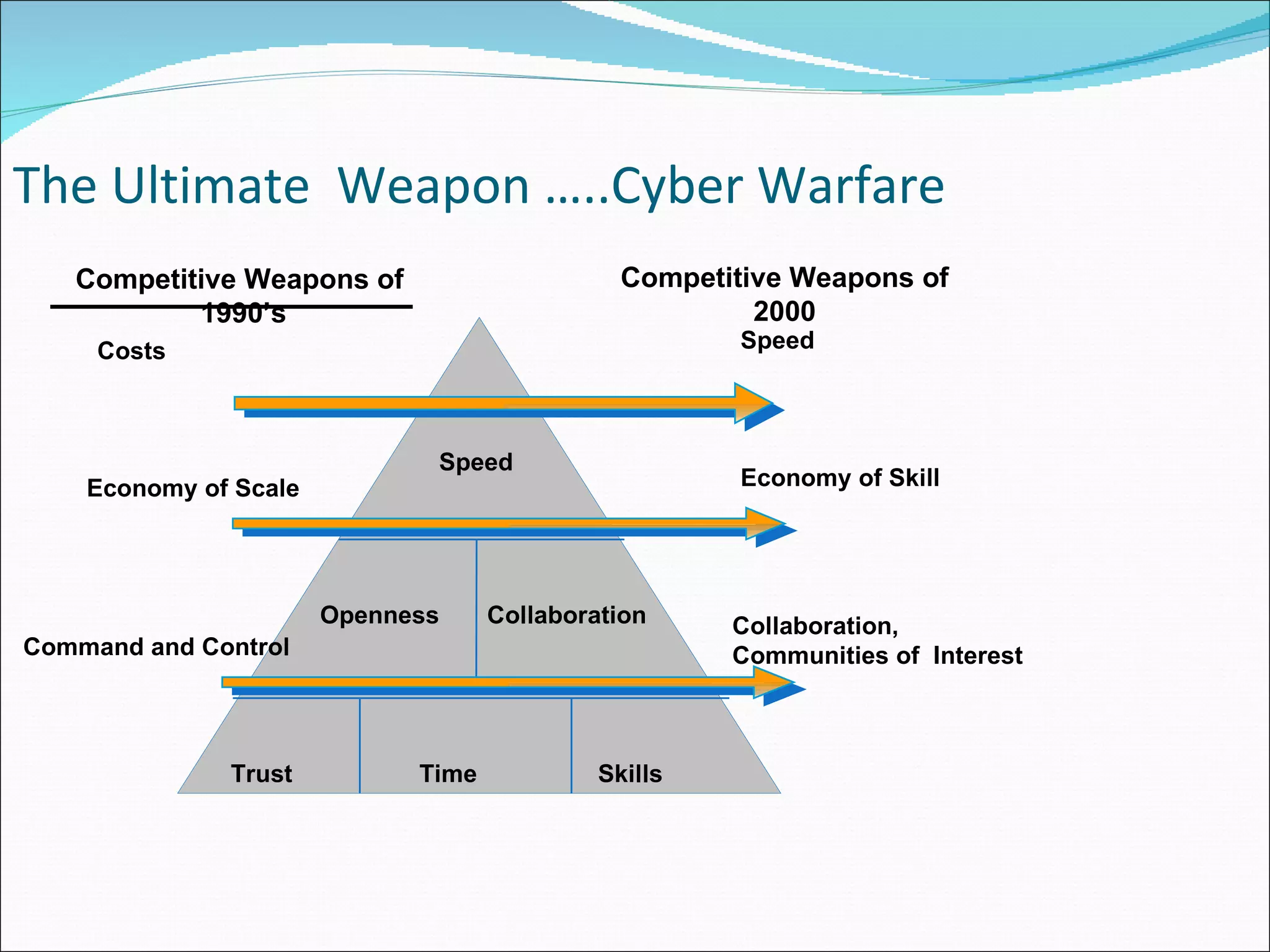
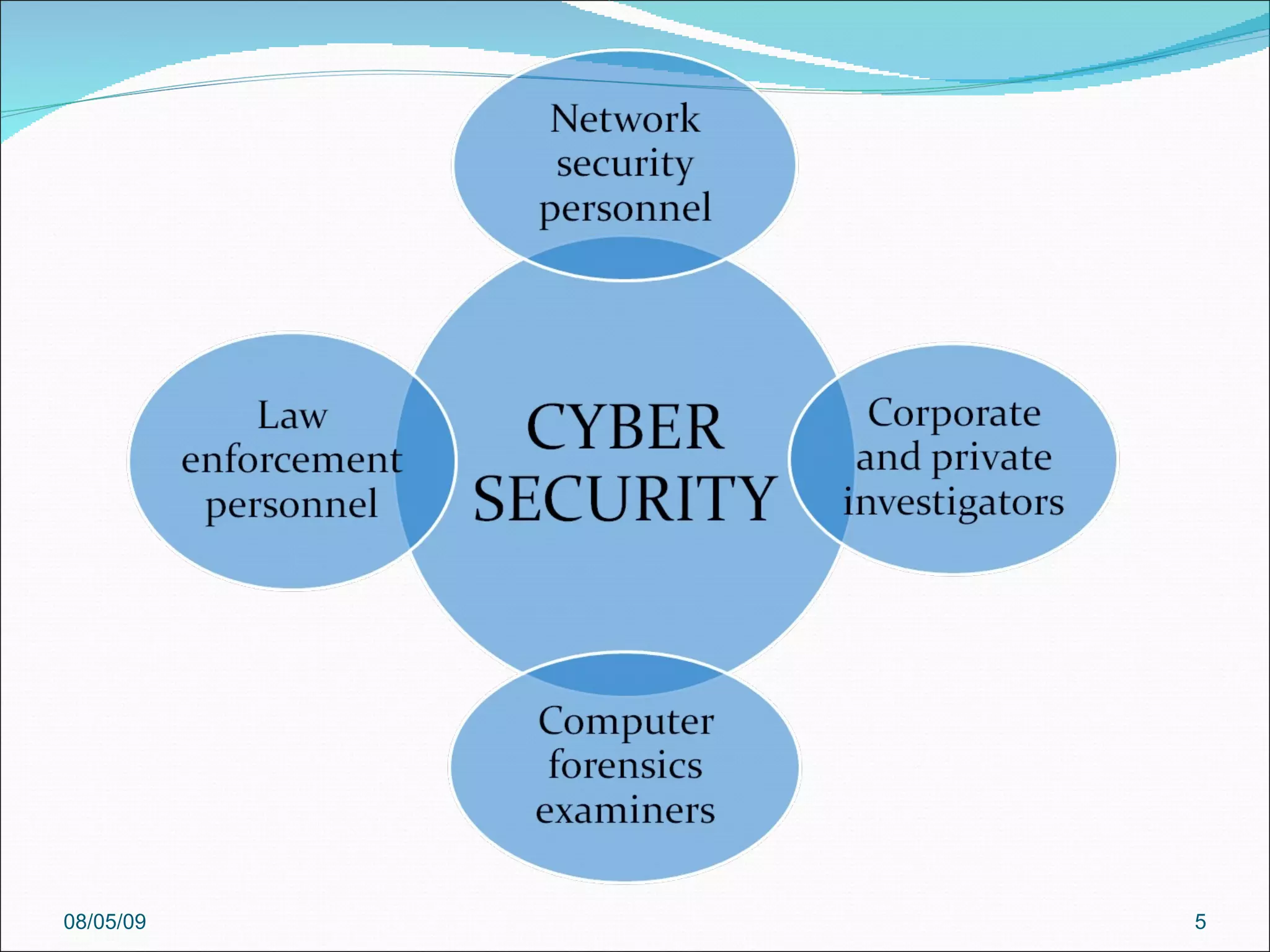
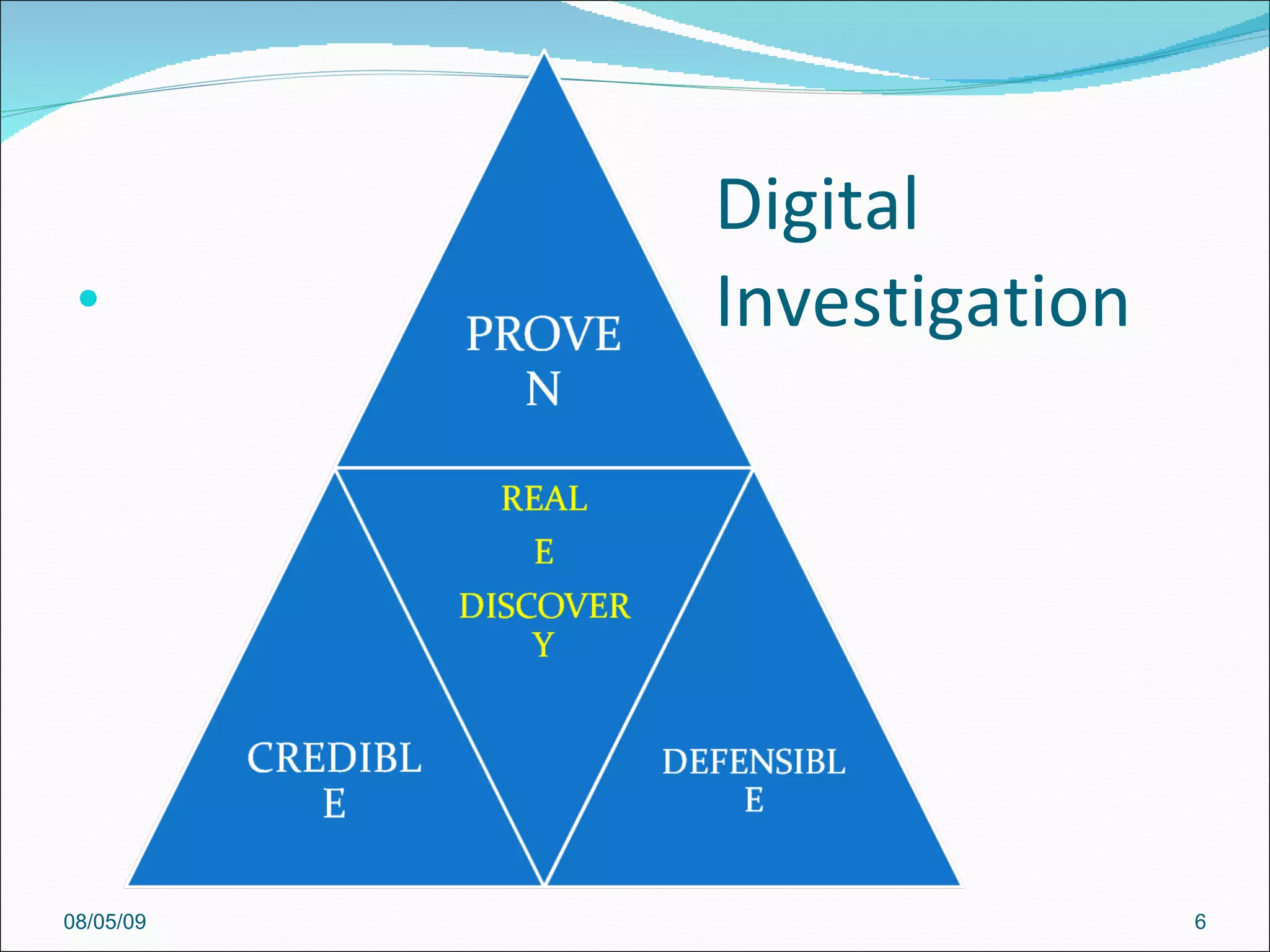
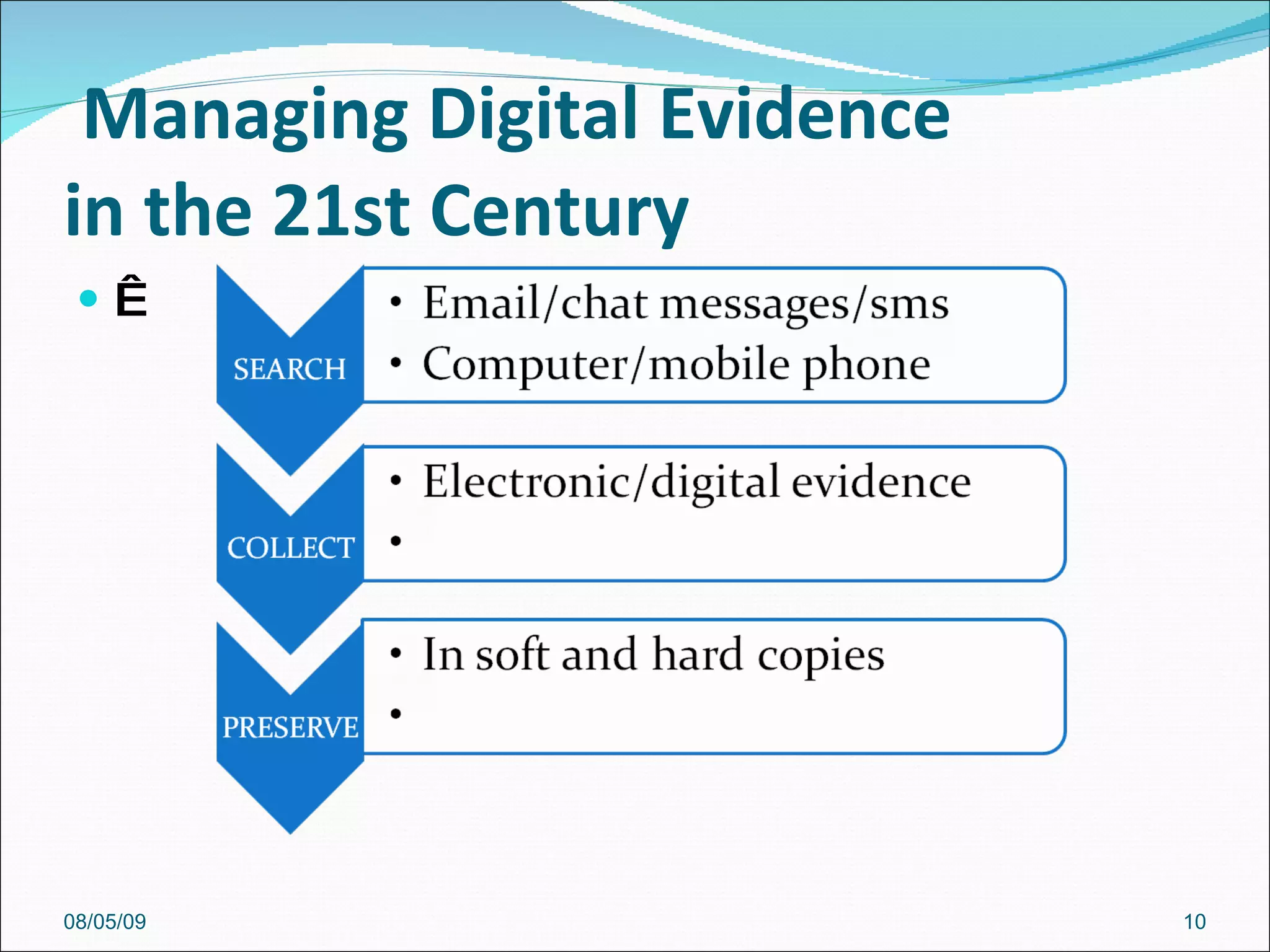
