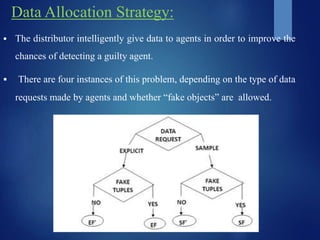
The document discusses data leakage detection, defining data leakage as the unauthorized transmission of sensitive information to external parties. It outlines the limitations of current watermarking techniques and presents a model where fake objects are introduced to enhance detection capabilities while fulfilling agent requests without altering original data. Various strategies for data allocation and distribution are explored, emphasizing the probability of identifying agents responsible for data leaks.