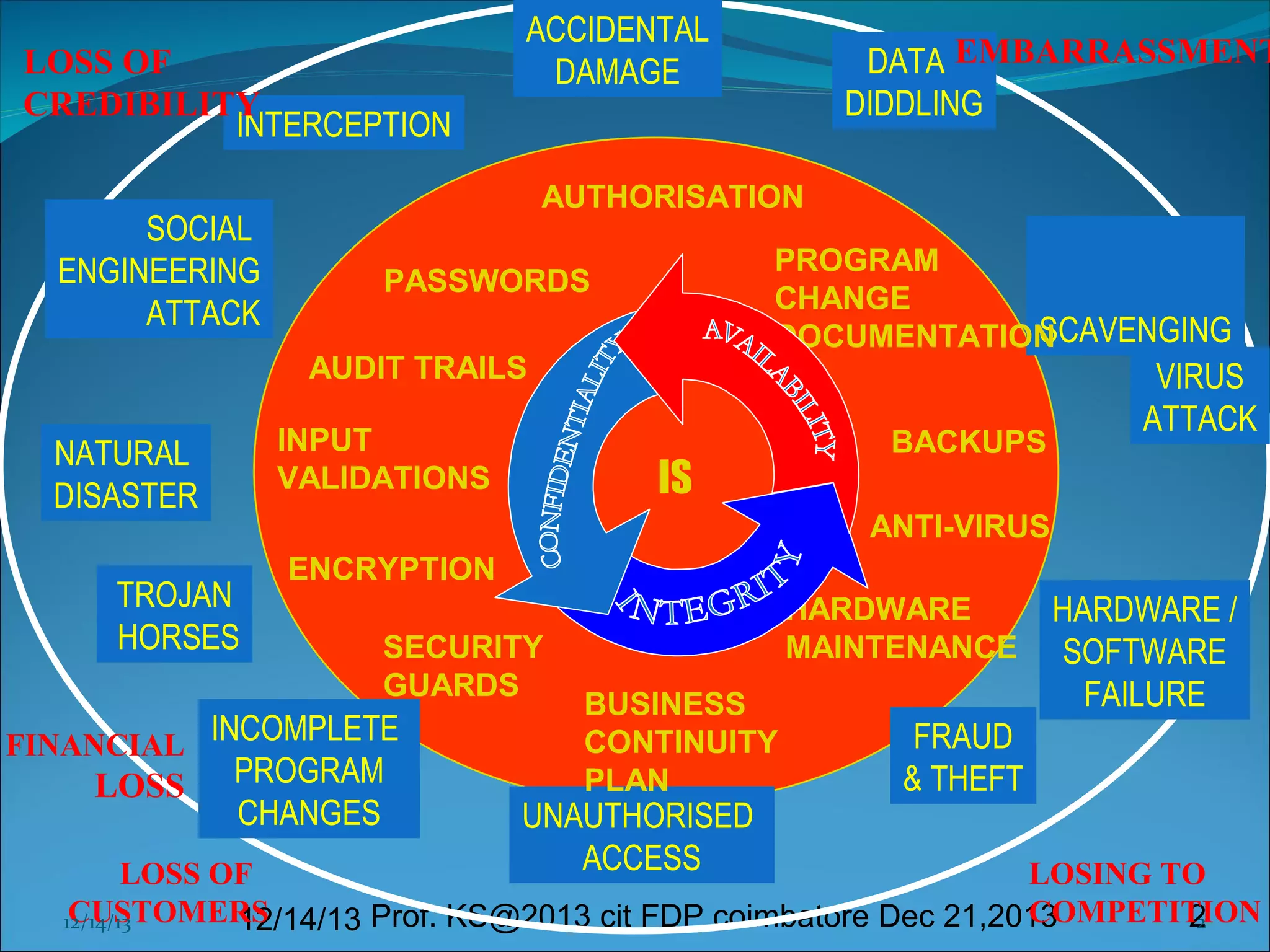
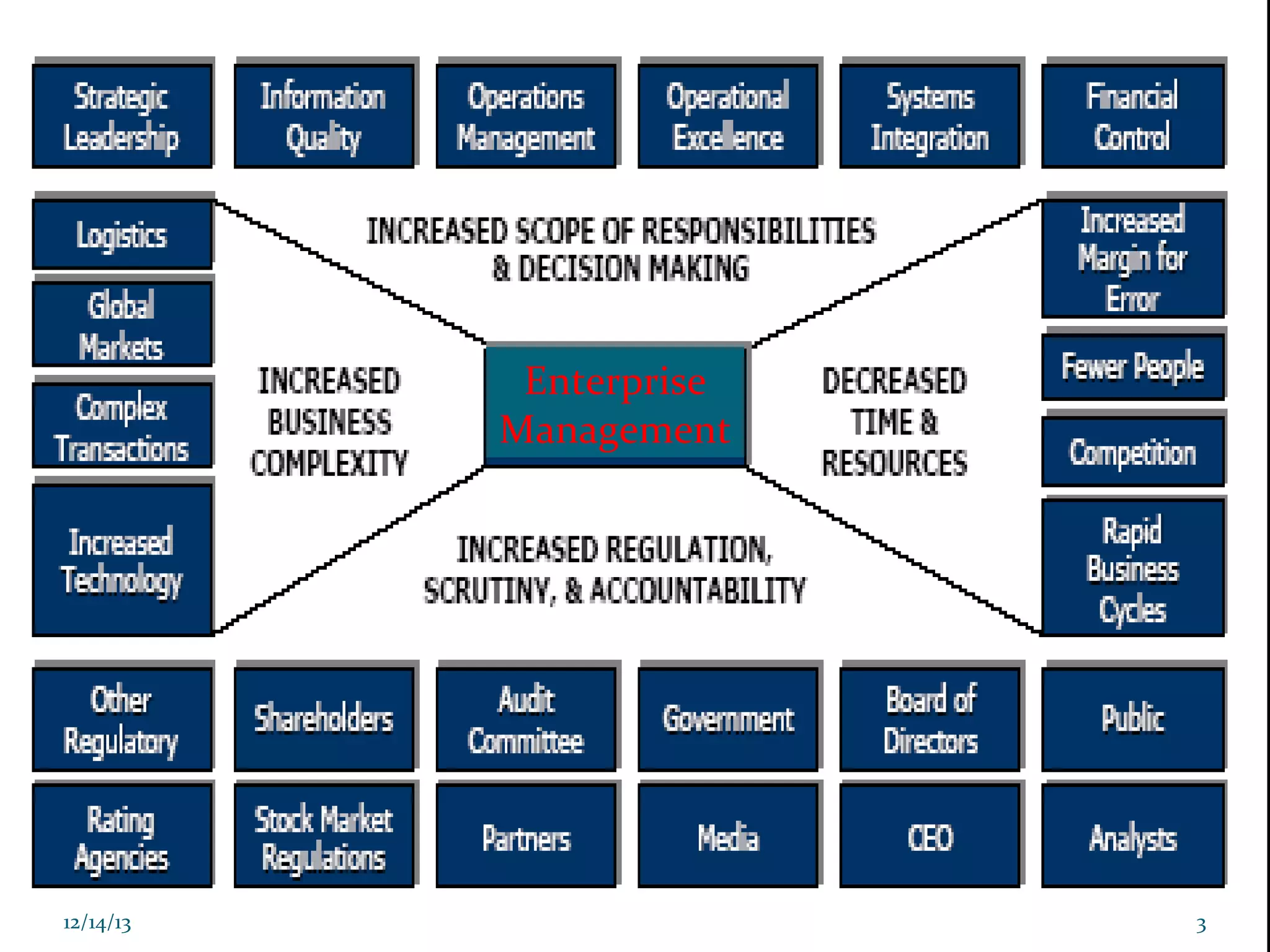
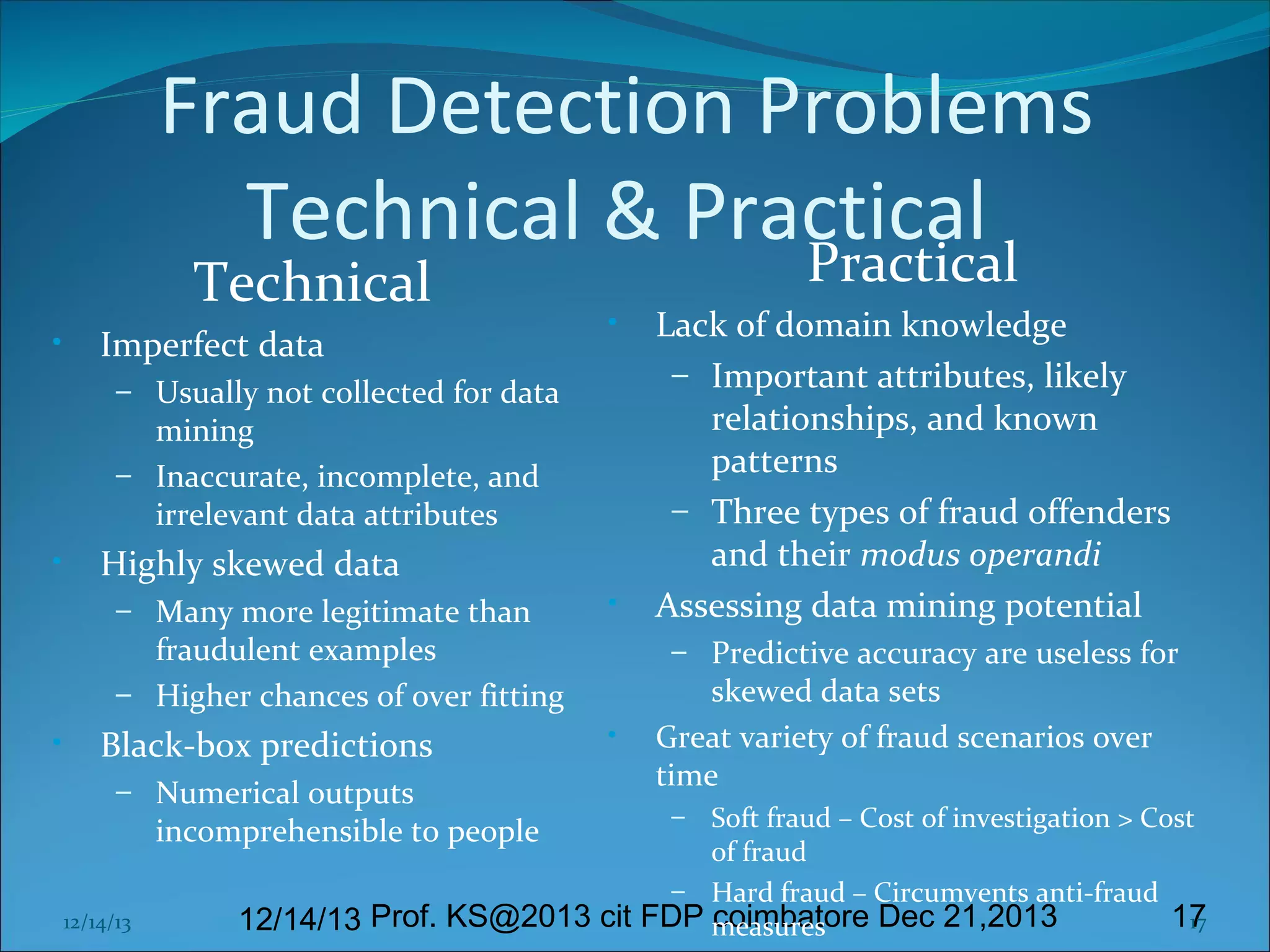
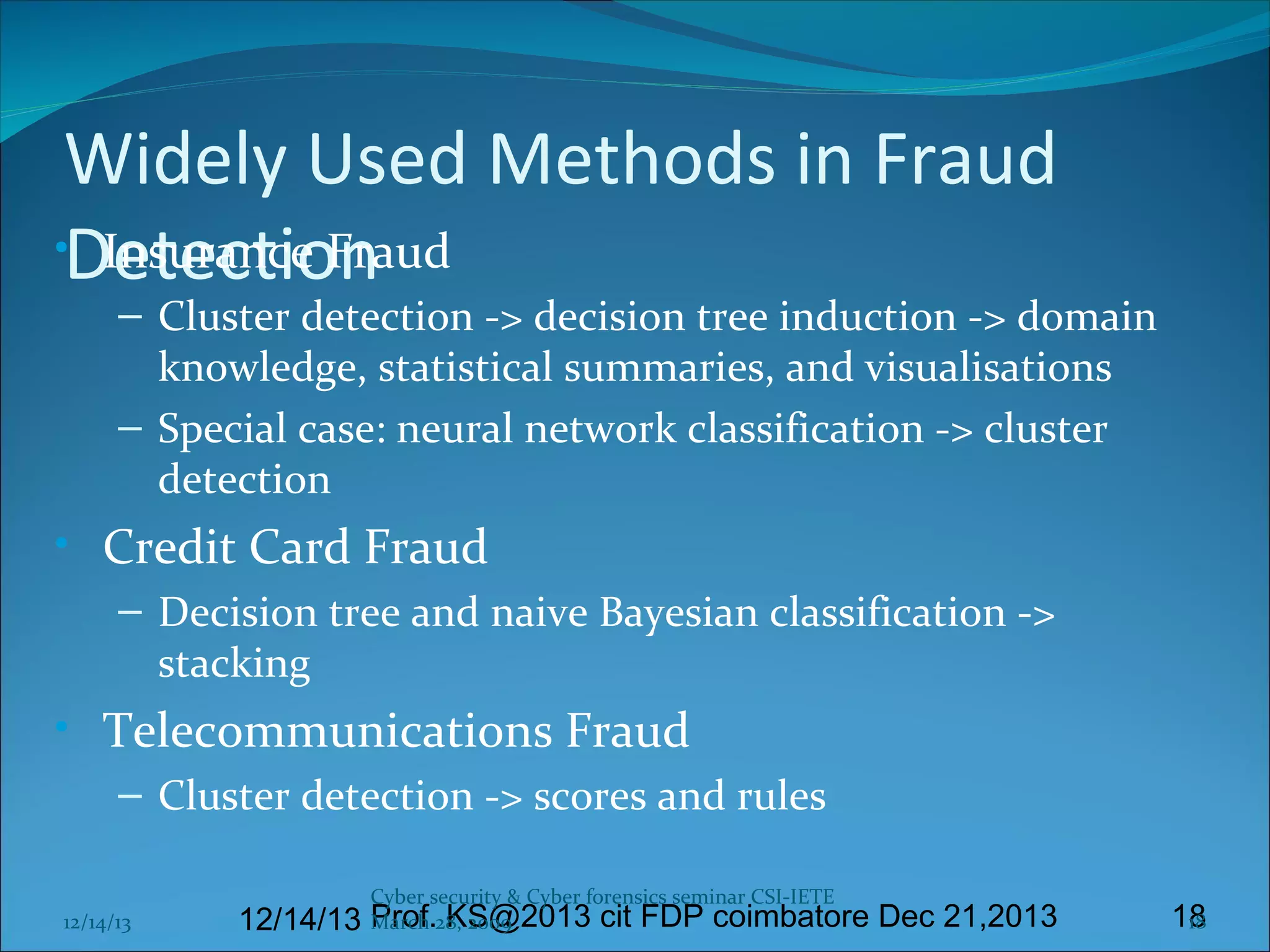
This document presents information on cyber forensics and fraud detection. It discusses the challenges of digital evidence collection and analysis. It also outlines the responsibilities of different parties in digital forensics like police, auditors, and technologists. Effective fraud detection requires highly trained personnel, appropriate tools, strong cyber laws, and certified fraud examiners. Common fraud types and detection methods using data mining techniques like decision trees and clustering are also summarized. The document emphasizes the importance of visualization and integrating multiple models to improve fraud prediction. Finally, it discusses challenges like imperfect data and the need for domain expertise in fraud detection.