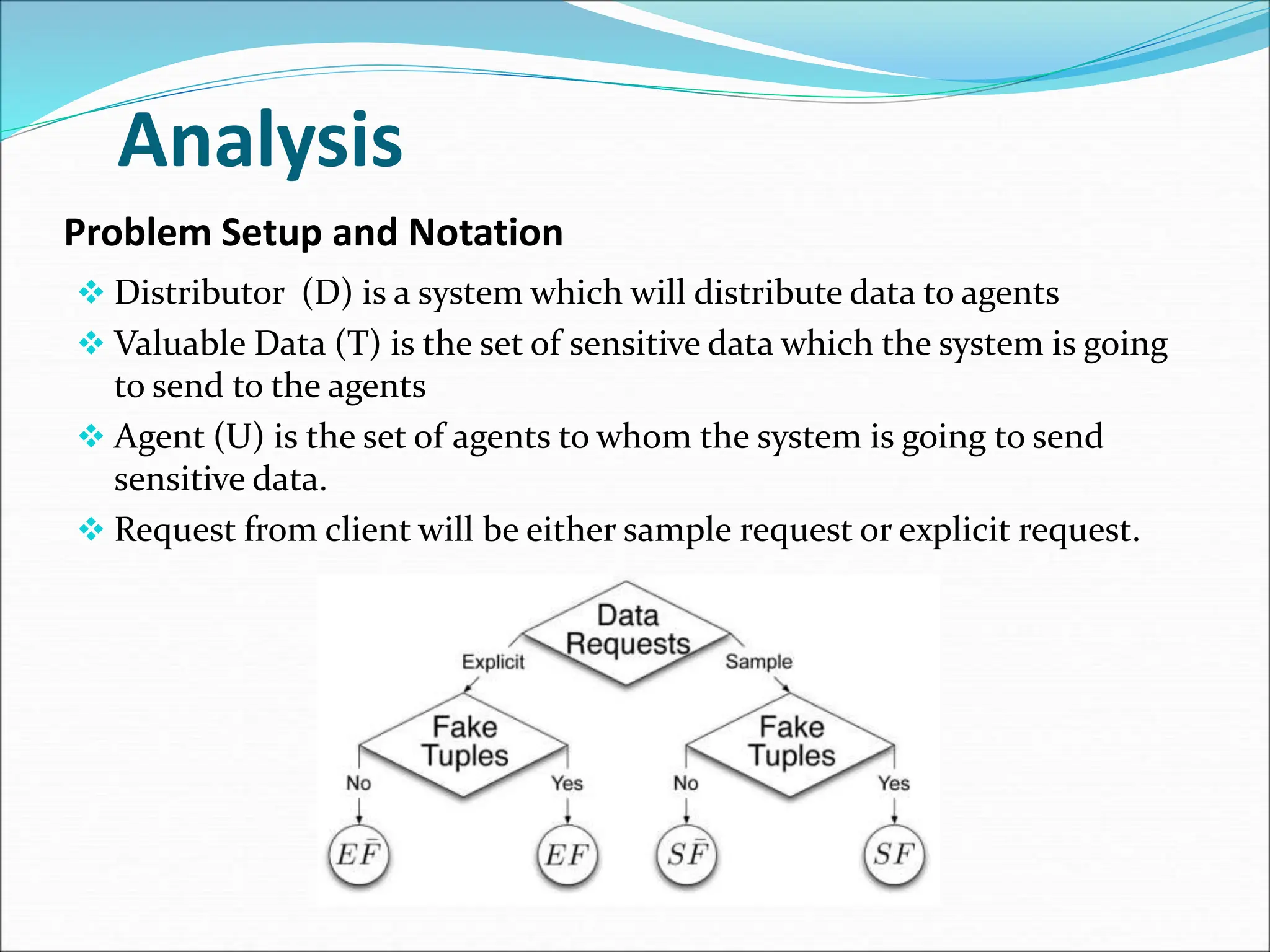
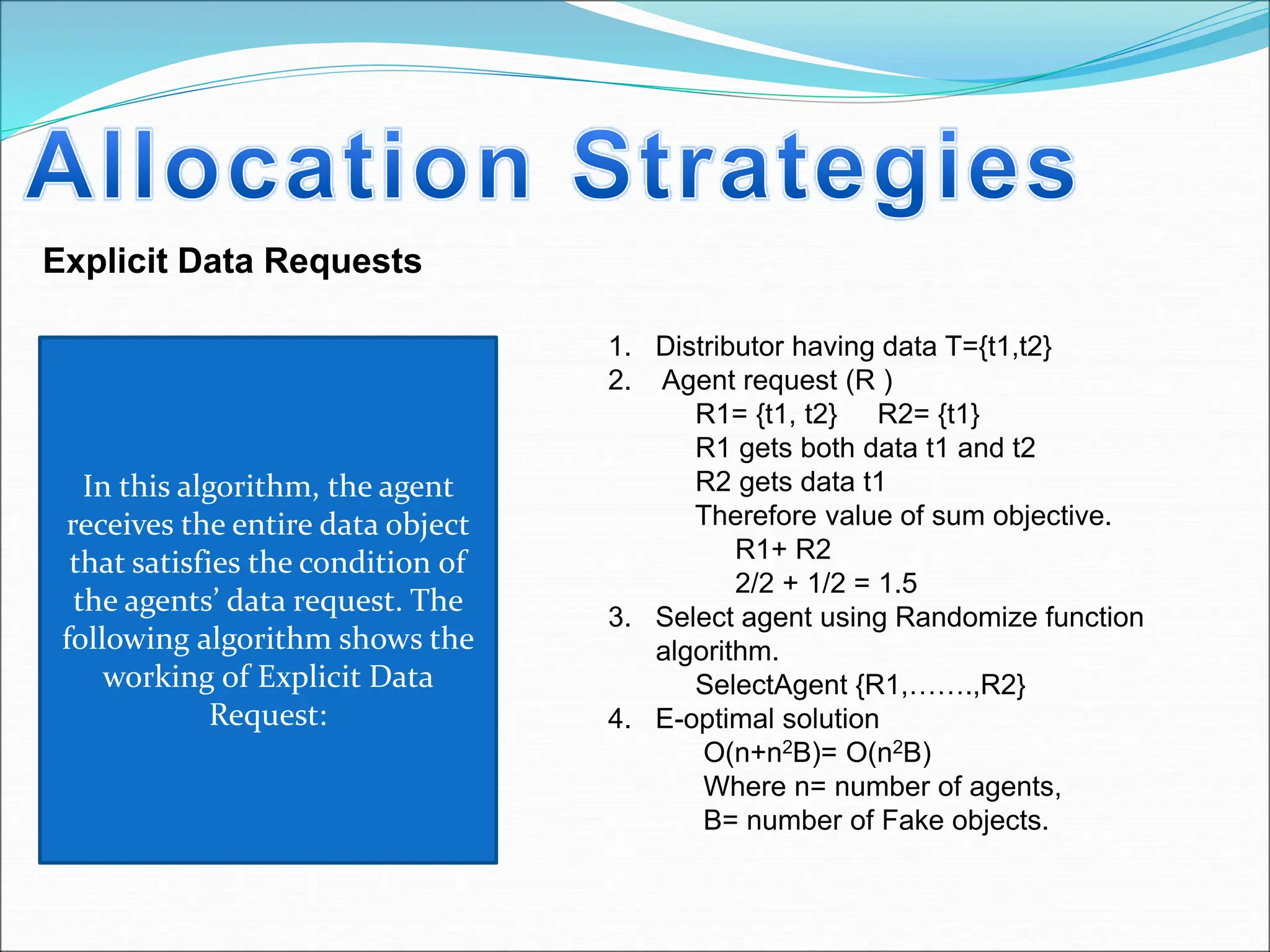
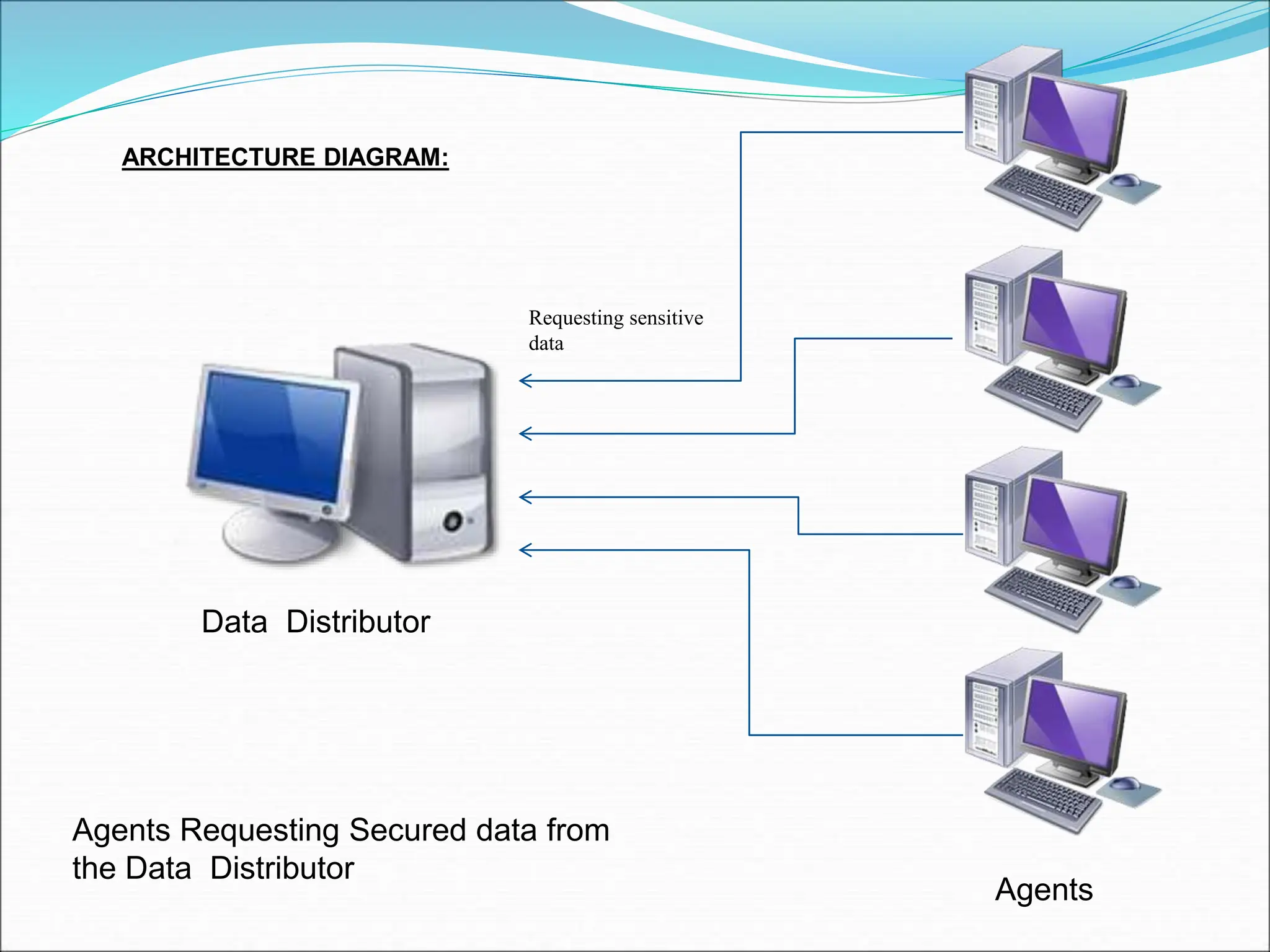
