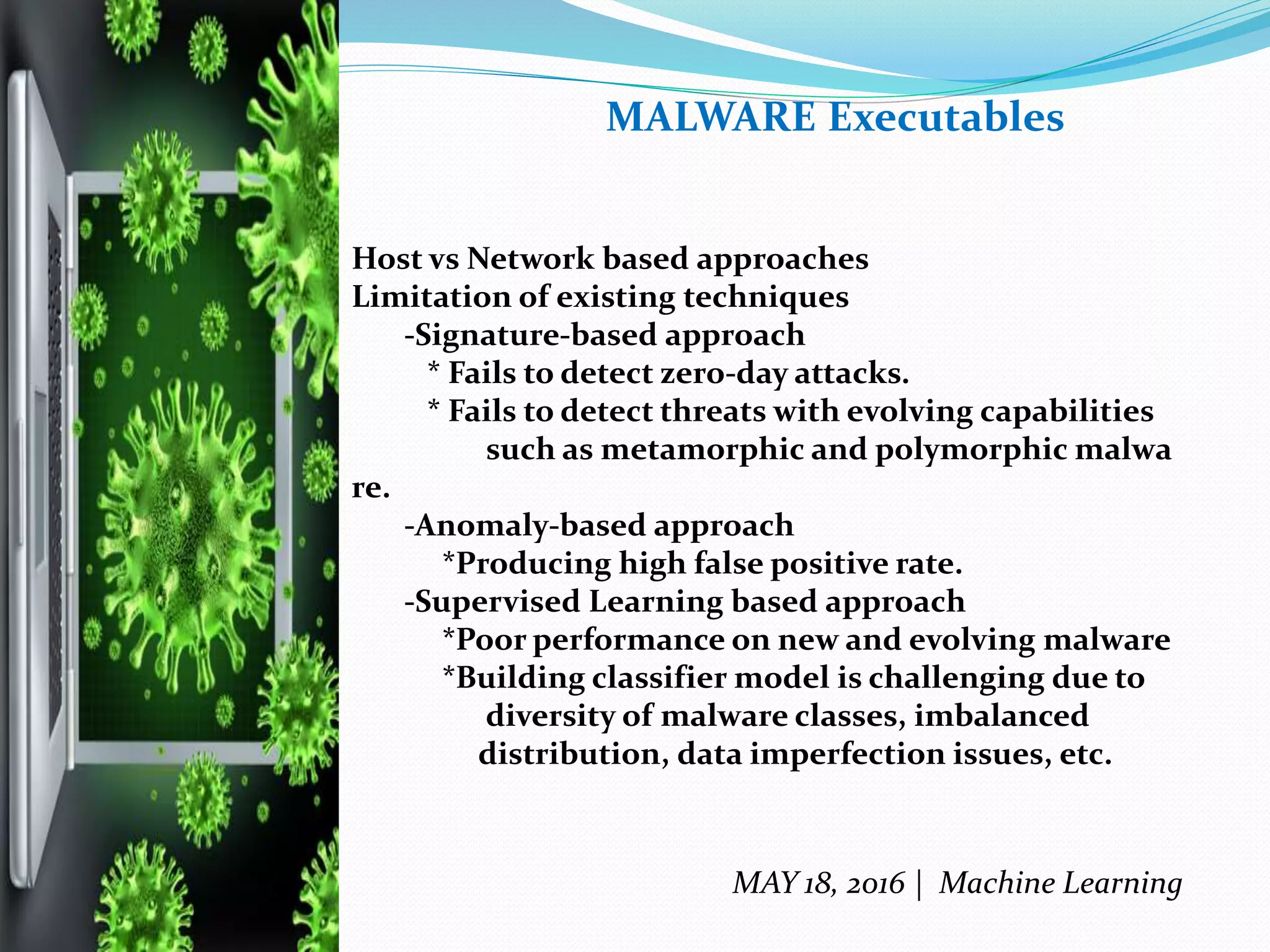
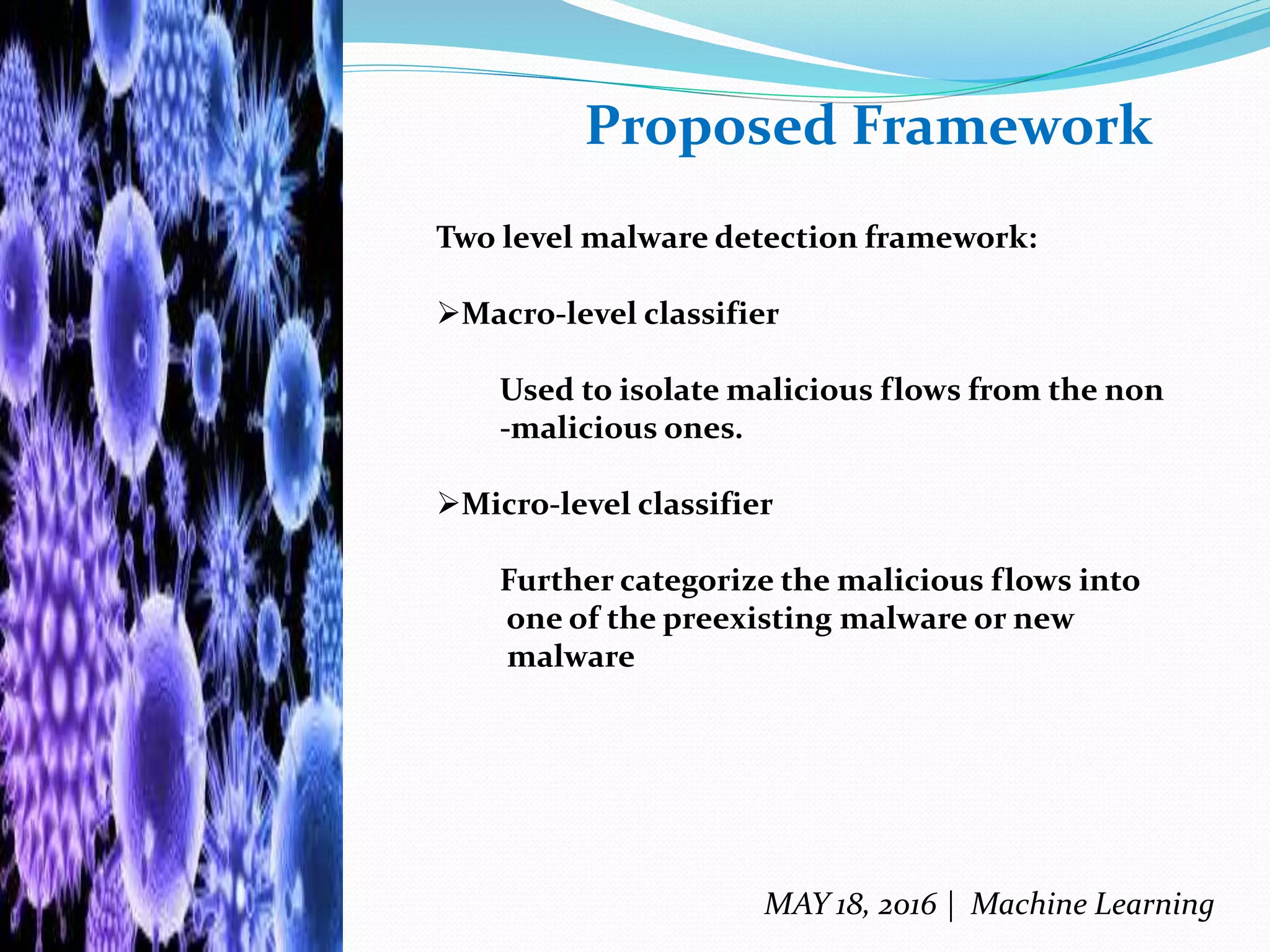
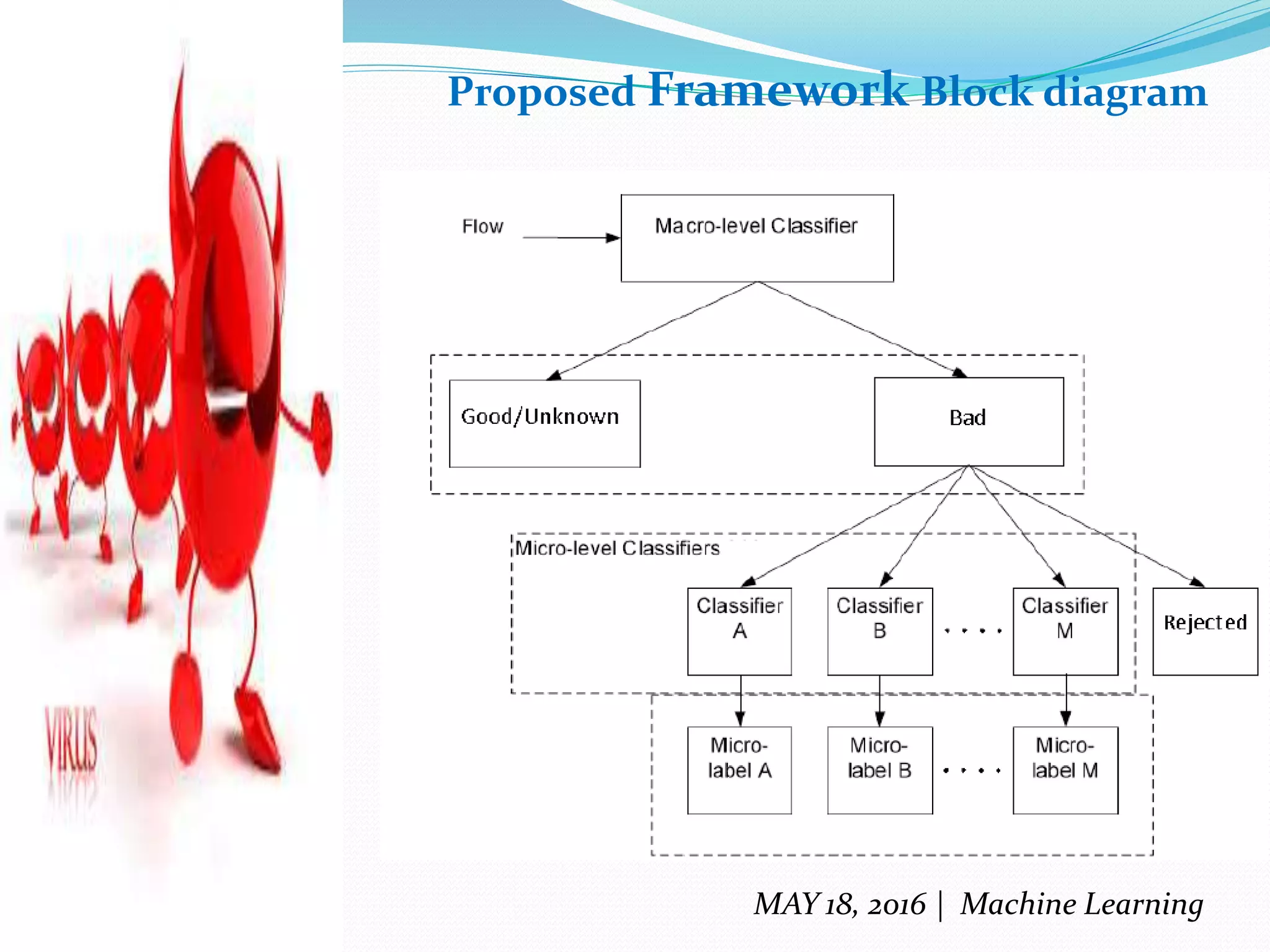