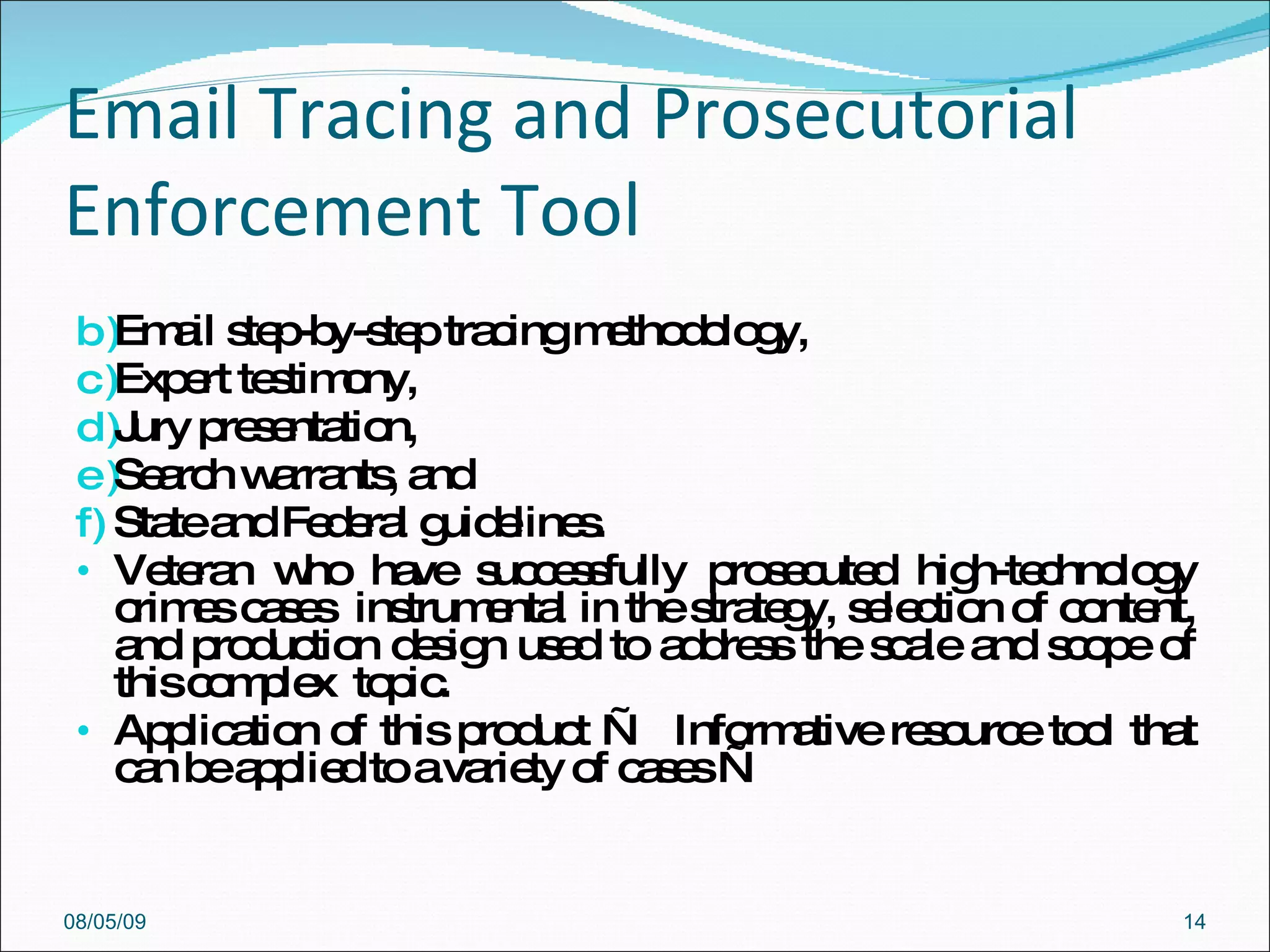
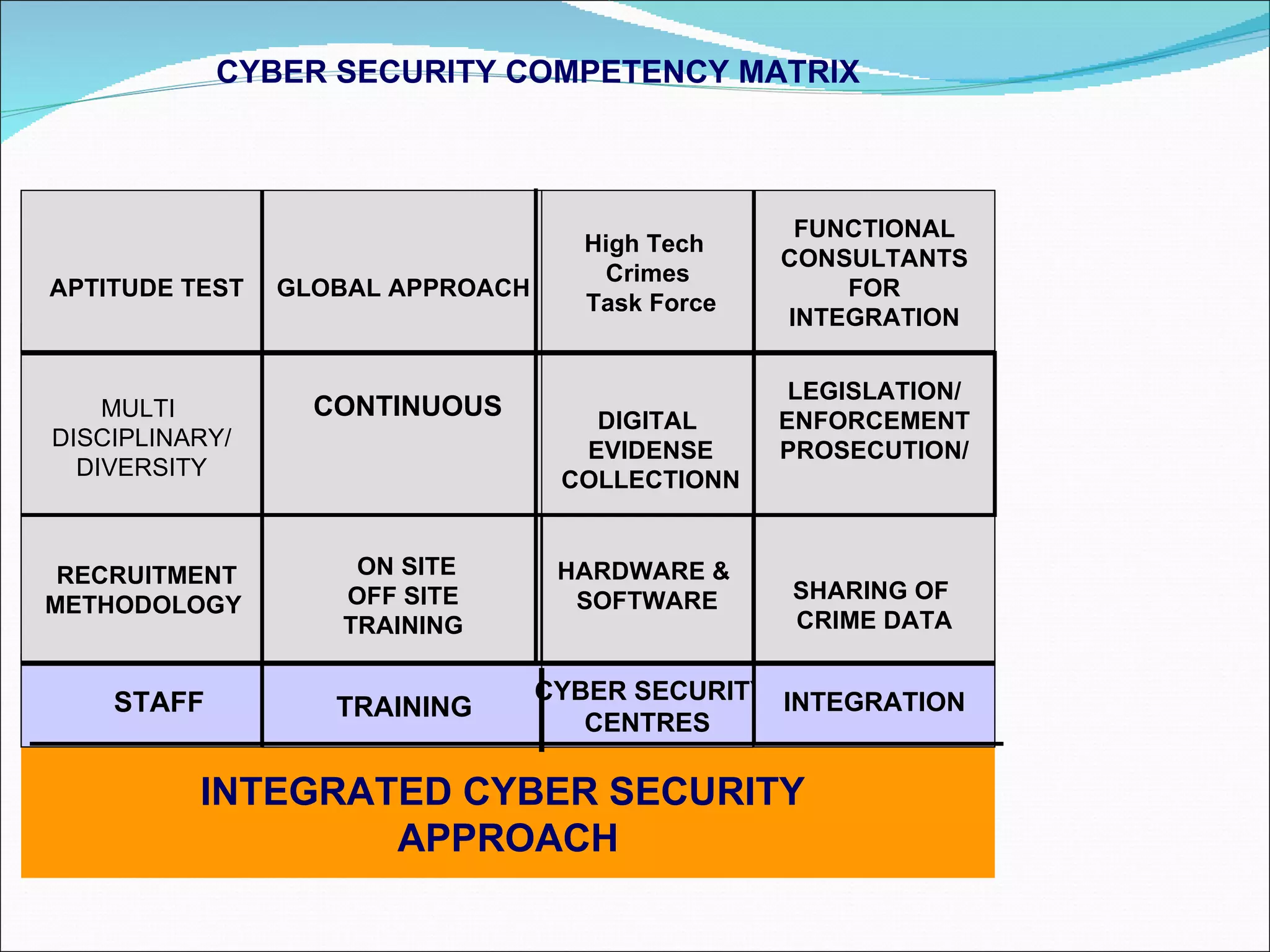
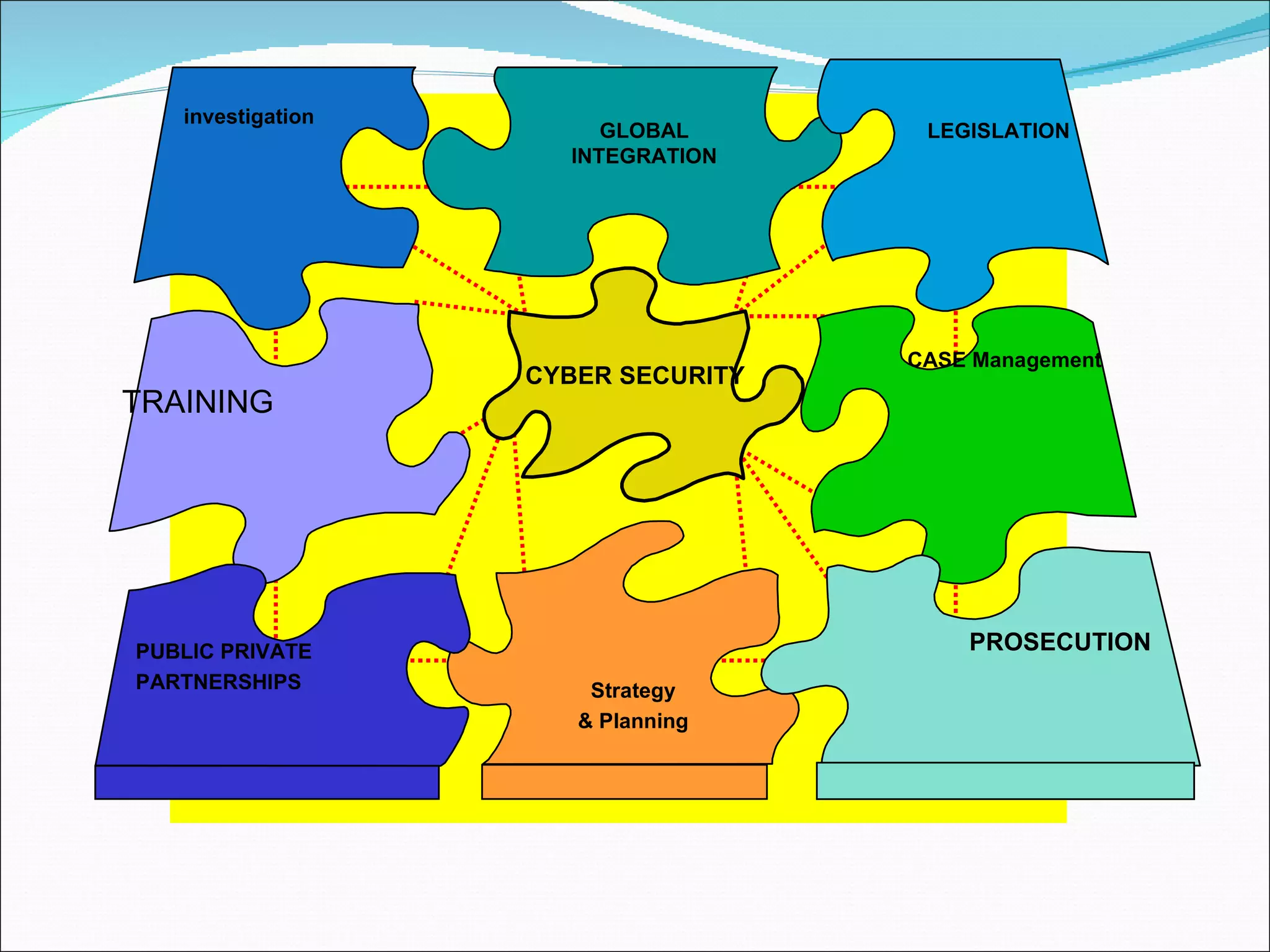
The document discusses cybersecurity and digital forensics. It covers topics like how cybercrimes are committed using email and viruses, what constitutes electronic evidence, investigating electronic crimes scenes and managing digital evidence. It also discusses digital forensics techniques, global initiatives on high-tech task forces, tools for tracing emails and presenting digital evidence in court. The document provides an overview of software used for cyber investigations, data recovery and legal holds on electronic evidence.
![Firoze Zia Hussain CEO Totem International Former Superintendent of Police Pondicherry [email_address] M-919618621234](https://image.slidesharecdn.com/cybersecurityisacabglrpresentation24thjuly-12494882125002-phpapp03/75/Cyber-Security-Isaca-Bglr-Presentation-24th-July-1-2048.jpg)