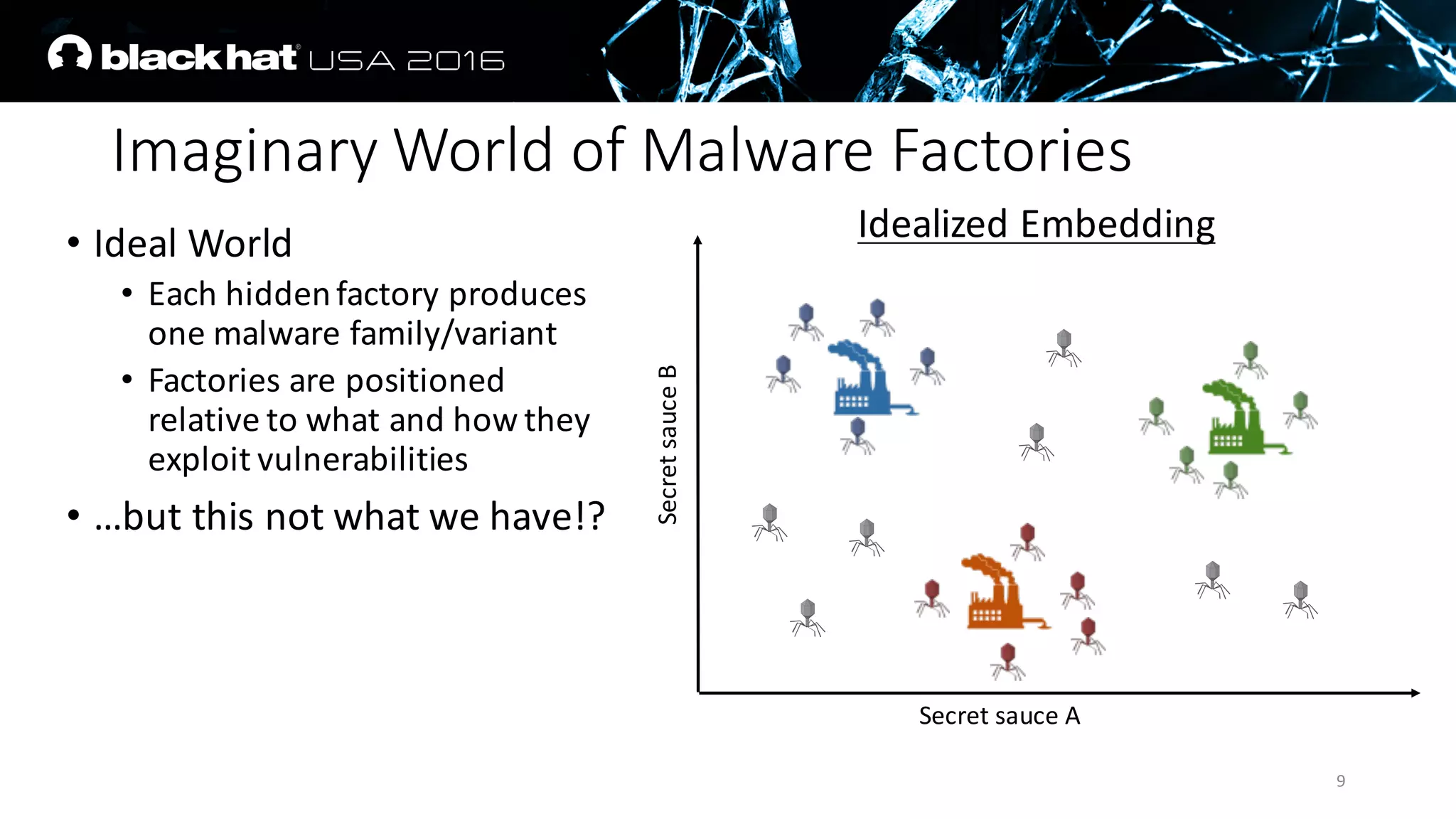
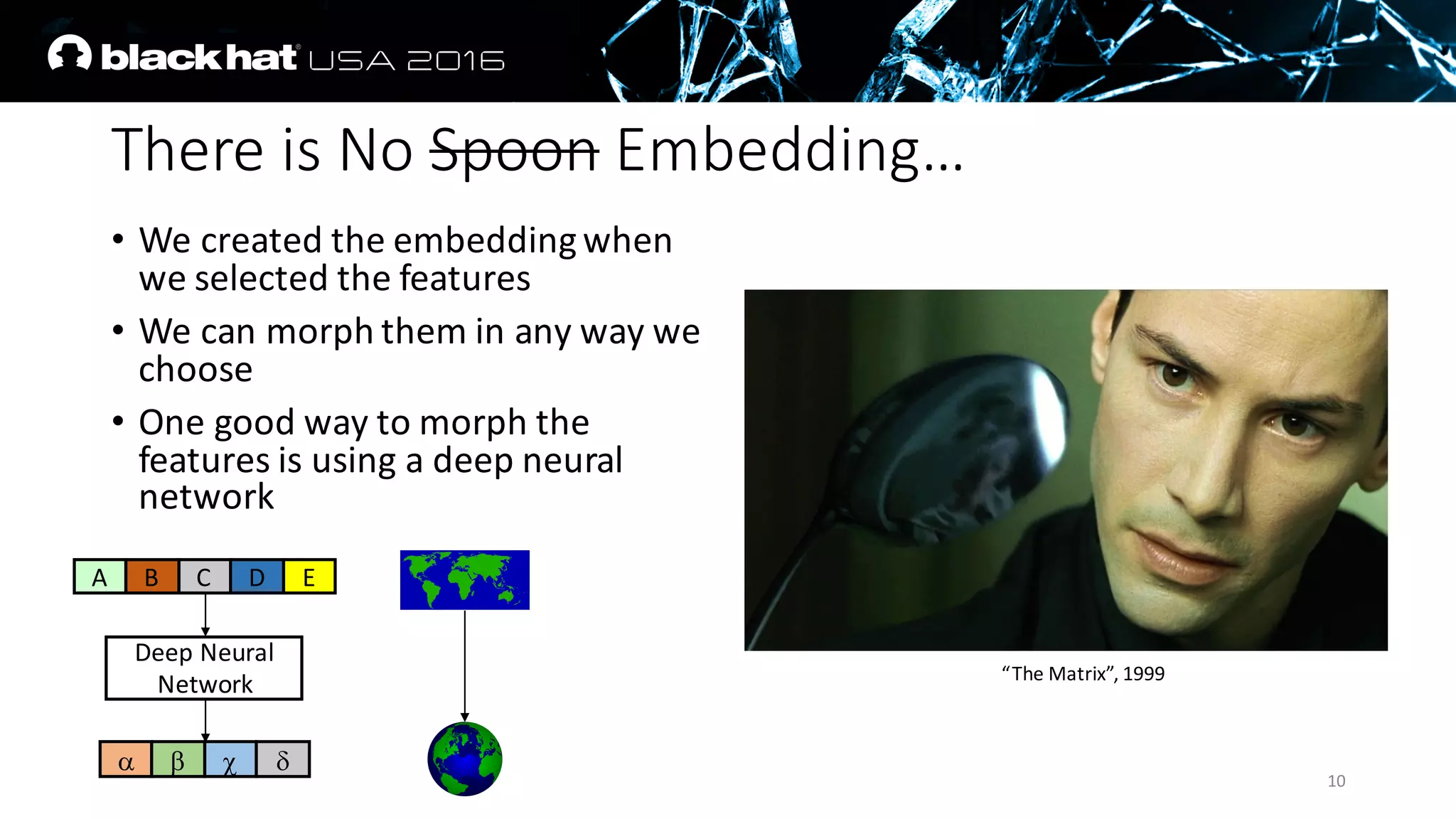
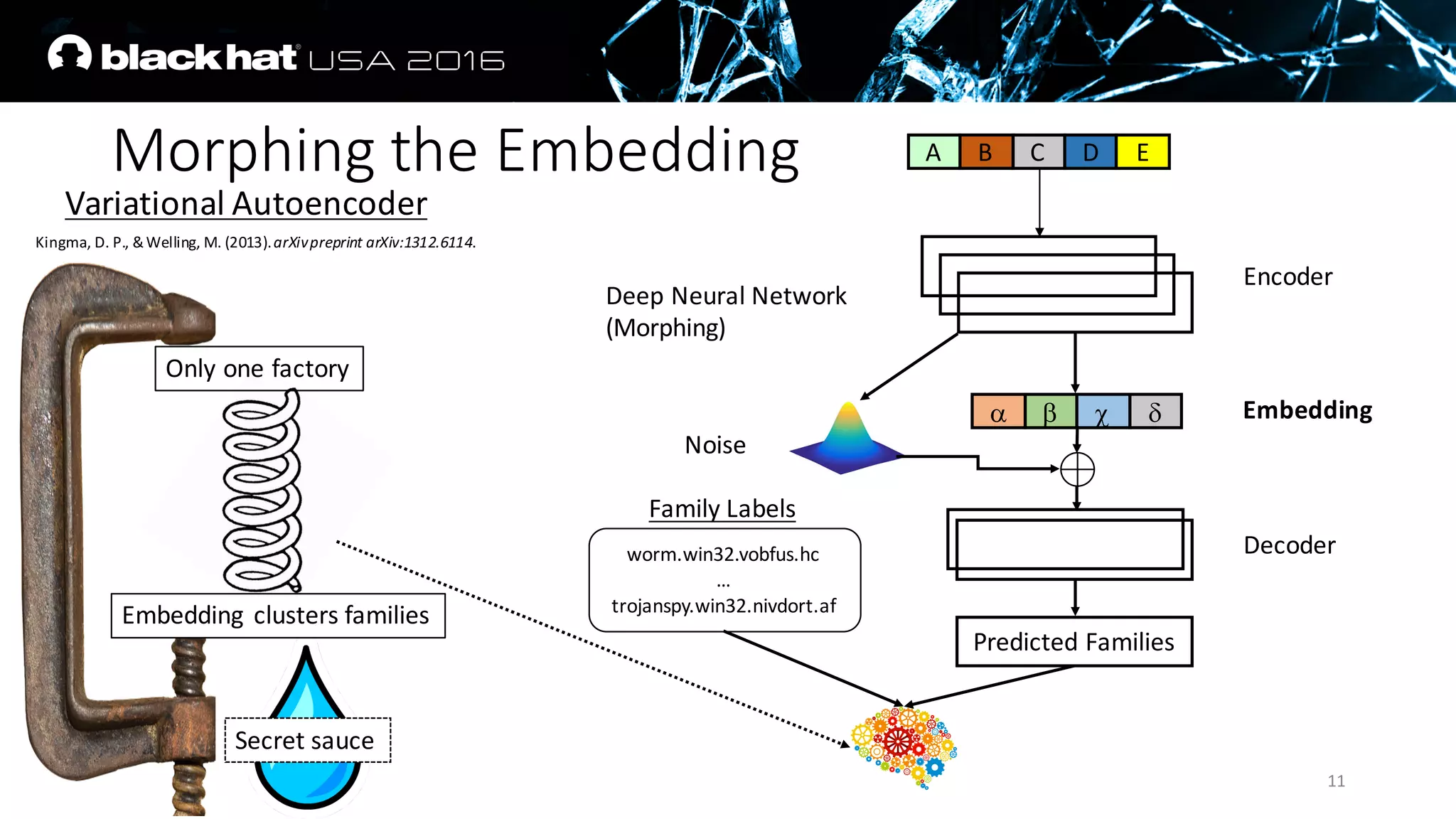
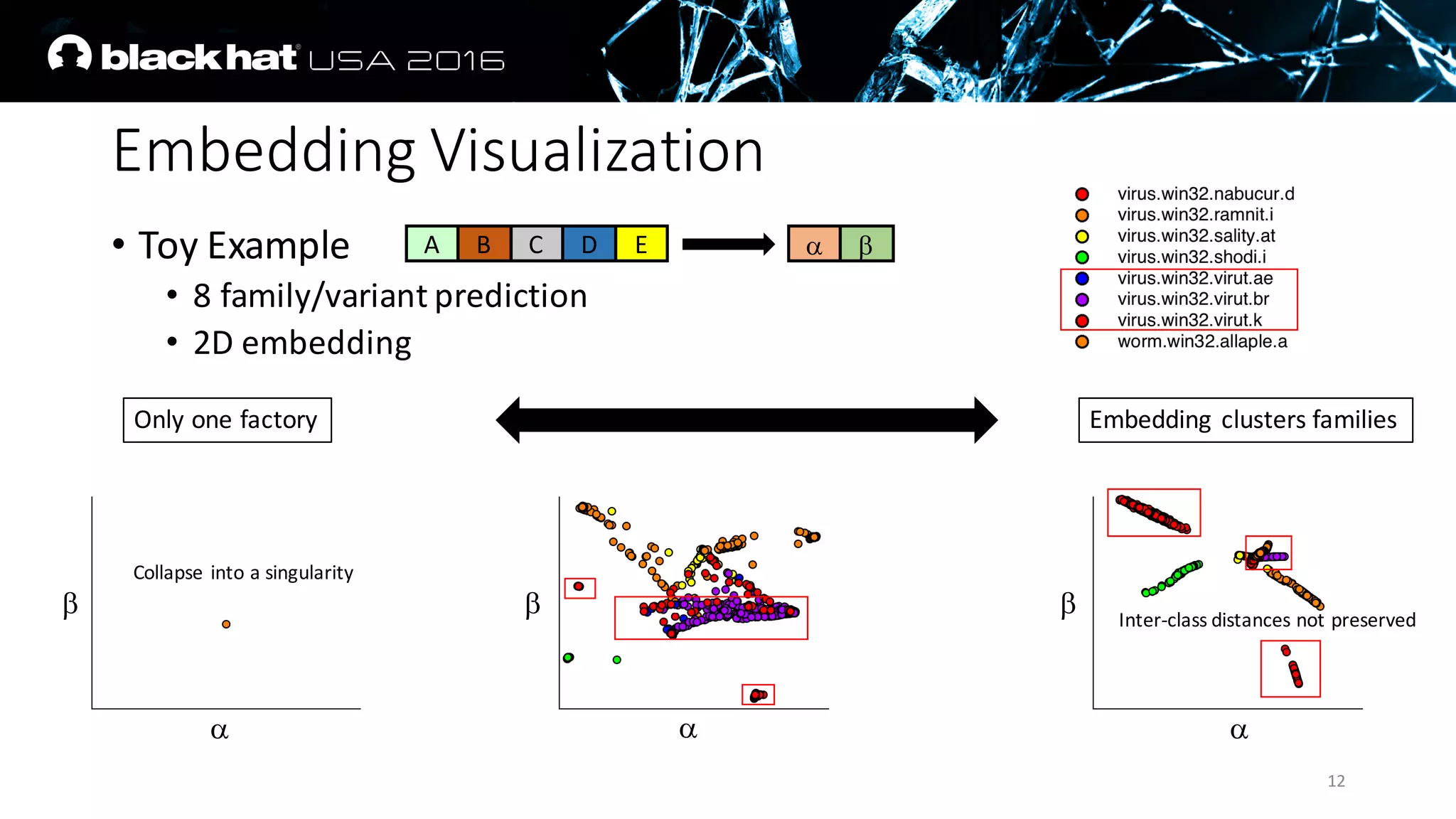
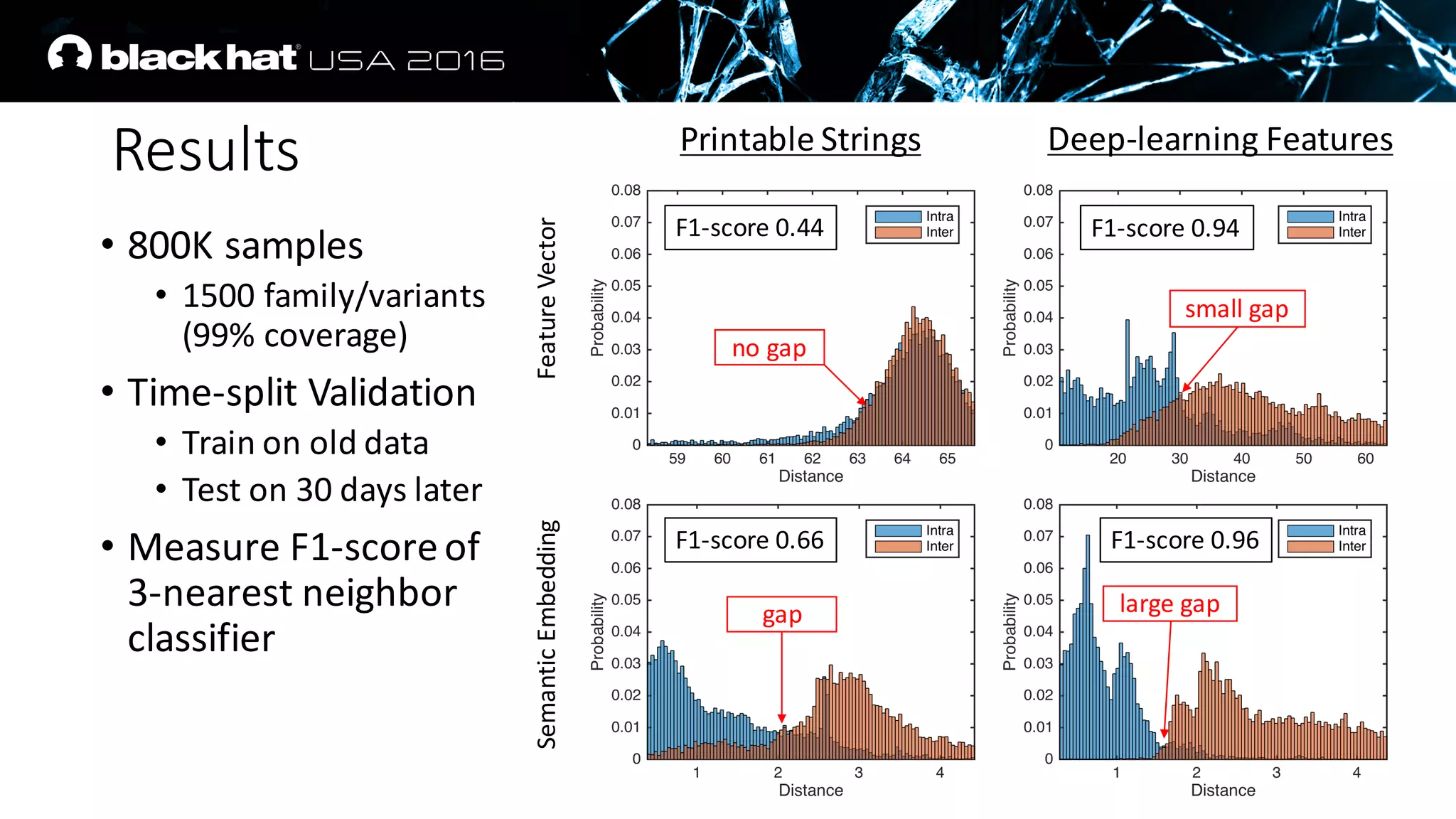
