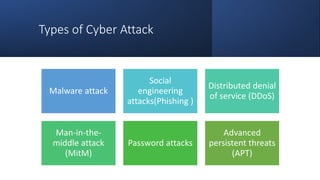
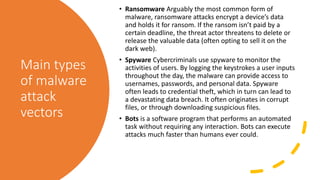
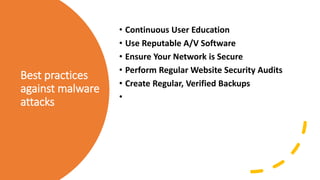
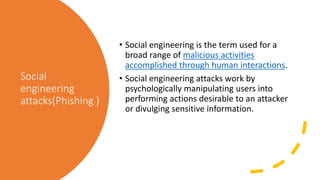
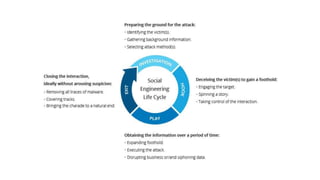
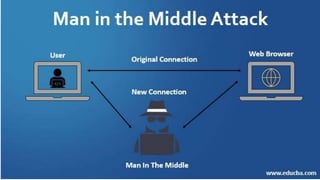
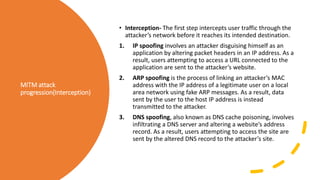
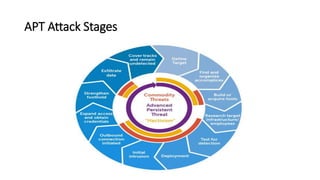
The document outlines various types of cyber attacks, including malware, social engineering, denial-of-service, man-in-the-middle attacks, and advanced persistent threats. It details the methods and objectives of these attacks, as well as best practices for prevention and protection against them. Additionally, it emphasizes the importance of user education, secure systems, and the use of advanced detection technologies like network detection and response.