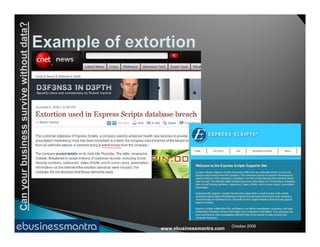
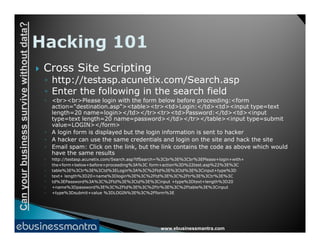
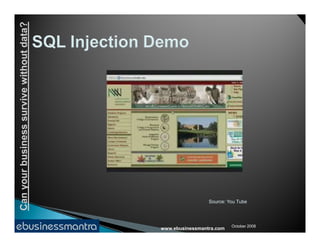
The document discusses the importance of web application security and the potential risks businesses face without proper data protection. It outlines common vulnerabilities in web applications, such as cross-site scripting and SQL injection, and emphasizes the need for regular application testing and awareness of security issues among stakeholders. The consequences of security breaches can include significant data loss, financial costs, and damage to a company's reputation.