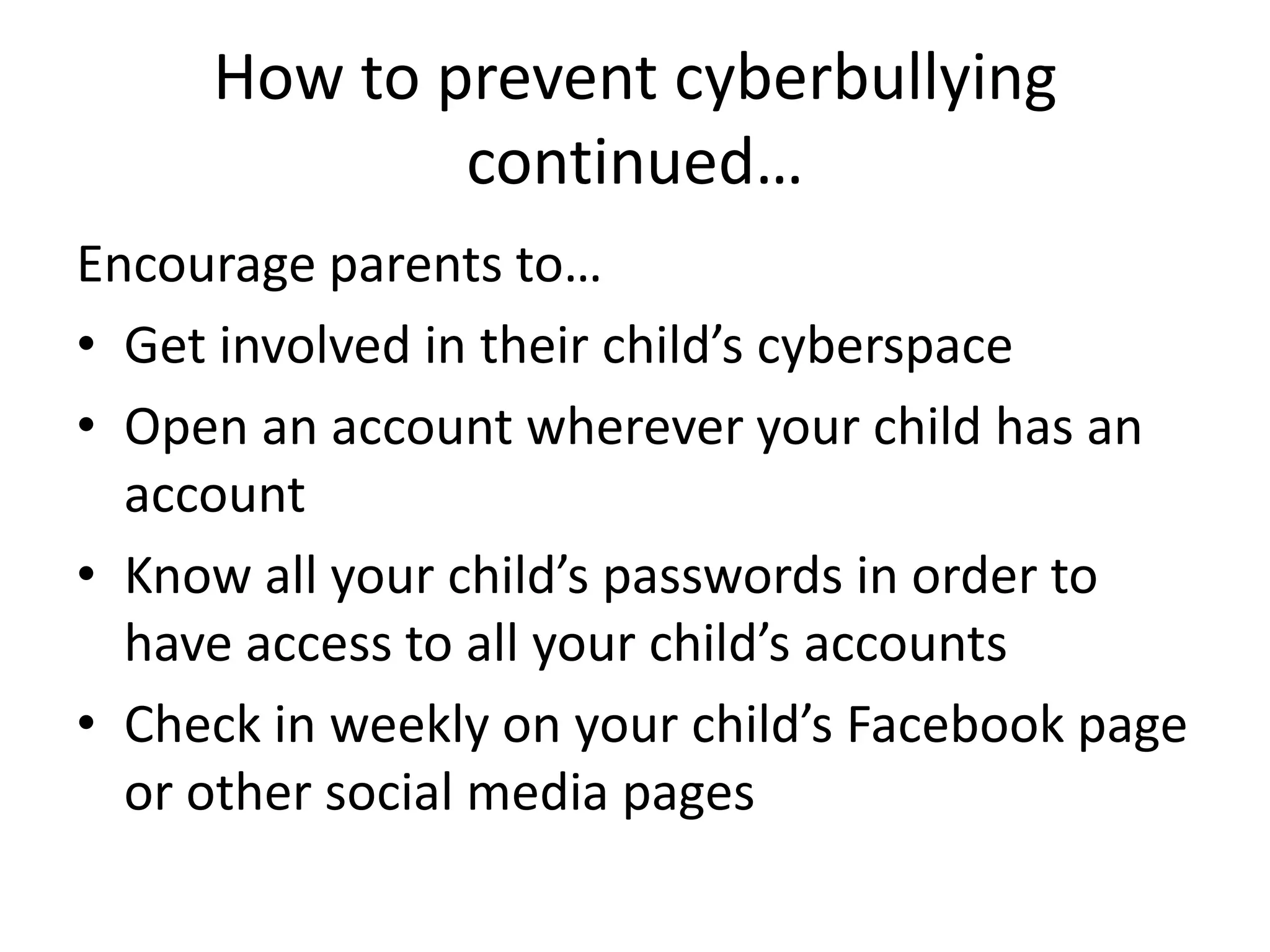
Cyberbullying involves using technology like phones or the internet to harass or threaten someone. Common tactics include gossip, impersonation, harassment, and cyberstalking. Victims can experience depression, low self-esteem, and even suicide. Rachael Neblett took her own life after receiving threatening emails from an anonymous cyberbully. Parents and schools should encourage students to report cyberbullying and monitor their online activities to help prevent further incidents.