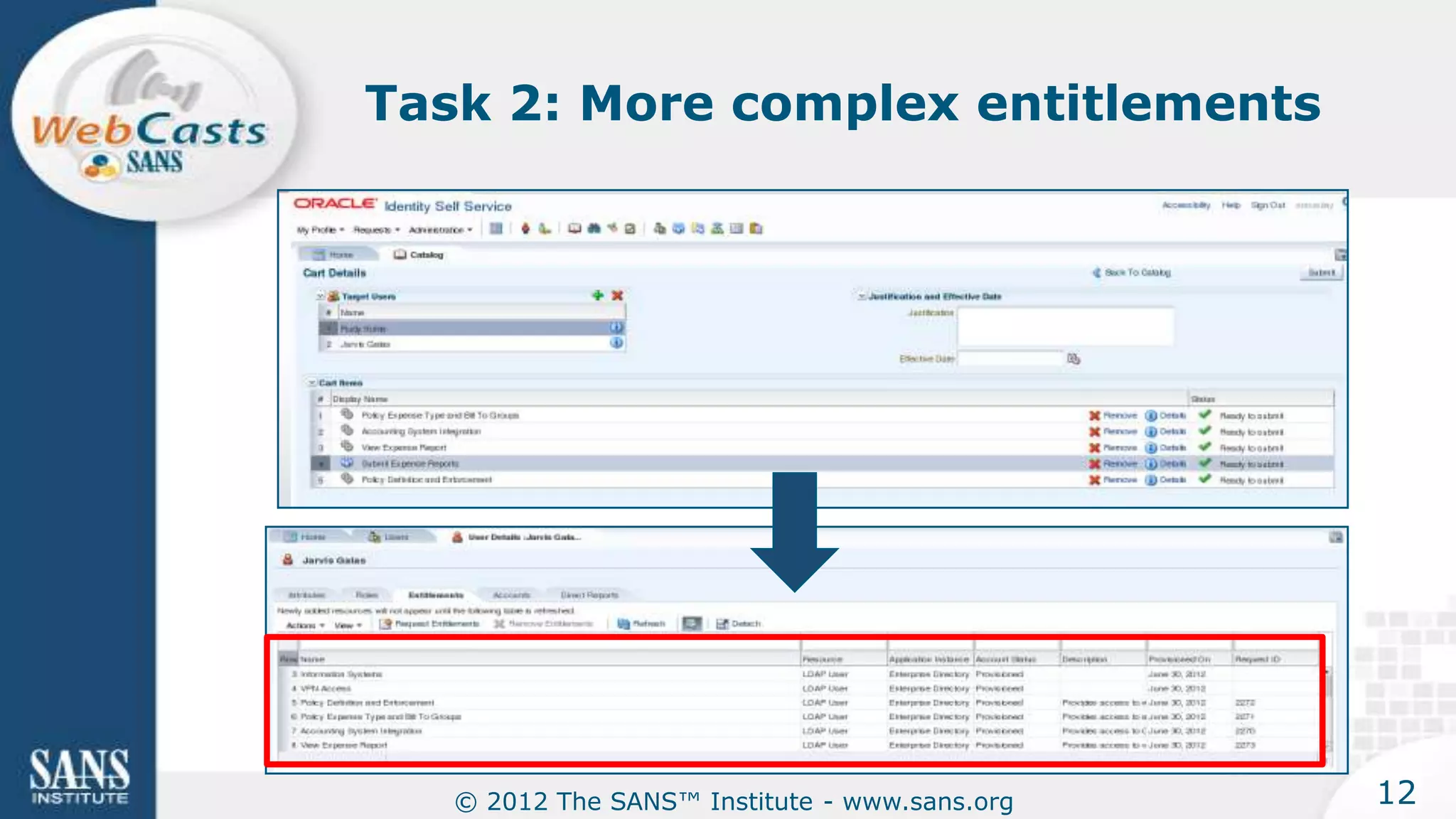
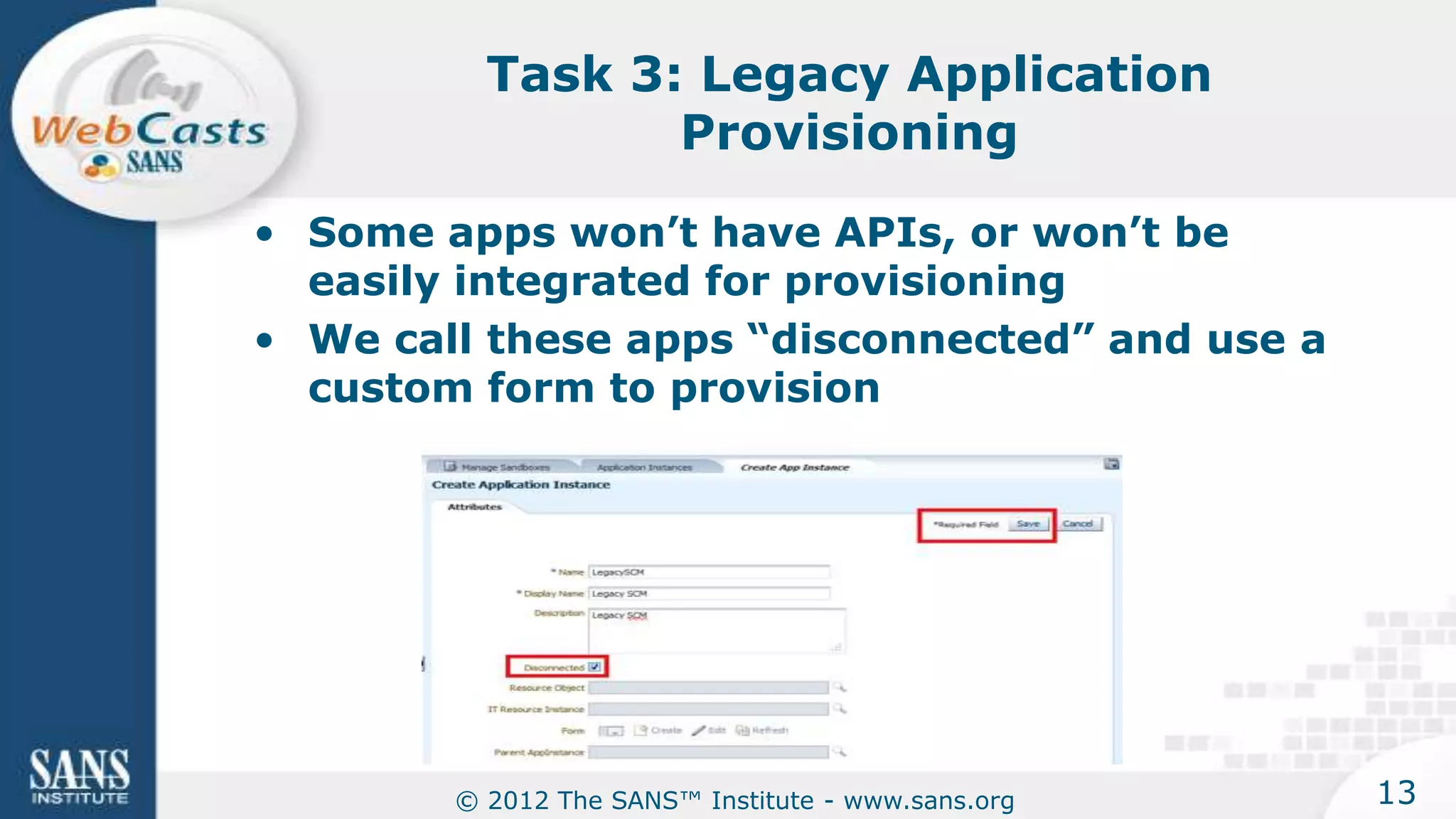
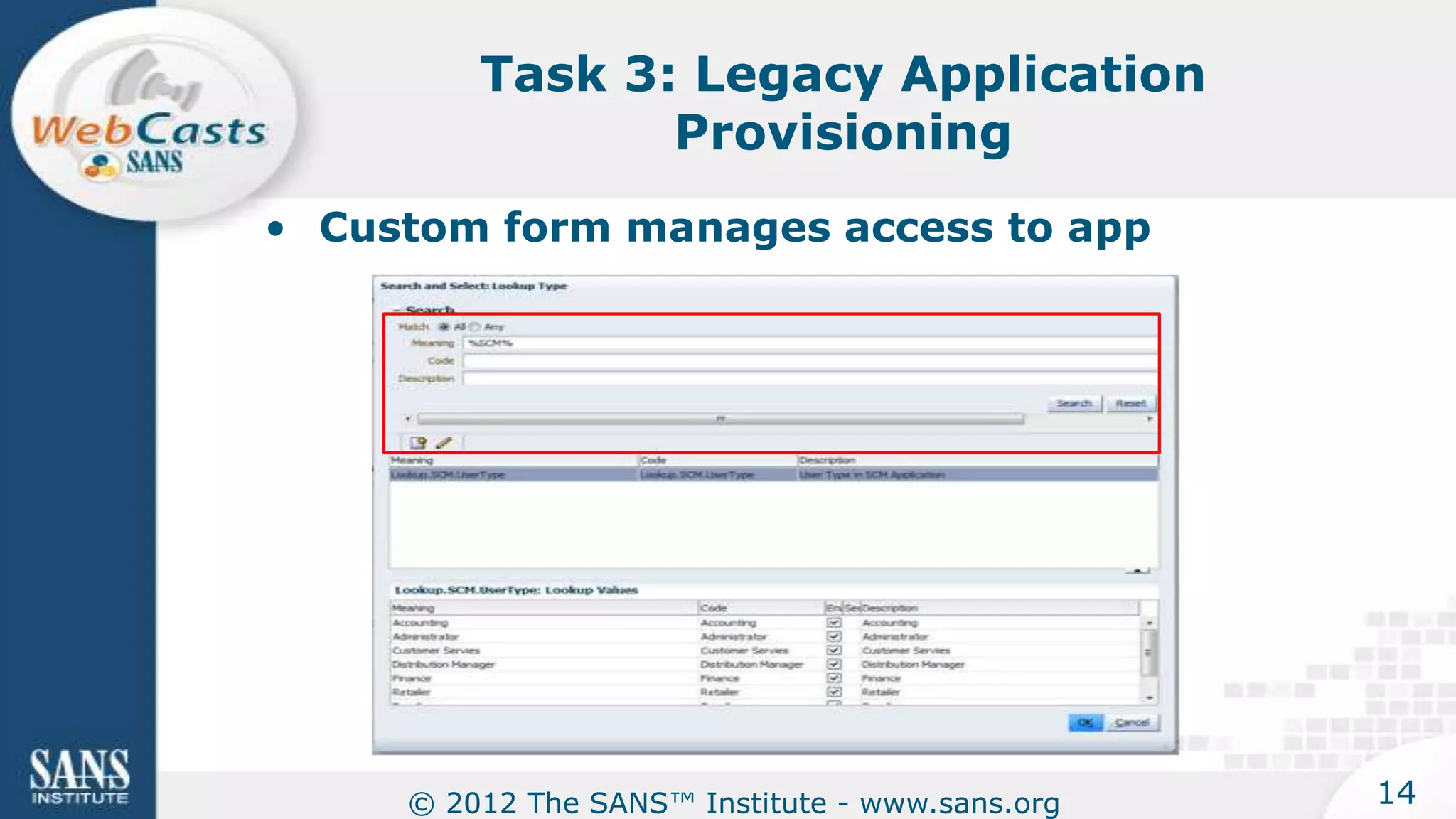
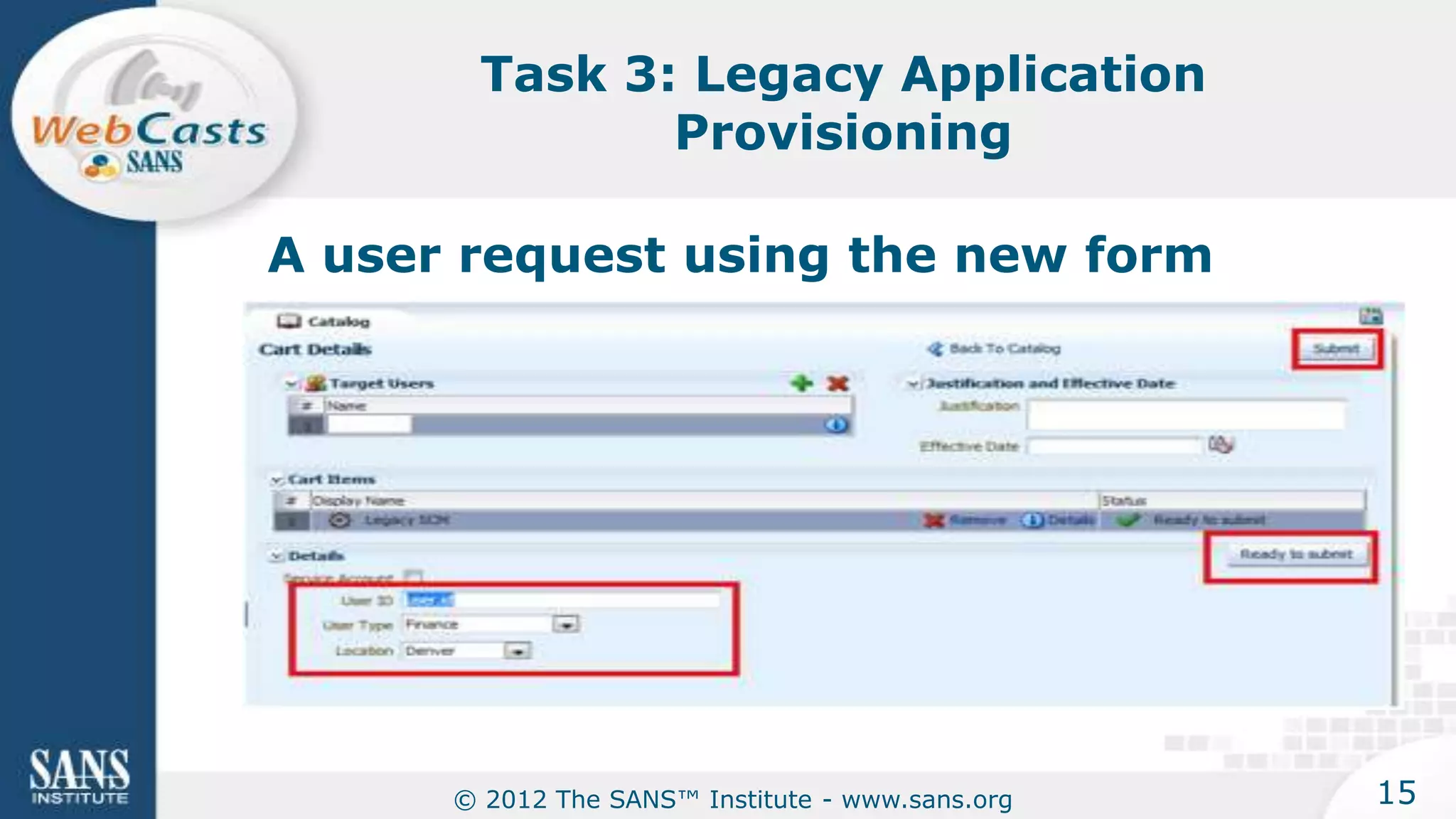
