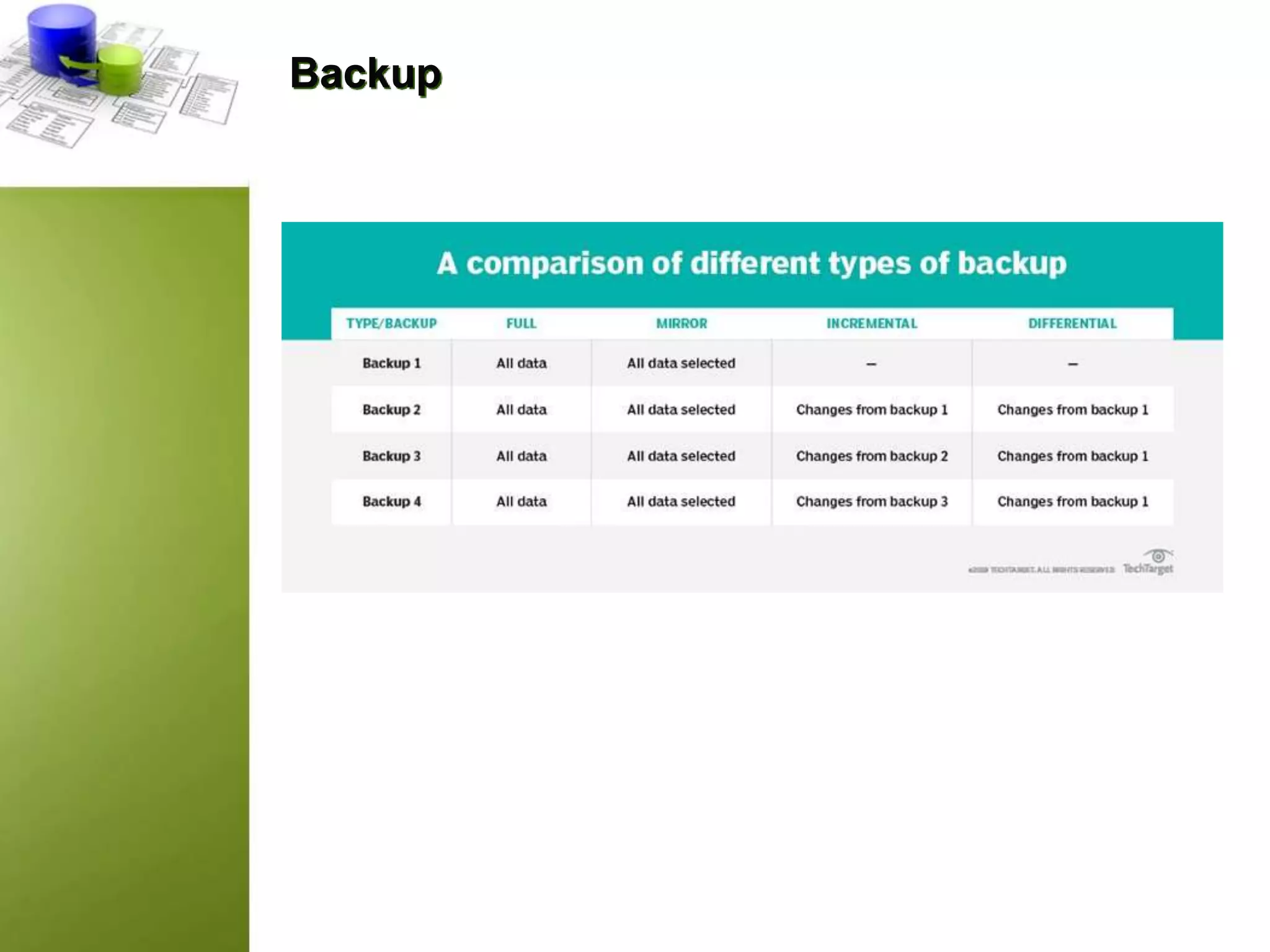
This document discusses data integrity and how to preserve it. It defines data integrity as the completeness, accuracy, and consistency of data throughout its lifecycle. Data integrity ensures the validity and accuracy of data and is different from data security which protects data. Threats to data integrity include human error, transfer errors, security issues, attacks, and hardware problems. Tools are recommended to check for duplicate files and remove them to maintain integrity. Backups are also important to prevent data loss. The document outlines features of data integrity like accessibility and reliability of data. It provides a checklist for input and data validation, duplicate removal, and access controls to preserve integrity.