Cs tations-pps xversion
•Download as PPSX, PDF•
0 likes•51 views
This document discusses cyber security and the need to protect networks, computers, programs, and data from unauthorized access and damage. It addresses risks to computer security like loss of hardware, software, data, or information from breaches. Some breaches are accidental, but some are intentional computer crimes. It also discusses information systems security, access controls, security systems, cyber technology, computer protection methods like antivirus software, and the importance of protecting confidential information stored on computers. Key areas of cyber security addressed include data security, network security, application security, information security, and disaster recovery.
Report
Share
Report
Share
Recommended
Masters in cyber security

With Masters in cyber security you will learn how to protect computer operating systems, networks, and data from cyber attacks. Cyber security will give you the knowledge about different types of cyber attacks like Malware, Phishing and many more.
Masters in cyber security also provides you the tools, insight and sets of skills you need to fight against these cyber crimes.
CYBER SECURITY

This document is a presentation on cyber security submitted by four students. It discusses the meaning of cyber security and the need for it to protect online data and systems from threats. It then covers major security problems like viruses, hackers, malware, Trojan horses, and password cracking. For each threat, it provides details on what they are, examples, and solutions or methods for prevention and protection. The presentation concludes by discussing some big cyber attacks in 2016, why cyber security is important, advantages of cyber security, individual responsibilities, and confirms that while complete security is impossible, being aware and smart can help reduce risks.
SYSTEM SECURITY - Chapter 1 introduction

This document discusses the history of technology and consumer markets from the 1980s to present day. It covers the evolution of internet access from dial-up modems to always-on broadband connections. It describes the transition to home networks connecting various devices and the development of triple play services. The document also provides examples of network infrastructure including residential gateways and broadband termination units.
Cyber security

Cyber crime involves using computers and the internet to commit unlawful acts where the computer is either a tool or target. Cyber security protects networks, computers, programs and data from attacks, damage or unauthorized access. There are two categories of cyber crime - where the computer is the target, such as hacking, and where it is used as a weapon to commit real-world crimes like credit card fraud. Information systems were developed to help businesses run more efficiently compared to manual systems by providing regular information to managers through management information systems, keeping track of transactions through transaction processing systems, giving managers information to make decisions using decision support systems, helping top management plan strategies with executive information systems, and storing expert knowledge to make logical suggestions for users in expert
Homework0703

Network security consists of provisions made in an underlying computer network infrastructure and policies adopted by a network administrator to protect the network, accessible resources, and communication between hosts from unauthorized access and privacy threats. Effective network security requires authentication of users, intrusion prevention and detection systems, encryption of communications, and different levels of security management depending on the size and needs of the business or organization.
Cyber security

Cyber security refers to the technologies and processes designed to protect computers, networks and data from unauthorized access, vulnerabilities and attacks delivered via the Internet by cyber criminals.
It includes communication security, network security and information security.
The main problem increasing day by day is cyber crime. Crime committed using a computer and the internet to steal data or information is known as cyber crime. It is one of the disadvantages of internet. It is totally an illegal activity.
Cyber security-briefing-presentation

This document summarizes an Intel briefing on cybersecurity trends, solutions, and opportunities. It discusses how computing trends have expanded the attack surface and opportunities for malware. It then introduces Intel and McAfee's partnership and hardware-enhanced security solutions that work below the operating system level to detect advanced threats. Examples of solutions using hardware acceleration for encryption and virtualization-based security are provided. The briefing argues that hardware-enhanced approaches can improve security by establishing layered defenses and isolating critical functions from malware.
Cyber Security Predictions 2016

2015 cemented the saying “No one is immune to hacking” and the high profile breaches of Ashley Madison, LastPass and others was proof of that. Quick Heal detected close to 1.4 billion malware samples in 2015 and this number simply shows how widespread and lucrative cyber-attacks have now become. In this webinar, we will look back at some of the notable highlights from malware attacks in 2015, and then chart the way forward for 2016 and provide our listeners with a heads up on what kind of malware threats to expect. The webinar will cover the following points:
1. Malware detection statistics and highlights from 2015
2. Platform statistics for Windows and Android vulnerabilities
3. Insight into Ransomware and Exploit Kits in 2015
4. A look ahead at the cyber security predictions for 2016 and how we can help you
Recommended
Masters in cyber security

