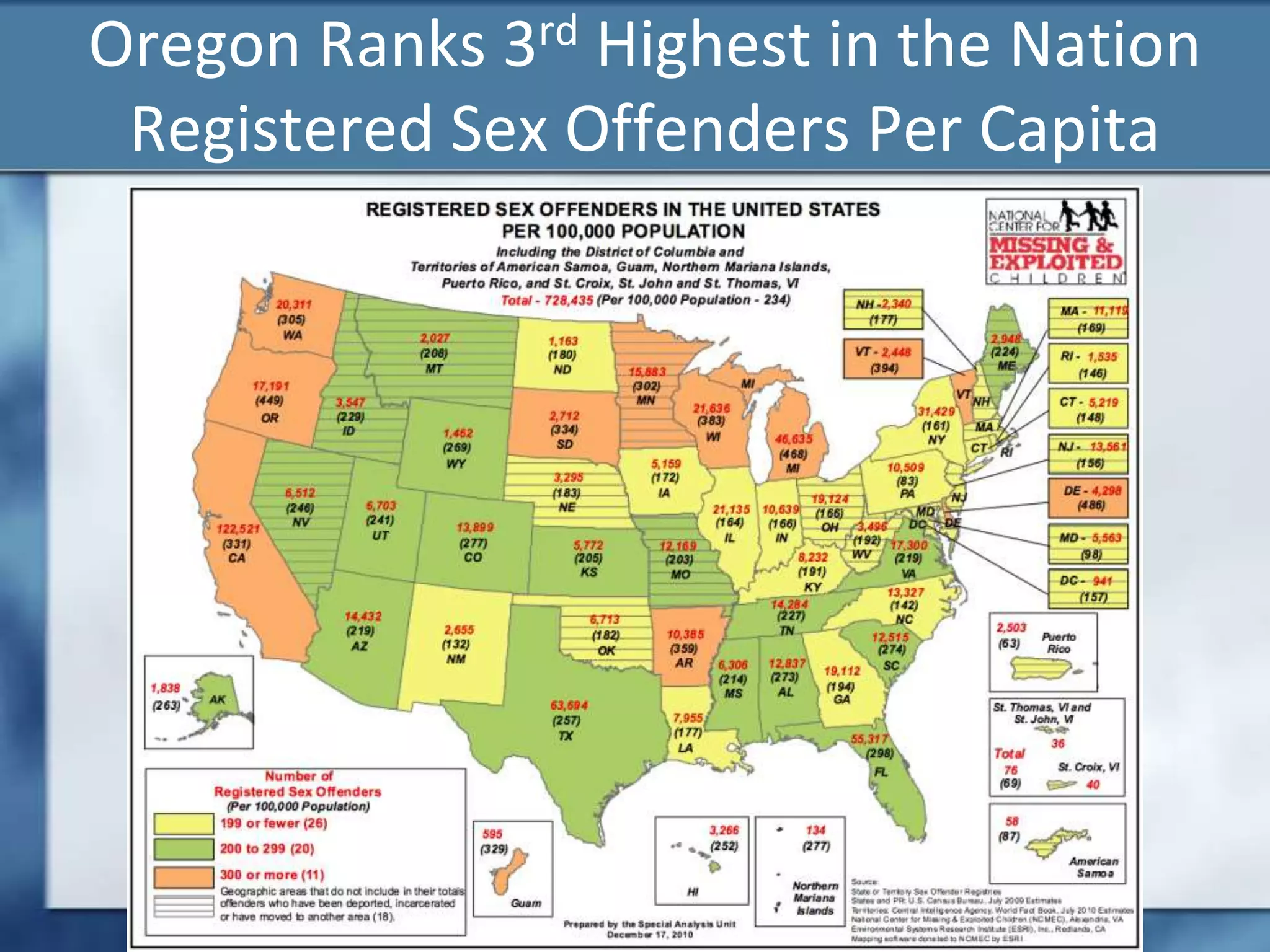
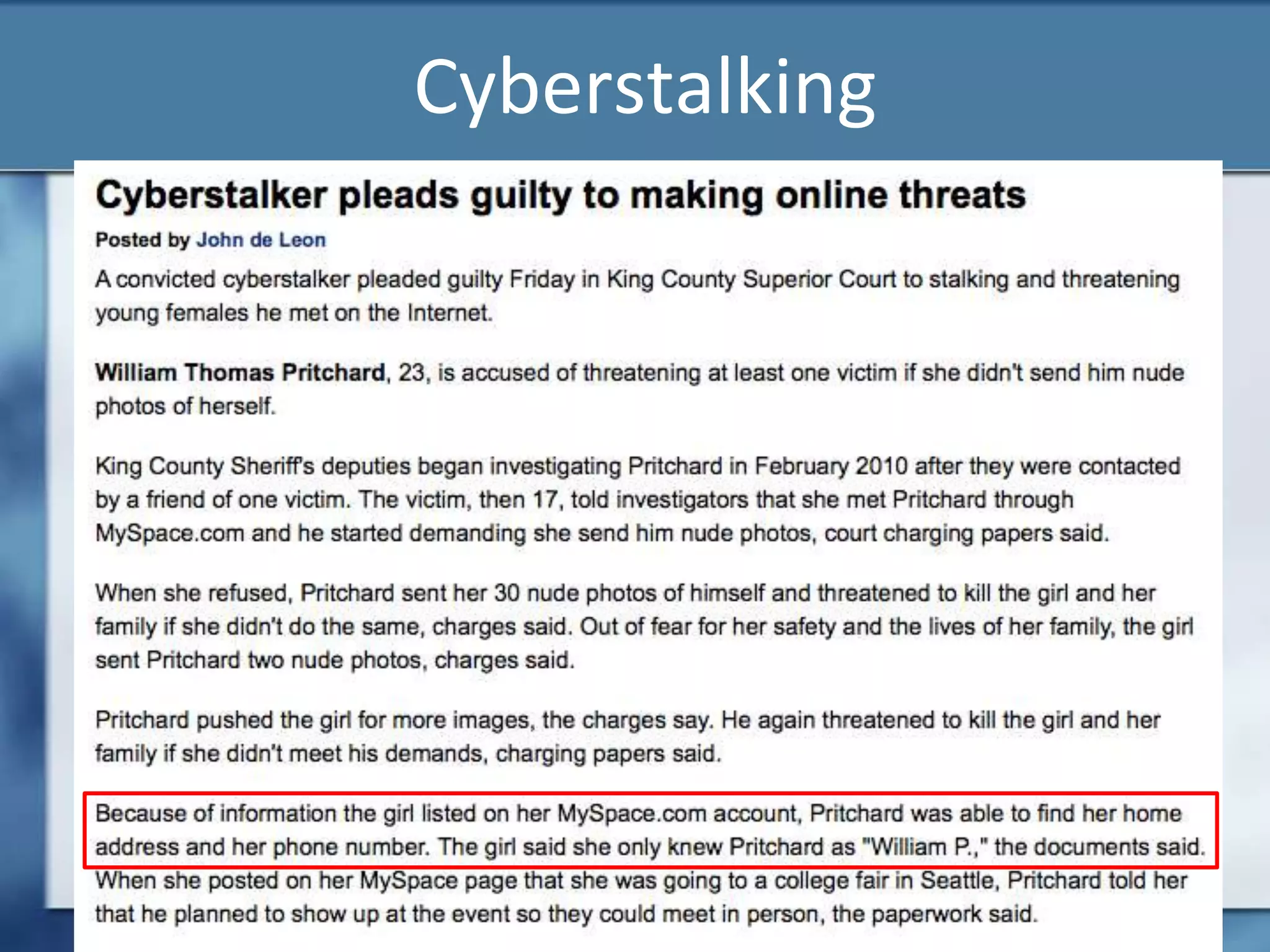
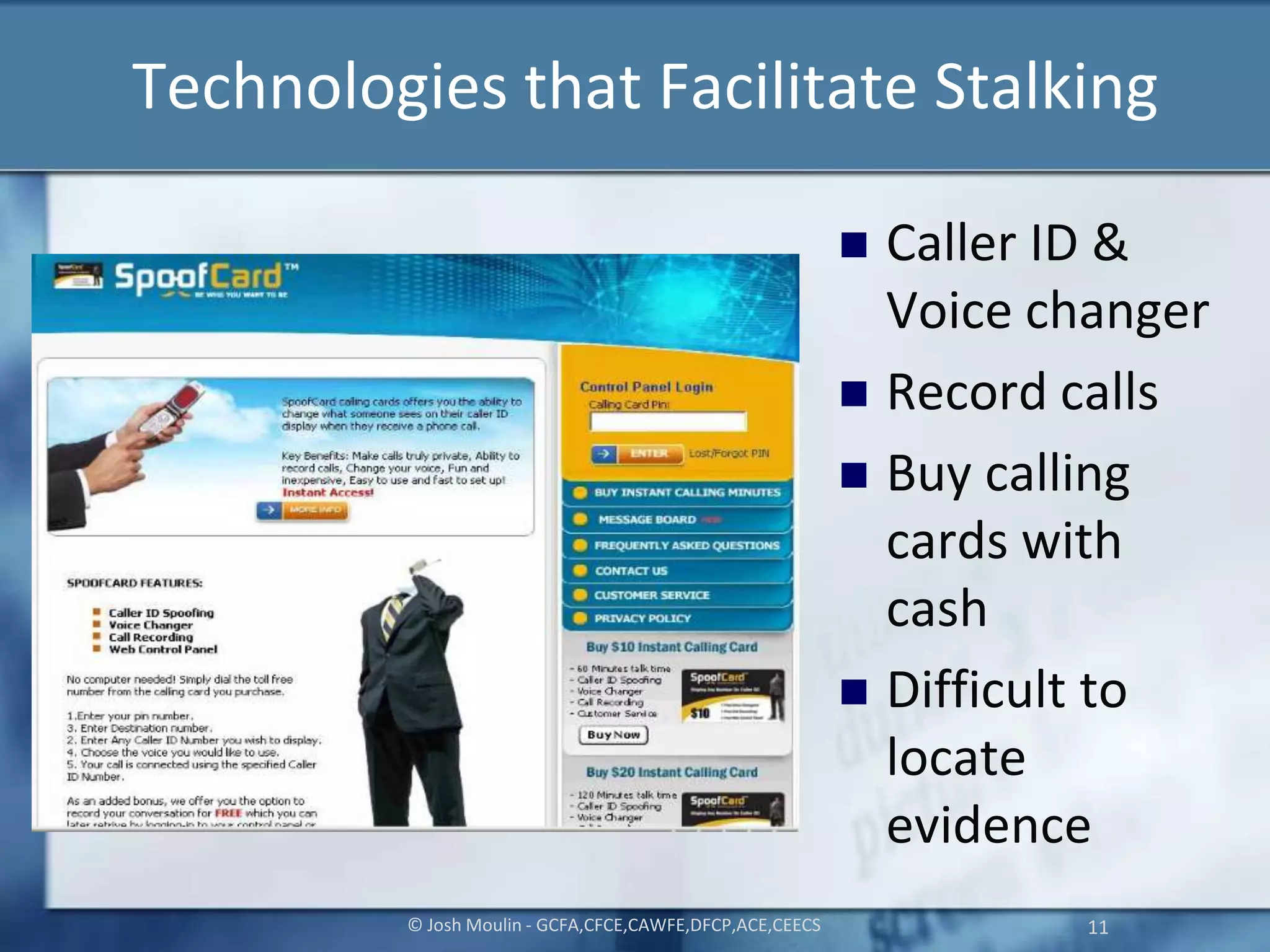