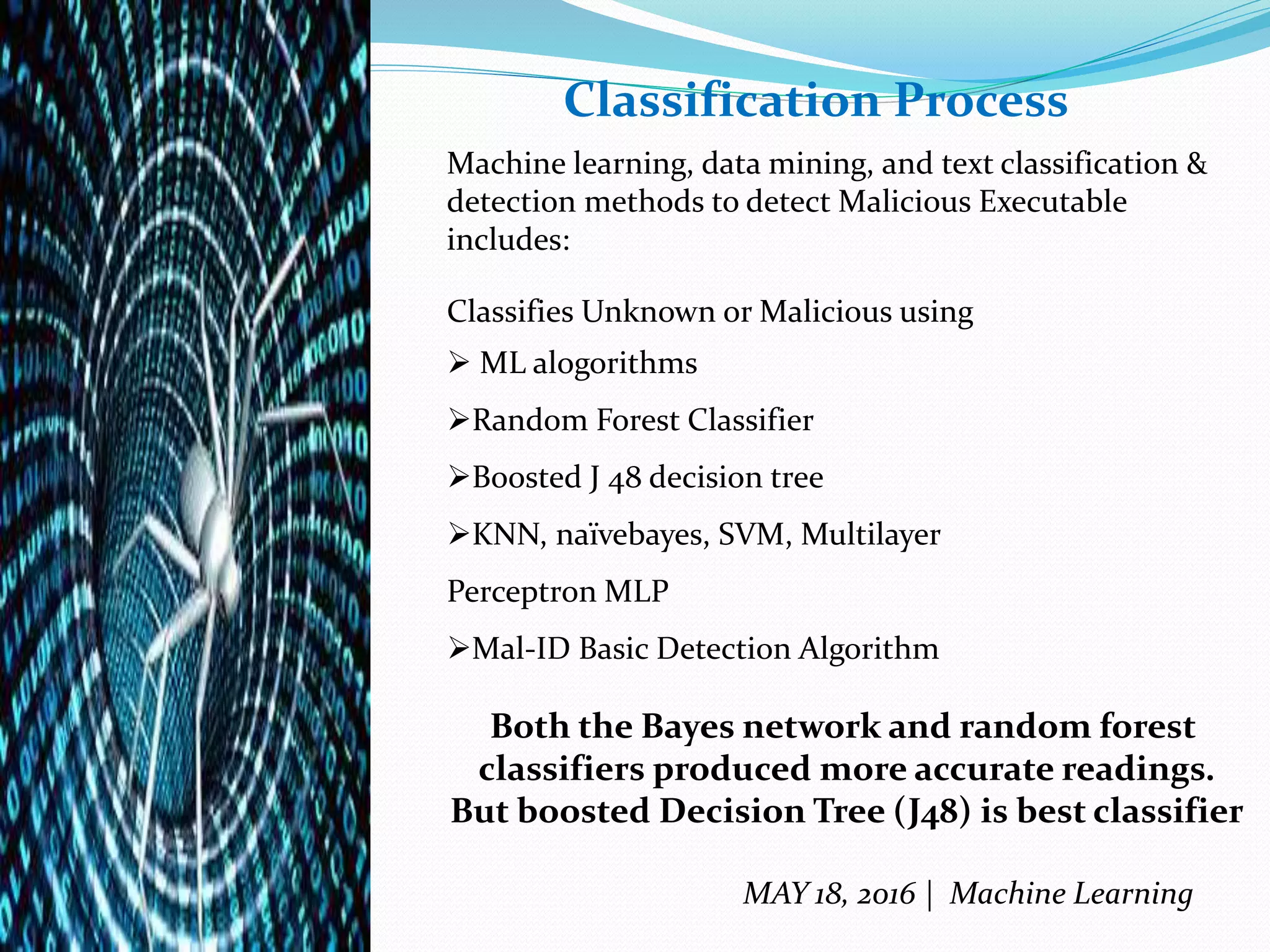
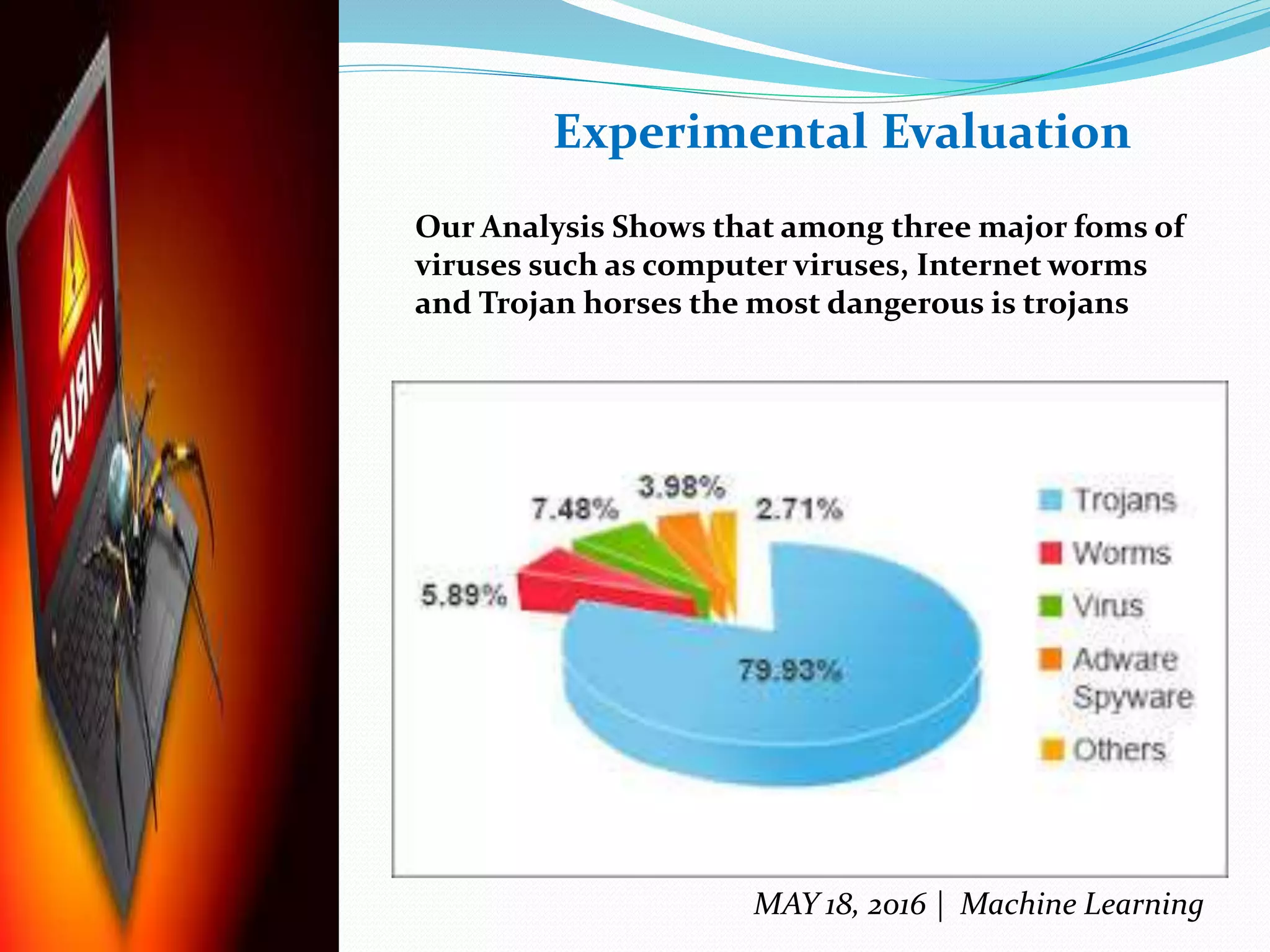
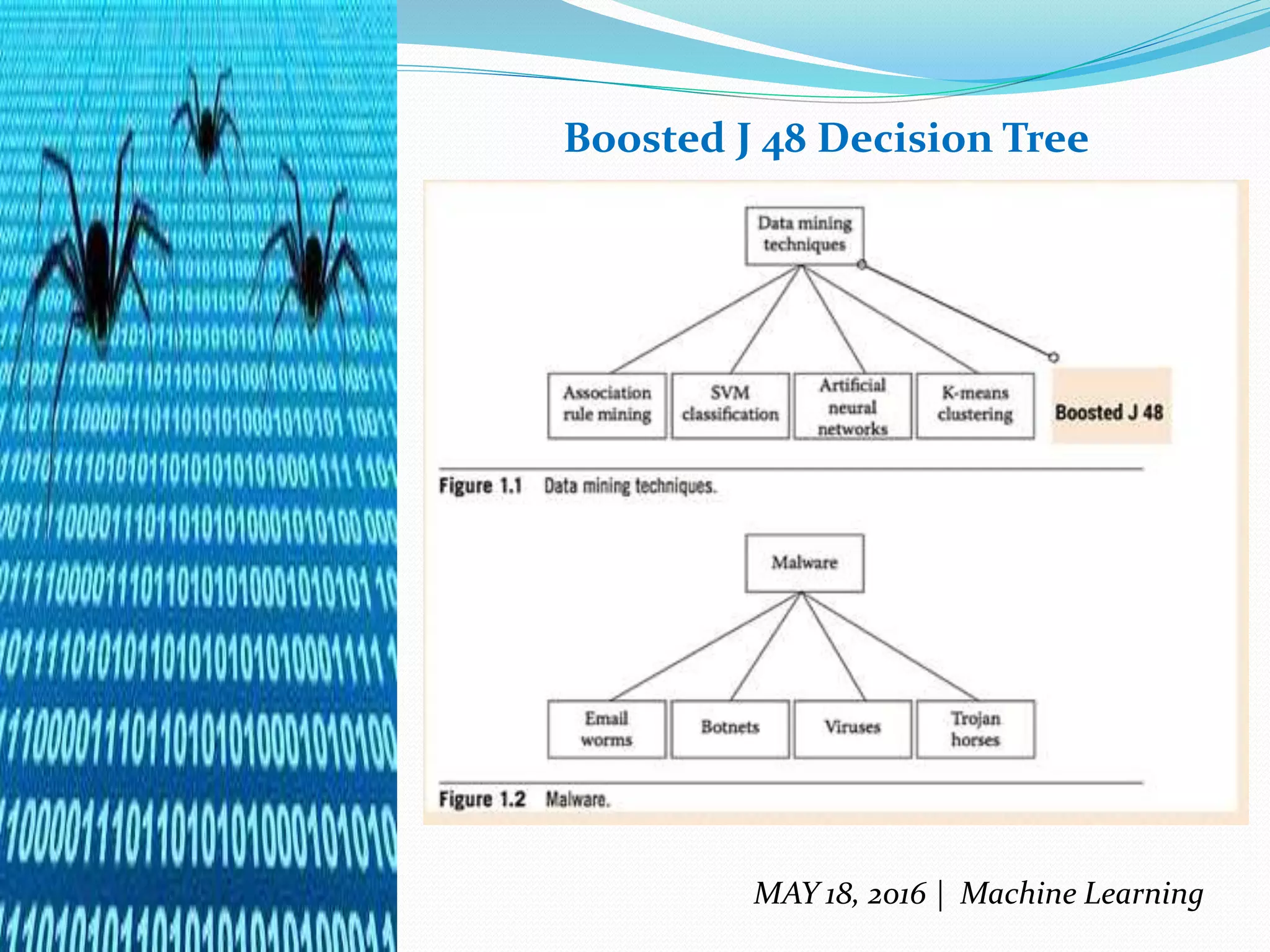
The document discusses machine learning techniques for detecting malware, highlighting the limitations of existing methods such as signature-based and anomaly-based approaches. It proposes a two-level classifier framework combining supervised and unsupervised learning to improve detection accuracy, particularly against evolving malware threats. The analysis emphasizes the effectiveness of the boosted J48 decision tree classifier and identifies trojans as the most dangerous form of malware, while suggesting future research avenues for enhancing detection capabilities.