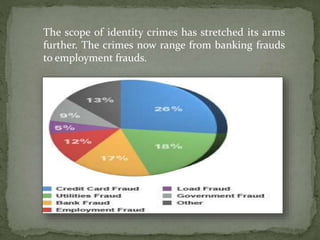
There are three main types of identity crimes: identity theft, identity fraud, and account takeover. Identity theft involves stealing someone's personal information. Identity fraud is using stolen or fake identities for ethical or unethical purposes. Account takeover occurs when a fraudster uses someone's identity information like an email to access unauthorized financial or personal accounts. Globalization and technology like hacking, phishing, and spyware have made identity crimes easier to commit from anywhere. Careless behavior and oversharing of information online and in documents discarded without shredding also contribute to identity losses, with a survey finding that every minute sees 19 new victims.