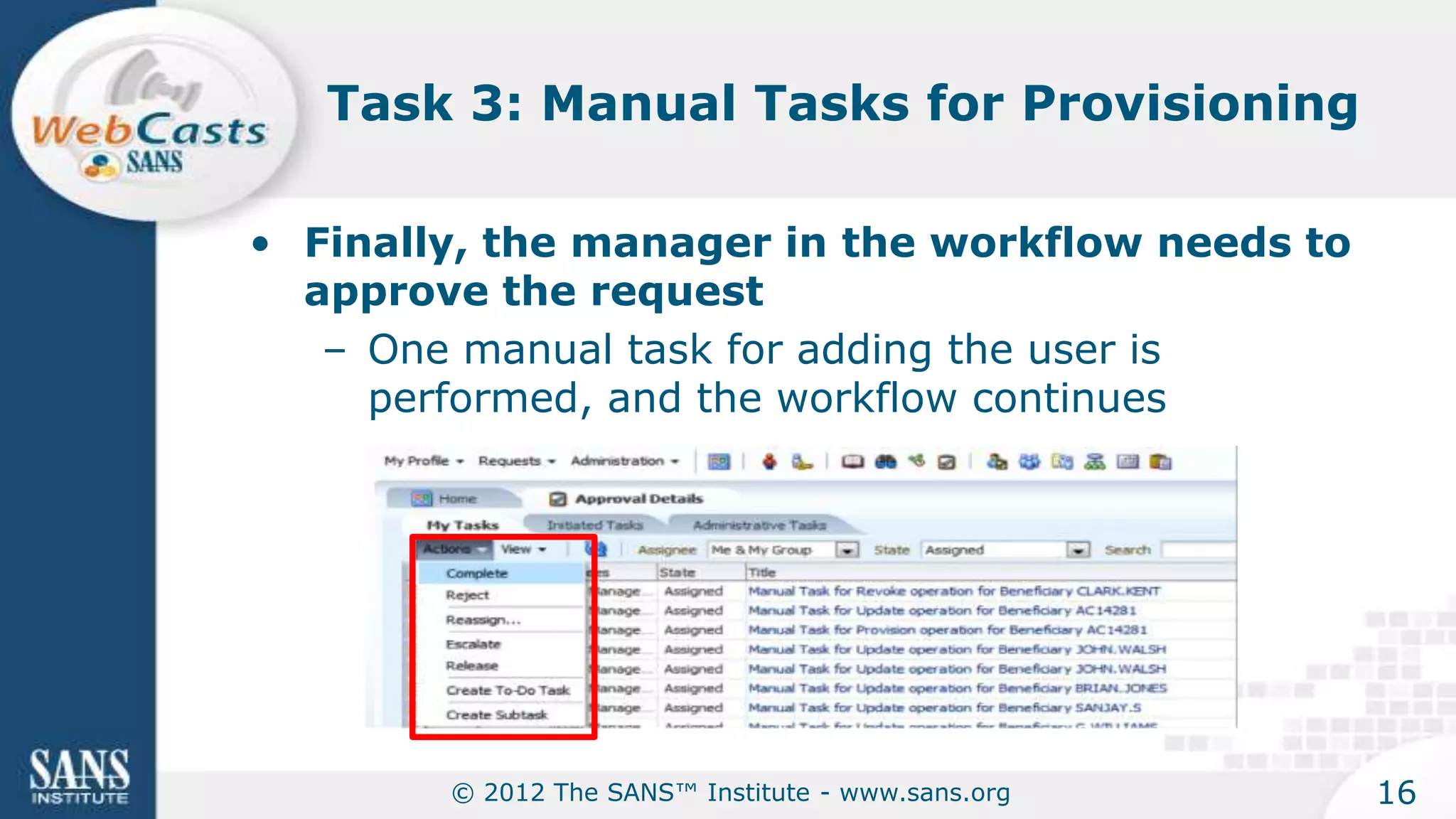
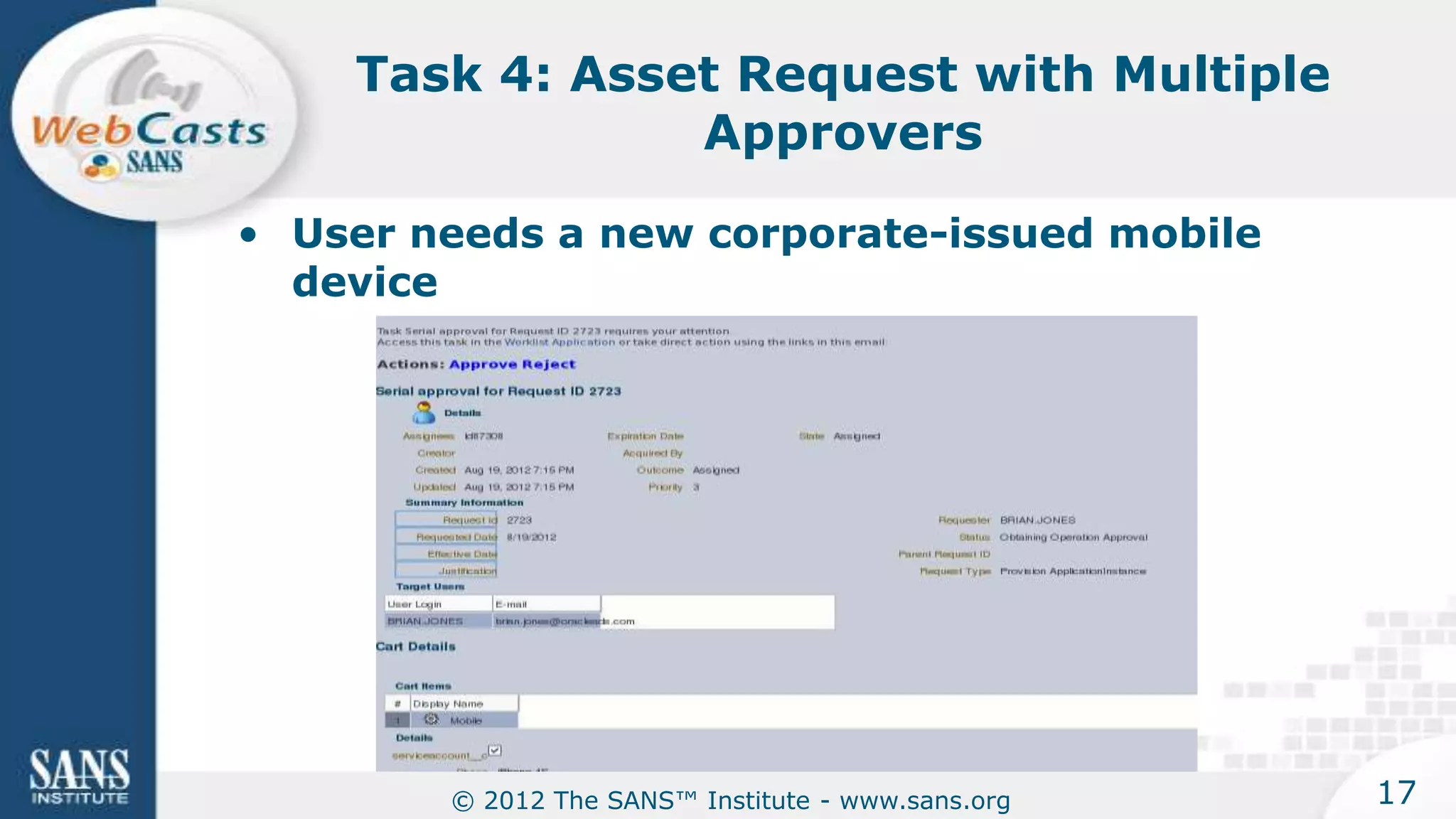
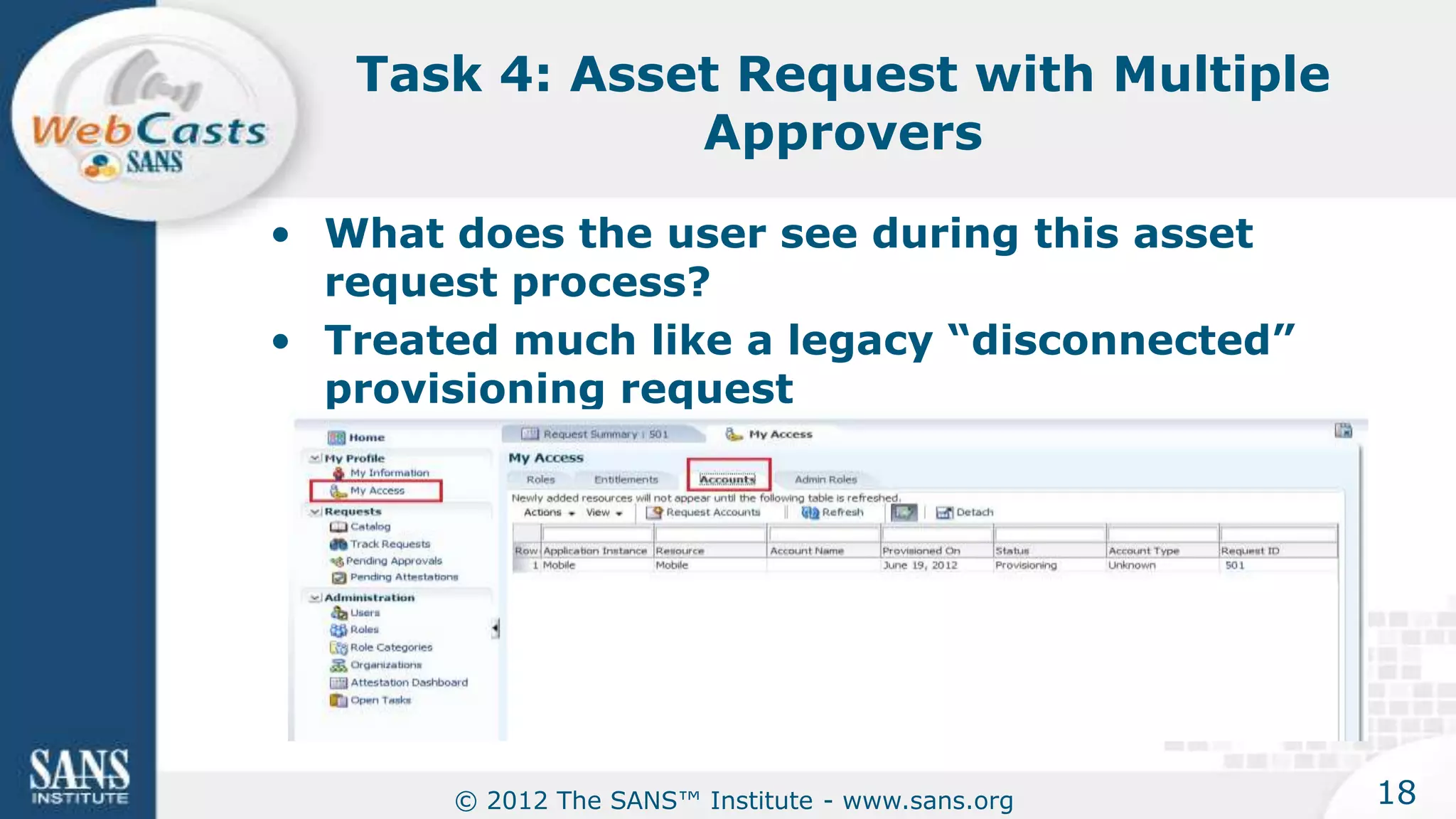
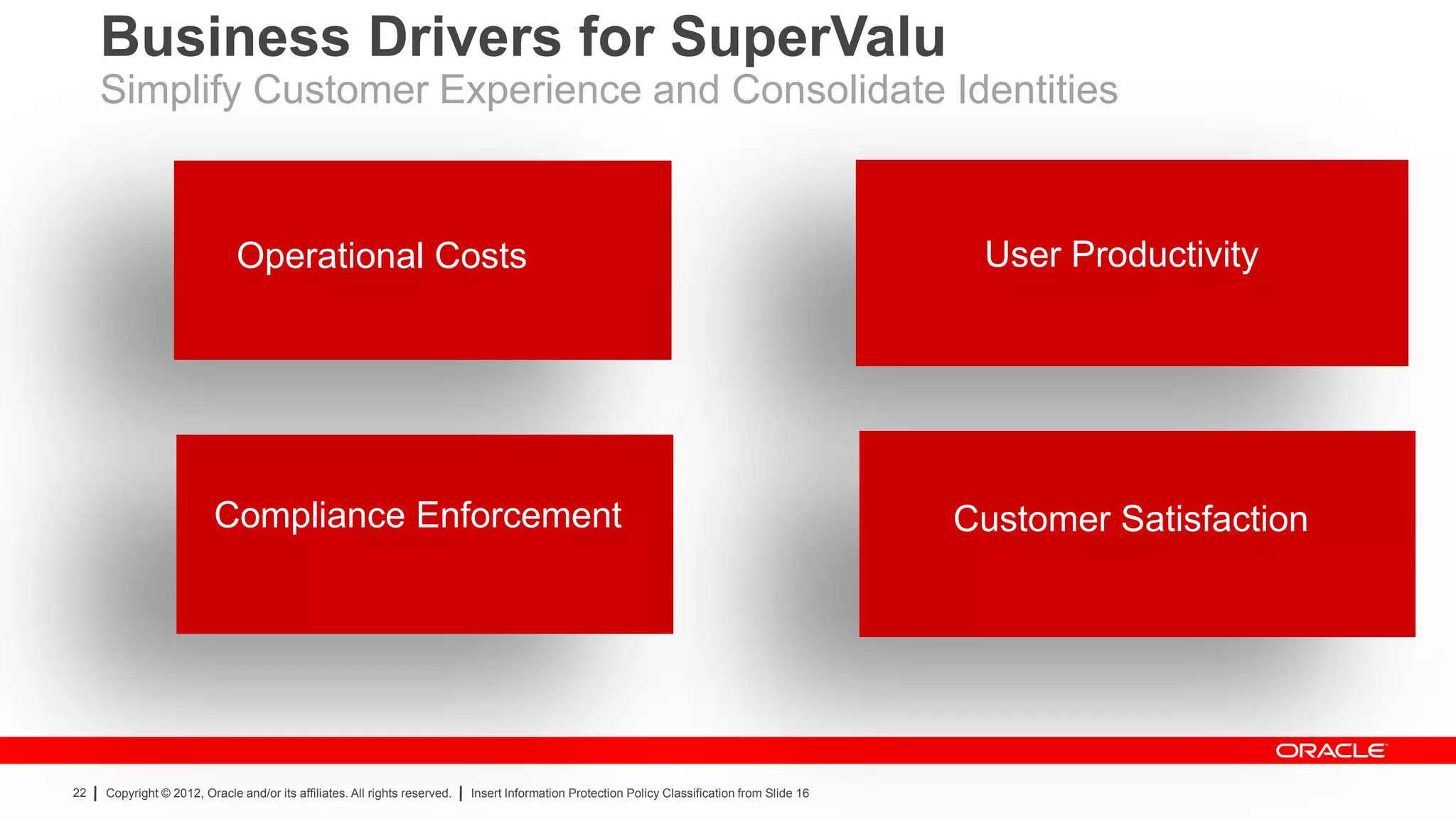
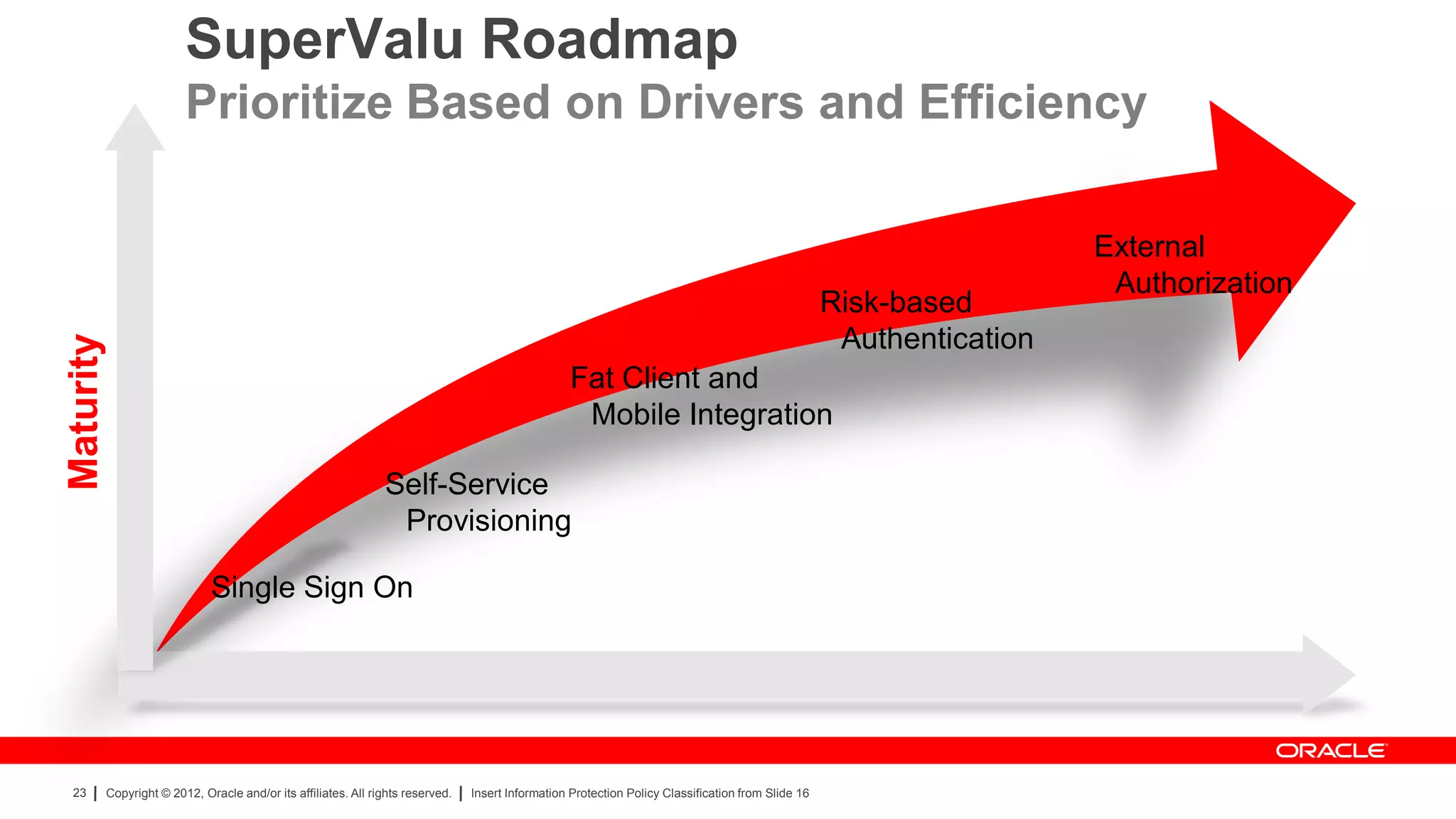
