This document summarizes 5 papers on researching CSRF protection in web frameworks.
Paper 1 analyzes CSRF mitigation levels in popular JavaScript frameworks and finds that Express, Koa, and Hapi provide level 3 protection through plugins, while Sails has level 4 built-in protection and Meteor level 5 through architecture.
Paper 2 surveys CSRF defenses across frameworks and maps them to threats. It finds defenses are inconsistently implemented and most frameworks combine multiple defenses.
Paper 3 presents an algorithm called Mitch that uses machine learning to detect CSRF vulnerabilities as a black-box by analyzing differences in responses to sensitive versus insensitive requests.
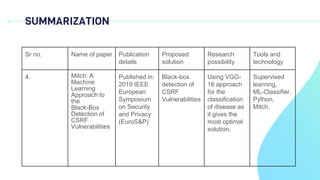
Paper 4 also uses machine learning for CSRF detection and tests it on existing






![PAPERS
1. CSRF protection in JavaScript frameworks and the security of JavaScript
applications. [1]
2. Where We Stand (or Fall): An Analysis of CSRF Defenses in Web Frameworks. [2]
3. Automatic Black-Box Detection of Resistance Against CSRF Vulnerabilities in
Web Applications. [3]
4. Machine Learning for Web Vulnerability Detection: The Case of Cross-Site
Request Forgery. [4]
5. Mitch: A Machine Learning Approach to the Black-Box Detection of CSRF
Vulnerabilities. [5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-7-320.jpg)
![PAPER 1
CSRF protection in JavaScript frameworks
and the security of JavaScript
applications. [1]
• Published in High-Confidence Computing on December 2021](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-8-320.jpg)

![WHY JAVASCRIPT
It’s because according to StackOverflow Developer Survey of 2021, JavaScript is named ”the
most commonly used programming language” for the ninth year in a row. [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-10-320.jpg)


![EXPRESS
For CSRF protection there are two popular plugins: csrf and csurf in
Express, csurf middleware builds on top of the csrf middleware and it
provides protection at level L3.
Fig:1.1 Express [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-13-320.jpg)
![Koa
The most commonly used for CSRF protection is the koa-csrf plugin in Koa. It
is used globally, and the token can be submitted in the request body, as a
query parameter, or as an HTTP header. The koa-csrf plugin implements the
CSRF security control at level L3.
Fig: 1.2 Koa [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-14-320.jpg)
![Hapi.js
The most common plugin for CSRF protection is crumb and it implements
CSRF protection with the double-submit cookie technique. Thus, similar to
Express and Koa, the Hapi framework provides the CSRF security control with
the crumb plugin at mitigation level L3.
Fig:1.3 Hapi [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-15-320.jpg)
![Sails.js
Sails has several built-in security features which are configured as policies
and implemented as middleware functions. One of such security features is
CSRF protection. Therefore, it implements the CSRF protection at level L4
Fig: 1.4 Sails [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-16-320.jpg)


![RESULT ANALYSIS
Table 1: Results Tables [1]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-19-320.jpg)


![TABLE 1
Overview of CSRF defenses and threats. The left part summarizes our survey of CSRF
defenses. The right part shows the mapping between each defense and potential threats. [2]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-22-320.jpg)
![TABLE 2
Frequency of the combination of CSRF defenses. Each
entry in this symmetric table shows the number of
frameworks that use a certain combination. [2]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-23-320.jpg)
![TABLE 3
Summary of results on top five frameworks of top five languages. [2]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-24-320.jpg)
![TABLE 4
Summary of results on less popular frameworks of top four languages. Only five
frameworks were identified for C#. [2]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-25-320.jpg)



![HTTP REQUEST CLASSIFICATION
● The average number of parameters of sensitive requests is around 6.27, while for
insensitive ones this is 3.43.
● it is evident that the median value of numOfParams is significantly higher for
sensitive than for insensitive HTTP requests.
Fig: 3.1 - Distribution of numOfParam [3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-29-320.jpg)
![HTTP REQUEST CLASSIFICATION
● This figure suggests that the length of sensitive requests is somewhat
more consistent and bounded within a smaller range of generally higher
values.
Fig: 3.2 - Distribution of reqLen [3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-30-320.jpg)
![HTTP REQUEST CLASSIFICATION
● Here this is distribution of the two features isGET and isPOST across sensitive and
insensitive requests.
● We observe that about 30% of POST requests are labeled as sensitive, while only
5% of GET requests are sensitive.
Fig: 3.3 - Distribution of class labels across the two functional
features [3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-31-320.jpg)
![Feature Importance
● we use the importance score as provided by the scikit-learn package, which in turn
implements it using Gini impurity Here is the top- 10 most important features
derived from our RF classifier.
● We can observe that the two most important features are and numOfParams,
followed by the two features reqLen encoding the request method.
Fig: 3.4 - Top10 most important features derived from
our RF [3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-32-320.jpg)
![CSRF Detection Algorithm
● the algorithm works by first building a set of candidate vulnerabilities,
based on sensitive requests which produce dissimilar responses.
Fig: 3.5 - Algorithm 1 CSRF Detection Algorithm [3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-33-320.jpg)
![SOLUTION
● Adversarial learning is an active research area whose main goal is designing
classification algorithms which are robust to the presence of attackers who actively
try to fool them into misprediction
Fig: 3.6 Mitch architecture[3]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-34-320.jpg)




![Architecture of Mitch
Fig: 4.1 Mitch architecture[4]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-39-320.jpg)
![CSRF DETECTION ON EXISTING WEBSITES
Table: 4.1 - CSRF DETECTION ON EXISTING WEBSITES [4]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-40-320.jpg)
![CSRF DETECTION ON PRODUCTION SOFTWARE
Table: 4.2 - CSRF DETECTION ON PRODUCTION
SOFTWARE [4]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-41-320.jpg)


![CSRF DETECTION SYSTEM
Architecture of the Proposed CSRF Detection
System.
Fig: 5.1 - The Architecture of the Proposed CSRF
Detection System. [5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-44-320.jpg)
![CSRF DETECTION RULES
The Order of Applying Anti-CSRF Detection
Rules.
Fig: 5.2 - The Order of Applying Anti-CSRF Detection
Rules. [5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-45-320.jpg)
![ARCHITECTURE
The Architecture of Our System to Detect
Resistant Requests Against CSRF.
Fig: 5.3 - The Architecture of Our System to Detect
Resistant Requests Against CSRF.[5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-46-320.jpg)

![RESULTS
The Number of Detected Anti-CSRF Tokens vs. the
Expected Number of Anti-CSRF Tokens for Chmail With
the Augmented Traffic.
Table: 5.1 - Anti-CSRF token detect.[5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-48-320.jpg)










![REFERENCES
1. CSRF protection in JavaScript frameworks and the security of JavaScript
applications. [1]
2. Where We Stand (or Fall): An Analysis of CSRF Defenses in Web Frameworks. [2]
3. Automatic Black-Box Detection of Resistance Against CSRF Vulnerabilities in
Web Applications. [3]
4. Machine Learning for Web Vulnerability Detection: The Case of Cross-Site
Request Forgery. [4]
5. Mitch: A Machine Learning Approach to the Black-Box Detection of CSRF
Vulnerabilities. [5]](https://image.slidesharecdn.com/sohilrm1-231013055412-347e75e9/85/SOHIL_RM-1-pptx-60-320.jpg)
