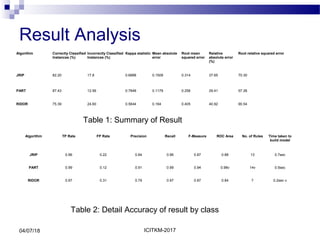
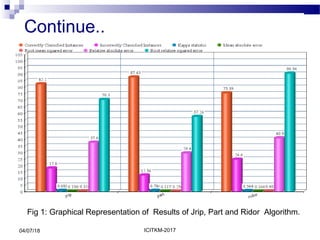
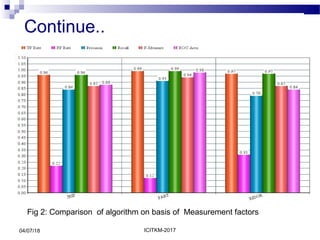
The document presents a study on the detection of malicious executables using rule-based classification algorithms JRip, PART, and Ridor, focusing on their accuracy in classifying threats from a dataset of malware. The results indicate that PART performed the best in terms of rule generation and classification accuracy, followed by JRip and Ridor. Future work includes extending the dataset and improving the classification model to predict the severity of threats more effectively.







![Resources
C. developers, “Cuckoo sandbox - open source automated malwareanalysis,” 2016.
[Online]. Available: https://media.blackhat.com/us-
13/US-13-Bremer-Mo-Malware-Mo-Problems-Cuckoo-Sandbox-WP.pdf
“Malware Classification Using Filesystem Footprints” George Cabau, Magda Buhu ,
CiprianOpris¸a Bitdefender Technical University of Cluj-Napoca {gcabau, math,
coprisa} @bitdefender.com 978-1-4673-8692-0/16/$31.00 c 2016 IEEE.
J. Stewart, "Behavioural malware analysis using Sandnets," Computer Fraud &
Security, vol. 2006, no.Issue, pp. 4-6, December 2006.
Hengli Zhao, Ming Xu, Ning Zhong, Jingjing Yao, and Q. Ho, "Malicious Executables
Classification
Based on Behavioral Factor Analysis," presented at the 2010 International
Conference on e-Education, e-Business, e-Management and e-Learning, Sanya,
China, 2010
“A Comparative Study of Classification Techniques for Intrusion Detection”,
HimadriChauhan, Vipin Kumar, SumitPundir and Emmanuel S. Pilli DePARTment of
Computer Science and Engineering Graphic Era University Dehradun India978-0-
7695-5066-4/13 $26.00 © 2013 IEEE DOI 10.1109/ISCBI.2013.16
04/07/18 ICITKM-2017](https://image.slidesharecdn.com/dme-180407170730/85/DETECTION-OF-MALICIOUS-EXECUTABLES-USING-RULE-BASED-CLASSIFICATION-ALGORITHMS-16-320.jpg)