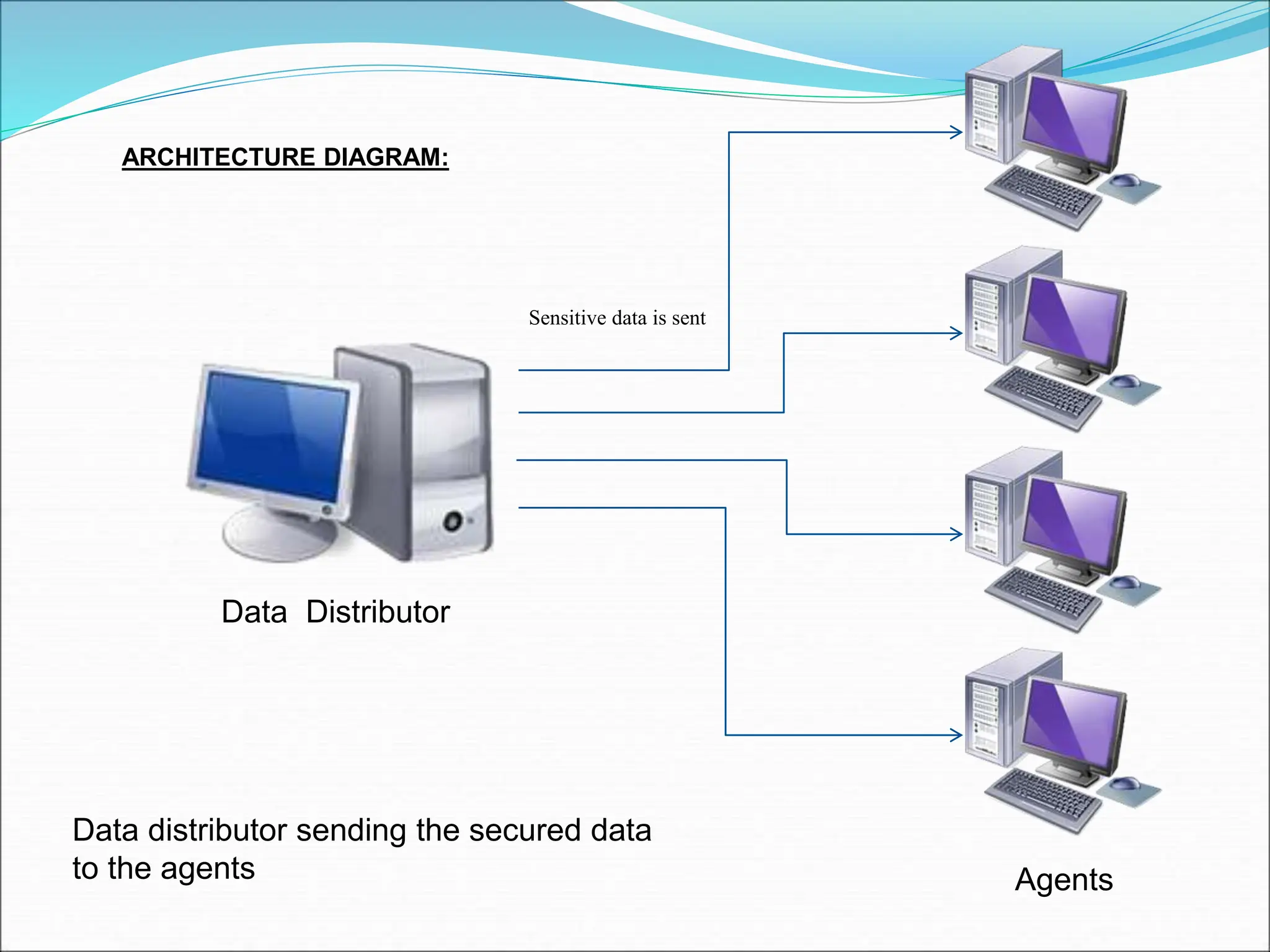
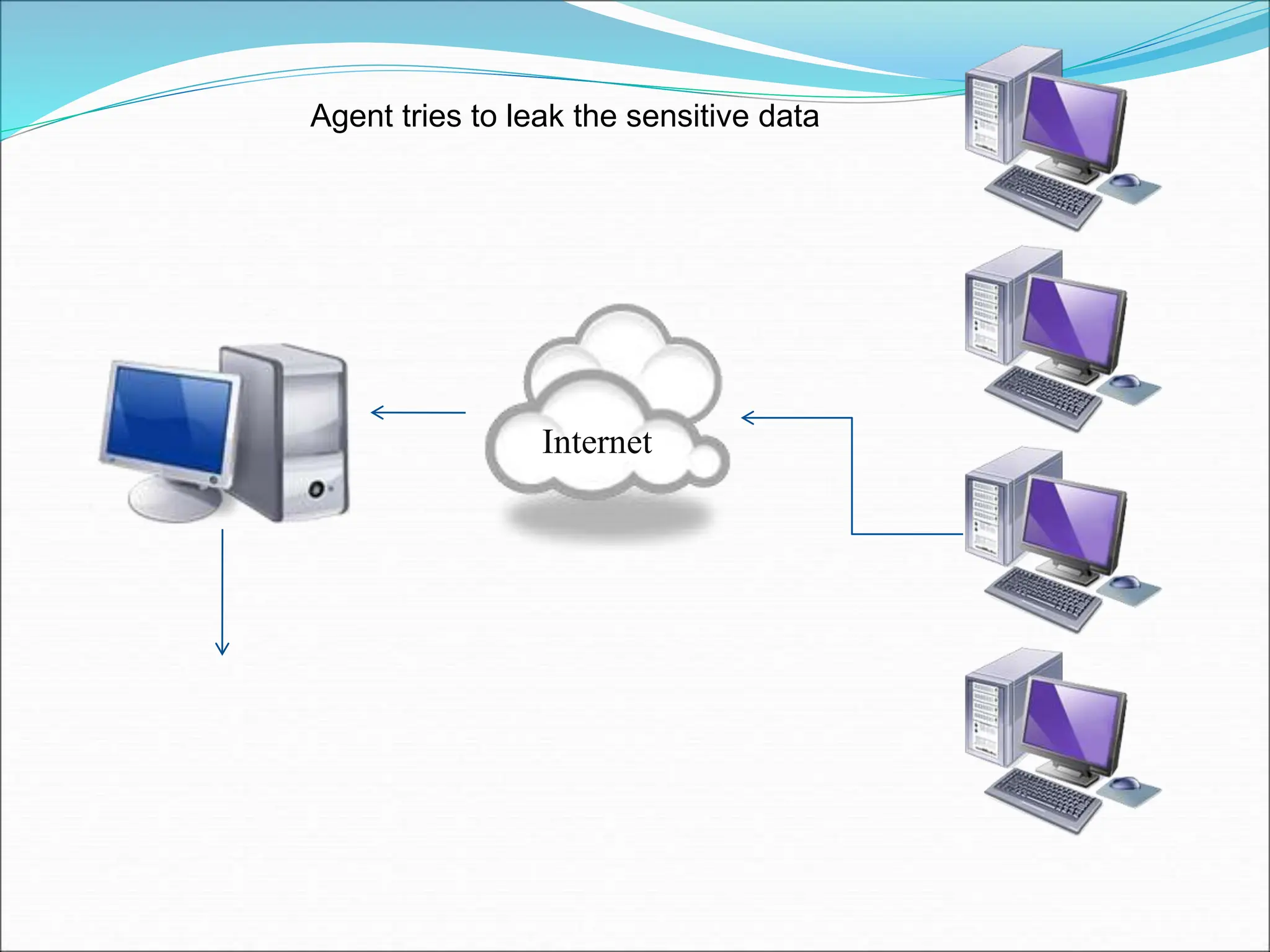