With Masters in cyber security you will learn how to protect computer operating systems, networks, and data from cyber attacks. Cyber security will give you the knowledge about different types of cyber attacks like Malware, Phishing and many more.
Masters in cyber security also provides you the tools, insight and sets of skills you need to fight against these cyber crimes.
CYBER SECURITY

This document is a presentation on cyber security submitted by four students. It discusses the meaning of cyber security and the need for it to protect online data and systems from threats. It then covers major security problems like viruses, hackers, malware, Trojan horses, and password cracking. For each threat, it provides details on what they are, examples, and solutions or methods for prevention and protection. The presentation concludes by discussing some big cyber attacks in 2016, why cyber security is important, advantages of cyber security, individual responsibilities, and confirms that while complete security is impossible, being aware and smart can help reduce risks.
SYSTEM SECURITY - Chapter 1 introduction

This document discusses the history of technology and consumer markets from the 1980s to present day. It covers the evolution of internet access from dial-up modems to always-on broadband connections. It describes the transition to home networks connecting various devices and the development of triple play services. The document also provides examples of network infrastructure including residential gateways and broadband termination units.
Cyber security

Cyber crime involves using computers and the internet to commit unlawful acts where the computer is either a tool or target. Cyber security protects networks, computers, programs and data from attacks, damage or unauthorized access. There are two categories of cyber crime - where the computer is the target, such as hacking, and where it is used as a weapon to commit real-world crimes like credit card fraud. Information systems were developed to help businesses run more efficiently compared to manual systems by providing regular information to managers through management information systems, keeping track of transactions through transaction processing systems, giving managers information to make decisions using decision support systems, helping top management plan strategies with executive information systems, and storing expert knowledge to make logical suggestions for users in expert
Homework0703

Network security consists of provisions made in an underlying computer network infrastructure and policies adopted by a network administrator to protect the network, accessible resources, and communication between hosts from unauthorized access and privacy threats. Effective network security requires authentication of users, intrusion prevention and detection systems, encryption of communications, and different levels of security management depending on the size and needs of the business or organization.
Cyber security

Cyber security refers to the technologies and processes designed to protect computers, networks and data from unauthorized access, vulnerabilities and attacks delivered via the Internet by cyber criminals.
It includes communication security, network security and information security.
The main problem increasing day by day is cyber crime. Crime committed using a computer and the internet to steal data or information is known as cyber crime. It is one of the disadvantages of internet. It is totally an illegal activity.
Cyber security-briefing-presentation

This document summarizes an Intel briefing on cybersecurity trends, solutions, and opportunities. It discusses how computing trends have expanded the attack surface and opportunities for malware. It then introduces Intel and McAfee's partnership and hardware-enhanced security solutions that work below the operating system level to detect advanced threats. Examples of solutions using hardware acceleration for encryption and virtualization-based security are provided. The briefing argues that hardware-enhanced approaches can improve security by establishing layered defenses and isolating critical functions from malware.
Cyber Security Predictions 2016

2015 cemented the saying “No one is immune to hacking” and the high profile breaches of Ashley Madison, LastPass and others was proof of that. Quick Heal detected close to 1.4 billion malware samples in 2015 and this number simply shows how widespread and lucrative cyber-attacks have now become. In this webinar, we will look back at some of the notable highlights from malware attacks in 2015, and then chart the way forward for 2016 and provide our listeners with a heads up on what kind of malware threats to expect. The webinar will cover the following points:
1. Malware detection statistics and highlights from 2015
2. Platform statistics for Windows and Android vulnerabilities
3. Insight into Ransomware and Exploit Kits in 2015
4. A look ahead at the cyber security predictions for 2016 and how we can help you
Cyber security

This slide provides details about cyber security as following;
what is cyber security or computer security?
why cyber security is important?
what is cyber crime?
cyber security problems,
how to prevent from cyber crime?
global scenario of cyber crime?
organisation in world for cyber security,
top companies in cyber security,
career choice in cyber security,
scope of cyber security.
Securing information system

