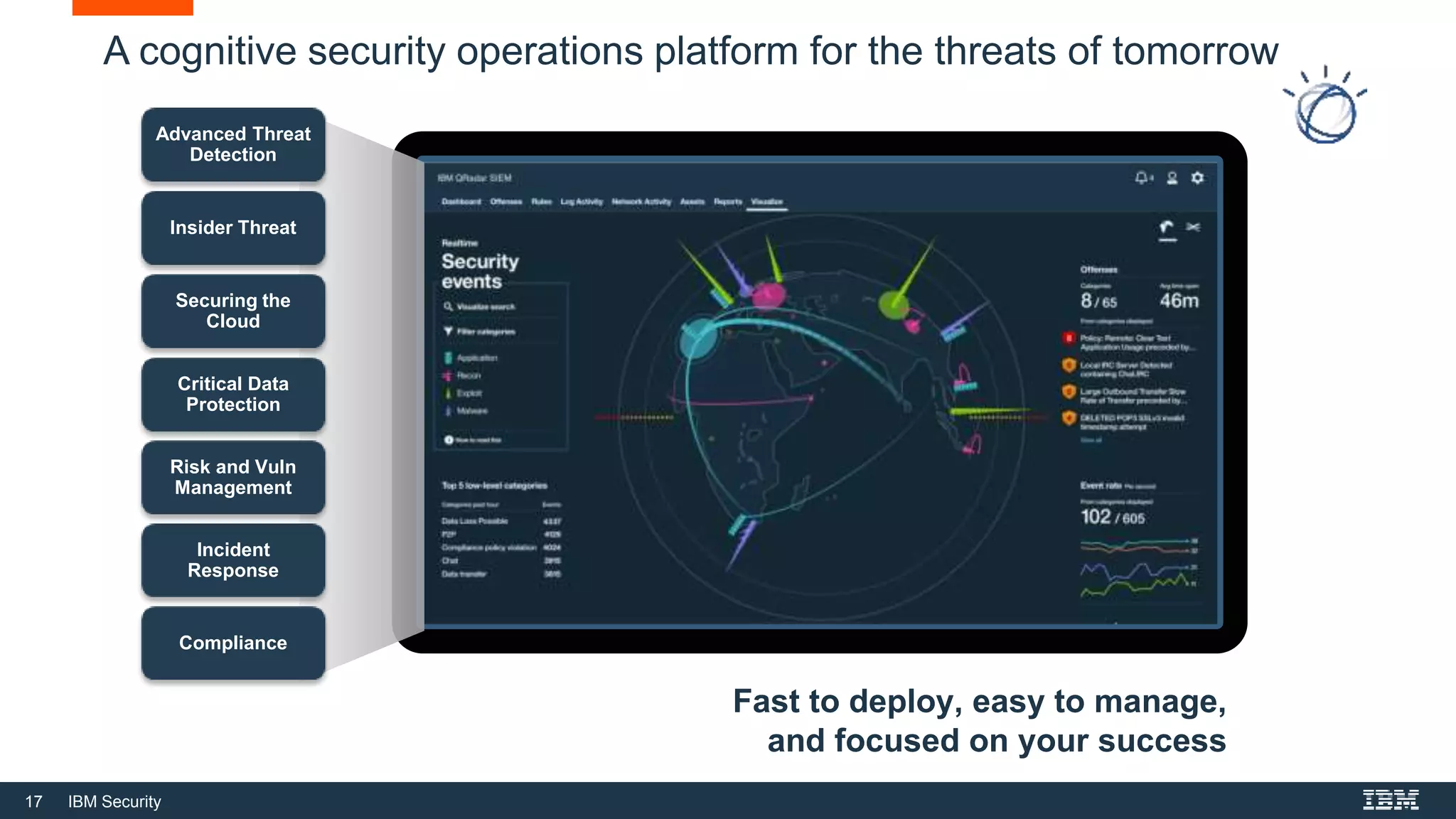
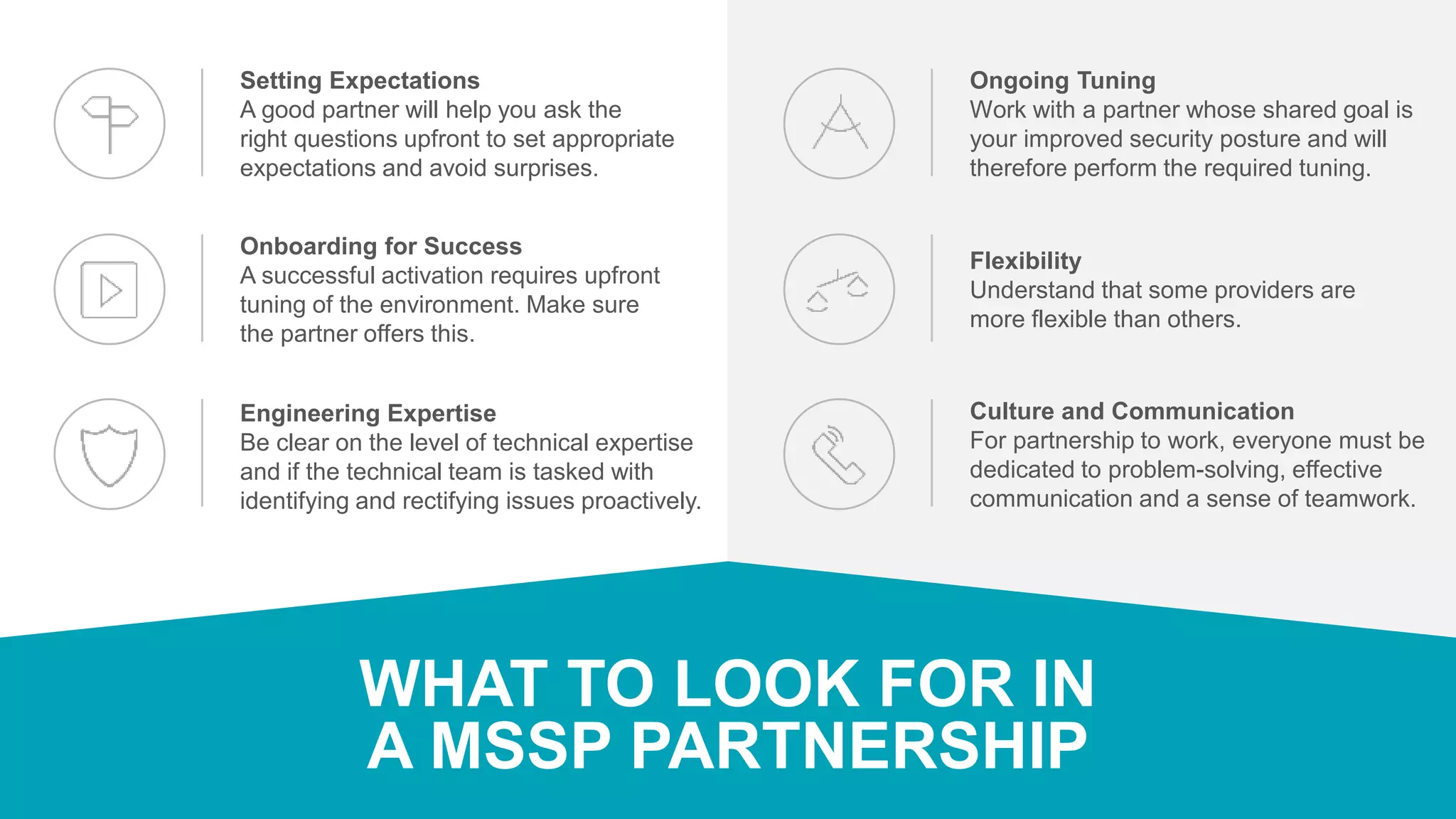
Forsythe offers managed SIEM solutions using IBM QRadar to help Fortune 1000 organizations enhance their cybersecurity posture amidst increasing threats and a growing talent gap in the security workforce. SIEM software analyzes alerts from various technologies to identify potential security threats, allowing security teams to focus on critical investigations while reducing false positives. The document emphasizes the importance of selecting a suitable managed security services partner and outlines best practices for establishing a successful SIEM deployment.