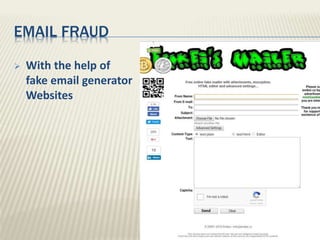
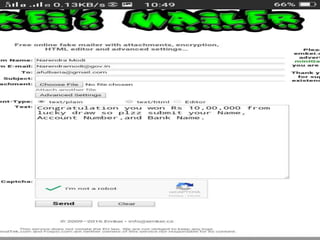
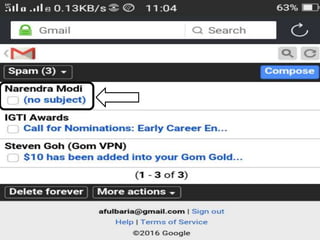
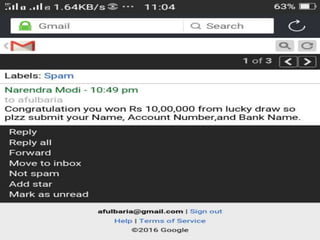
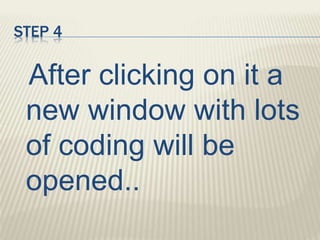
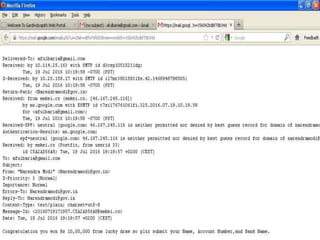
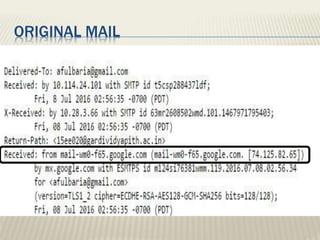
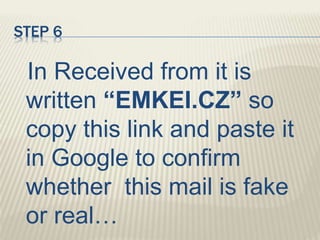
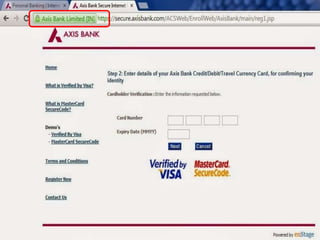
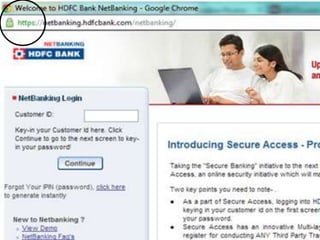
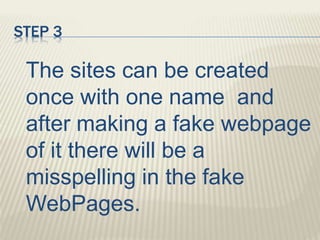
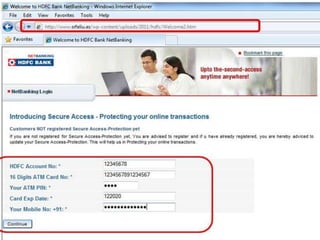
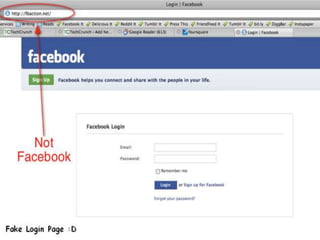
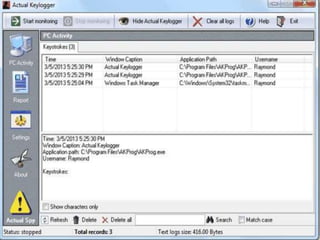
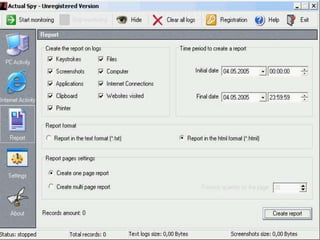
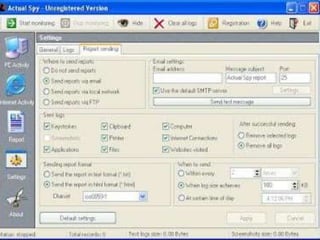
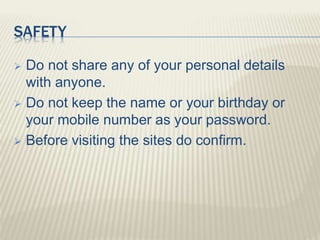
The document discusses various types of cyber crimes, including hacking, email fraud, and cyber terrorism, emphasizing the role of computers and the internet in facilitating these unlawful activities. It offers safety tips, such as using antivirus software and checking the authenticity of websites and emails to protect against cyber threats. The importance of personal security and awareness in safeguarding against cyber crimes is also highlighted.