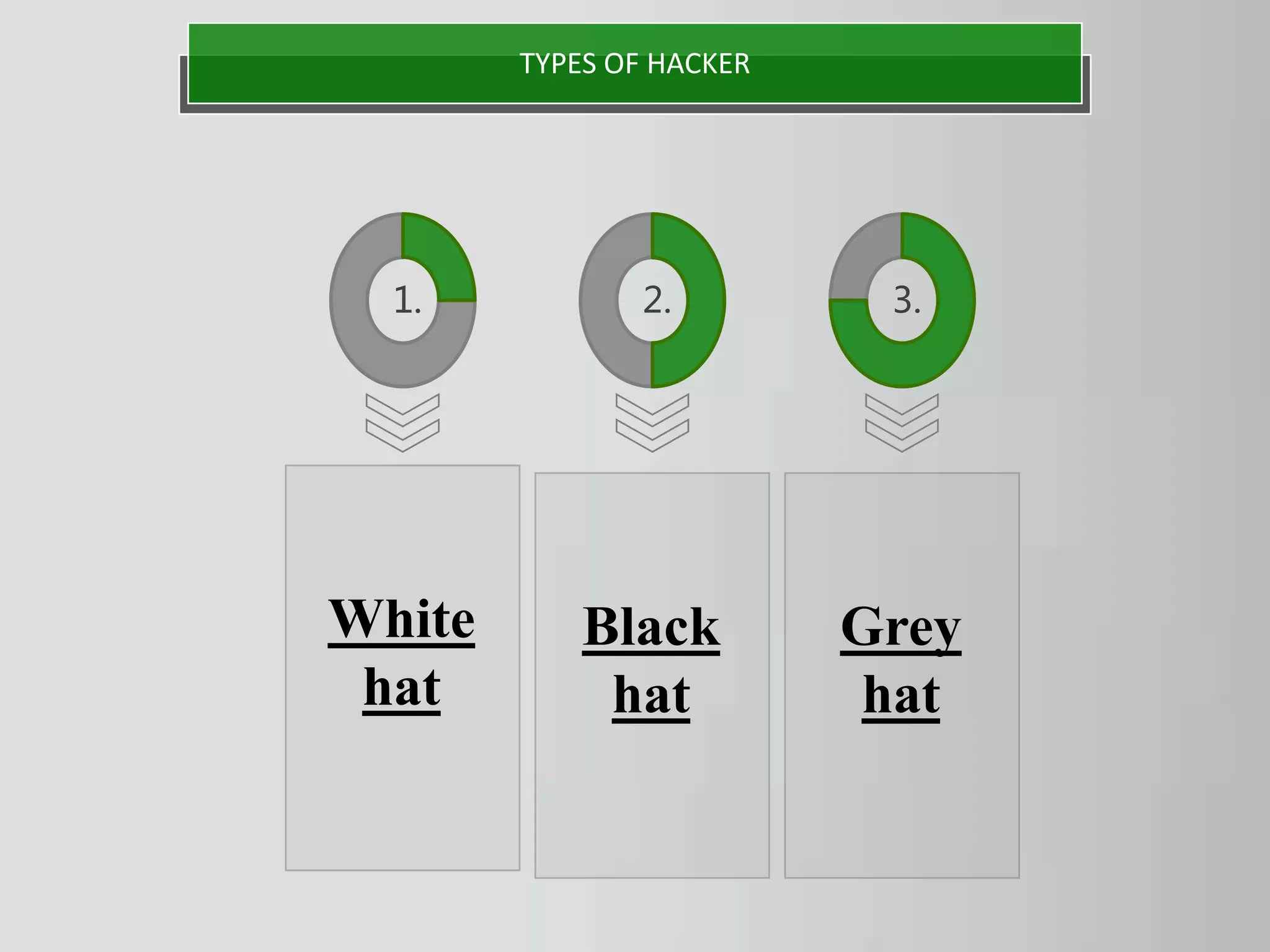
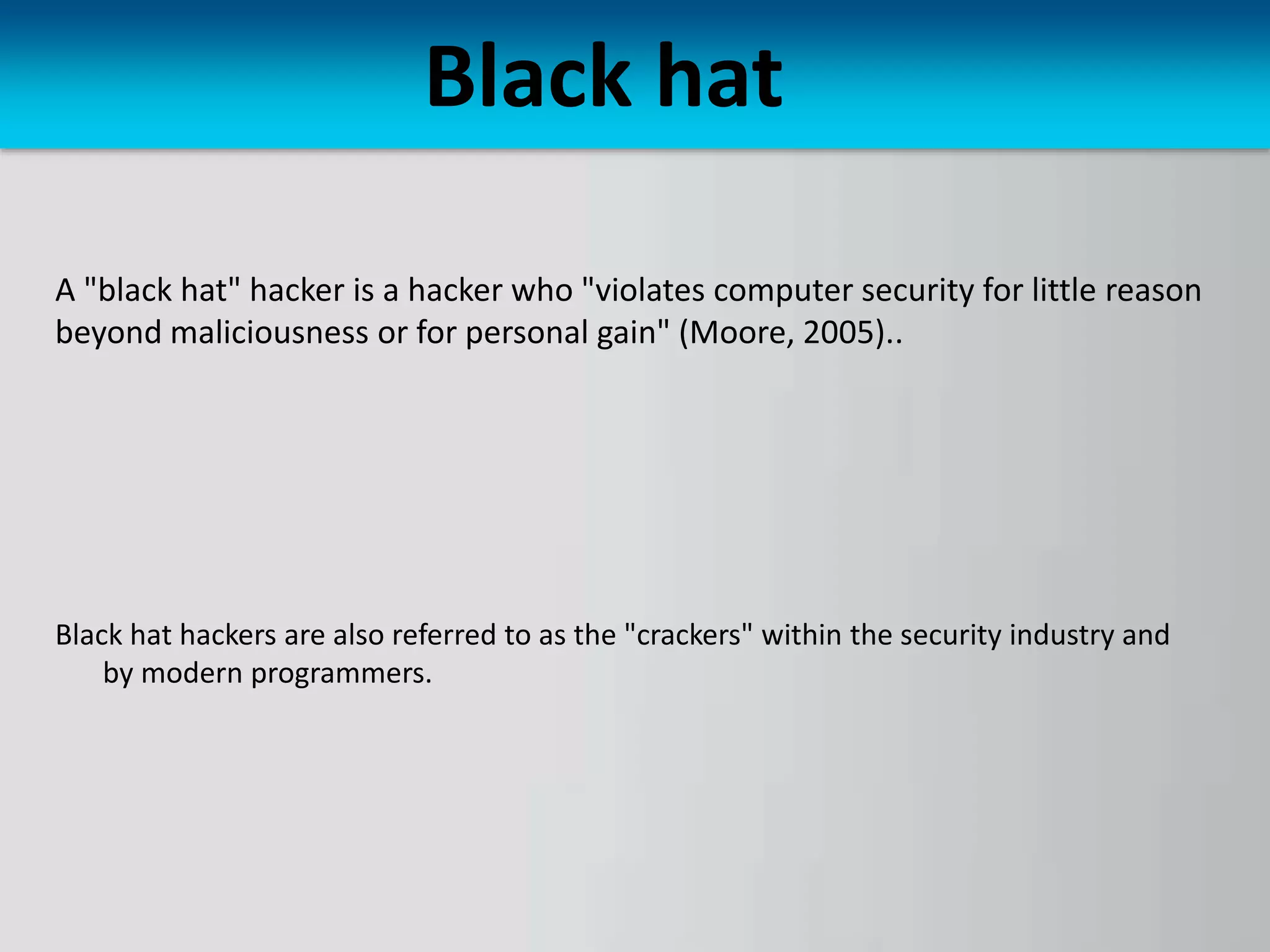
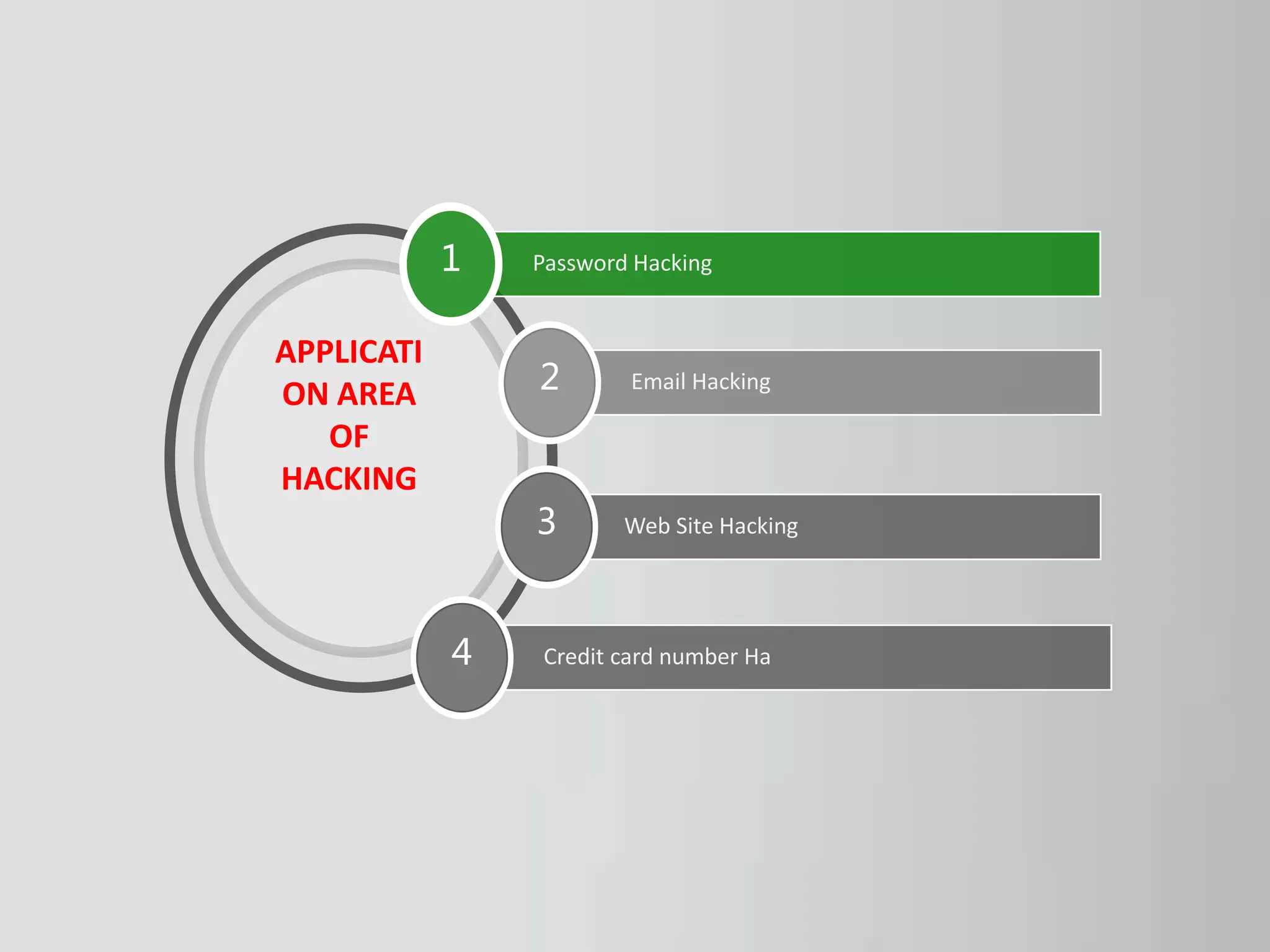