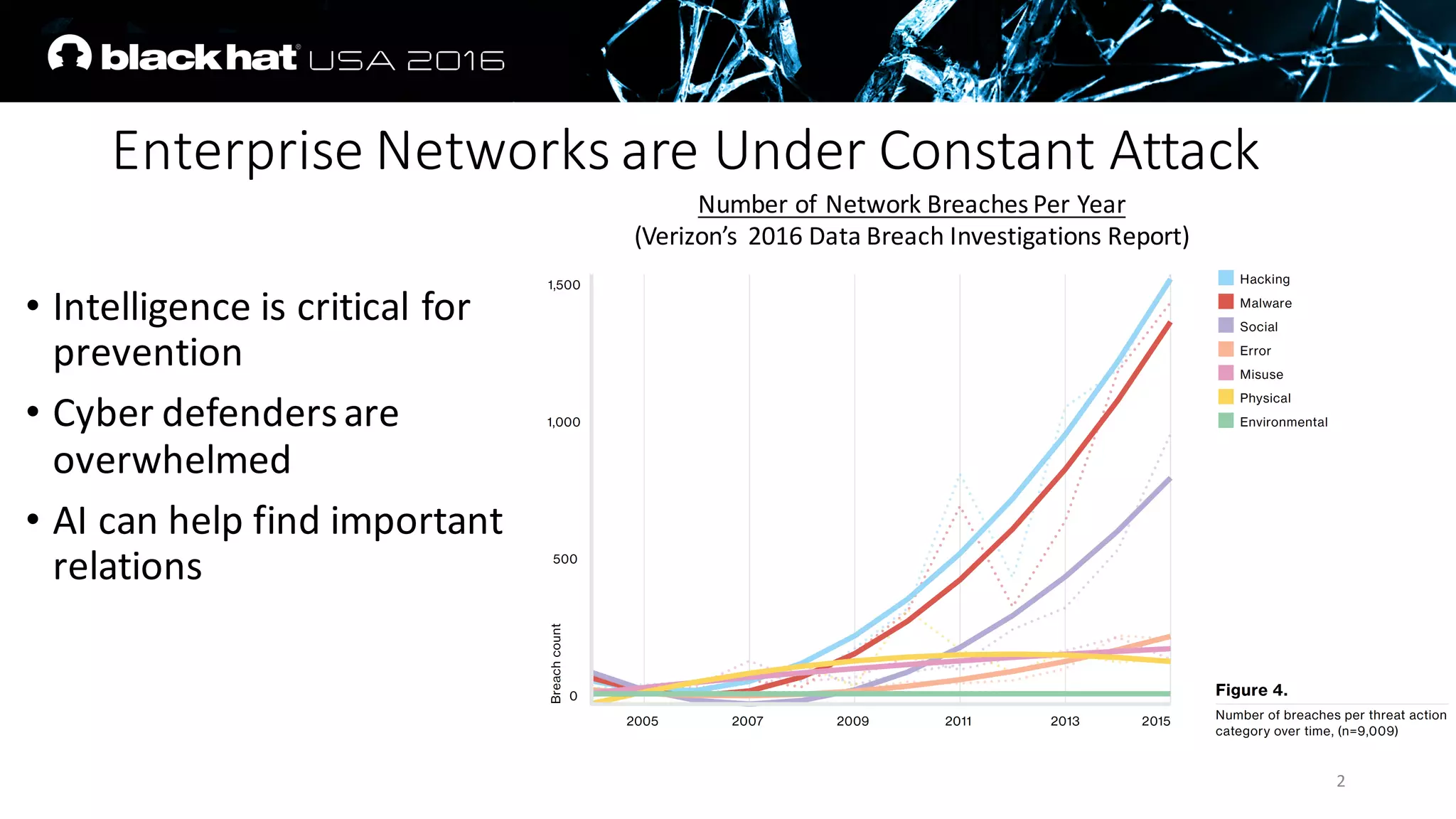
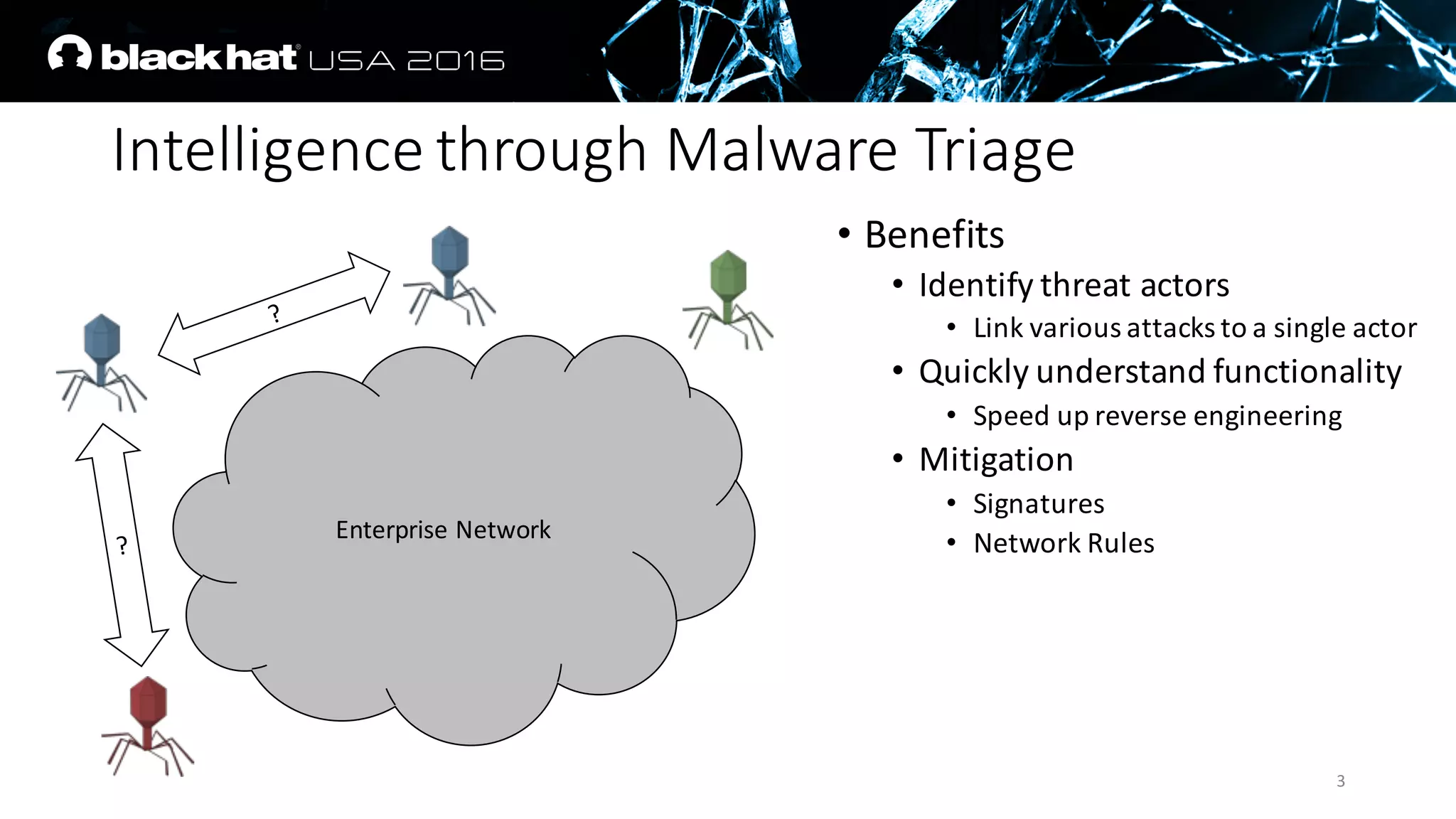
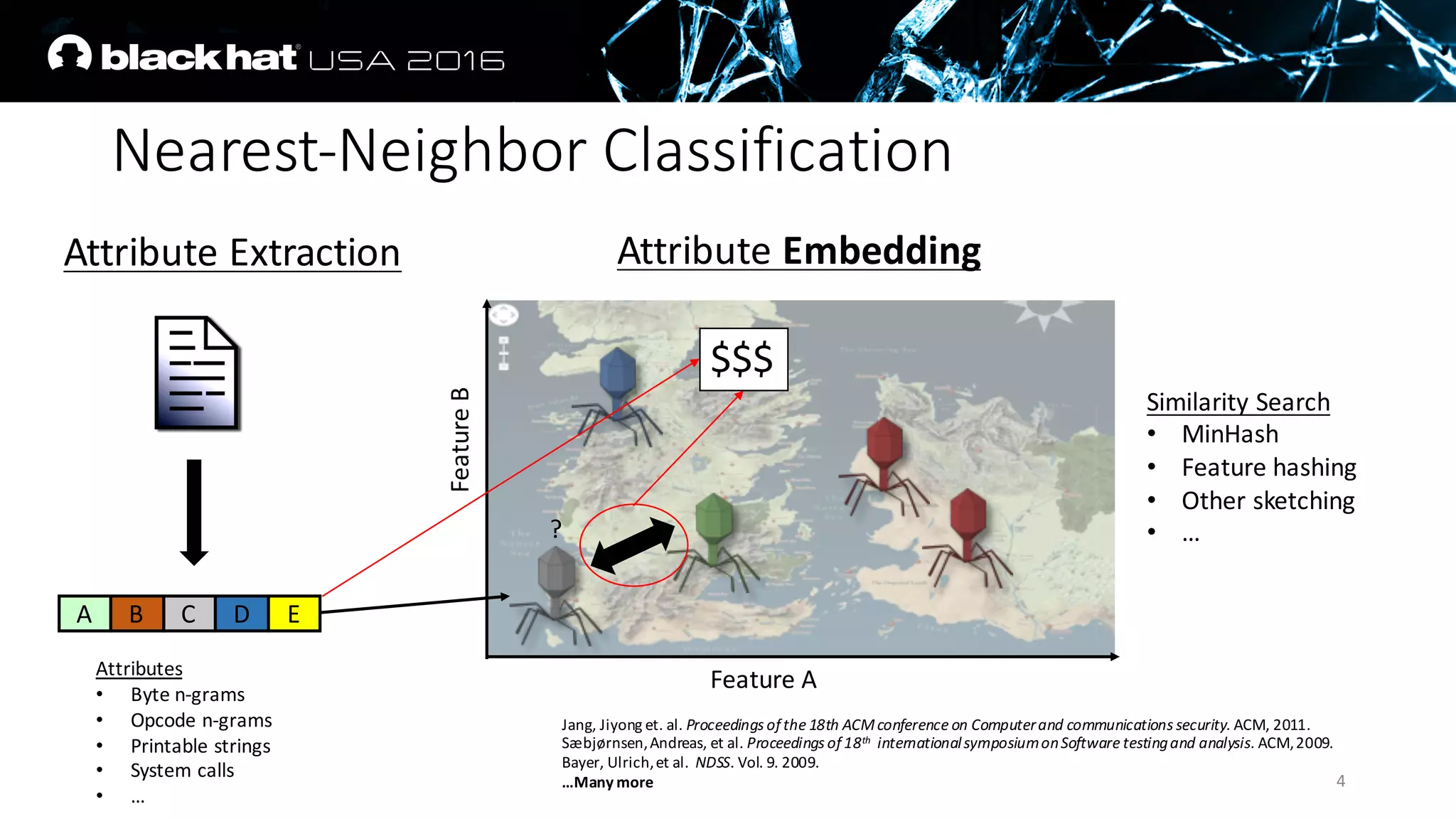
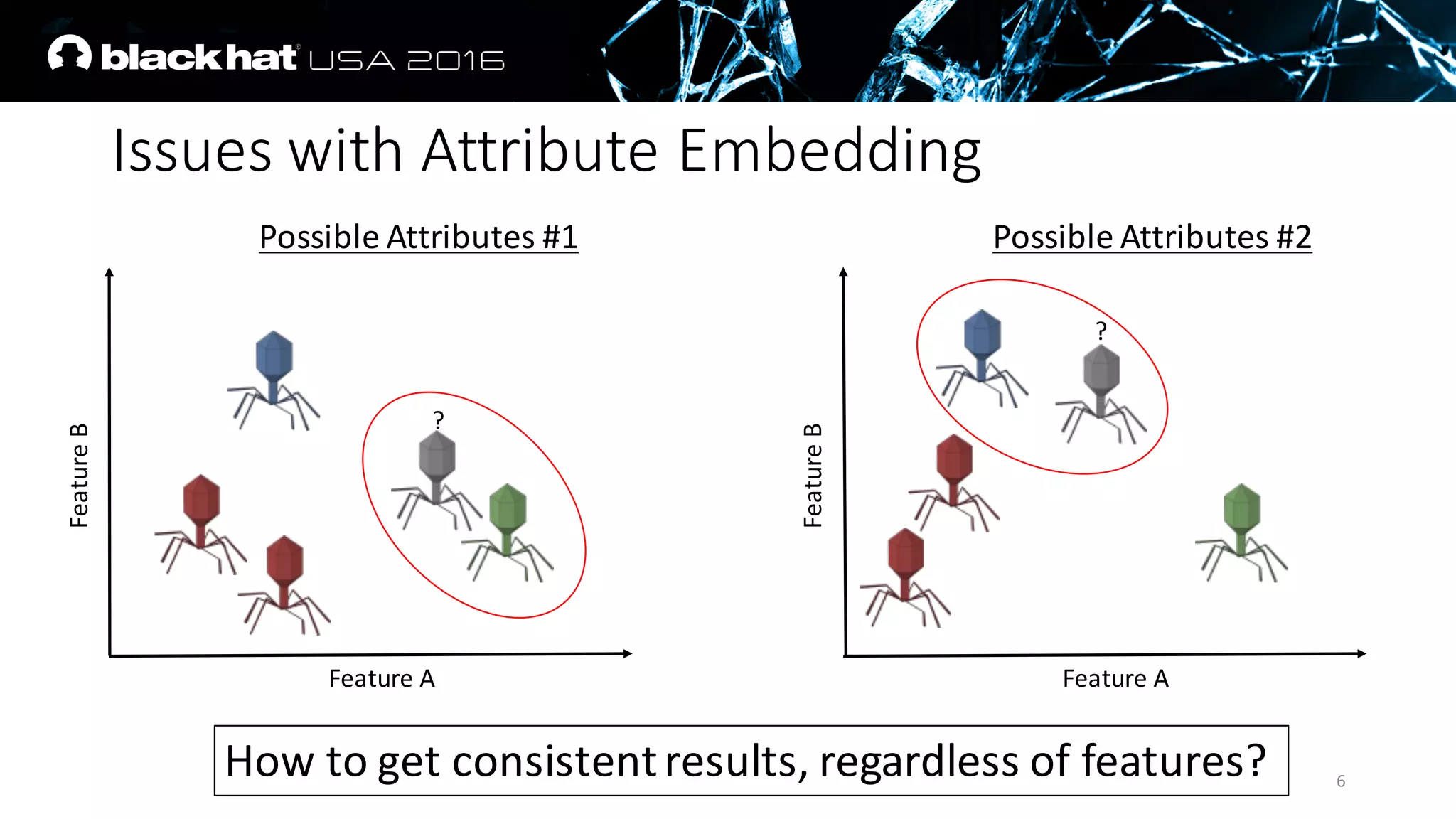
The document discusses an AI approach to malware similarity analysis using deep neural networks, highlighting the challenges in feature extraction and embedding for effective malware classification. It emphasizes the need for supervised learning over traditional unsupervised methods to enhance detection rates and reduce costs in malware triage systems. The research proposes a novel embedding technique that maps malware families based on their attributes, improving the consistency and semantic relevance of distance measurements in classification tasks.
![Supervised Classification (Endpoint Solution)
7
Layer 1
Layer 2
Layer 3
Layer N
[0,1]
…
Layer X
backdoor.msil.bladabindi.aa
backdoor.msil.bladabindi.aj
worm.winnt.lurka.a…
XJoshua Saxe and Konstantin Berlin, (MALWARE). IEEE, 2015.
0.97 F1-score (precision
and recall)
• 1500 Microsoft
Families
• 2.0M Training files
Malware Detection
Categorical Classification
Not enough for a triage system!
ABCDE](https://image.slidesharecdn.com/ai-approach-to-malware-similarity-analysis-mapping-the-malware-genome-with-a-deep-neural-network-161124071417/75/AI-approach-to-malware-similarity-analysis-Maping-the-malware-genome-with-a-deep-neural-network-7-2048.jpg)