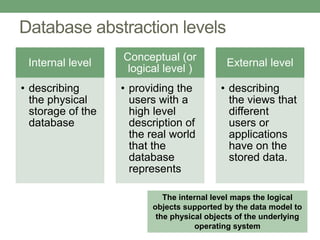
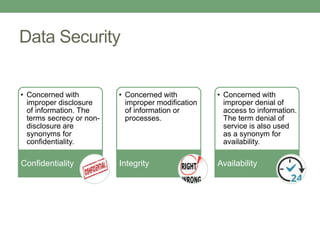
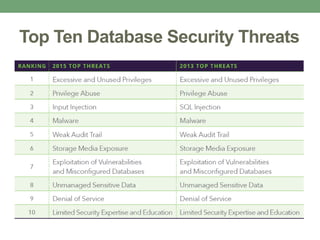
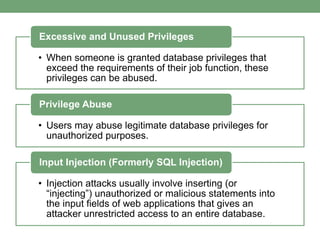
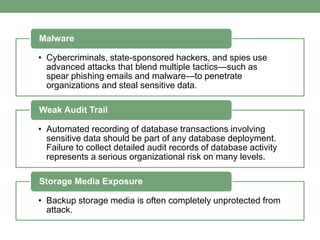
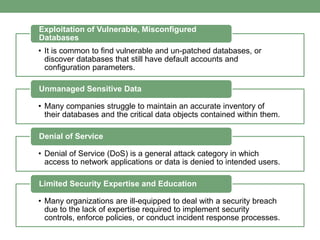
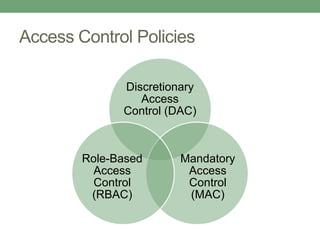
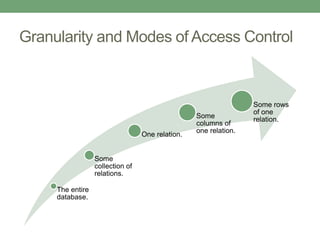
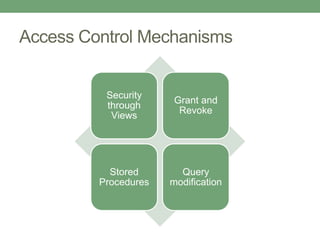
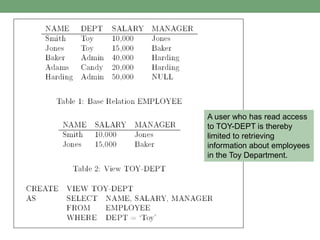
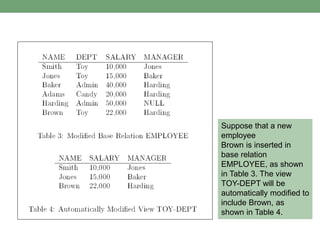
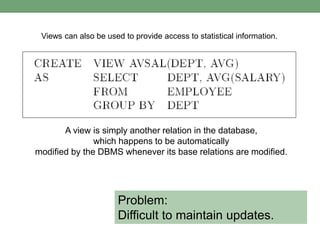
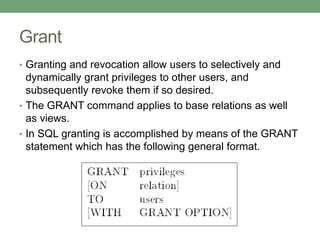
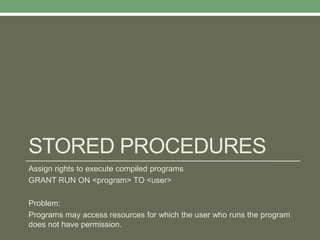
Databases store logically interrelated data representing real-world aspects. They require security measures to protect data confidentiality, integrity, and availability from threats. Common threats include privilege abuse, injection attacks, and unmanaged sensitive data. Database security uses prevention techniques like access control and detection techniques like auditing. Access control policies include discretionary access control based on authorization rules, mandatory access control, and role-based access control. Views and stored procedures also help implement access control by restricting data access.