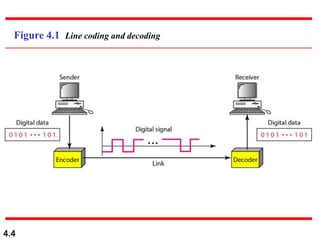
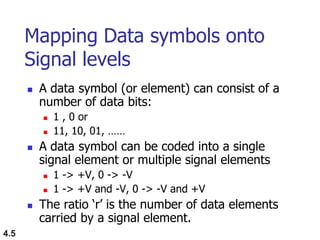
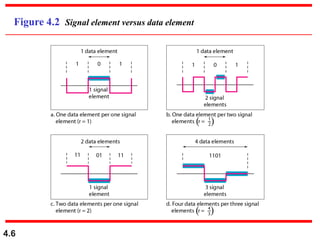
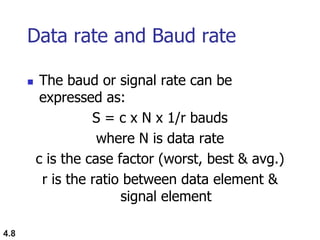
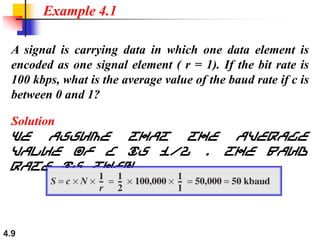
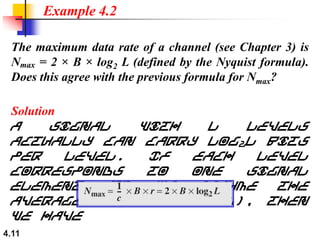
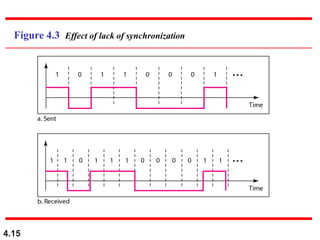
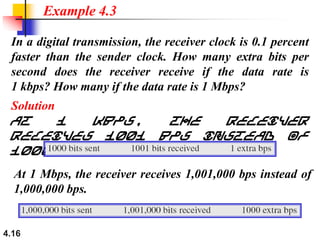
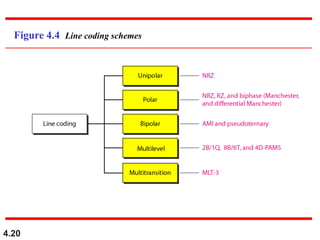
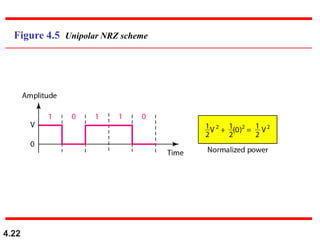
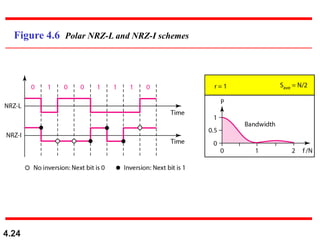
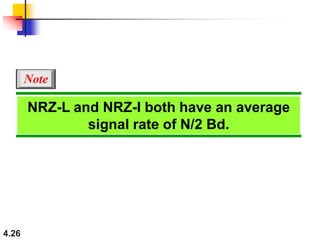
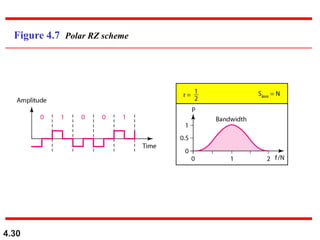
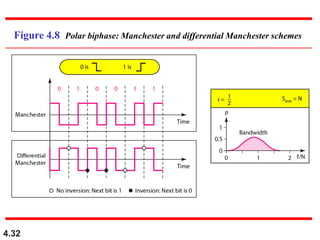
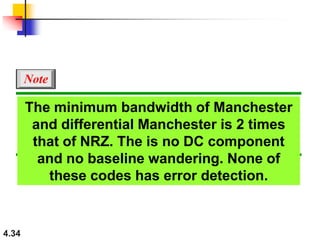
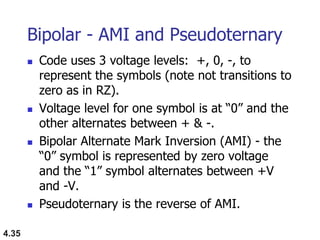
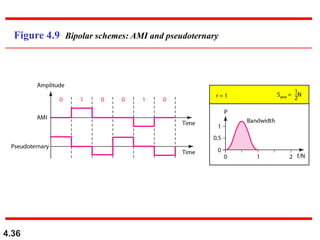
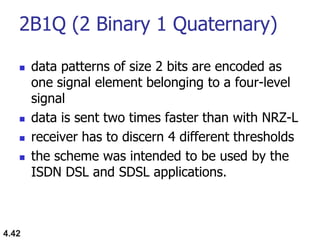
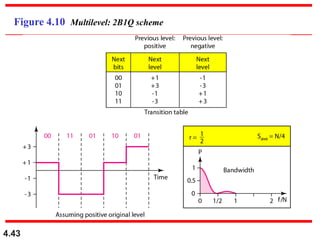
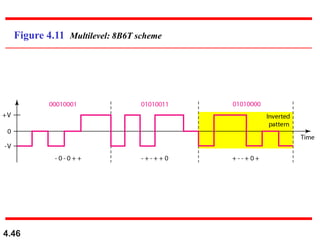
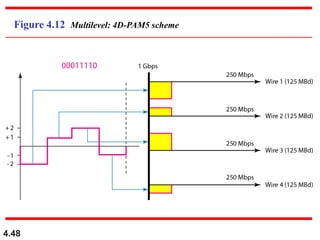
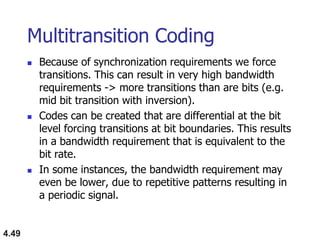
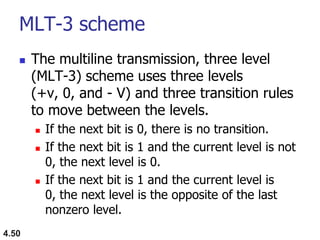
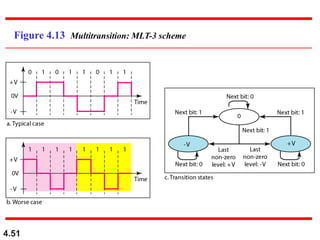
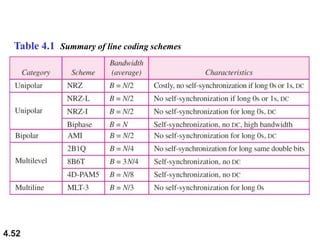
