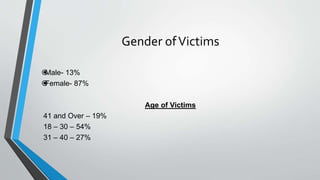
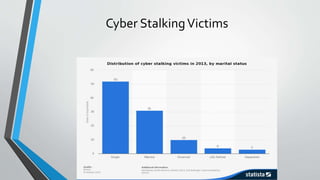
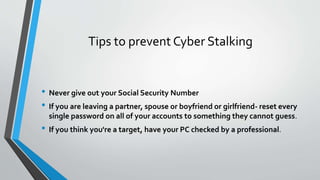
Cyberstalking involves the use of electronic means to harass individuals, encompassing actions such as identity theft, threats, and false accusations. Females are more frequently victims, with common platforms for such behavior including email, chat rooms, and message boards. Preventative measures include safeguarding personal information and being cautious with digital communications.