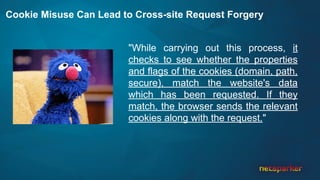
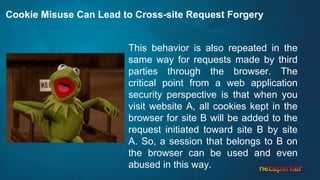
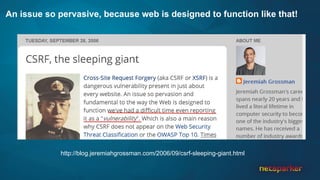
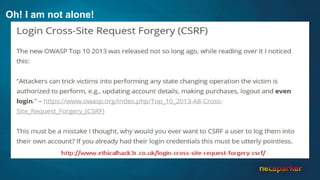
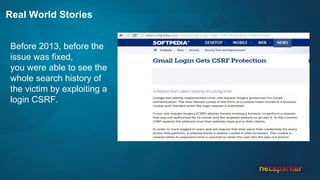
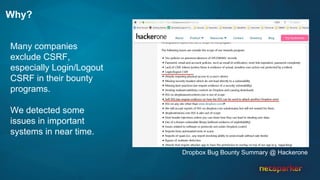
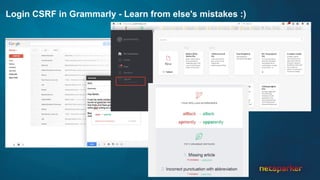
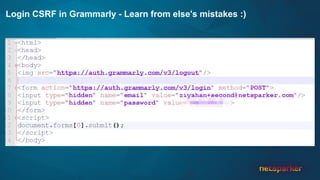
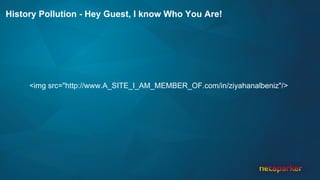
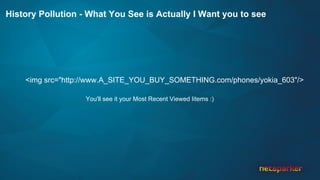
The document discusses cross-site request forgery (CSRF), explaining how it exploits the behavior of browsers sending cookies with HTTP requests, which can lead to unauthorized actions on behalf of users. It highlights the decline of CSRFs in the OWASP Top 10 due to increased awareness and implementation of anti-CSRF tokens, while also providing real-world examples of vulnerabilities in popular applications. The text emphasizes the importance of addressing CSRF vulnerabilities in web application security.