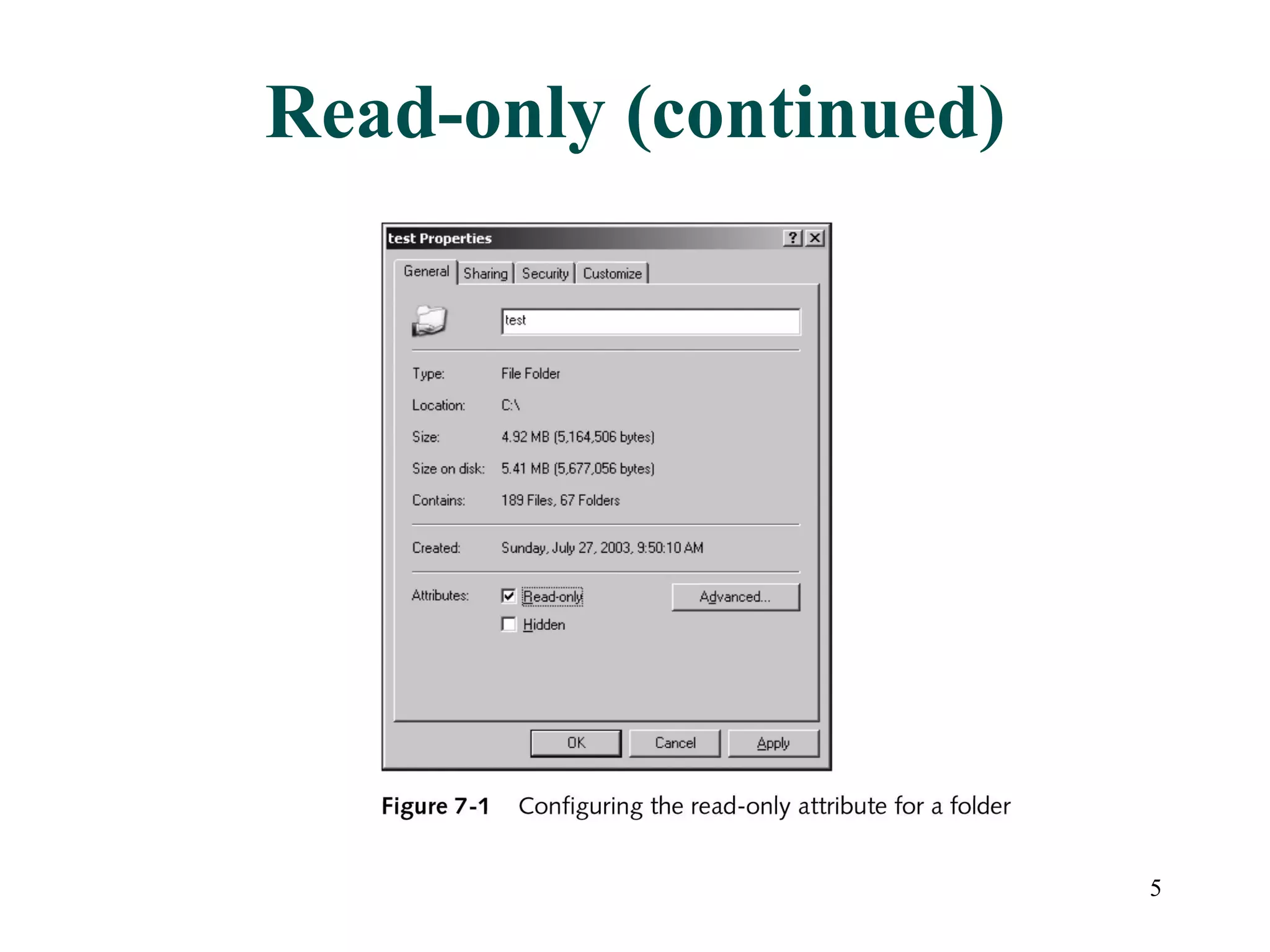
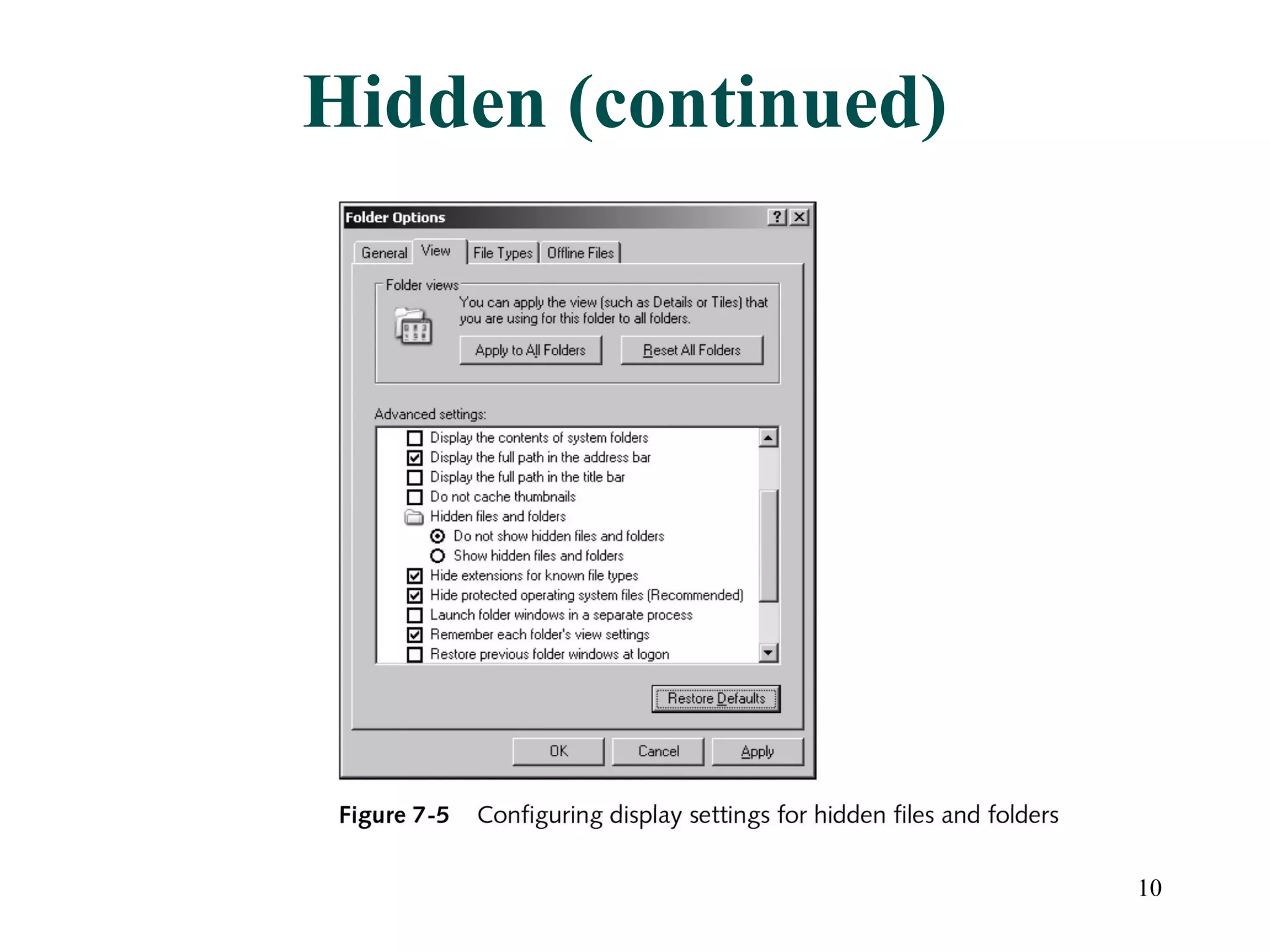
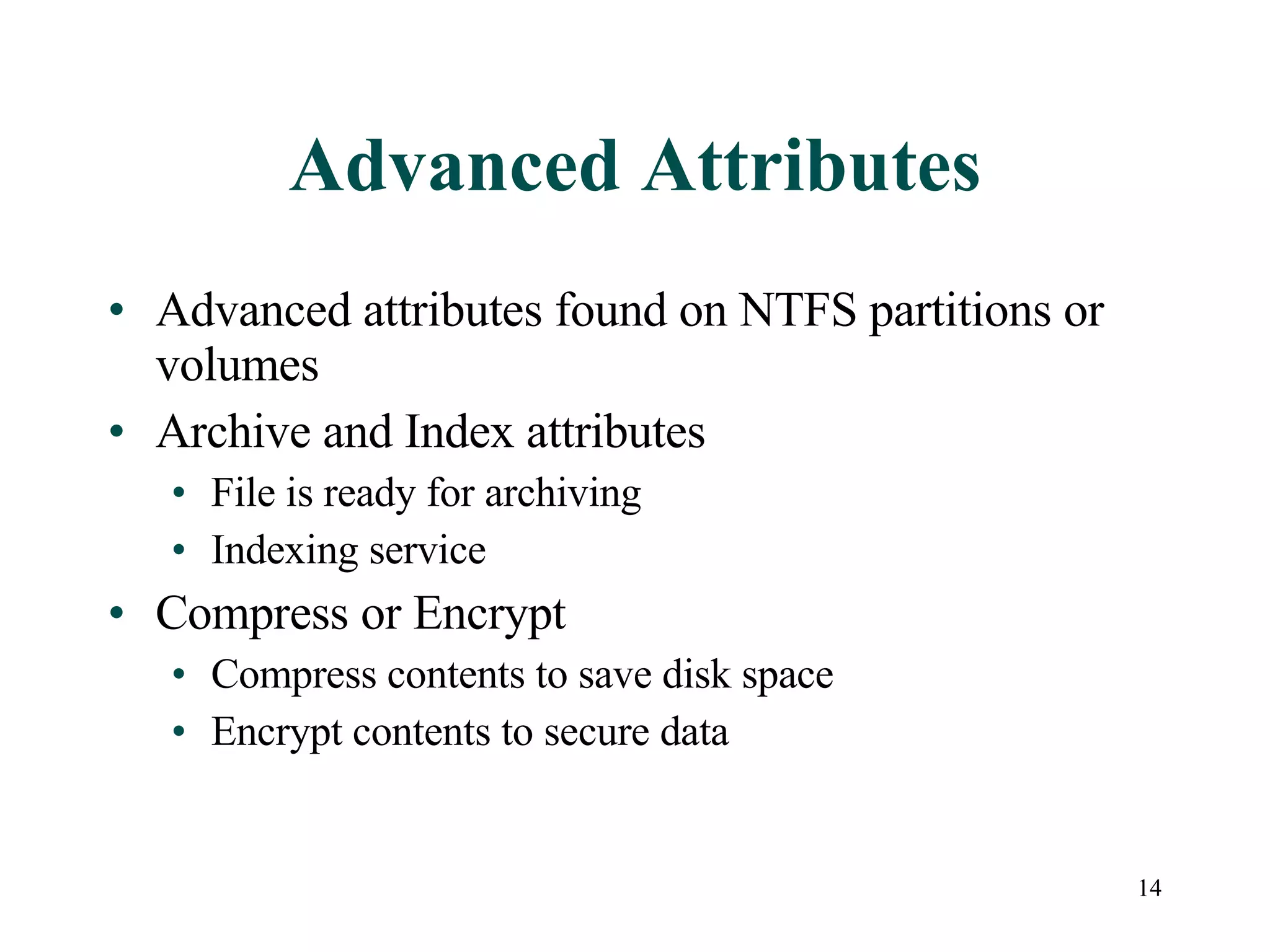
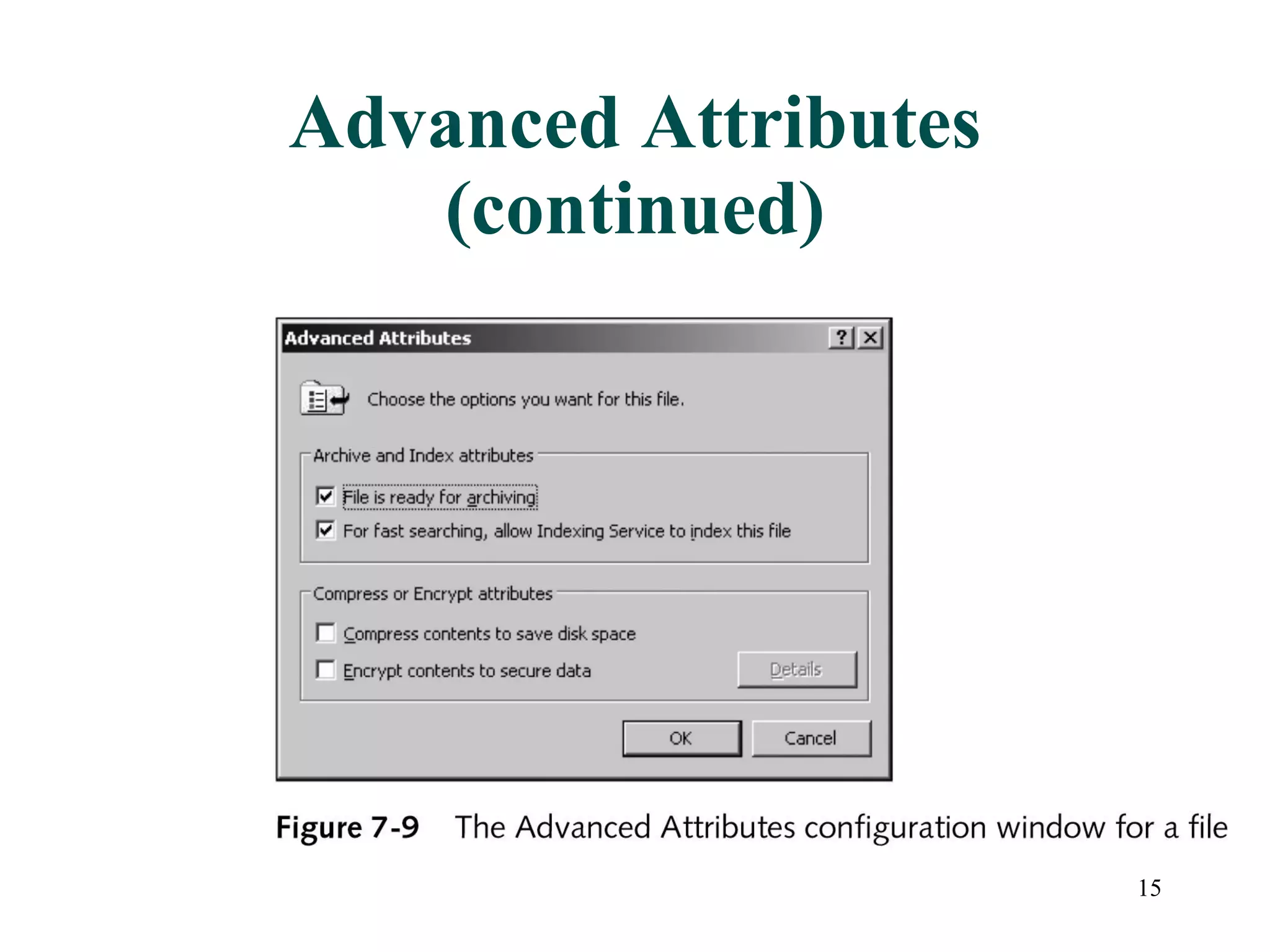
