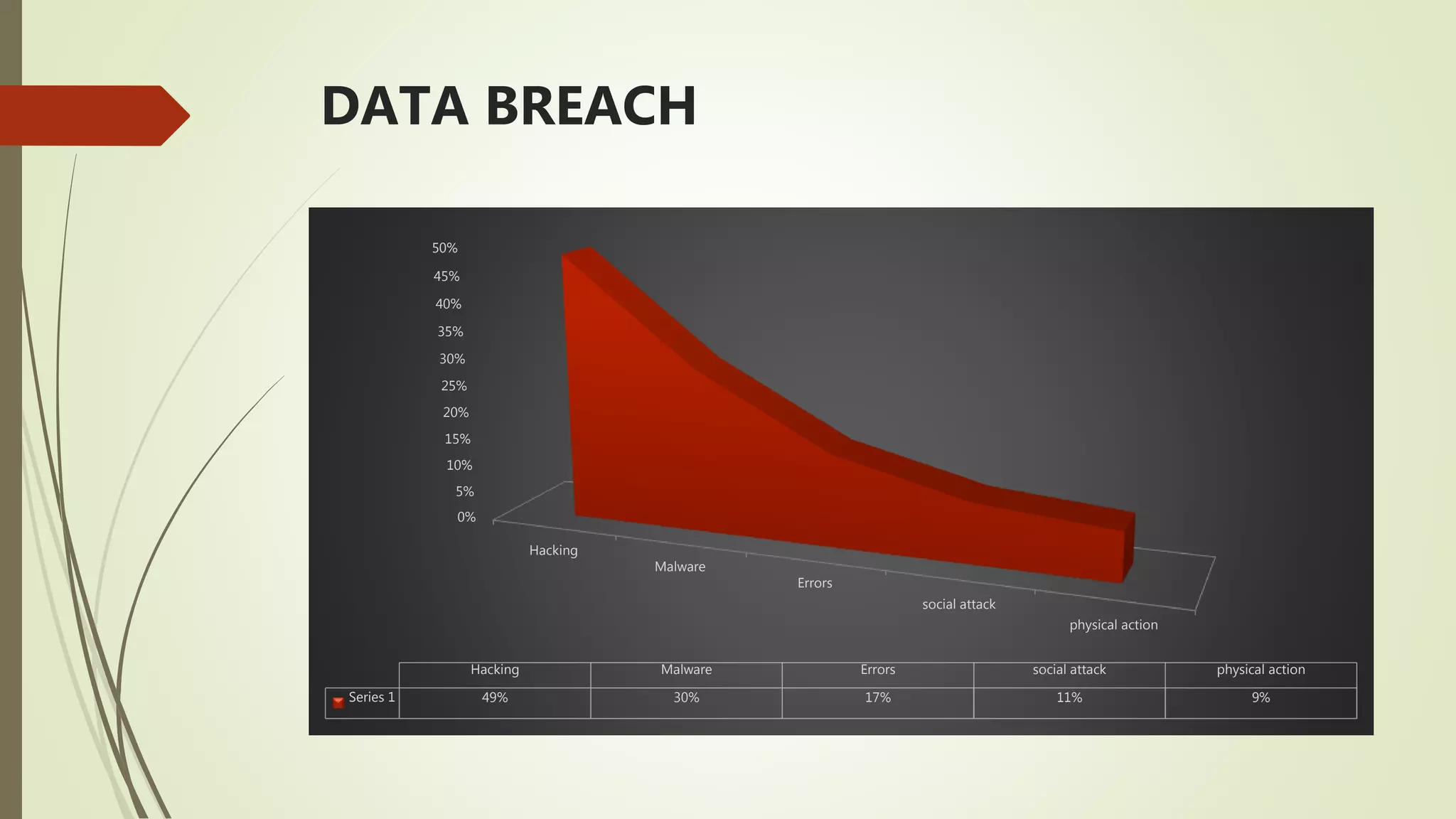
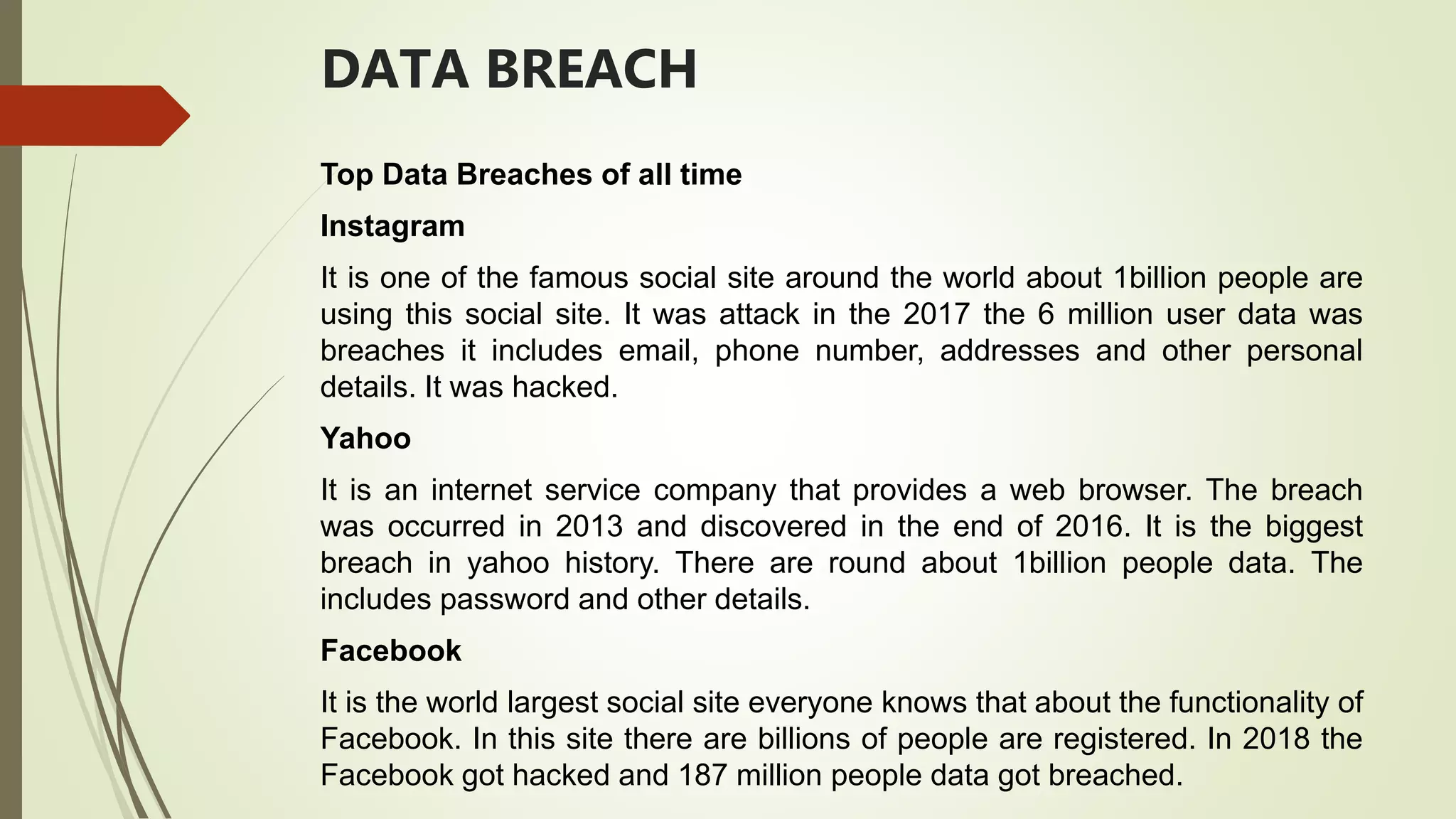
The document discusses the impact of data breaches on both small and large businesses, analyzing causes, notable incidents, and consequences. It highlights how small businesses suffer more due to limited resources compared to larger organizations, and emphasizes the importance of security measures to prevent breaches. Additionally, it outlines various causes of data breaches, including weak passwords and malware, while providing strategies for businesses to mitigate risks.