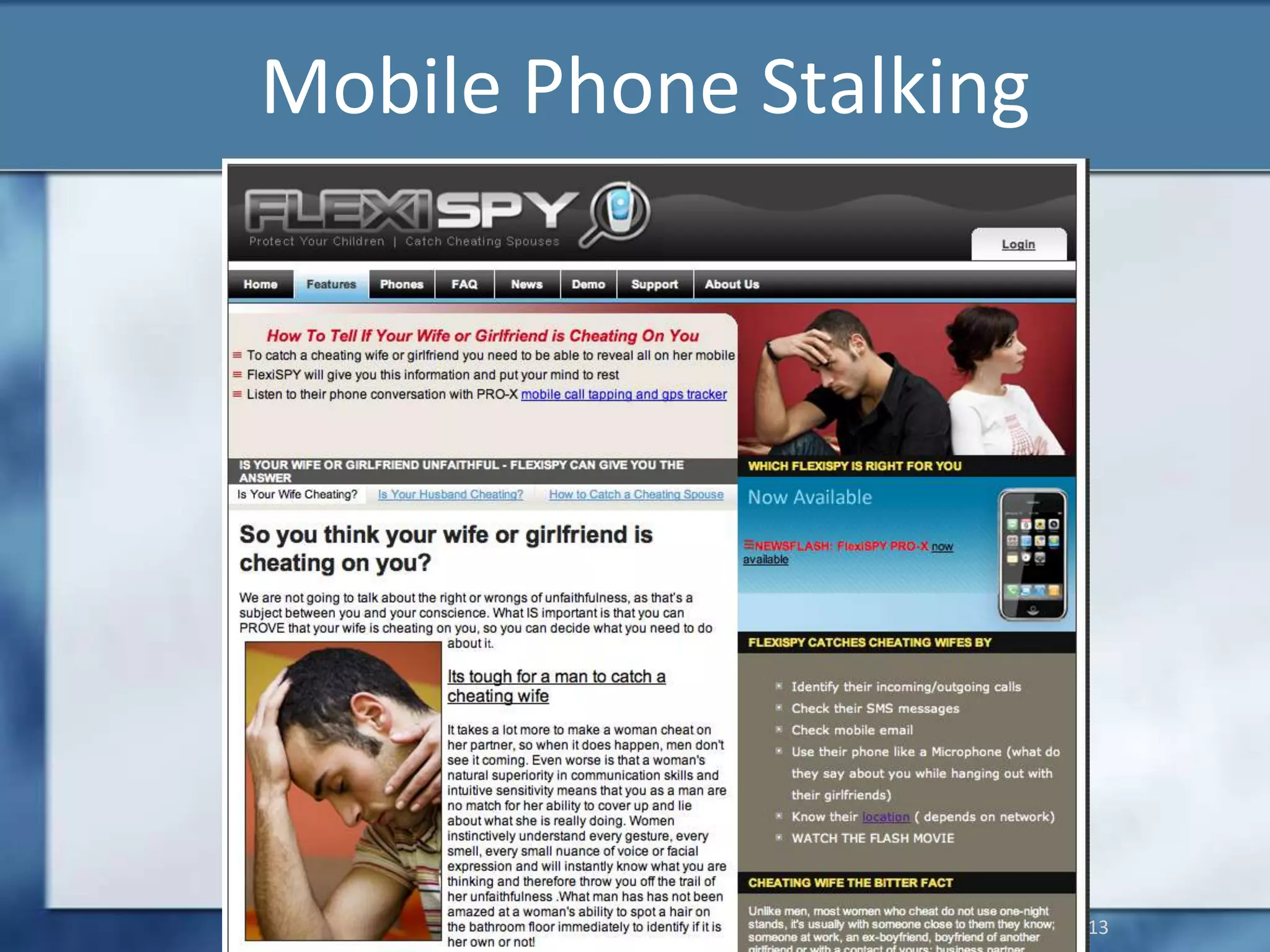
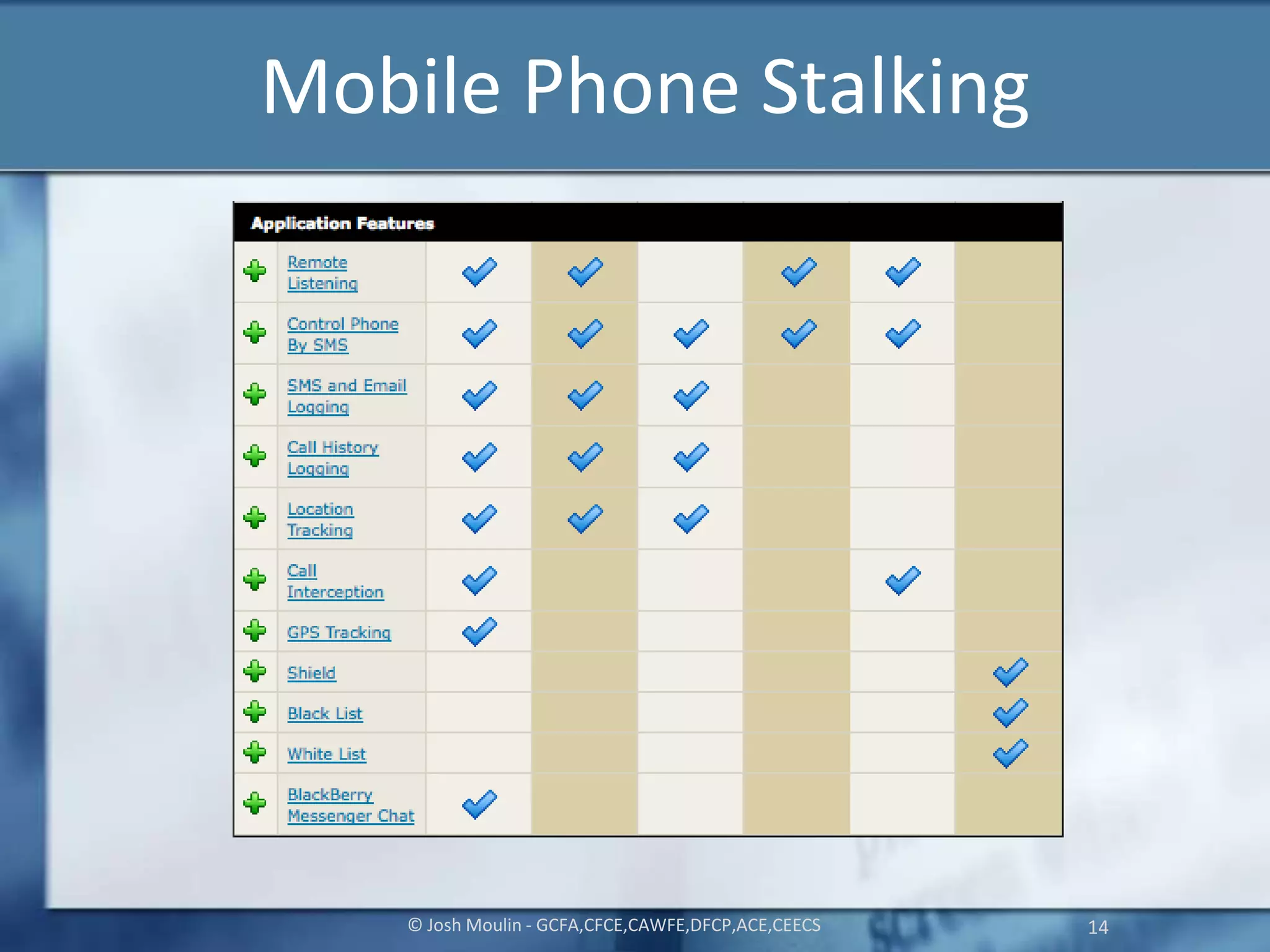
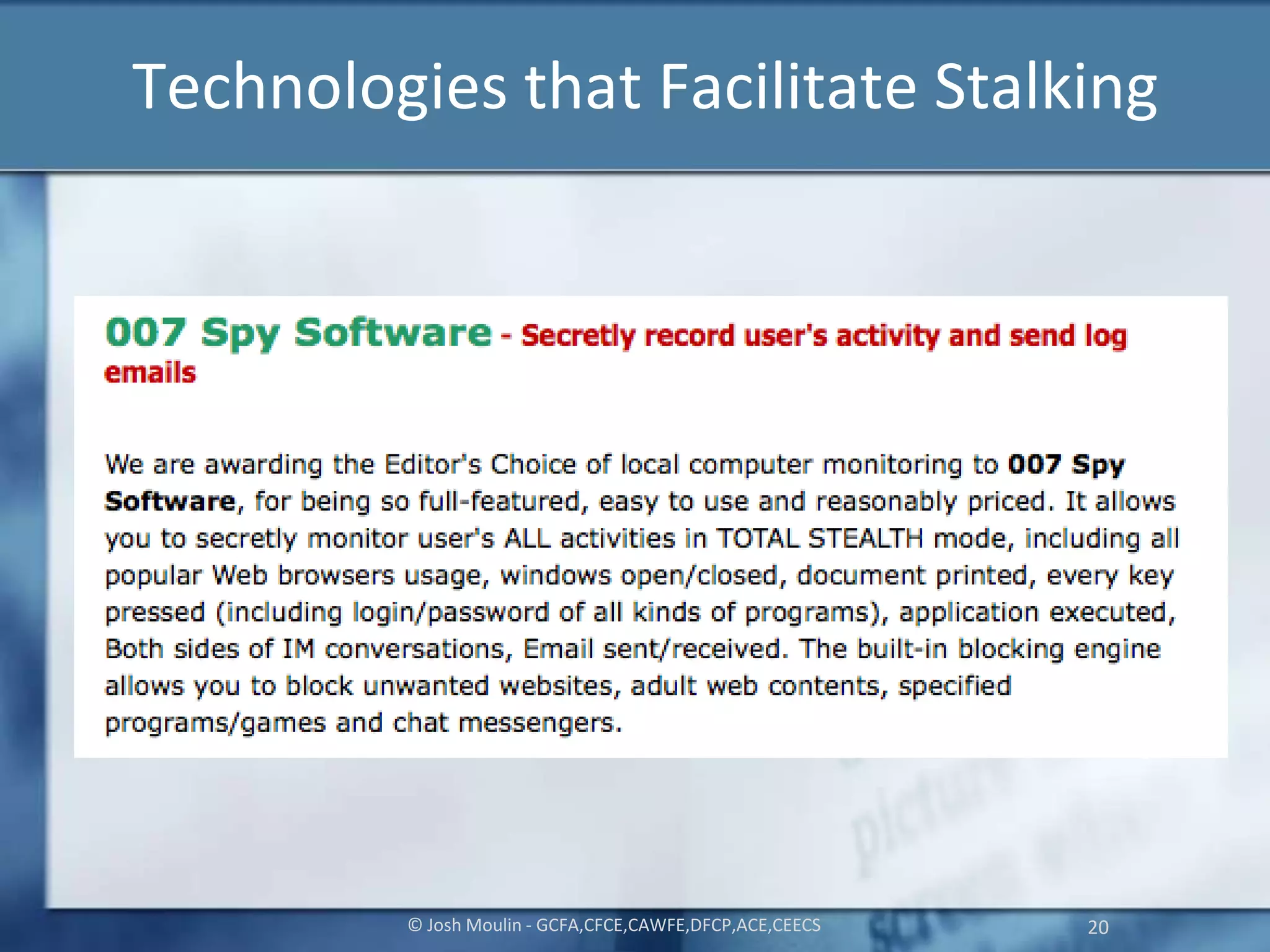