This document discusses securing information systems. It defines an information system as a combination of hardware, software, infrastructure, and trained personnel used to collect, filter, process, create, and distribute data. The document outlines some threats to information systems like viruses, phishing, and application-specific hacks. It discusses three main security goals - integrity, availability, and confidentiality. Integrity aims to keep data trustworthy by protecting it from changes. Availability aims to keep data and resources accessible, especially during emergencies. Confidentiality preserves privacy through access control and encryption.
Ics & computer security for nuclear facilities

The document discusses computer security guidance for nuclear facilities' instrumentation and control (I&C) systems. It reviews Nuclear Security Series No. 17 (NSS-17) and a new publication NST036. NST036 aims to provide more robust guidance on applying computer security throughout the lifecycle of I&C systems, including addressing both safety and security considerations. It outlines key principles like prioritizing safety over security if there is a conflict. The document also discusses potential security controls and measures that could be applied to I&C systems, such as system hardening, application whitelisting, data diodes, and intrusion detection systems. It emphasizes the importance of considering computer security for vendors and during maintenance/testing activities involving
Incident handling of cyber espionage

Incident handling of intrusions related to cyber espionage operations is a complex and challenging task. As a national CERT with a unique national early warning detection system, NSM NorCERT has detected and responded to incidents that vary from traditional incident response and abuse handling to counter-intelligence operations. Based on some real-world examples, this talk will be about incident handling of cyber espionage intrusions. What are the most common pitfalls and how can companies be better prepared?
Cyber security

This document discusses cyber security and the need for protecting online information. It defines cyber security as protecting computer systems, software, data and services from disruption or theft. Common security threats are discussed such as viruses, hackers including white hat, grey hat and black hat hackers, malware like Trojan horses, and password cracking. The document provides solutions for implementing security like using antivirus software, firewalls, strong unique passwords, and backups.
CYBER SECURITY

This document discusses cyber security. It defines cyber security as technologies and processes designed to protect computers, networks, and data from unauthorized access and attacks over the internet. The three core principles of cyber security are confidentiality, integrity, and availability. Several types of cyber attacks are described such as malware, phishing, and denial of service attacks. Major historical cyber attacks are outlined including the Morris Worm in 1988 and the Anthem hack in 2015 that breached 80 million records. Common attack patterns and measures to prevent cyber attacks like using complex passwords and encryption are also summarized.
Cyber security and demonstration of security tools

Presentation on Cybersecurity and demonstration of security tools, conducted by Vicky Fernandes on 10th September 2019 at Don Bosco Institute of Technology, Mumbai.
Computer security

The presentation is being carried out to lay down a solution to a problem arising related to computer security
Cyber Security

Cyber security involves protecting computer systems and networks from criminal activity like fraud, theft, and blackmail. It aims to protect information and property while allowing authorized access. The field is growing due to increased internet connectivity of devices and the need to secure critical systems and infrastructure. Cyber security education covers traditional security topics like cryptography as well as emerging areas like cloud, mobile, and cyber-physical security. Career opportunities in cyber security include security analyst, engineer, architect, and administrator roles.
Cyber security

This document provides an introduction to cyber security. It discusses key concepts like confidentiality, integrity, and availability that are the goals of cyber security. Methods to achieve these goals are described, including encryption, access control, authentication, and physical protections. Cyber security skills and technologies like backups, check-sums, and computational redundancies that ensure integrity are also outlined. Finally, the document discusses various career opportunities in cyber security and lists common roles and job titles.
Cybersecurity

The document discusses cybersecurity issues including:
- The original open design of the internet lacked security concerns
- Cybersecurity issues can be classified by the type of action, perpetrator, and targets
- National and international initiatives have been established to address cybersecurity including organizations like DHS, ITU, UN, and policies on standards, legal measures, and capacity building
- Future e-commerce requires high cybersecurity but additional measures may impact privacy, such as regulations on encryption software.
Network Security

This document discusses the importance of security and how companies can protect themselves from a variety of cyber threats. It notes that cybercrime costs $575 billion per year and attacks are increasing rapidly. It then describes the types of attacks, including phishing, denial of service attacks, and SQL injection. Finally, it provides steps companies can take to enhance their security, such as implementing firewalls, access rules, encryption, and regular software updates. The key message is that all organizations are at risk from sophisticated hackers and must have appropriate security measures in place.
HIPAA, Privacy, Security, and Good Business

