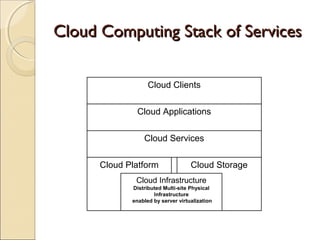
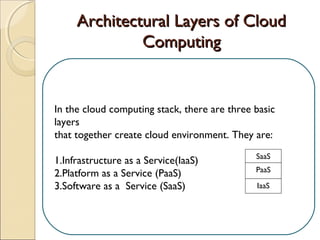
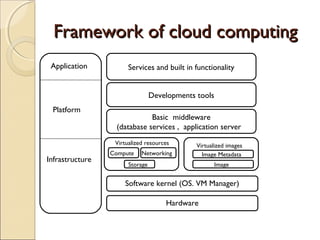
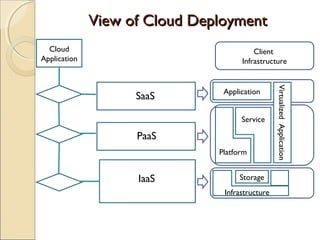
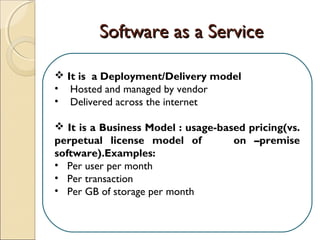
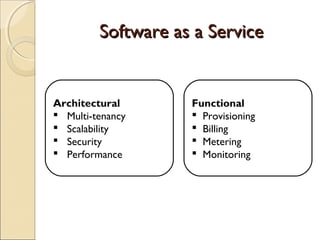
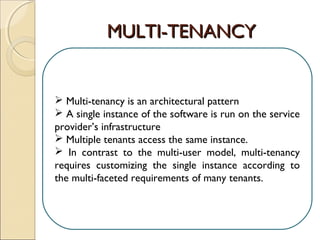
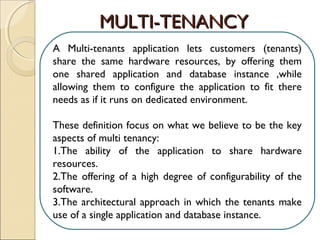
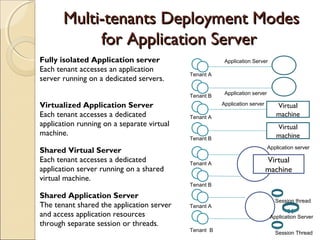
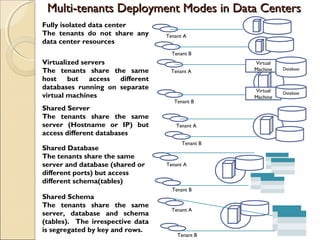
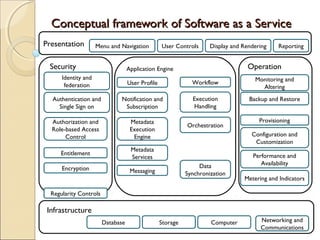
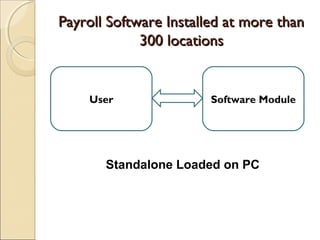
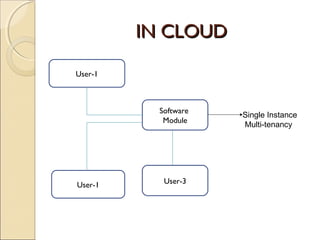
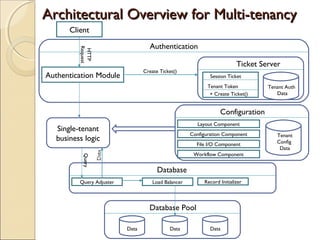
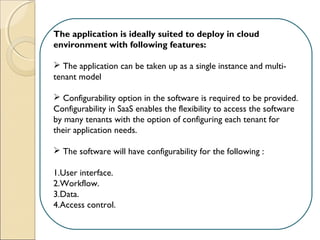
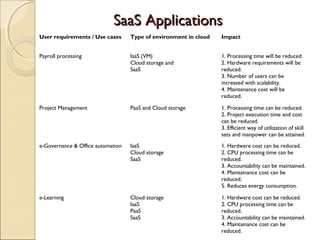
The document discusses cloud architecture and describes the different layers of cloud computing including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). It explains how virtualization allows for the pooling of computing resources and rapid provisioning of these resources. The document also discusses multi-tenancy and how a single software instance can be configured for multiple tenants' needs in a SaaS environment. As an example, it describes how a payroll processing application currently used by multiple government departments could be migrated to a cloud environment for improved maintenance and reduced costs.