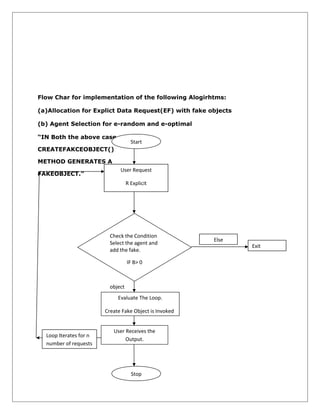
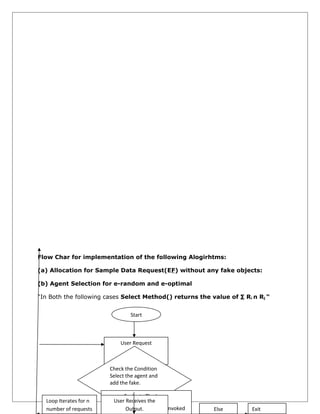
The document discusses a system for detecting data leakage when a data distributor shares sensitive data with third party agents. The system aims to identify which agent leaked the data if a leak occurs. It proposes allocating data across agents strategically and injecting fake records to improve the ability to detect leaks and identify guilty parties. The key modules are an administrator module to manage the system, an employee module for read-only access, and a data leakage detection module that uses techniques like fake object generation and watermarking to monitor access and provide proof against leaks.