HIPAA's implications for privacy and security practices in American businesses, addressed in March of 2001 at the Employers' Summit on Health Care, by Stephen Cobb, CISSP. Uploaded in 2014 for the historical record.
Cyber Security & Information Warfare : A global security issue

Presentation : Vesalius Summer School 2018
Vesalius College | Royal Military Academy
Cyber Security & Information Warfare : A global security Issue
Bl cybersecurity z_dooly

This document provides an overview of a blended learning course on Introduction to Cybersecurity. The course is targeted at level 8 students in business information systems programs. It will be delivered over 5 weeks, with one face-to-face session per week along with pre-and post-activities. The expected time commitment is 5-8 hours per week. This presentation provides an overview of the first pillar - Cybersecurity Fundamentals. The course aims to introduce students to cybersecurity theory and applications. It will cover fundamentals, societal considerations, the state of the art, business opportunities, and more over the 5 weeks.
cyber security

Cyber security refers to technologies and processes designed to protect computers, networks, and data from unauthorized access and cyber attacks. It involves security standards that enable organizations to safely minimize successful cyber attacks. Cyber crime involves criminal acts conducted via the internet and where computers are tools or targets. Common cyber crimes include illegal access, interception, system interference, data interference, misuse of devices, and fraud. Proper cyber security through tools like antivirus software, firewalls, and strong unique passwords can help protect against cyber crimes.
Chapter 1 introduction(web security)

The document provides an overview of web security. It discusses the internet and the World Wide Web, vulnerabilities and threats to web applications like phishing and SQL injection, as well as countermeasures. It also outlines a generic security model covering security policies, host security, network security, organizational security, and legal security. Finally, it examines the components of web application architecture like user interface elements, structural components involving web browsers, application servers, and database servers.
Understanding the need for security measures

This document discusses basic security concepts and threats to users, hardware, and data from computers. It outlines threats such as identity theft, loss of privacy from data collection, cookies and spyware that track users, spam, power issues, theft, natural disasters, viruses, Trojan horses, cybercrime like internet fraud, hacking, distributed denial of service attacks, and cyber terrorism. It provides countermeasures for many of these threats, including anti-virus software, firewalls, spam filters, surge protectors, locking computers, backing up data, and government response teams.
Cyber Security

The document discusses an introduction to cyber security presented by Himansh Bhandari. It defines cyber security as the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. It discusses the history and evolution of the internet. It also covers types of malware like viruses, worms, Trojan horses and spyware. It discusses types of hackers like white hat, grey hat and black hat hackers. It provides information on implementing cyber security for mobile phones, banking and in India. It highlights major cyber security problems like viruses, hackers, malware and password cracking and discusses solutions to prevent them.
Security tools

This document discusses security frameworks and tools for information systems. It begins by explaining why systems are vulnerable, such as accessibility of networks and software/hardware problems. It then describes organizational frameworks for security, including risk assessment, security policies, identity management, disaster recovery planning, and information systems audits. Finally, it discusses tools for safeguarding resources, such as identity management software. The document provides an overview of securing information systems from multiple perspectives.
Cyber Security: A Hands on review

Cyber Security: A Hands on review on what is cyber security and how to prevent your devices from hacking and data breach. In today's era almost all devices are connected to internet are available for hackers to breach into and do their work. The data breach can be very dangerous and sometimes even more that it can demolish a company or a person.
In this presentation we will discuss about the ways and short description on Cyber Securty and Techniques.
More Related Content
What's hot
Cyber security

This slide provides details about cyber security as following;
what is cyber security or computer security?
why cyber security is important?
what is cyber crime?
cyber security problems,
how to prevent from cyber crime?
global scenario of cyber crime?
organisation in world for cyber security,
top companies in cyber security,
career choice in cyber security,
scope of cyber security.
Securing information system

