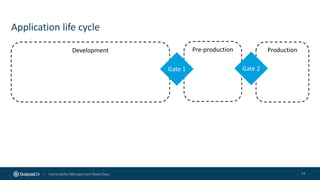
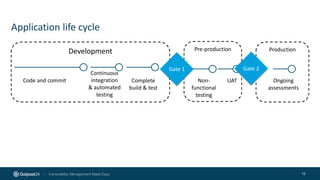
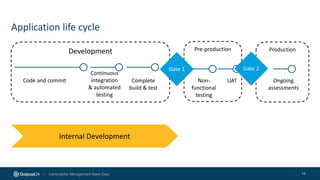
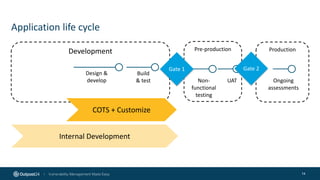
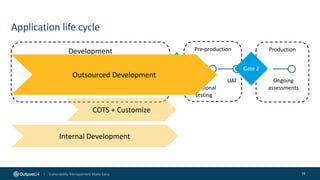
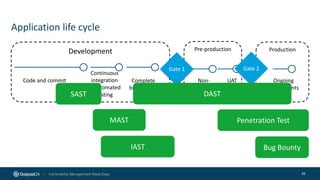
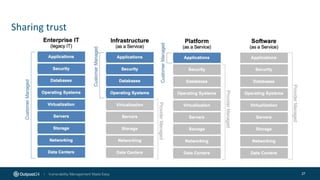
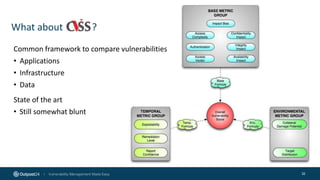
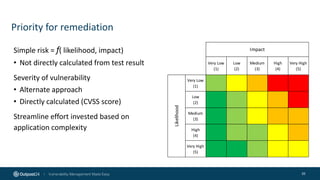
The document outlines the importance of building an application security (AppSec) program to enhance security posture amidst the app revolution. It discusses objectives such as better security, compliance, and shrinking the attack surface while detailing the application lifecycle and various security testing tools. Additionally, it emphasizes integrating security into the development process and utilizing automated assessments to manage vulnerabilities effectively.