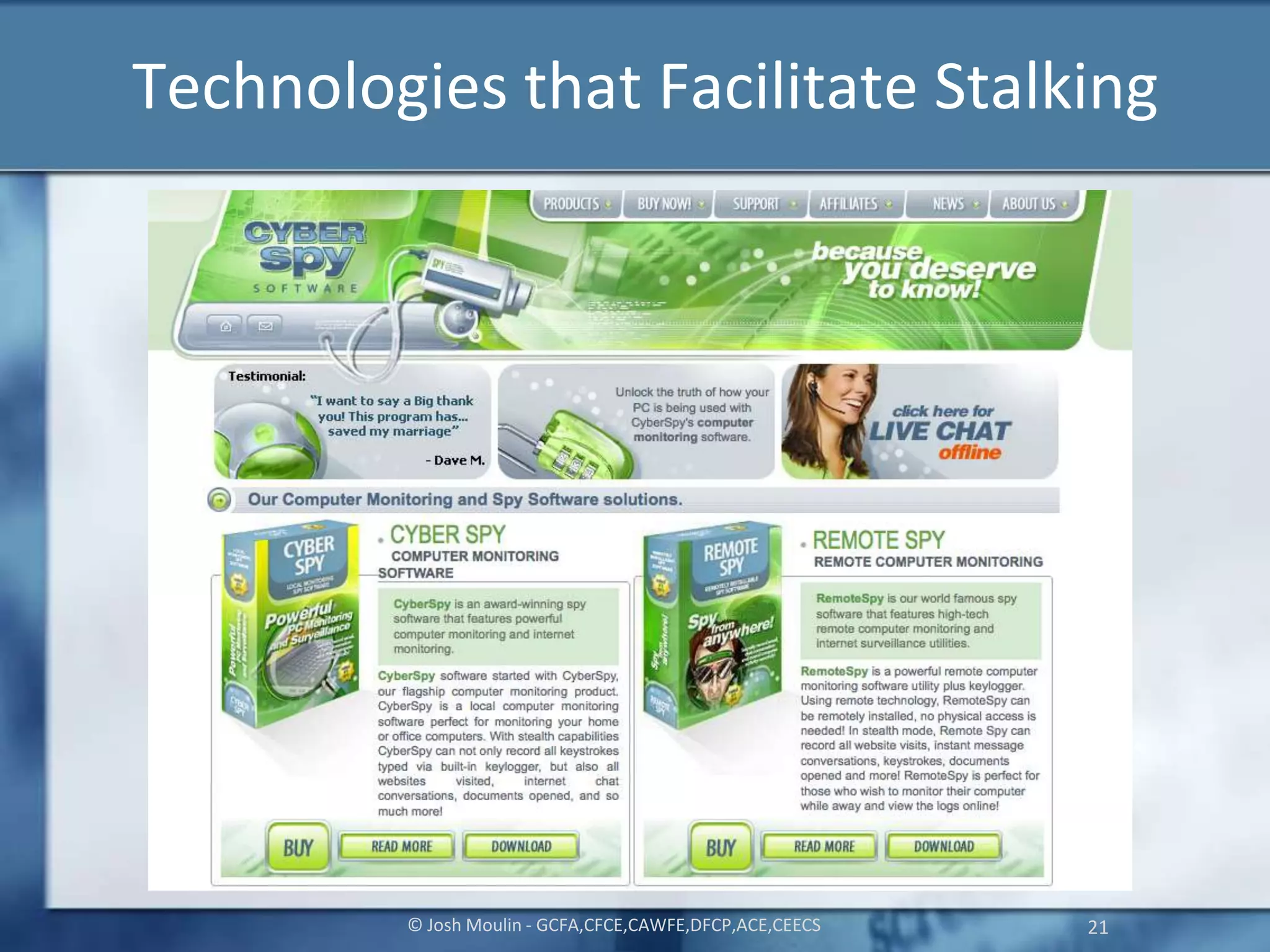
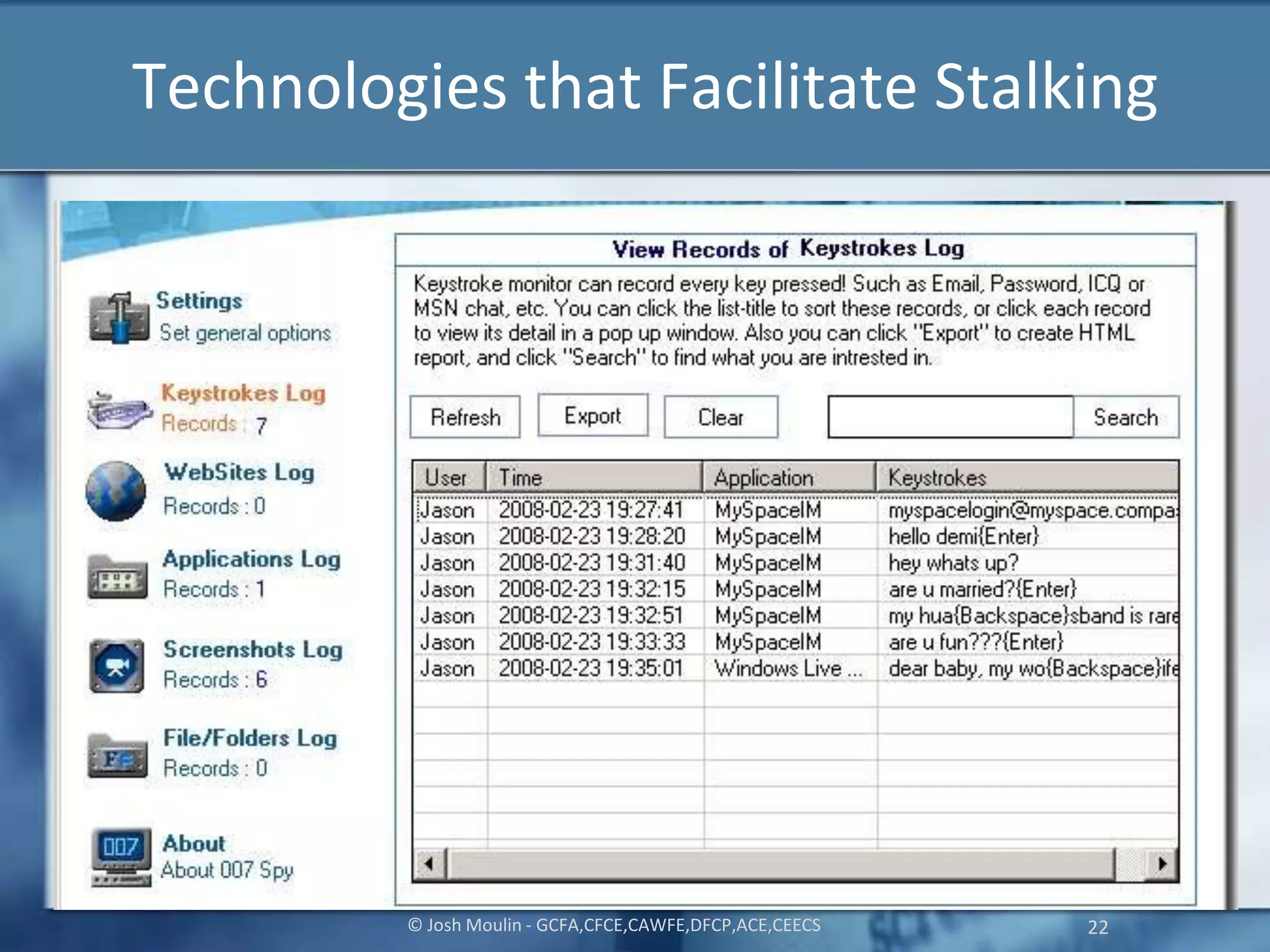
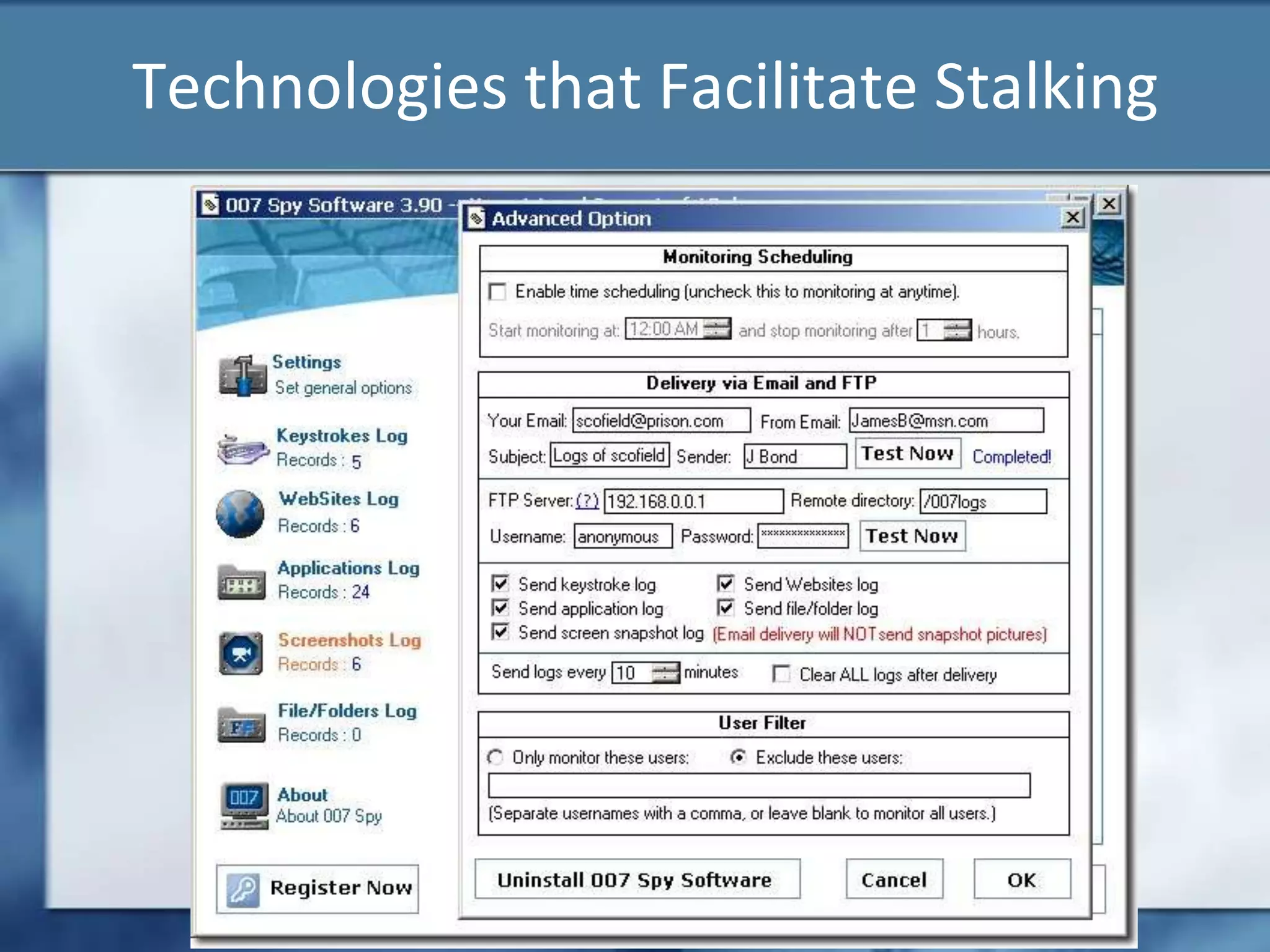
