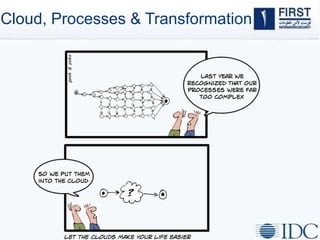
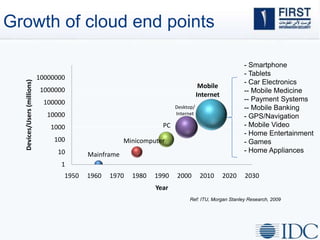
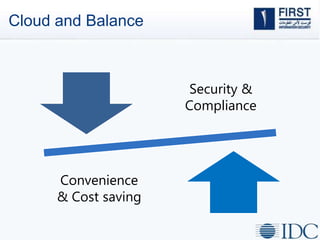
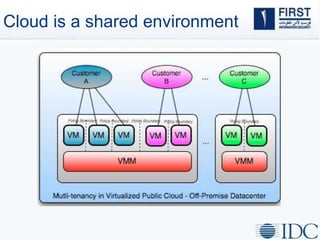
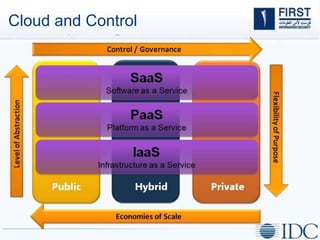
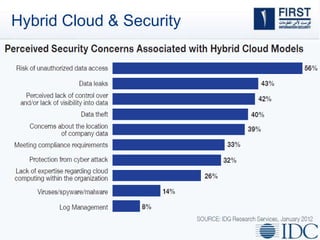
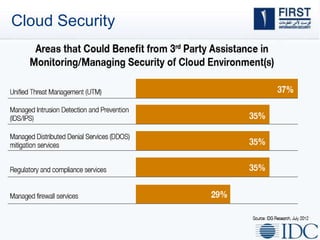
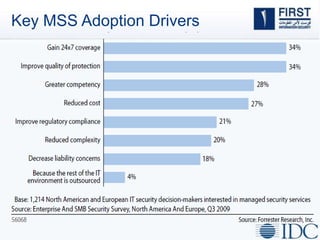
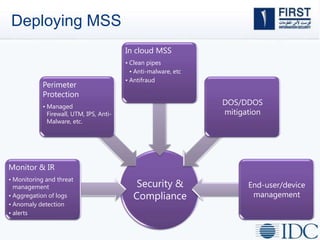
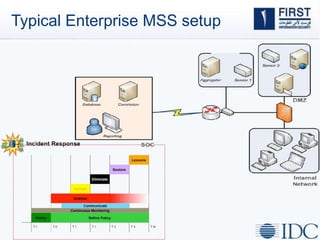
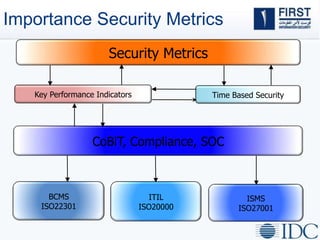
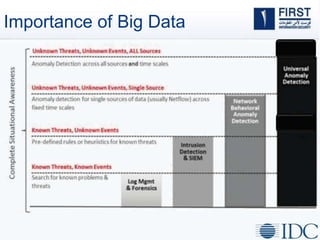
This document discusses opportunities and challenges for cloud security and managed security services. It begins by outlining the growth of cloud computing and connected devices. This brings both convenience and complexity from a security perspective as the cloud is a shared environment prone to high profile failures. The top 10 security issues for the cloud are identified, including governance, compliance, identity and access control, and data protection. Common threats are also outlined. The document then discusses the benefits of managed security services for enterprises using cloud computing, including security monitoring, incident response, and perimeter protection. It emphasizes that security requires transformation and a proactive approach involving collaboration to keep pace with evolving threats.