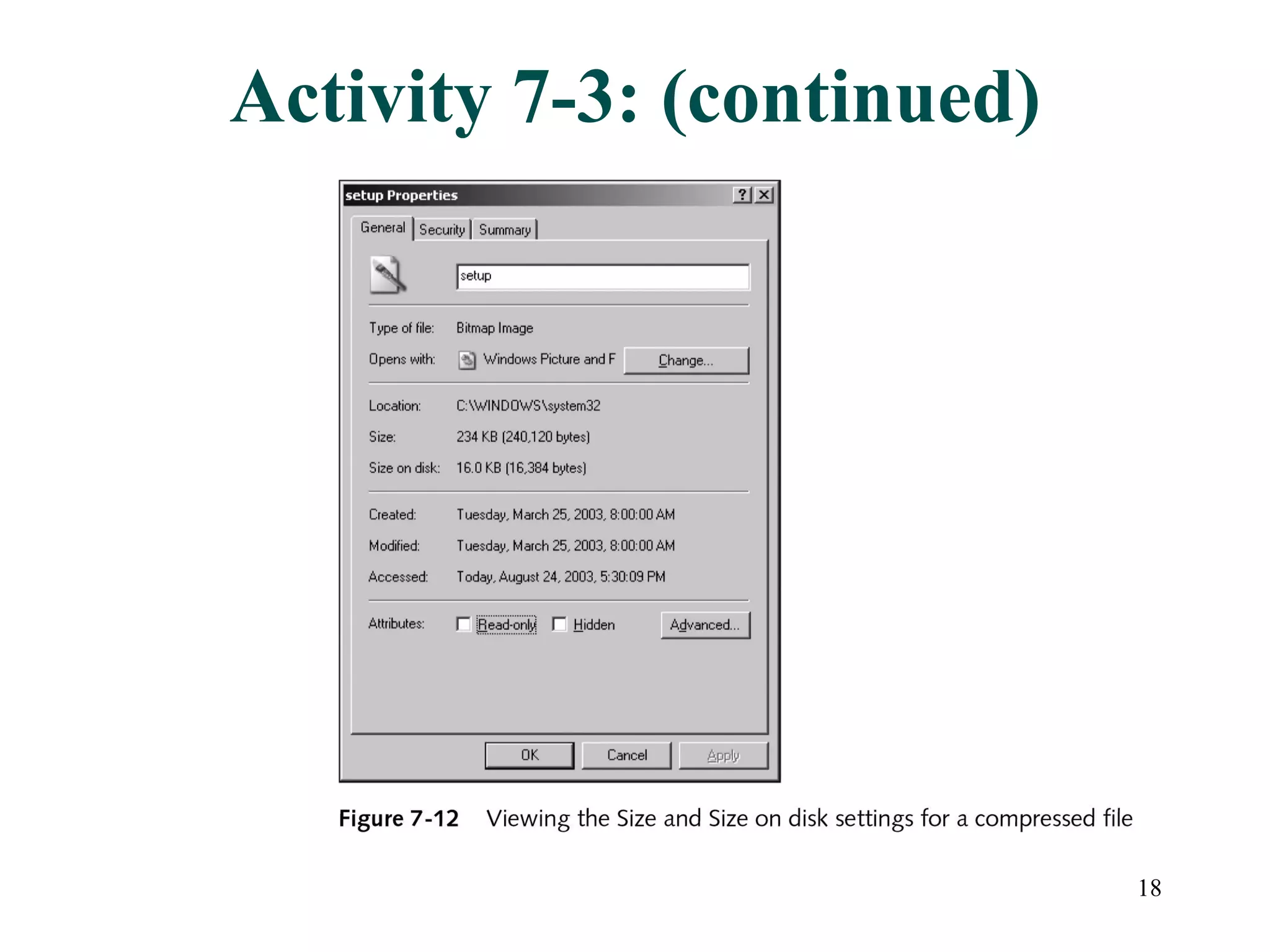
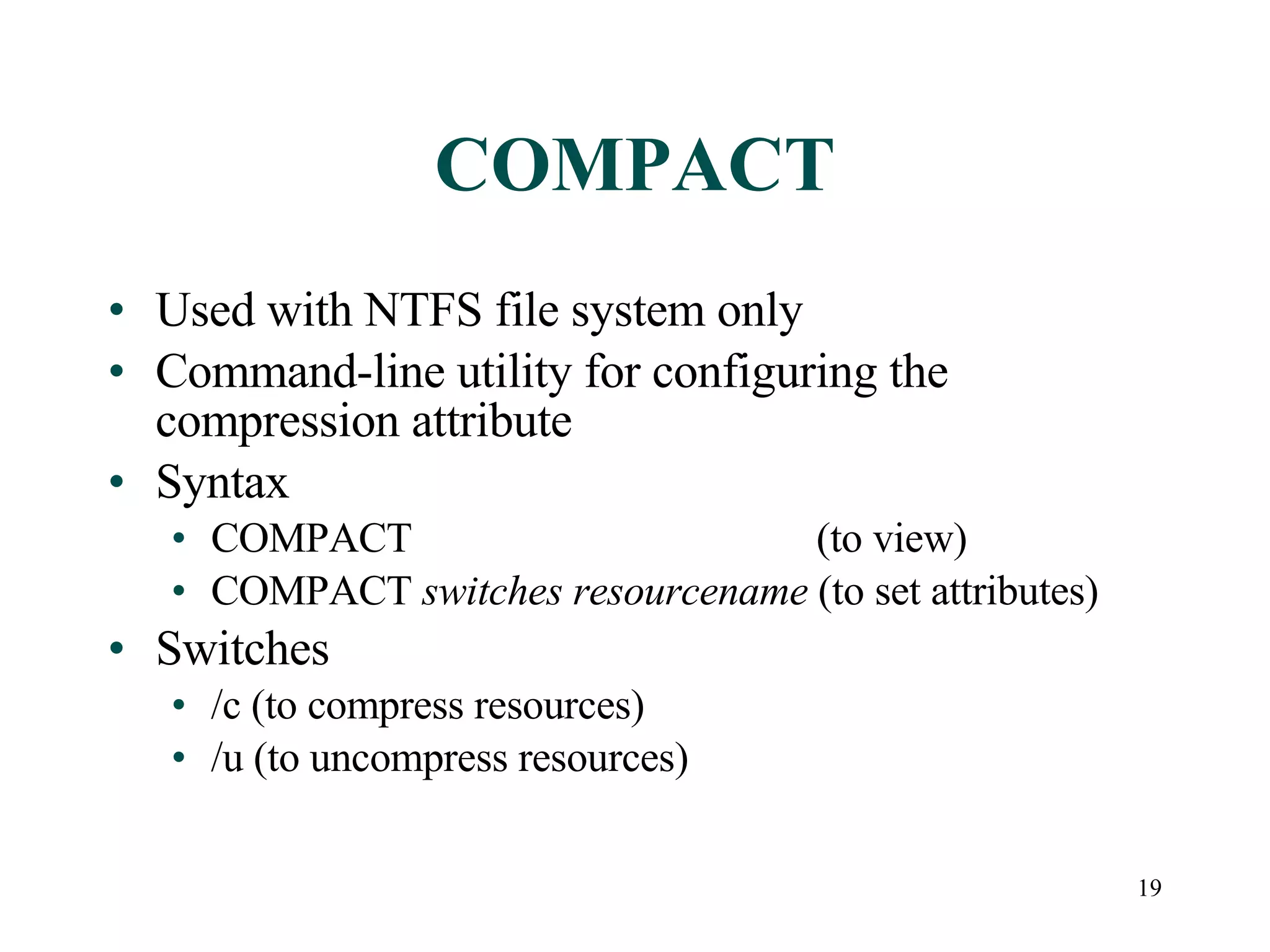
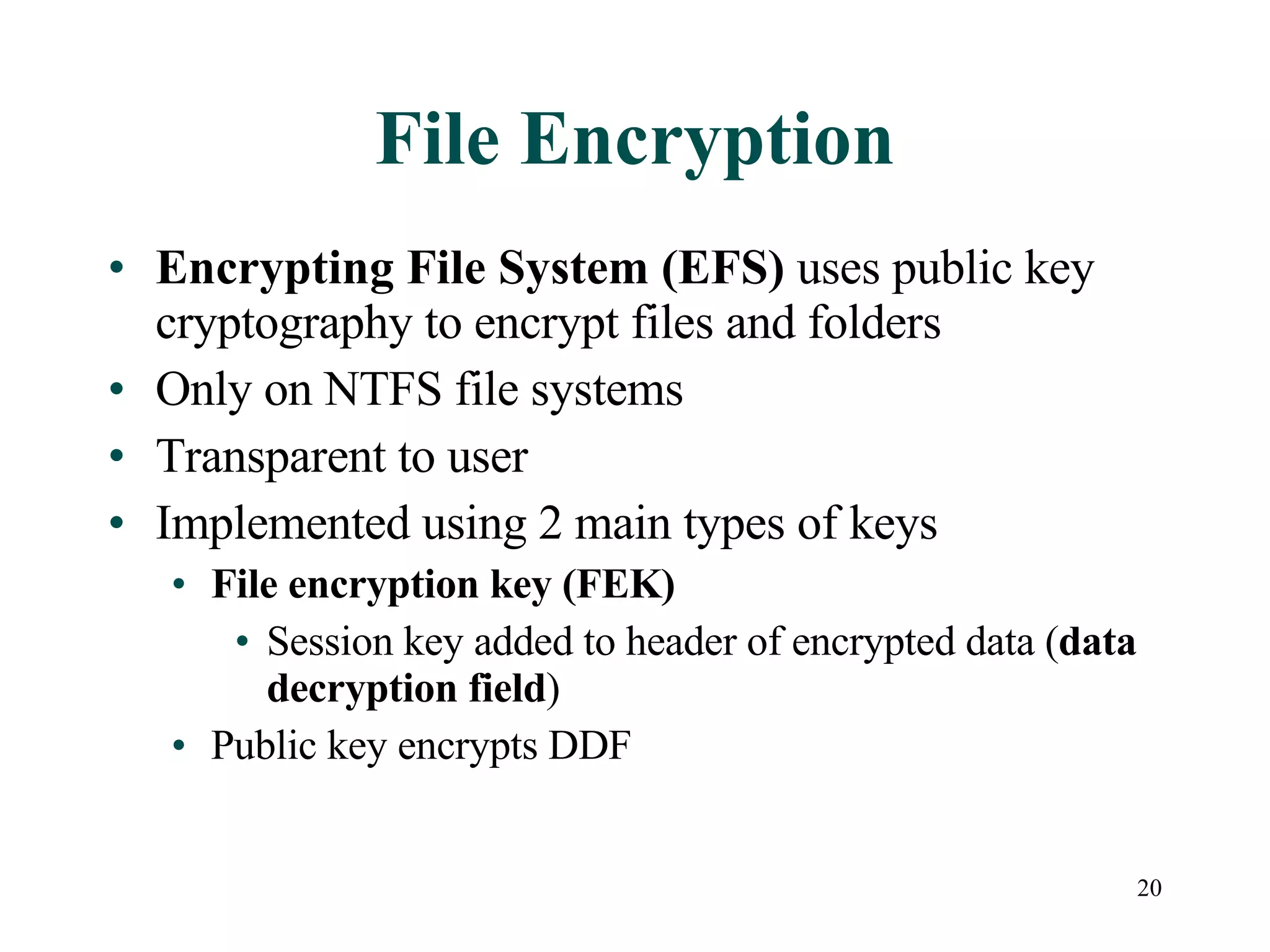
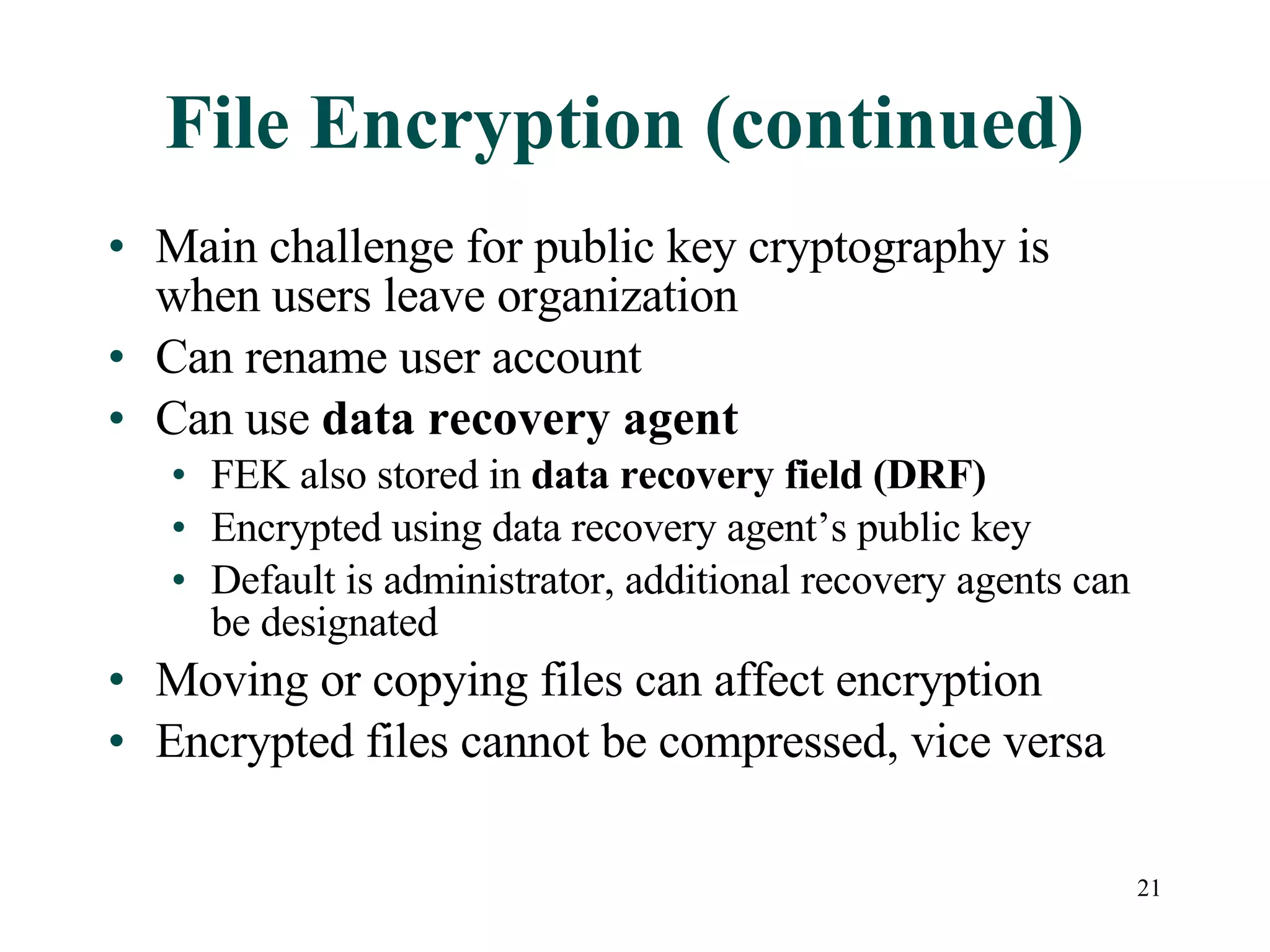
