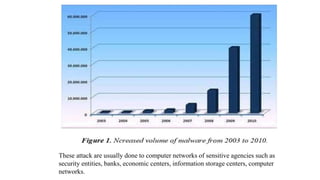
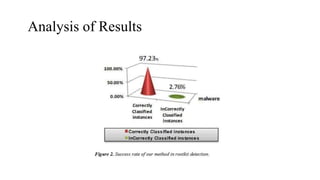
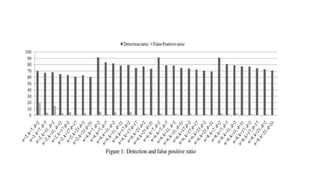
This document discusses techniques for malware detection using data mining. It begins by defining the problem of malware as one of the most serious issues faced on the internet. It then discusses types of malware like viruses, worms, trojans, and rootkits. It describes how rootkits can hide themselves and their activities. The document outlines static and dynamic analysis methods for malware detection and describes signature-based and behavior-based detection techniques. It shows results from using the Weka tool achieving over 97% success in rootkit detection. Advanced techniques discussed include n-grams and analyzing API/system calls.