This document discusses securing information systems. It defines an information system as a combination of hardware, software, infrastructure, and trained personnel used to collect, filter, process, create, and distribute data. The document outlines some threats to information systems like viruses, phishing, and application-specific hacks. It discusses three main security goals - integrity, availability, and confidentiality. Integrity aims to keep data trustworthy by protecting it from changes. Availability aims to keep data and resources accessible, especially during emergencies. Confidentiality preserves privacy through access control and encryption.
Ics & computer security for nuclear facilities

The document discusses computer security guidance for nuclear facilities' instrumentation and control (I&C) systems. It reviews Nuclear Security Series No. 17 (NSS-17) and a new publication NST036. NST036 aims to provide more robust guidance on applying computer security throughout the lifecycle of I&C systems, including addressing both safety and security considerations. It outlines key principles like prioritizing safety over security if there is a conflict. The document also discusses potential security controls and measures that could be applied to I&C systems, such as system hardening, application whitelisting, data diodes, and intrusion detection systems. It emphasizes the importance of considering computer security for vendors and during maintenance/testing activities involving
Incident handling of cyber espionage

Incident handling of intrusions related to cyber espionage operations is a complex and challenging task. As a national CERT with a unique national early warning detection system, NSM NorCERT has detected and responded to incidents that vary from traditional incident response and abuse handling to counter-intelligence operations. Based on some real-world examples, this talk will be about incident handling of cyber espionage intrusions. What are the most common pitfalls and how can companies be better prepared?
Cyber security

This document discusses cyber security and the need for protecting online information. It defines cyber security as protecting computer systems, software, data and services from disruption or theft. Common security threats are discussed such as viruses, hackers including white hat, grey hat and black hat hackers, malware like Trojan horses, and password cracking. The document provides solutions for implementing security like using antivirus software, firewalls, strong unique passwords, and backups.
CYBER SECURITY

This document discusses cyber security. It defines cyber security as technologies and processes designed to protect computers, networks, and data from unauthorized access and attacks over the internet. The three core principles of cyber security are confidentiality, integrity, and availability. Several types of cyber attacks are described such as malware, phishing, and denial of service attacks. Major historical cyber attacks are outlined including the Morris Worm in 1988 and the Anthem hack in 2015 that breached 80 million records. Common attack patterns and measures to prevent cyber attacks like using complex passwords and encryption are also summarized.
Cyber security and demonstration of security tools

Presentation on Cybersecurity and demonstration of security tools, conducted by Vicky Fernandes on 10th September 2019 at Don Bosco Institute of Technology, Mumbai.
Computer security

The presentation is being carried out to lay down a solution to a problem arising related to computer security
Cyber Security

Cyber security involves protecting computer systems and networks from criminal activity like fraud, theft, and blackmail. It aims to protect information and property while allowing authorized access. The field is growing due to increased internet connectivity of devices and the need to secure critical systems and infrastructure. Cyber security education covers traditional security topics like cryptography as well as emerging areas like cloud, mobile, and cyber-physical security. Career opportunities in cyber security include security analyst, engineer, architect, and administrator roles.
Cyber security

This document provides an introduction to cyber security. It discusses key concepts like confidentiality, integrity, and availability that are the goals of cyber security. Methods to achieve these goals are described, including encryption, access control, authentication, and physical protections. Cyber security skills and technologies like backups, check-sums, and computational redundancies that ensure integrity are also outlined. Finally, the document discusses various career opportunities in cyber security and lists common roles and job titles.
Cybersecurity

The document discusses cybersecurity issues including:
- The original open design of the internet lacked security concerns
- Cybersecurity issues can be classified by the type of action, perpetrator, and targets
- National and international initiatives have been established to address cybersecurity including organizations like DHS, ITU, UN, and policies on standards, legal measures, and capacity building
- Future e-commerce requires high cybersecurity but additional measures may impact privacy, such as regulations on encryption software.
Network Security

This document discusses the importance of security and how companies can protect themselves from a variety of cyber threats. It notes that cybercrime costs $575 billion per year and attacks are increasing rapidly. It then describes the types of attacks, including phishing, denial of service attacks, and SQL injection. Finally, it provides steps companies can take to enhance their security, such as implementing firewalls, access rules, encryption, and regular software updates. The key message is that all organizations are at risk from sophisticated hackers and must have appropriate security measures in place.
HIPAA, Privacy, Security, and Good Business