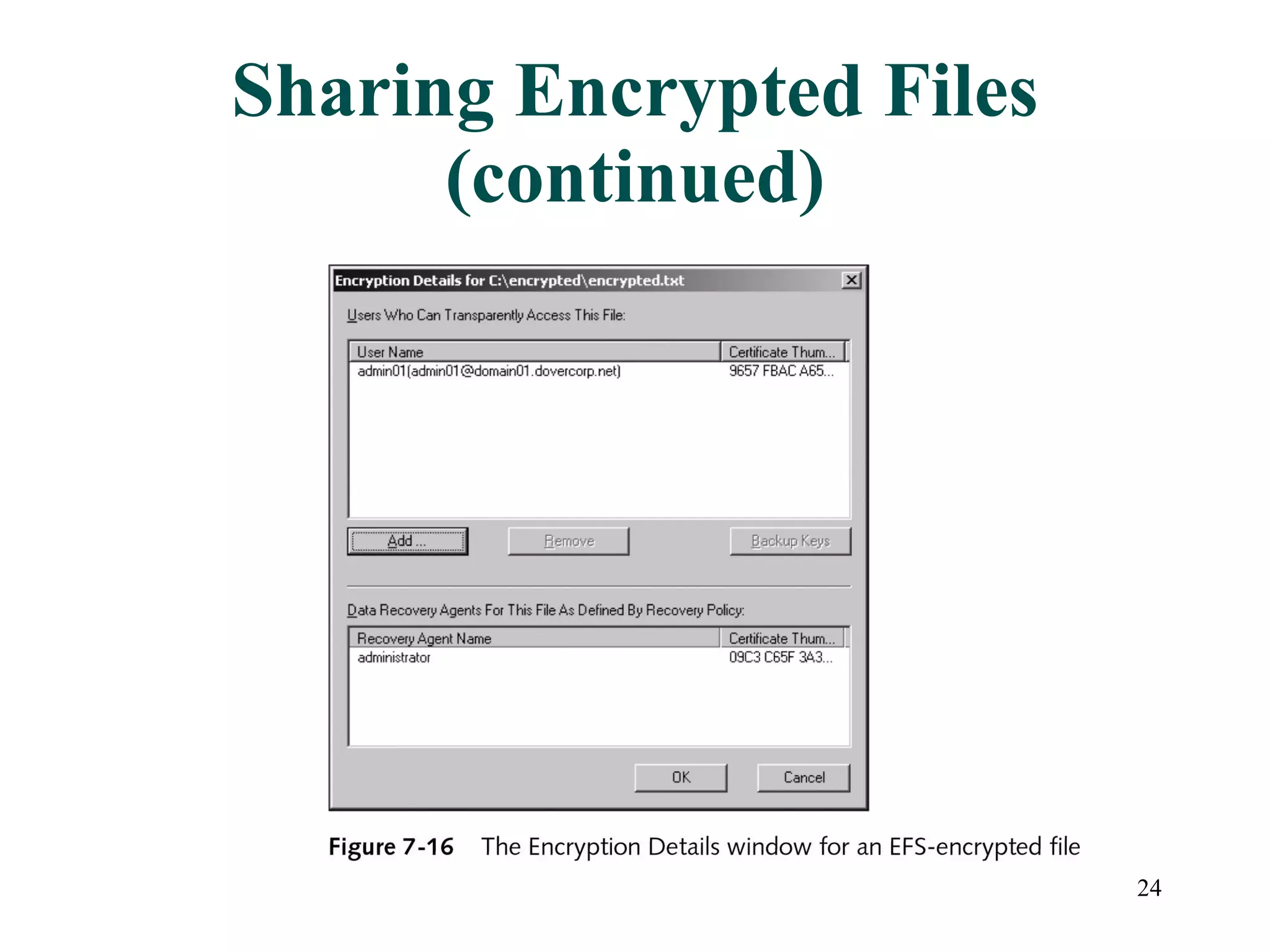
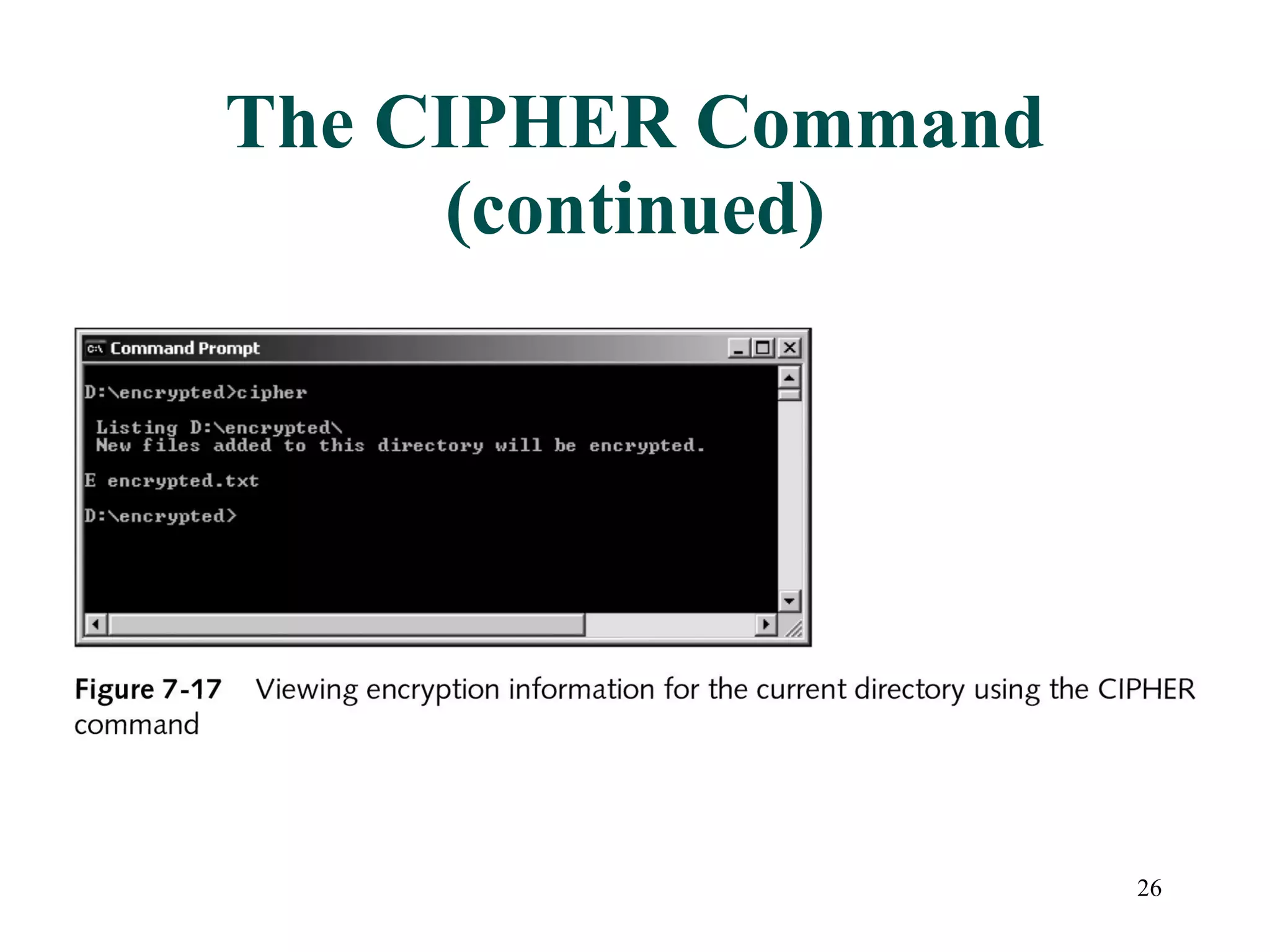
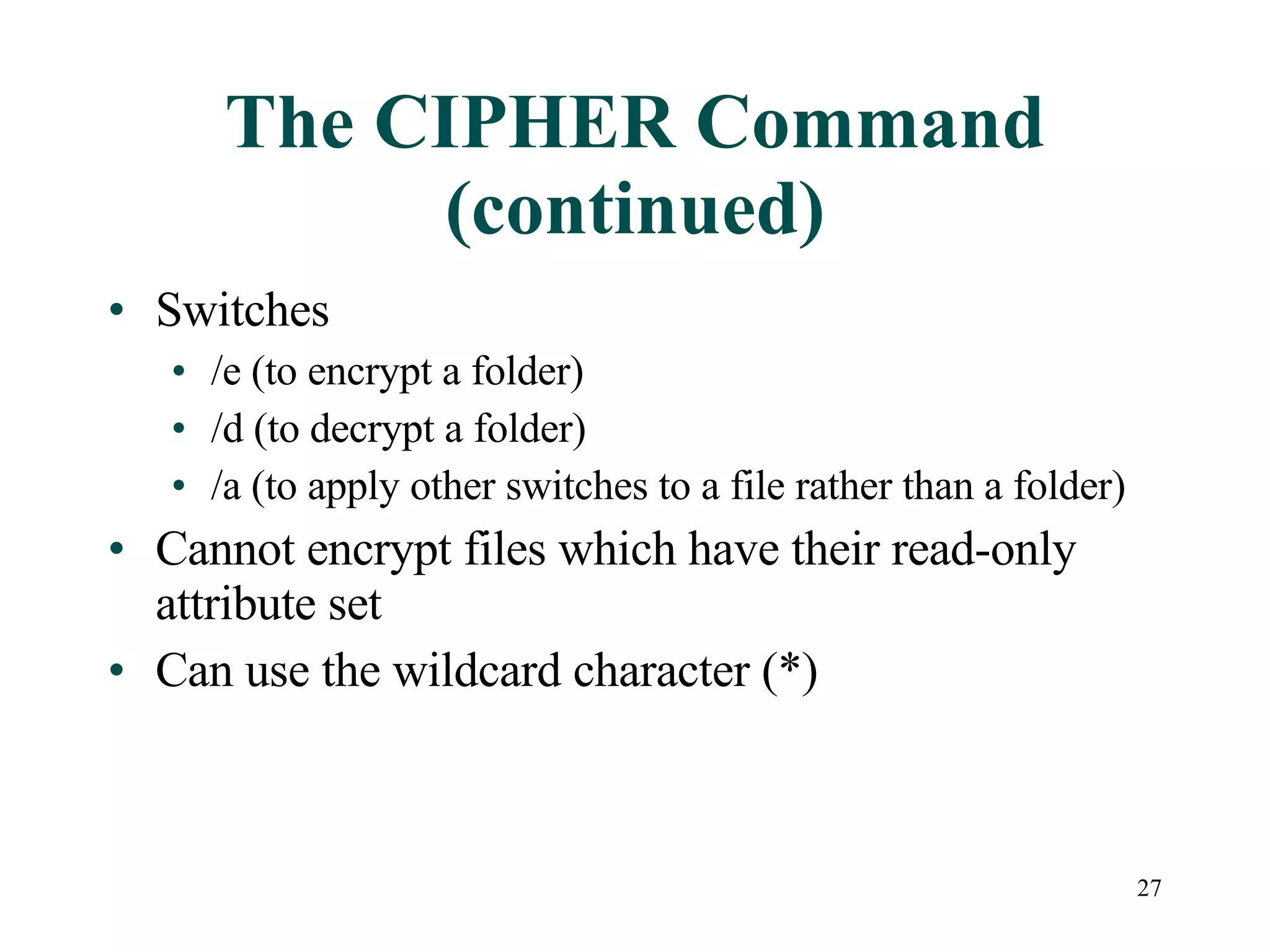
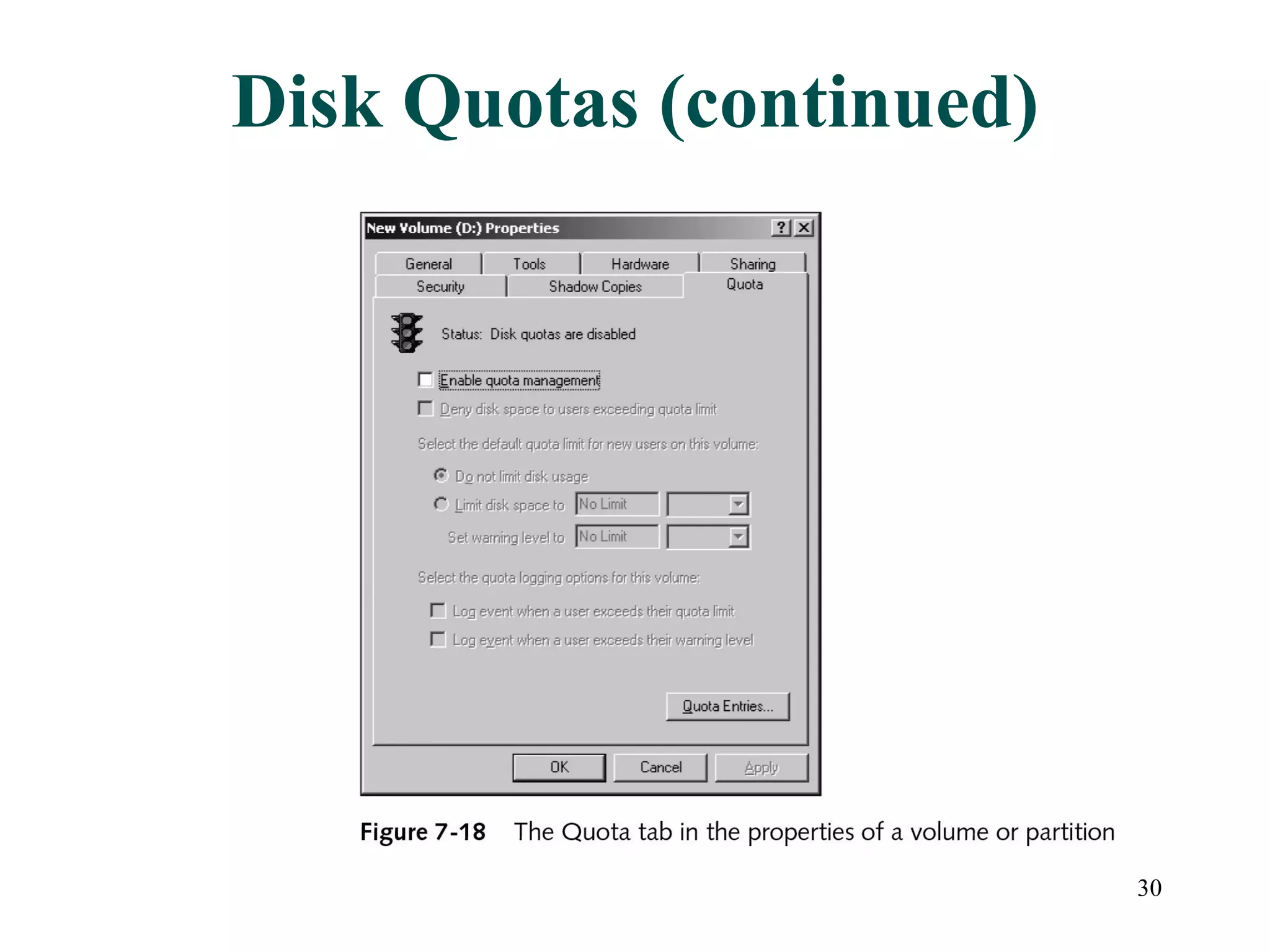