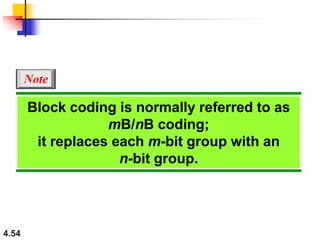
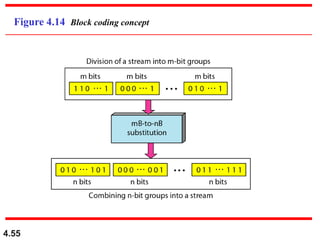
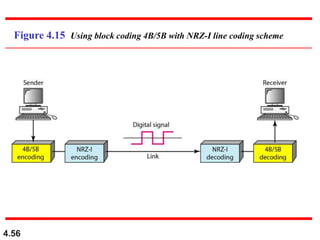
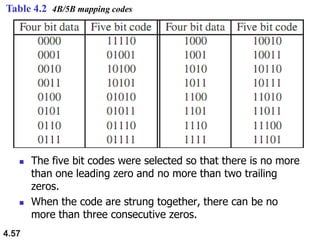
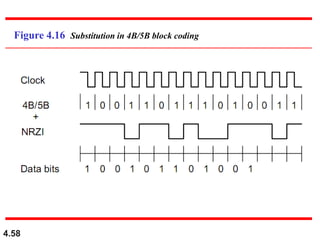
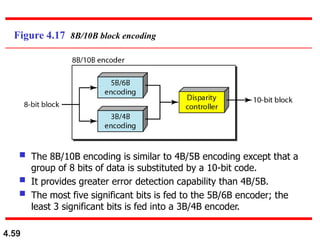
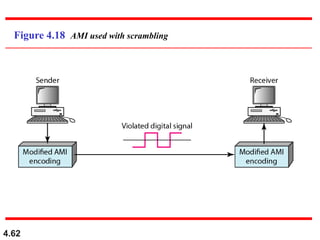
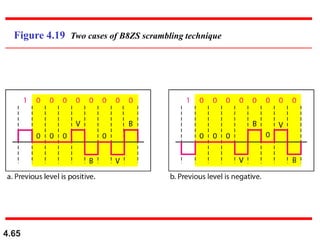
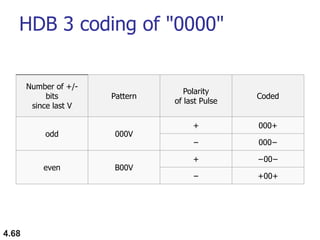
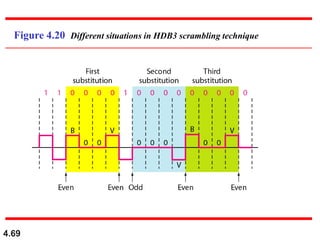
This document discusses digital transmission techniques for converting digital data into digital signals. It covers line coding, which maps binary data bits to signal levels. Common line coding schemes include NRZ, RZ, Manchester, and AMI. Multilevel coding schemes are also introduced, which encode multiple data bits as a single signal element to increase data rates. Key considerations for line coding include baseline wandering, DC components, self-synchronization, error detection, noise immunity, and complexity. Worked examples calculate baud rates and minimum bandwidths for different schemes.