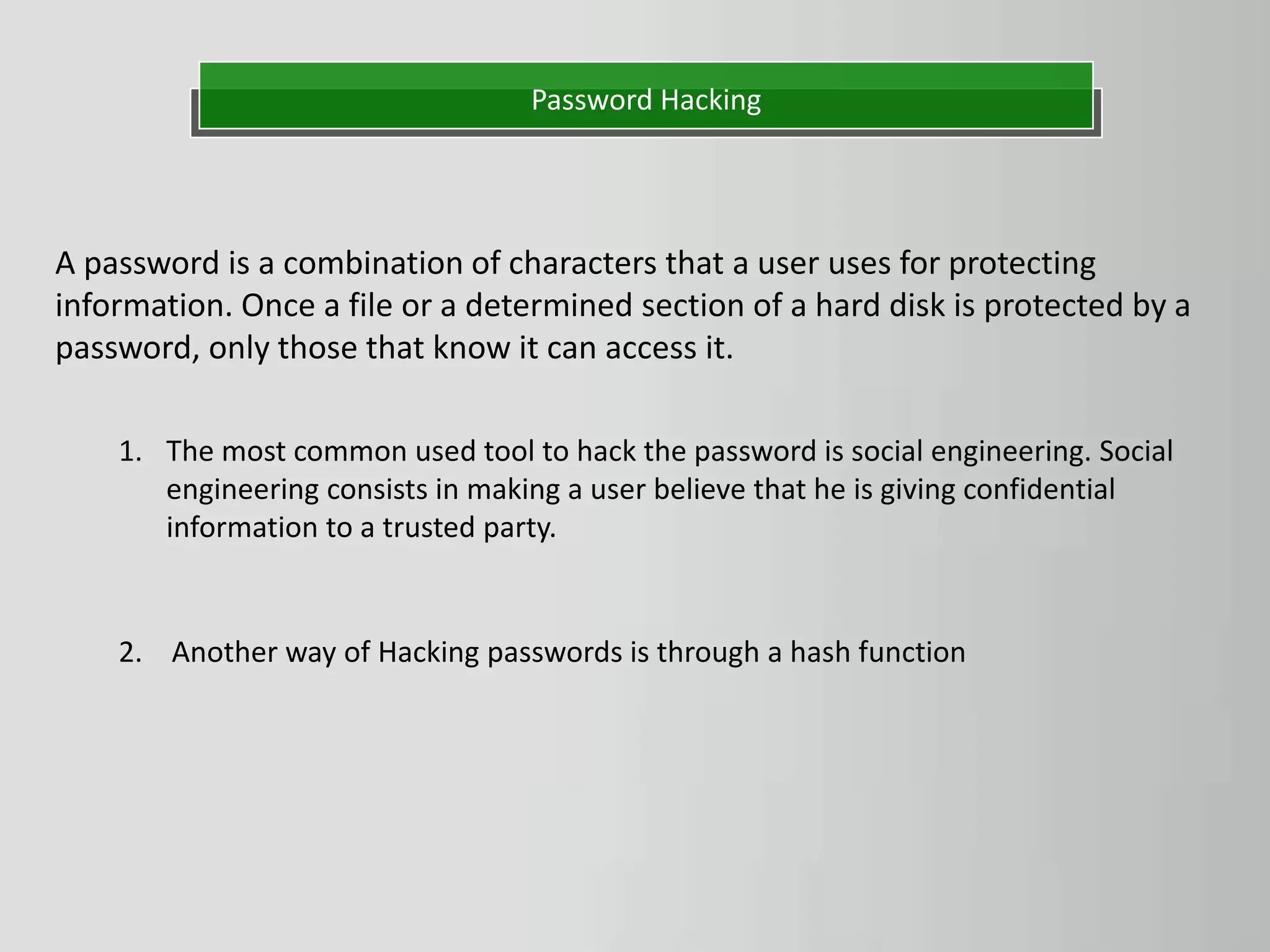
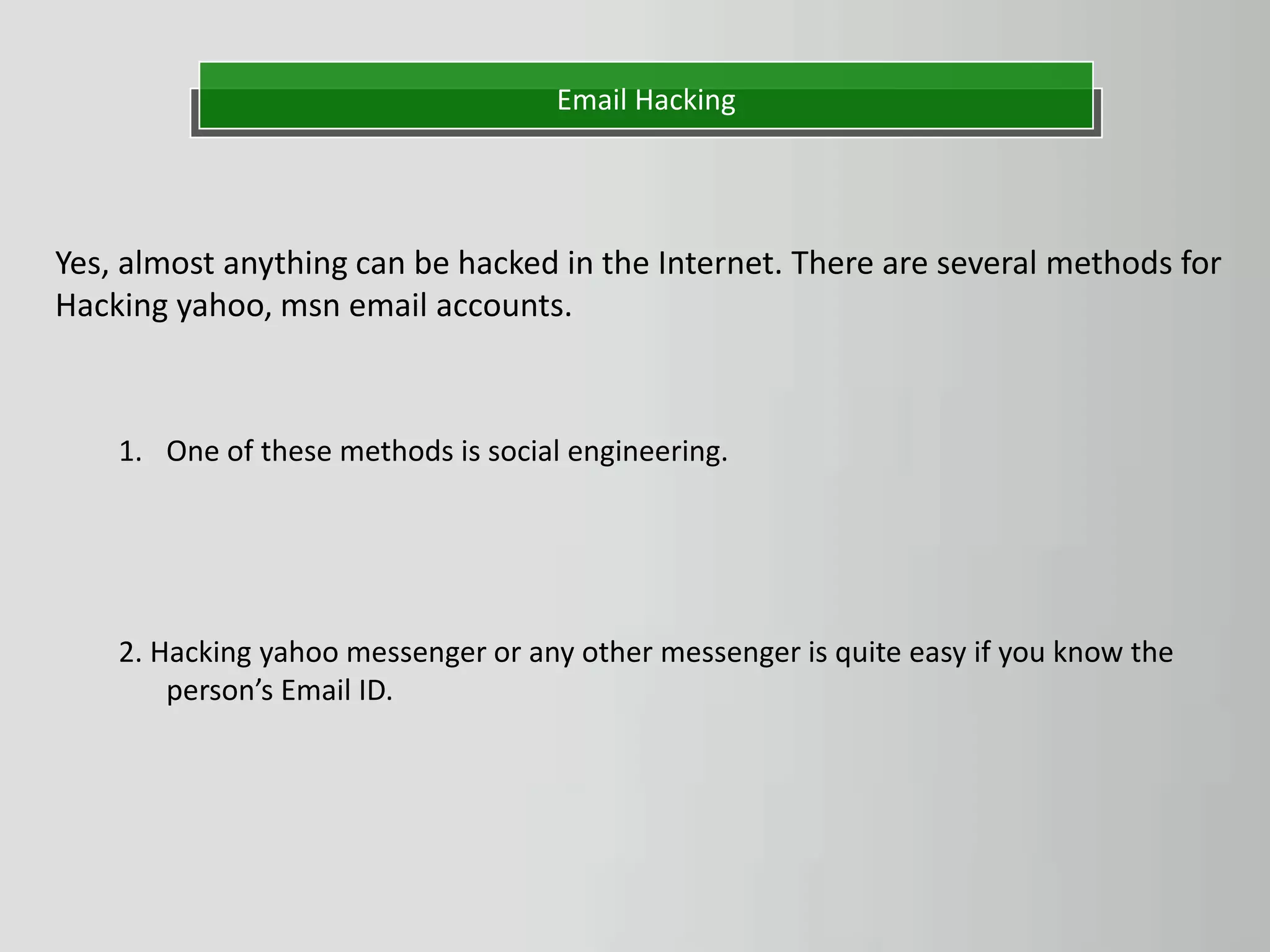
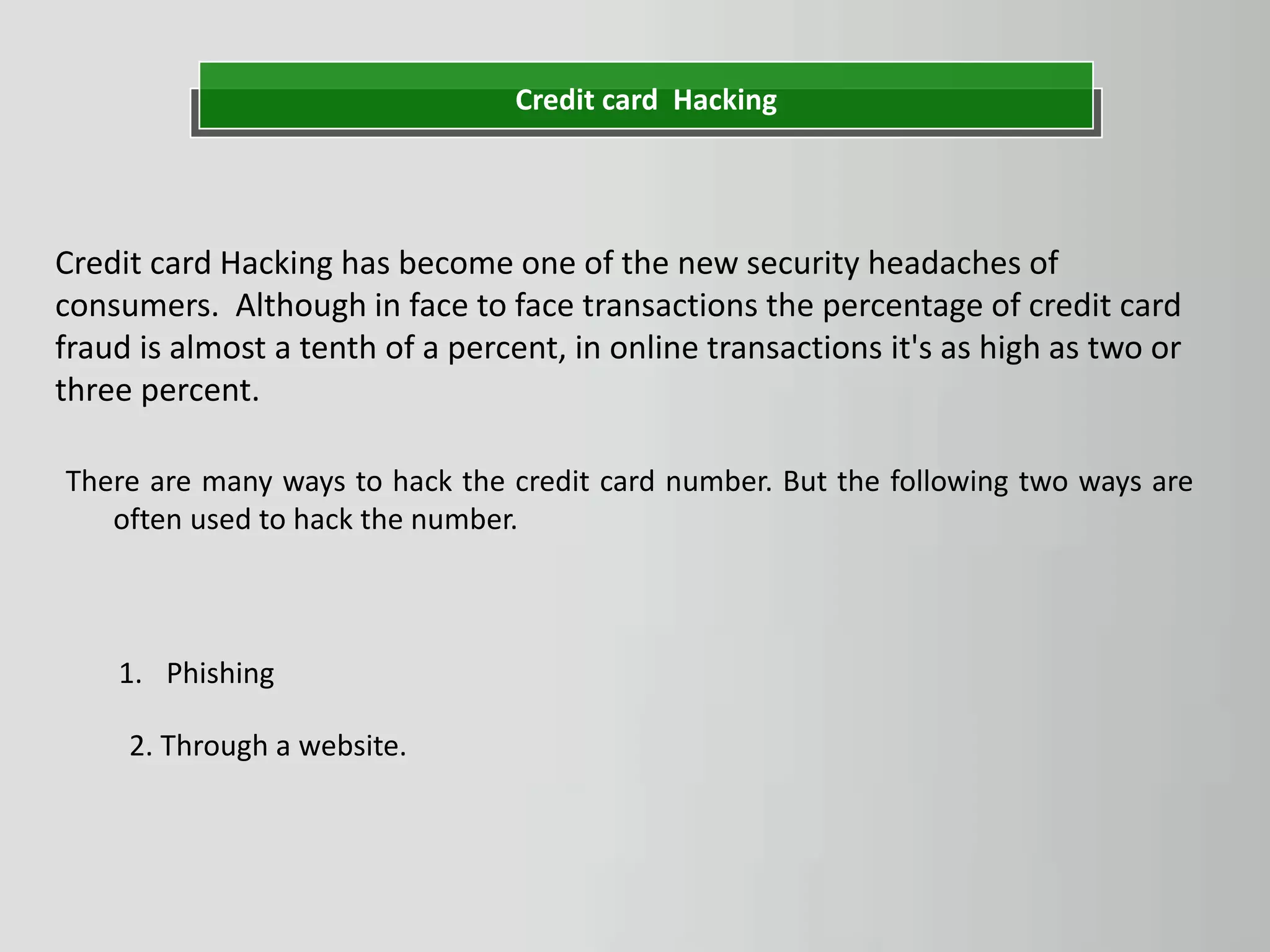
The document discusses hacking as the unauthorized access to information systems, categorizing hackers into three types: white hat (ethical hackers), black hat (malicious hackers), and grey hat (a mix of both). It also details various hacking methods including password, email, and credit card hacking, along with their advantages and disadvantages. While hacking can recover lost information and test security, it poses significant risks to privacy and can be illegal.