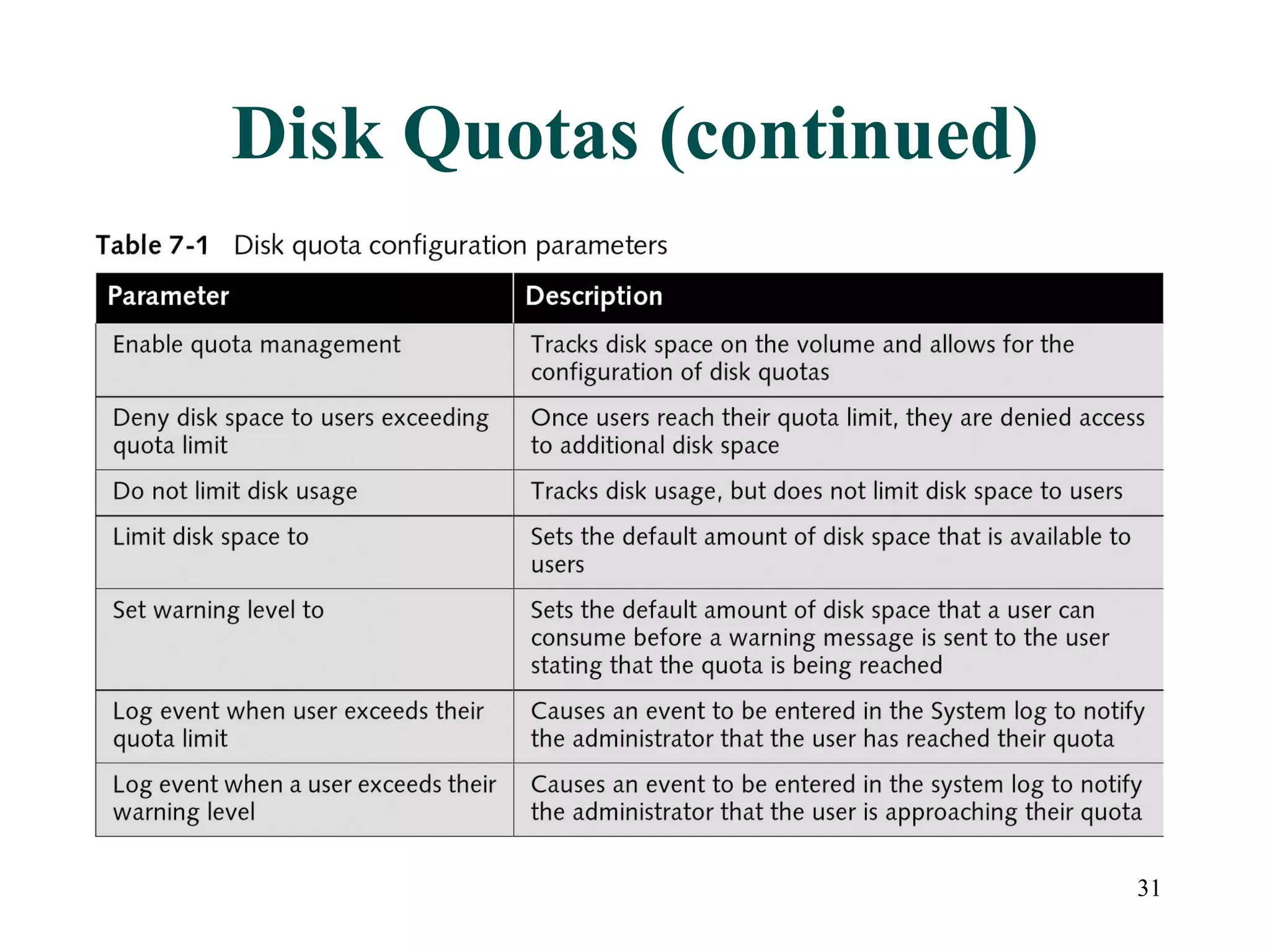
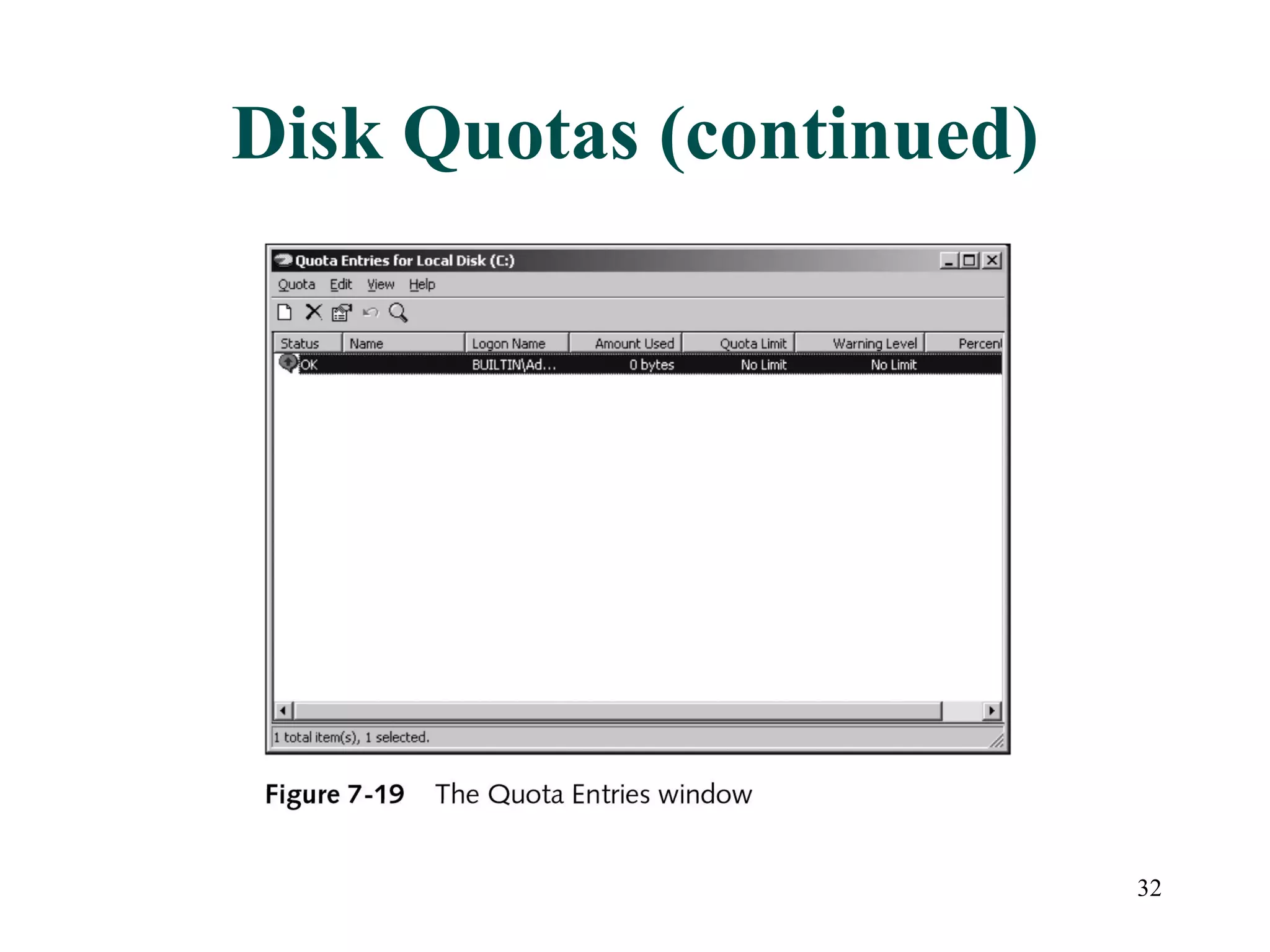
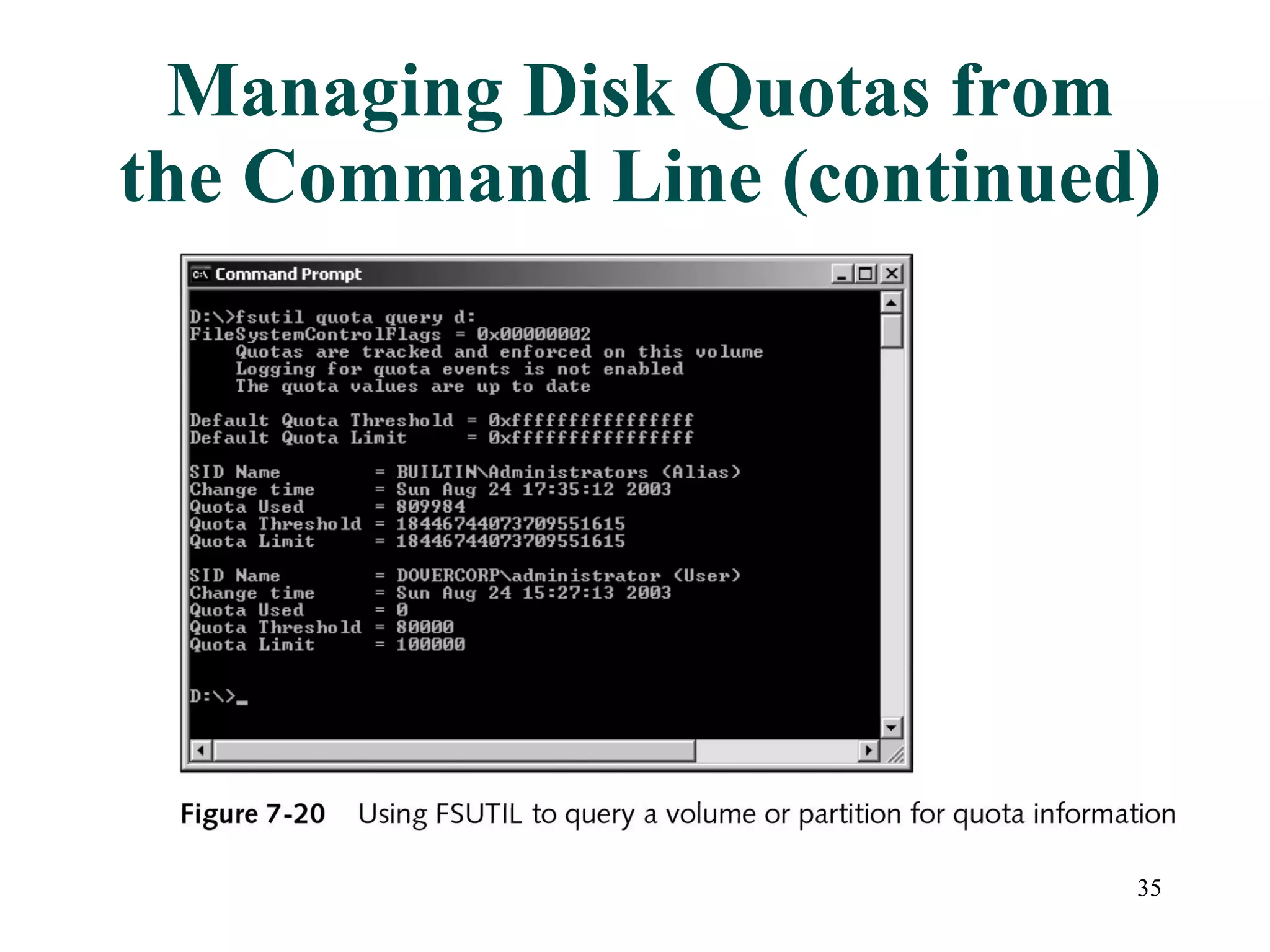
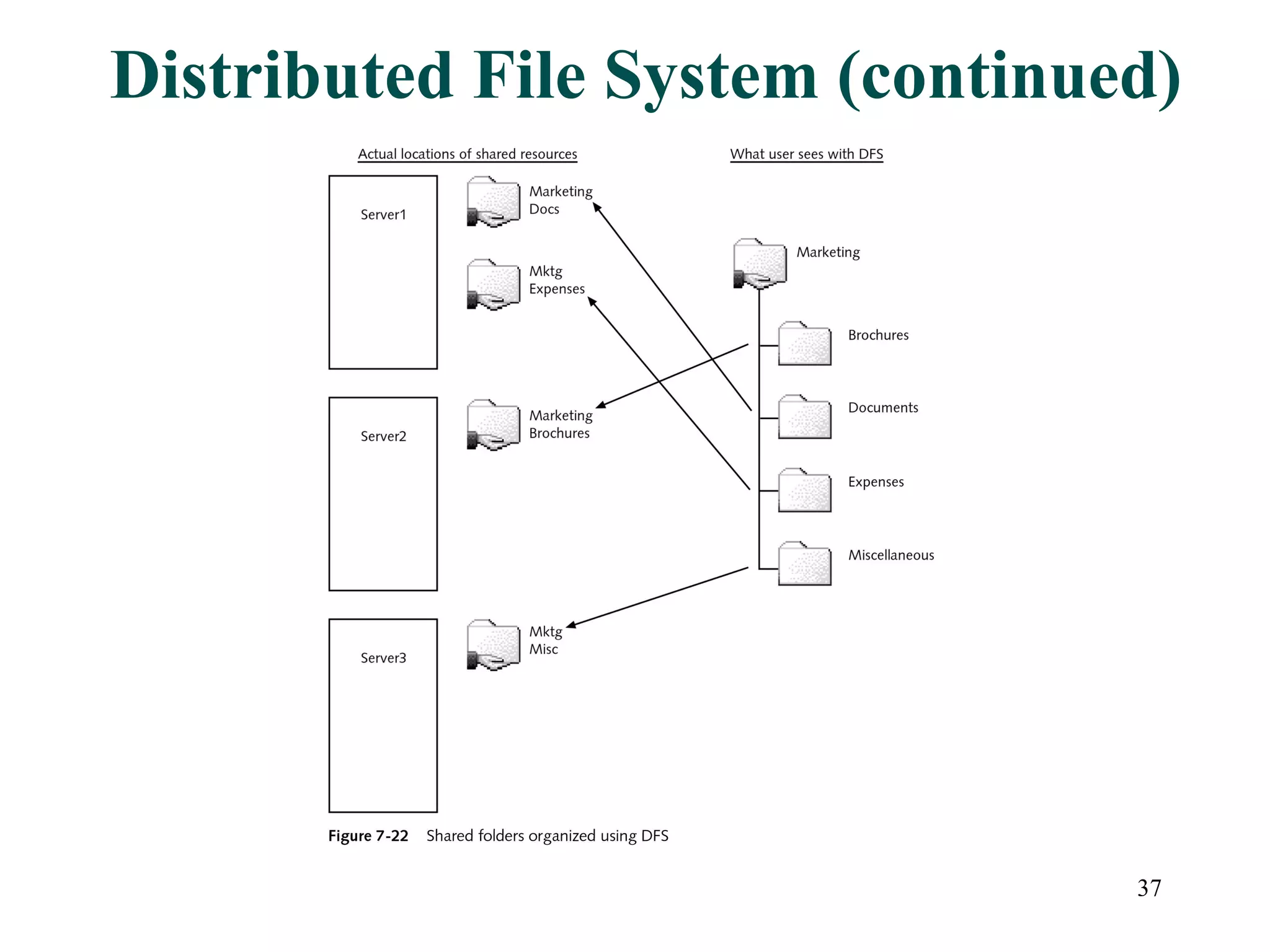