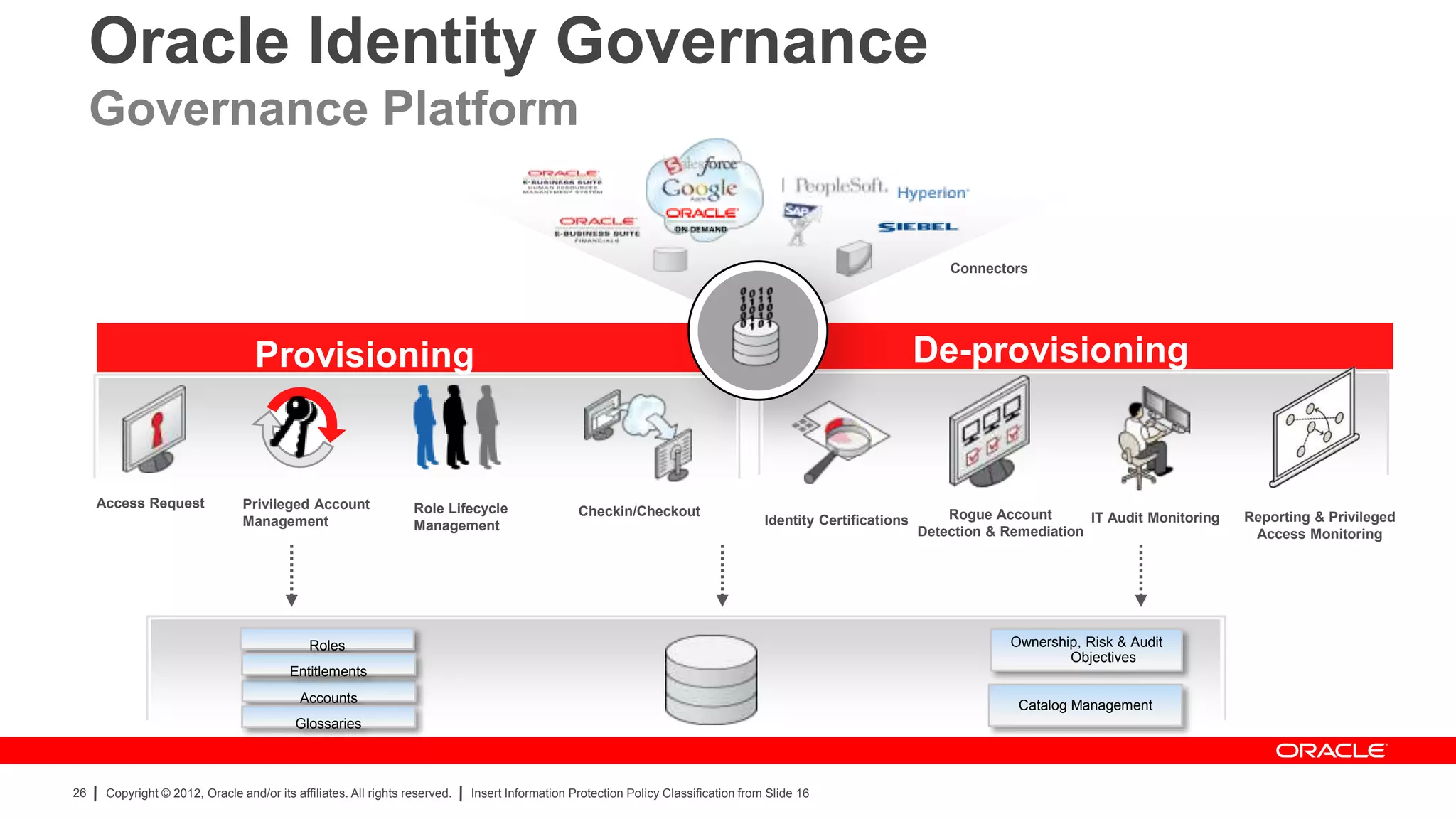
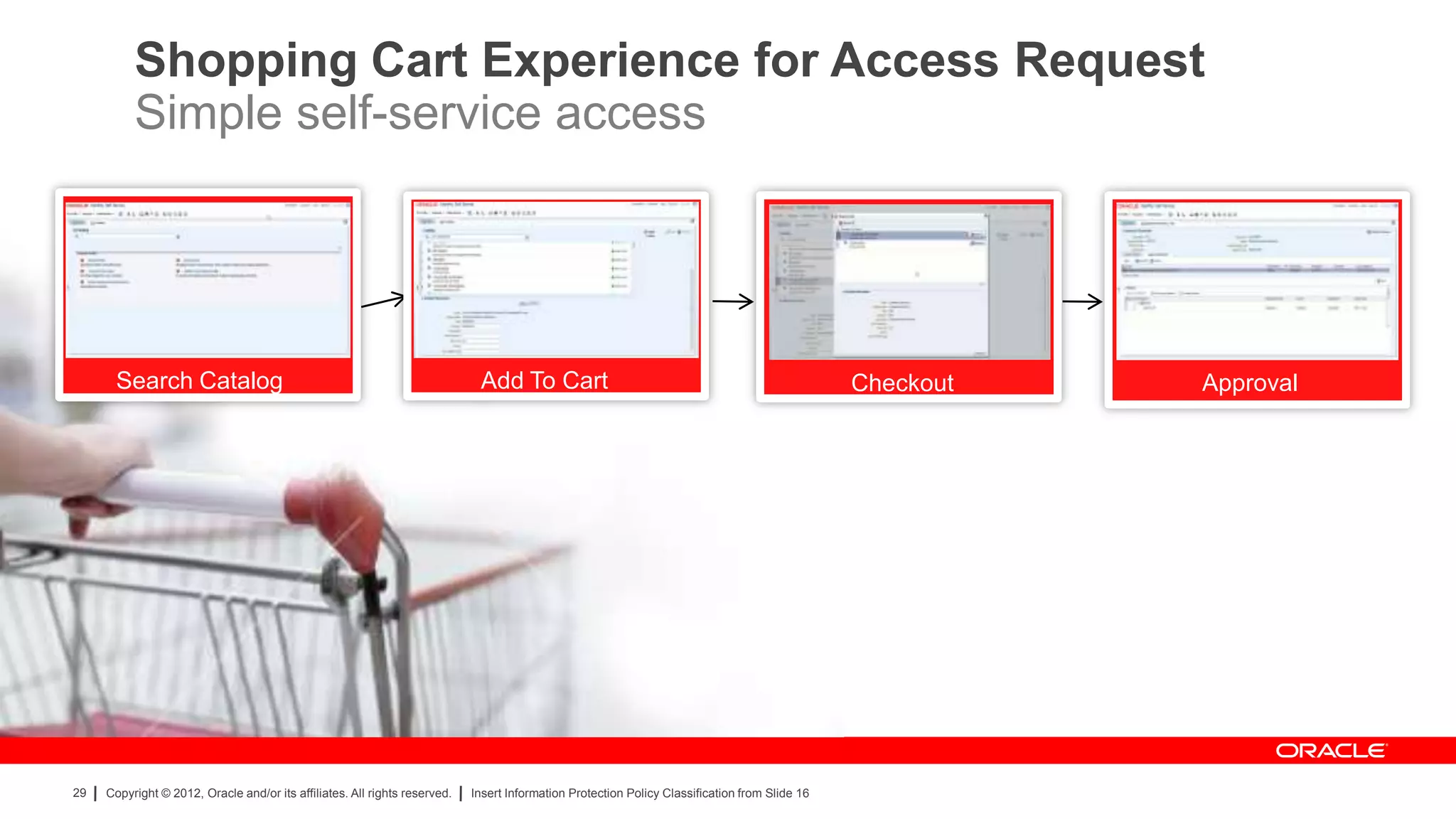
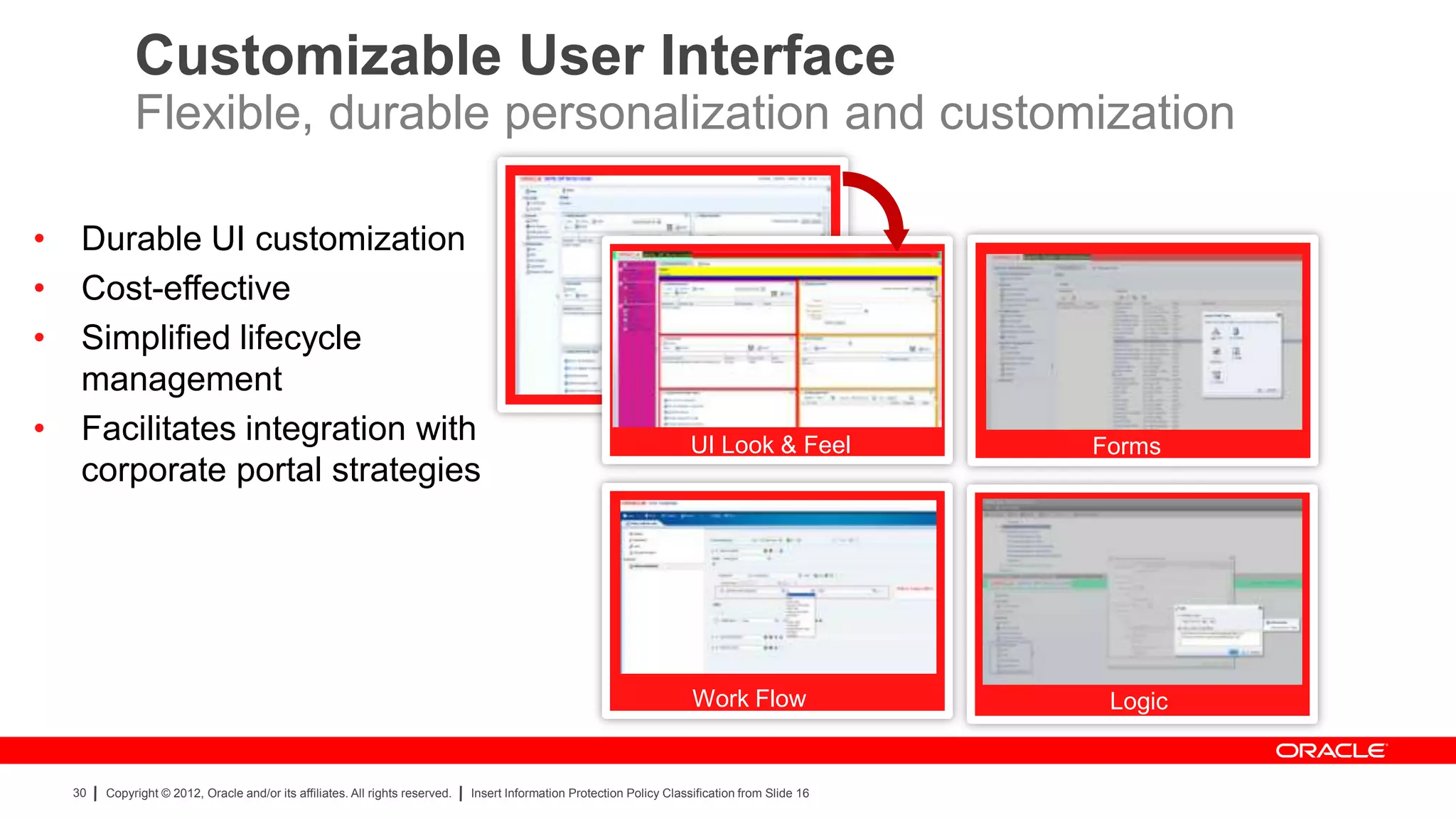
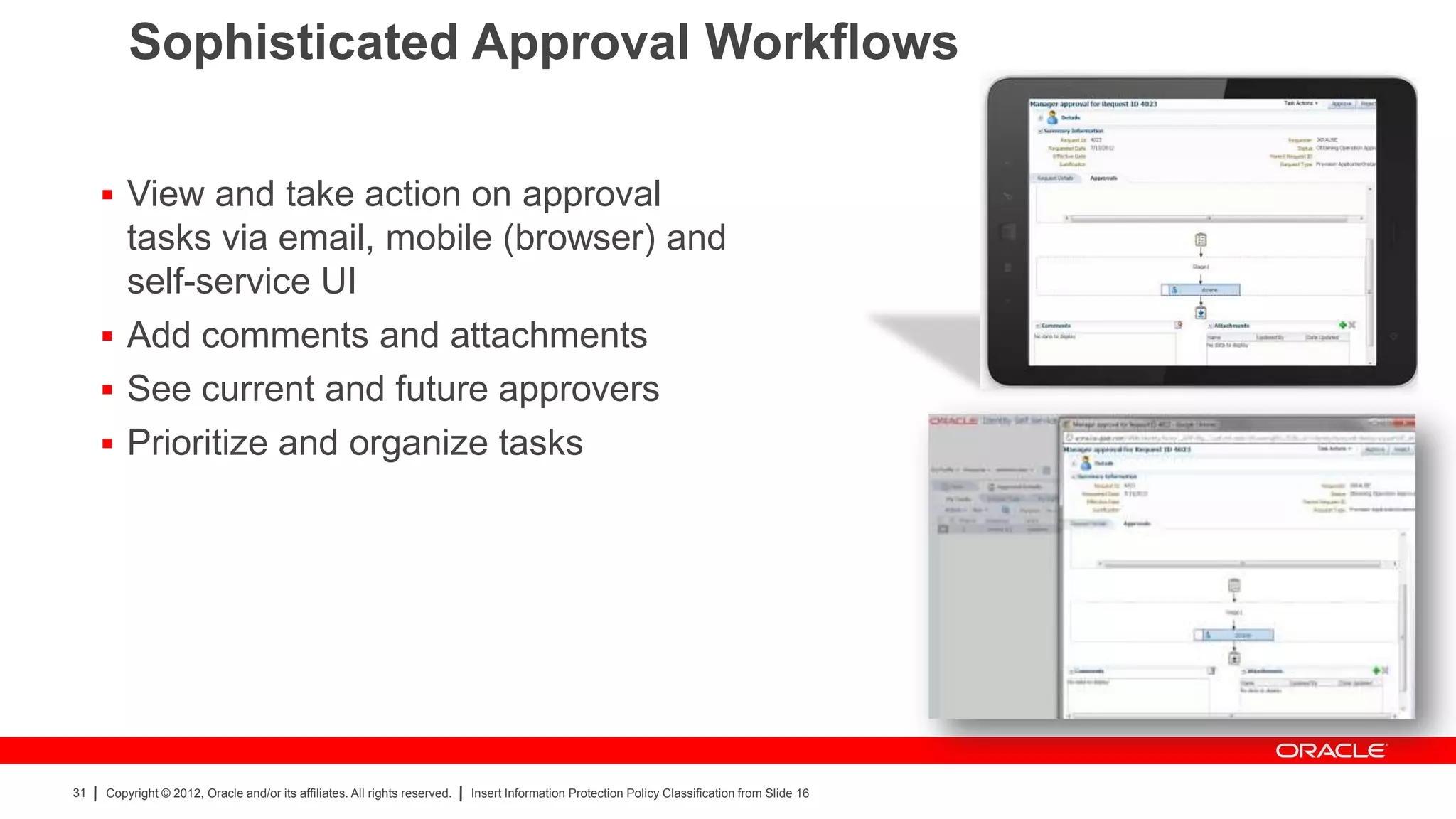