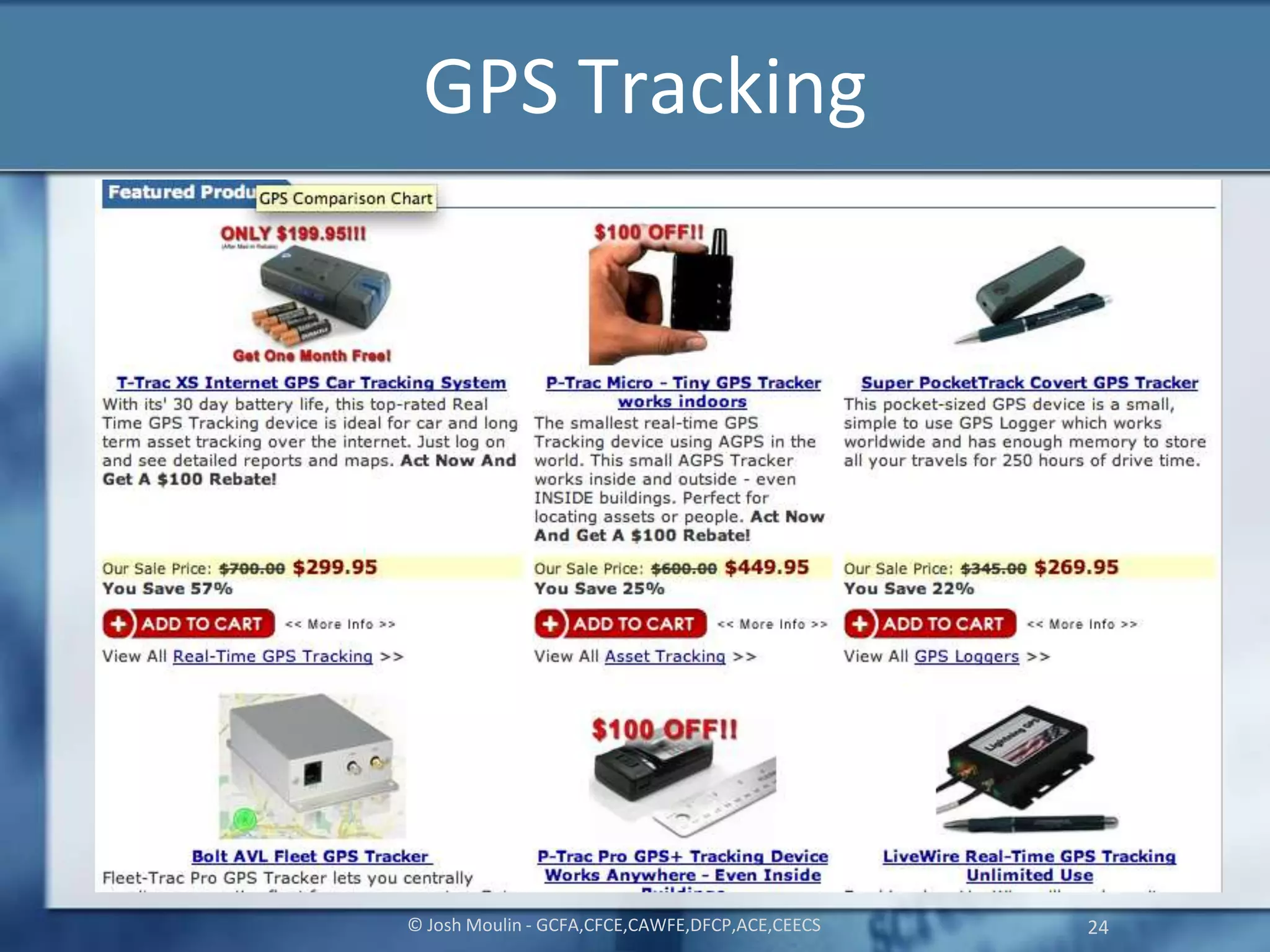
Joshua Moulin is a cyber security expert with a background as a police lieutenant and FBI cyber crime task force commander. He currently works as a contractor for the US federal government. The document discusses cyberstalking and how technology has enabled new forms of stalking behavior, noting that 65% of stalking cases are initiated online. Tips are provided on how to avoid becoming a victim, such as using strong passwords, not accepting unknown file attachments, and being aware of location data disclosed on social media.