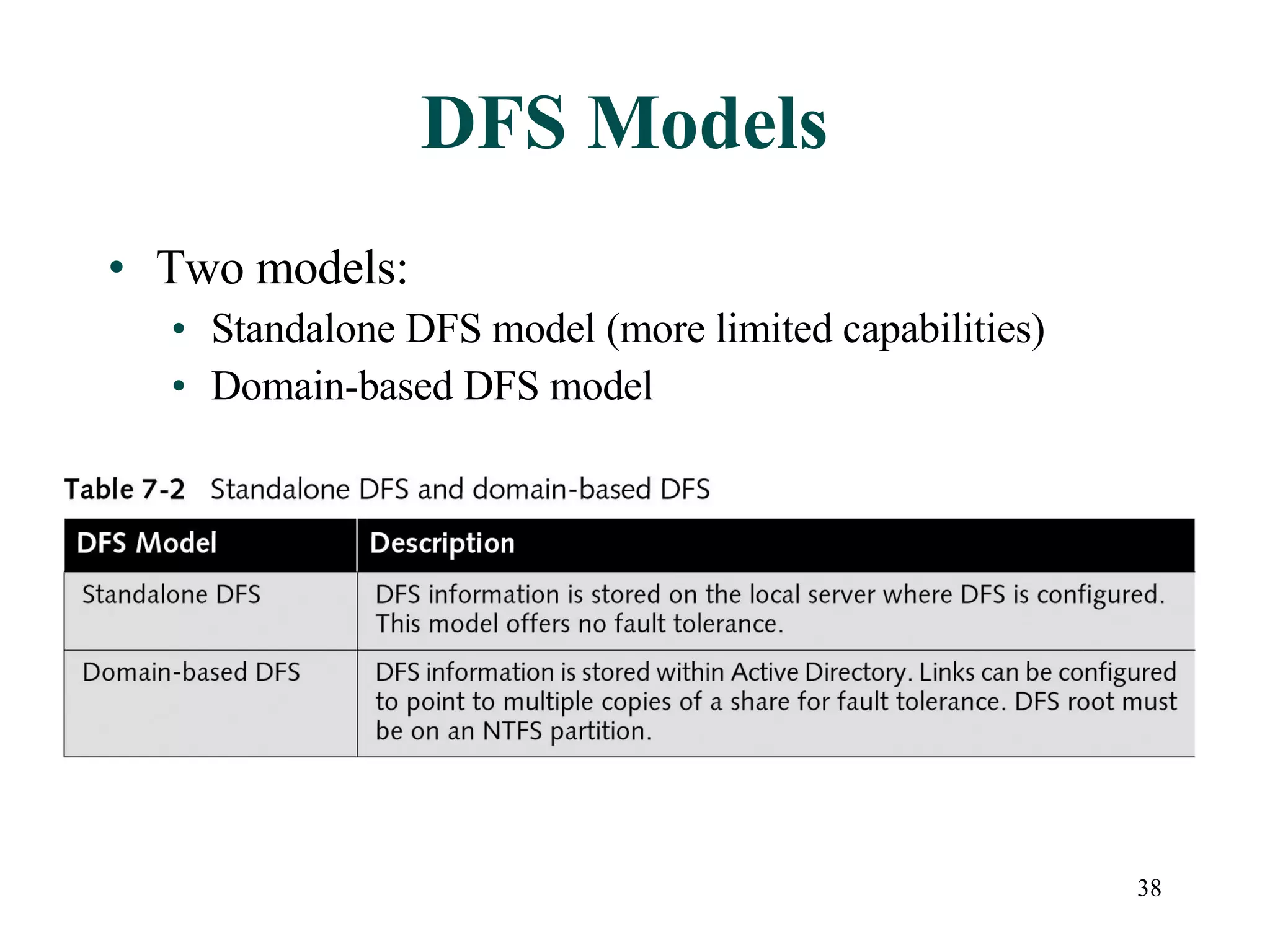
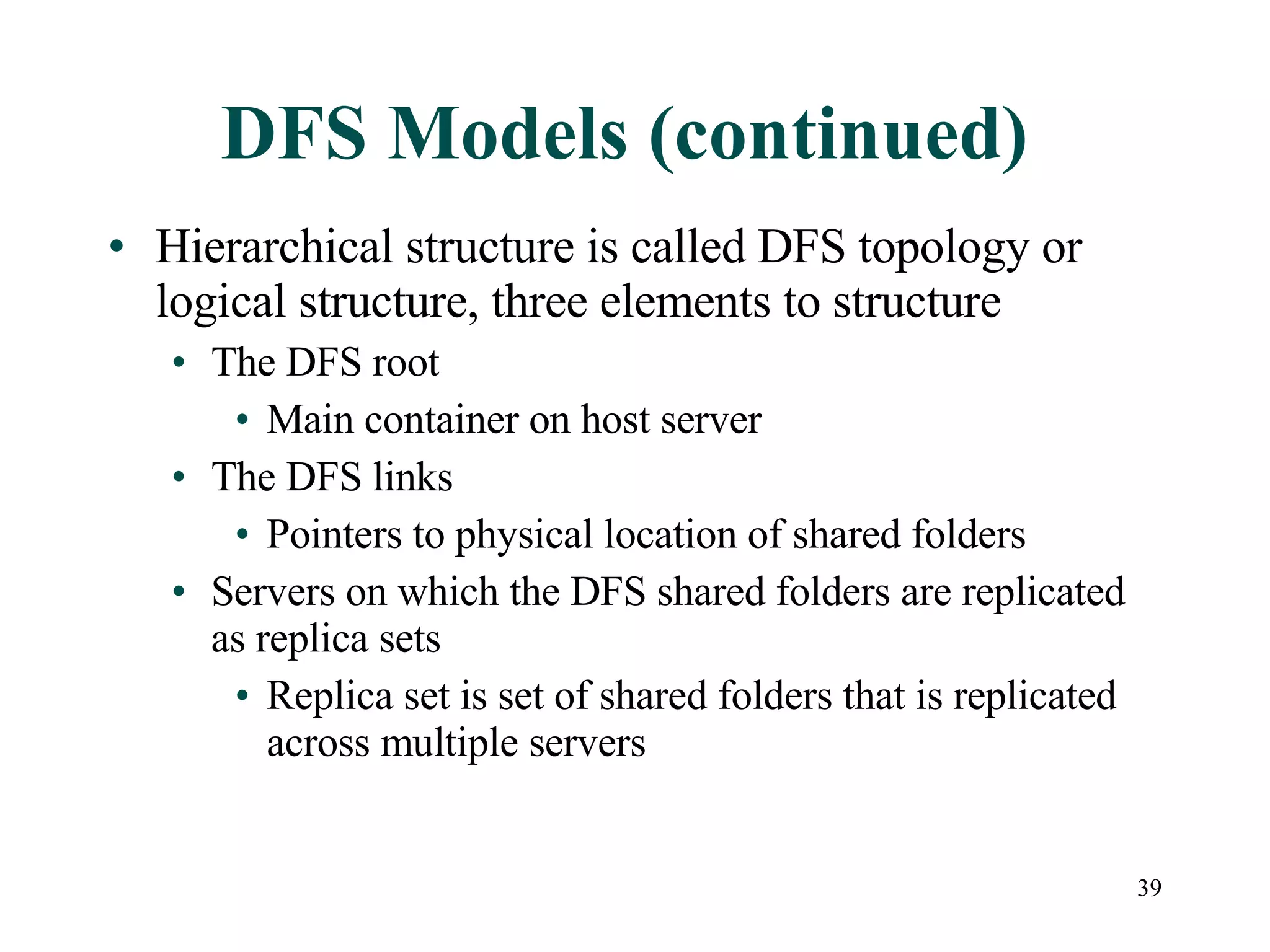
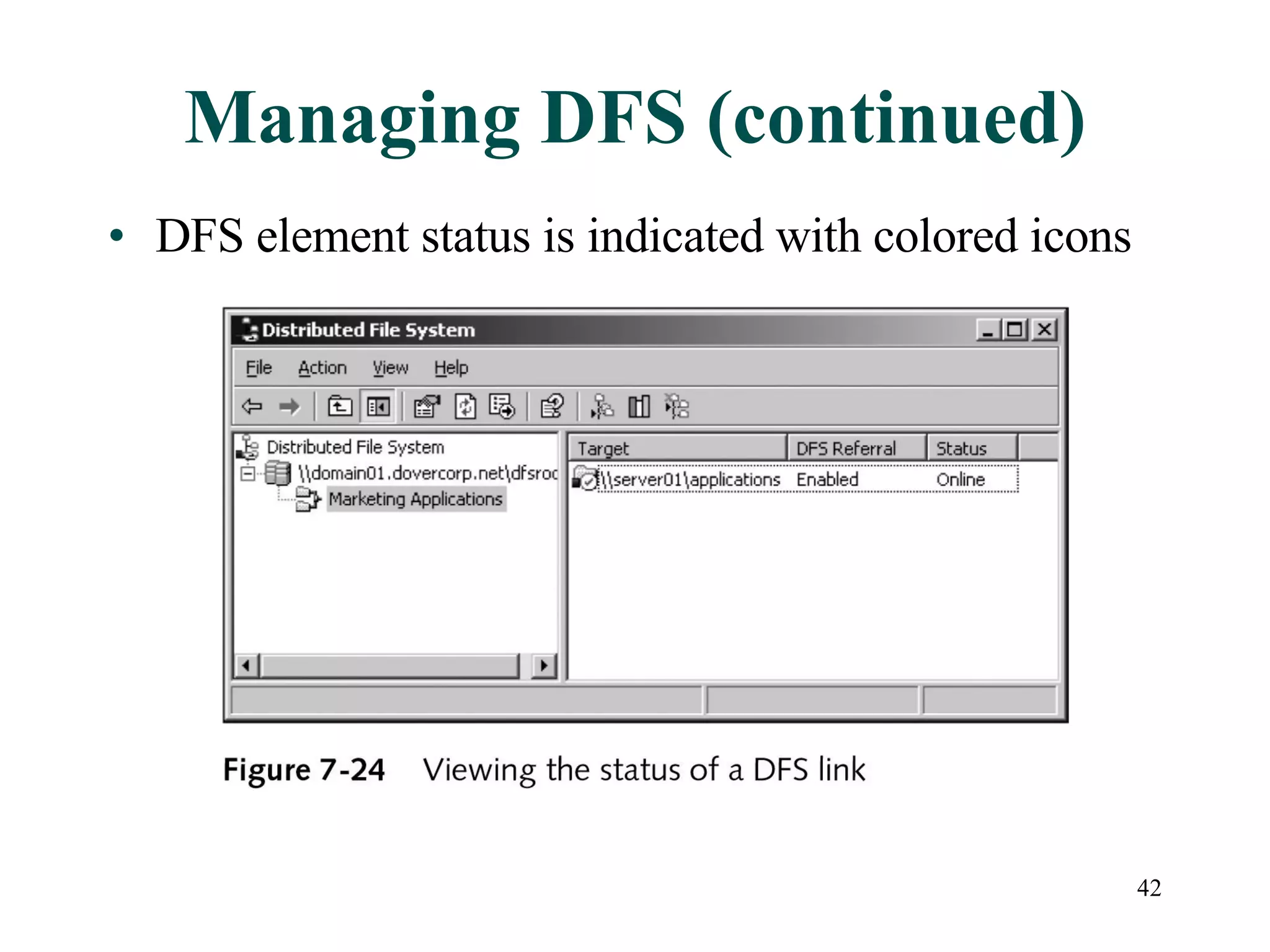
This document discusses advanced file system management in a Microsoft Windows Server 2003 environment. It covers configuring file and folder attributes such as read-only, archive, system, and hidden. Advanced attributes like compression and encryption are also described. Disk quotas and the Distributed File System (DFS) are explained as ways to manage storage and share files across multiple servers. A series of activities are provided to demonstrate viewing, setting, and managing these file system features using Windows Explorer and command line utilities.