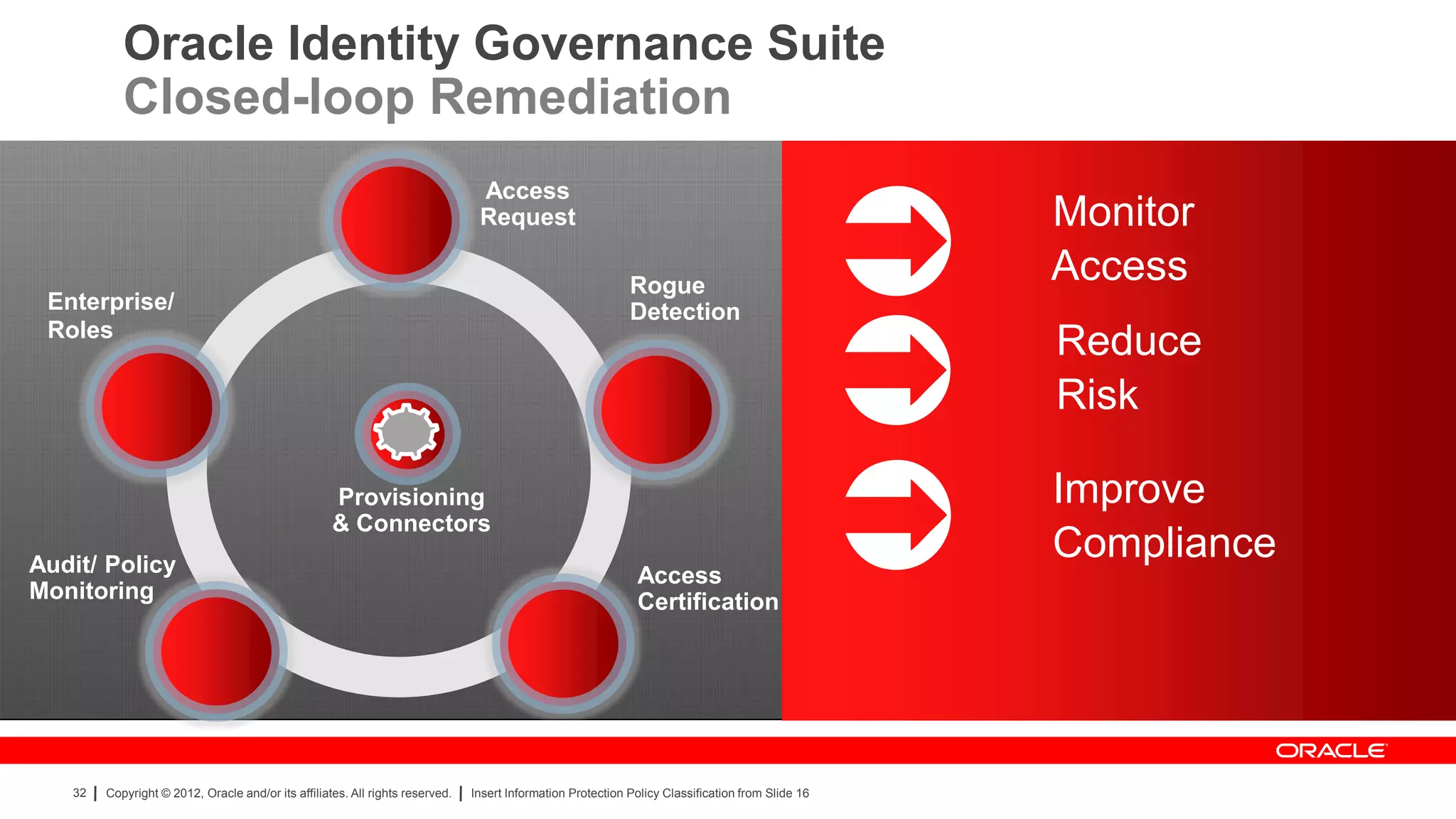
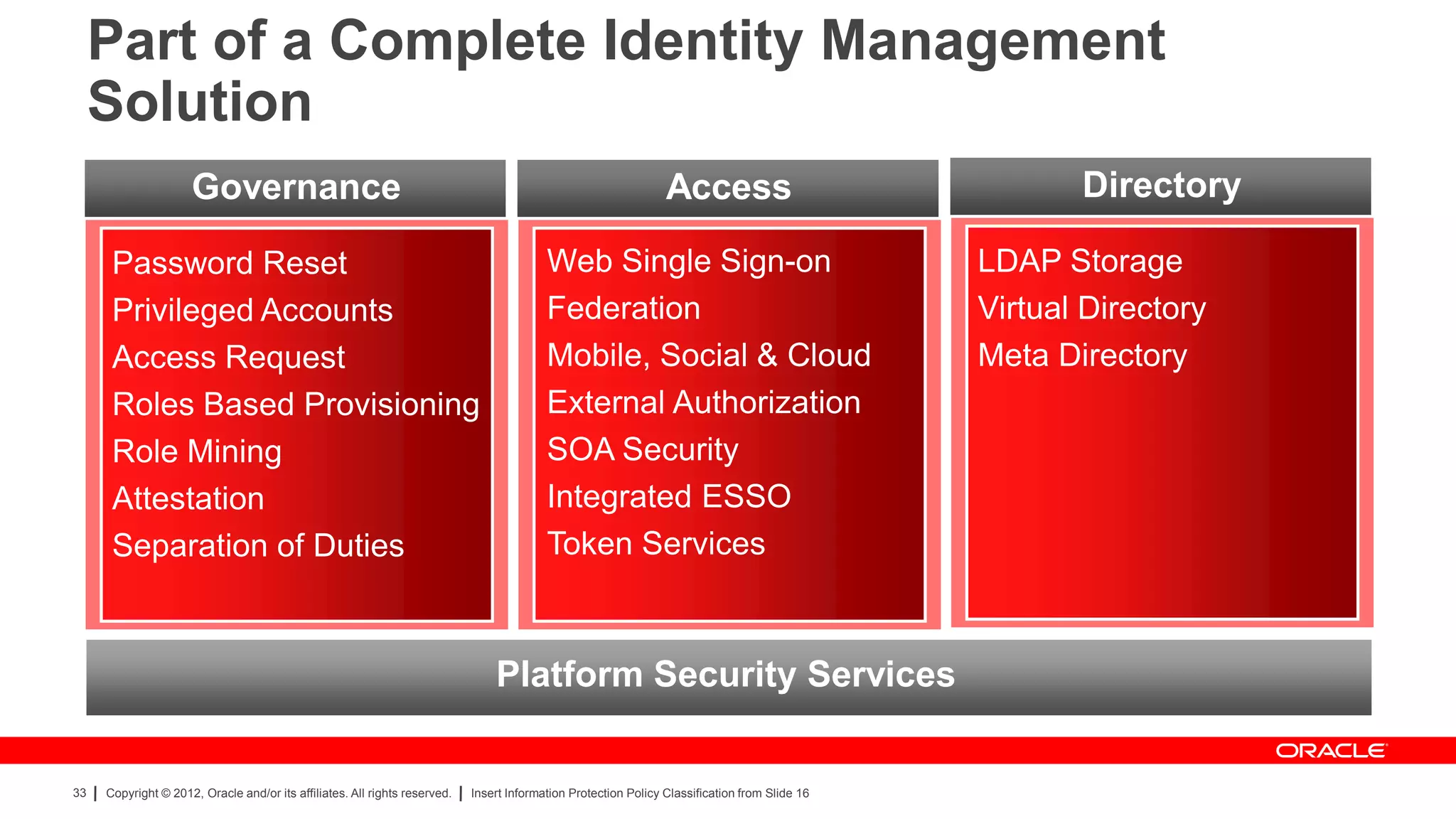
The document provides an overview of a SANS Institute product review of Oracle Identity Manager. It summarizes the review of Oracle Identity Manager 11gR2, which focused on personalizing the user interface, provisioning entitlements based on use cases, creating self-service permissions and workflows, an asset request workflow involving multiple approvers, and provisioning to mobile devices. The review found that Oracle Identity Manager 11gR2 simplified complexities normally associated with identity and access management self-service tools by automating workflows, provisioning to legacy applications without new coding, and incorporating familiar features like shopping carts. It also provided customer perspectives from SuperValu on their identity management roadmap and key learning experiences.