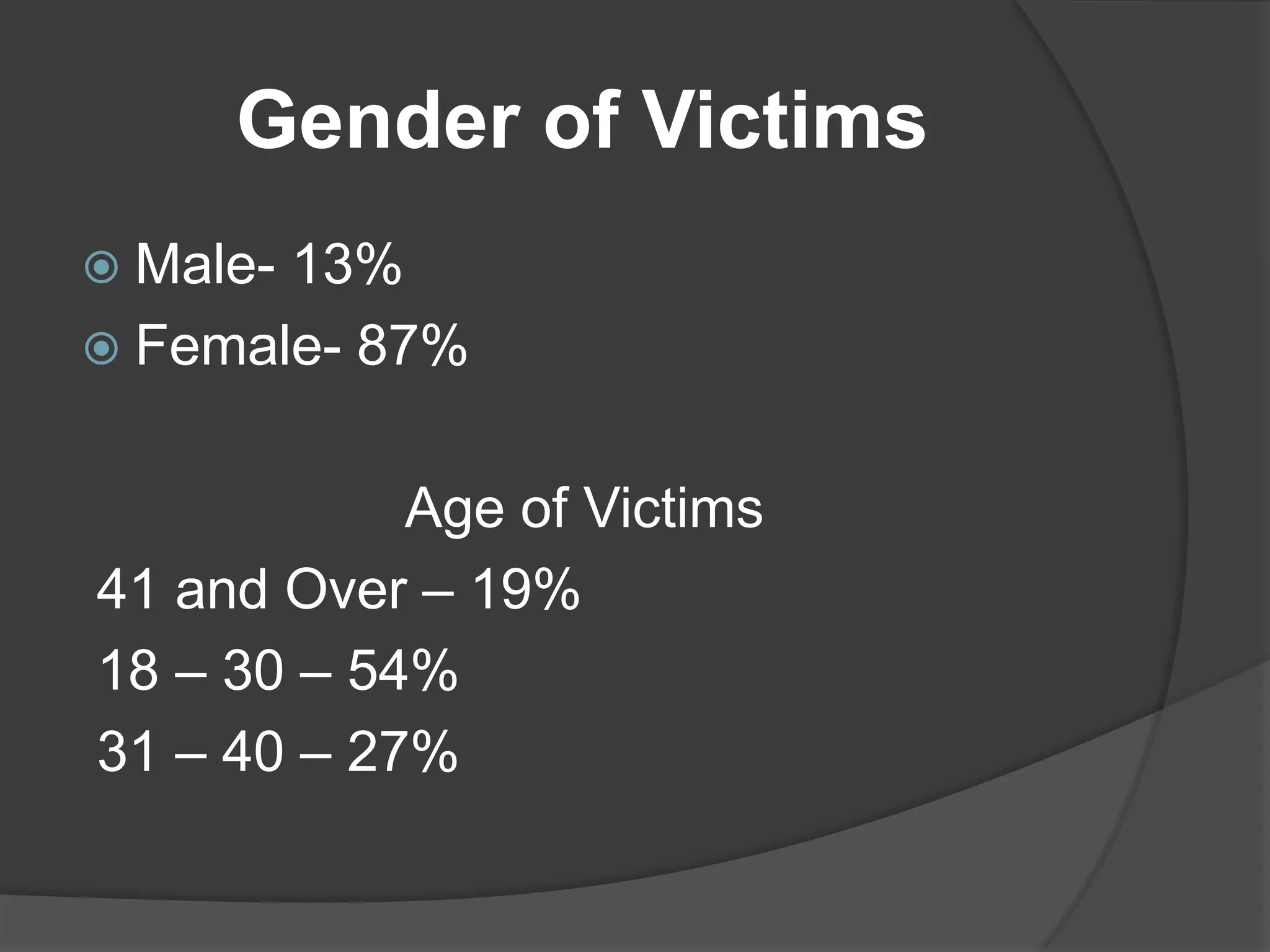
Cyberstalking is defined as the repeated use of electronic communication devices like the internet or email to harass or threaten an individual or group. Females between the ages of 18-30 are most likely to be victims of cyberstalking. Common forms of cyberstalking include threatening emails, defamatory posts on message boards or websites, harassment in chat rooms or through instant messages, and creation of fake user profiles pretending to be the victim. Cyberstalking can have serious psychological effects on victims like changes in sleep and eating, nightmares, anxiety, and fear for their safety. All 50 U.S. states have laws against cyberstalking to protect victims.