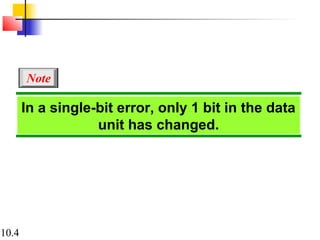
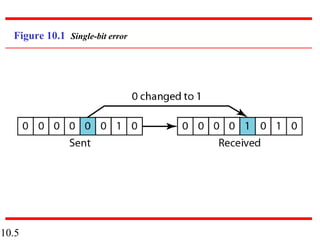
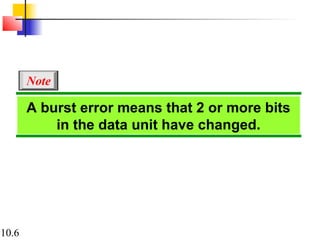
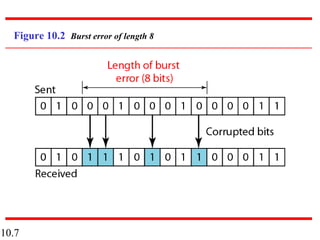
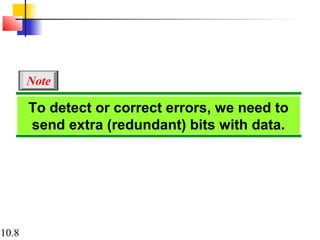
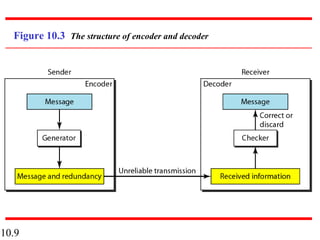
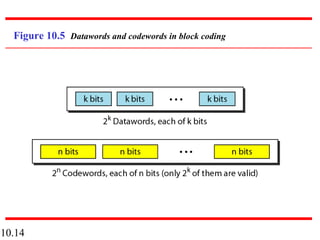
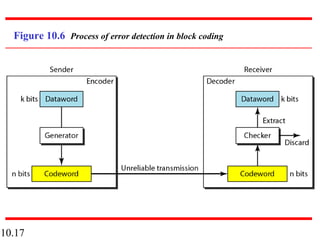
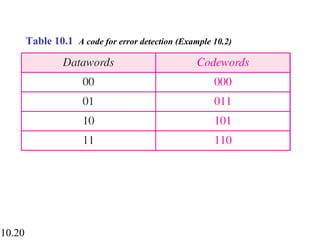
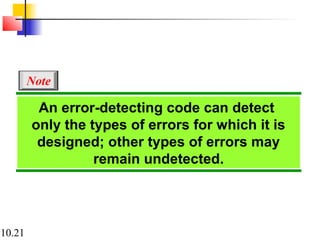
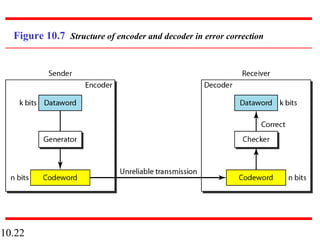
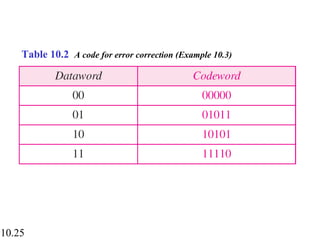
This document discusses error detection and correction in digital communications. It begins by explaining the different types of errors that can occur like single-bit and burst errors. It then introduces the concept of adding redundant bits to detect or correct errors. The document focuses on block coding, where the message is divided into blocks and redundant bits are added to each block to form a codeword. Error detection codes are able to detect errors but not correct them, while error correction codes can correct errors by encoding extra redundant bits. Examples of block codes for error detection and correction are provided to illustrate these concepts.