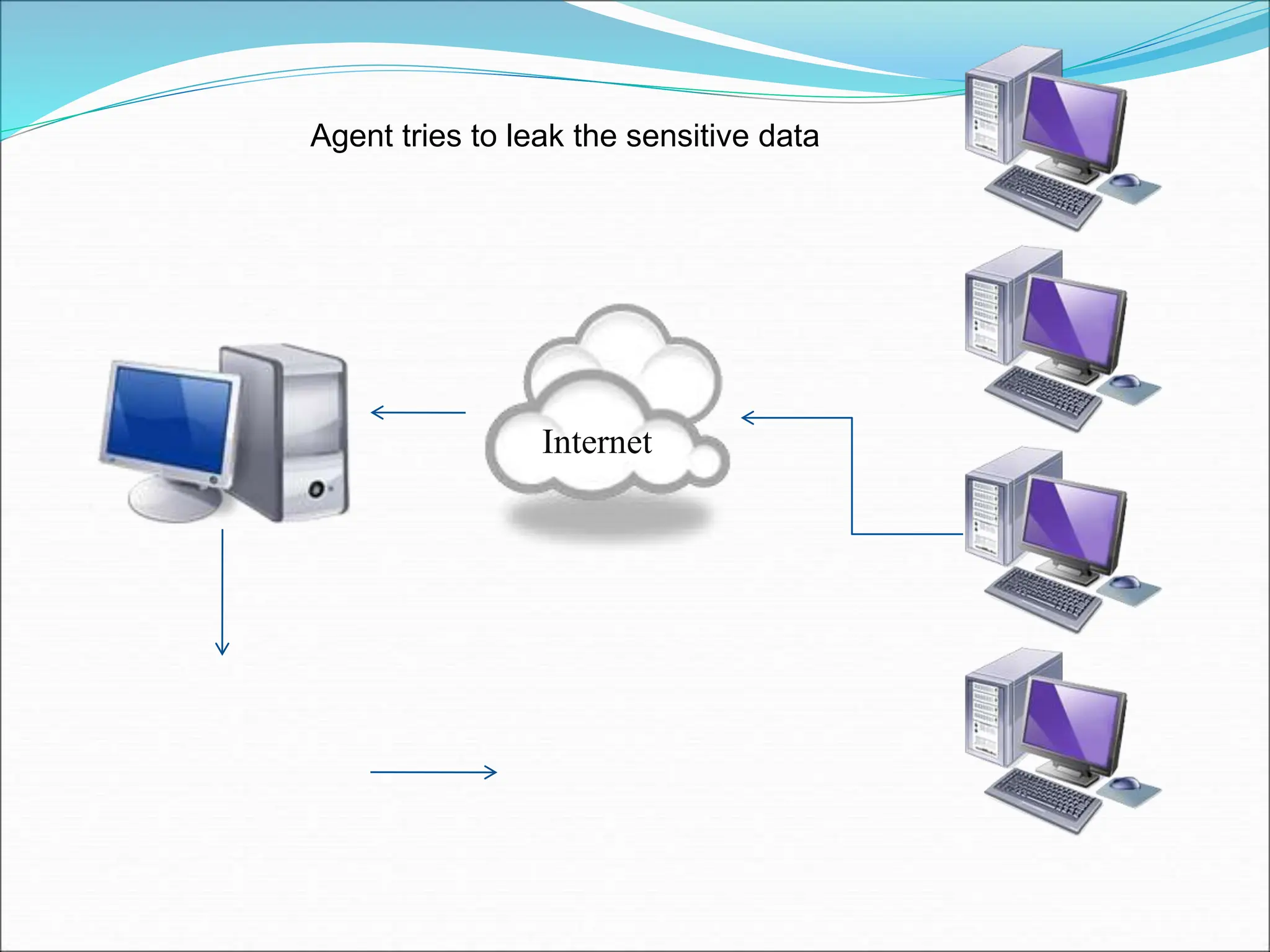
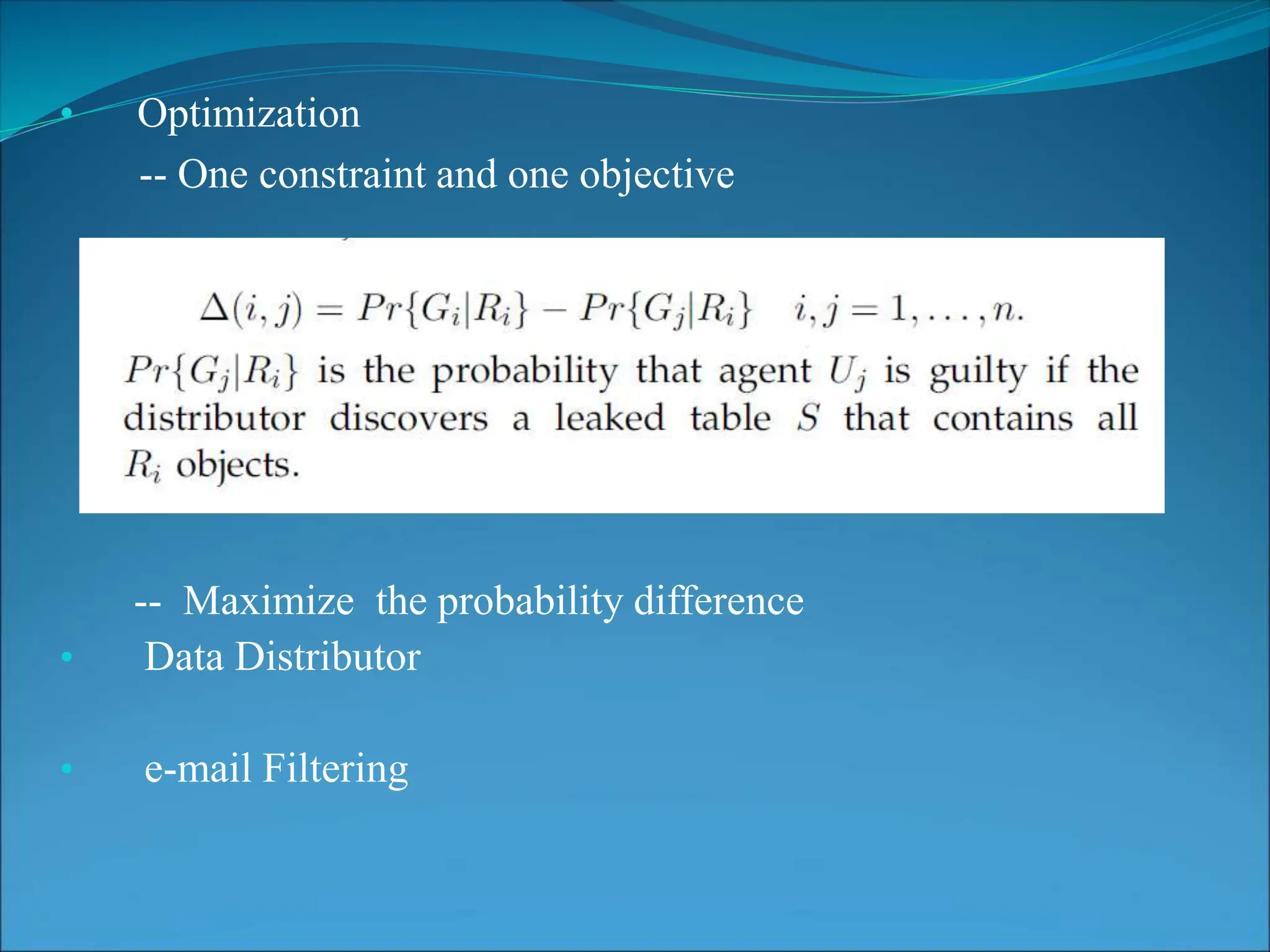
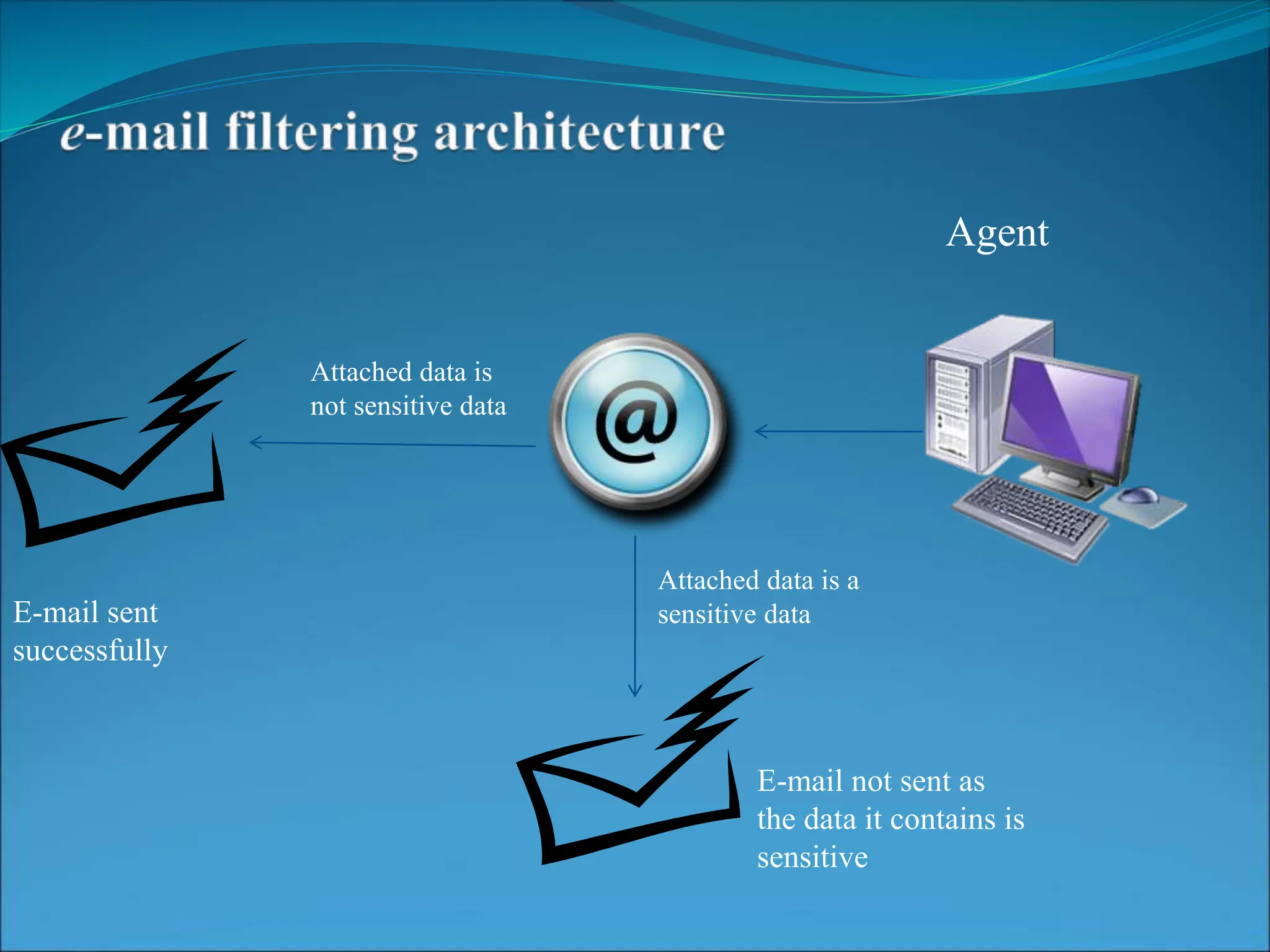
This document presents a system for detecting data leakage from agents. It discusses generating fake objects to embed in distributed data to track its source if leaked. The system architecture includes a data distributor that sends sensitive data to agents, with an email filtering system to detect leaked data. If sensitive company data is detected in an agent's email, the message will not be sent. The system aims to maximize the probability of identifying the leaking agent using optimization algorithms during data distribution.