HIPAA's implications for privacy and security practices in American businesses, addressed in March of 2001 at the Employers' Summit on Health Care, by Stephen Cobb, CISSP. Uploaded in 2014 for the historical record.
Cyber Security & Information Warfare : A global security issue

Presentation : Vesalius Summer School 2018
Vesalius College | Royal Military Academy
Cyber Security & Information Warfare : A global security Issue
Bl cybersecurity z_dooly

This document provides an overview of a blended learning course on Introduction to Cybersecurity. The course is targeted at level 8 students in business information systems programs. It will be delivered over 5 weeks, with one face-to-face session per week along with pre-and post-activities. The expected time commitment is 5-8 hours per week. This presentation provides an overview of the first pillar - Cybersecurity Fundamentals. The course aims to introduce students to cybersecurity theory and applications. It will cover fundamentals, societal considerations, the state of the art, business opportunities, and more over the 5 weeks.
cyber security

Cyber security refers to technologies and processes designed to protect computers, networks, and data from unauthorized access and cyber attacks. It involves security standards that enable organizations to safely minimize successful cyber attacks. Cyber crime involves criminal acts conducted via the internet and where computers are tools or targets. Common cyber crimes include illegal access, interception, system interference, data interference, misuse of devices, and fraud. Proper cyber security through tools like antivirus software, firewalls, and strong unique passwords can help protect against cyber crimes.
Chapter 1 introduction(web security)

The document provides an overview of web security. It discusses the internet and the World Wide Web, vulnerabilities and threats to web applications like phishing and SQL injection, as well as countermeasures. It also outlines a generic security model covering security policies, host security, network security, organizational security, and legal security. Finally, it examines the components of web application architecture like user interface elements, structural components involving web browsers, application servers, and database servers.
Understanding the need for security measures

This document discusses basic security concepts and threats to users, hardware, and data from computers. It outlines threats such as identity theft, loss of privacy from data collection, cookies and spyware that track users, spam, power issues, theft, natural disasters, viruses, Trojan horses, cybercrime like internet fraud, hacking, distributed denial of service attacks, and cyber terrorism. It provides countermeasures for many of these threats, including anti-virus software, firewalls, spam filters, surge protectors, locking computers, backing up data, and government response teams.
Cyber Security

The document discusses an introduction to cyber security presented by Himansh Bhandari. It defines cyber security as the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. It discusses the history and evolution of the internet. It also covers types of malware like viruses, worms, Trojan horses and spyware. It discusses types of hackers like white hat, grey hat and black hat hackers. It provides information on implementing cyber security for mobile phones, banking and in India. It highlights major cyber security problems like viruses, hackers, malware and password cracking and discusses solutions to prevent them.
Security tools

This document discusses security frameworks and tools for information systems. It begins by explaining why systems are vulnerable, such as accessibility of networks and software/hardware problems. It then describes organizational frameworks for security, including risk assessment, security policies, identity management, disaster recovery planning, and information systems audits. Finally, it discusses tools for safeguarding resources, such as identity management software. The document provides an overview of securing information systems from multiple perspectives.
What's hot (20)
Ics & computer security for nuclear facilities

Ics & computer security for nuclear facilities
Cyber security and demonstration of security tools

Cyber security and demonstration of security tools
Cyber Security & Information Warfare : A global security issue

Cyber Security & Information Warfare : A global security issue
Similar to Cs tations-pps xversion
Cyber Security: A Hands on review

Cyber Security: A Hands on review on what is cyber security and how to prevent your devices from hacking and data breach. In today's era almost all devices are connected to internet are available for hackers to breach into and do their work. The data breach can be very dangerous and sometimes even more that it can demolish a company or a person.
In this presentation we will discuss about the ways and short description on Cyber Securty and Techniques.
Security & control in management information system

The document discusses security concepts in information systems including prevention of unauthorized access, modification, and deletion of information. It outlines unintentional threats like human error and intentional threats like criminal attacks. The goals of information security are prevention, detection, and response. Risks to applications and data include computer crime, hacking, cyber-theft, unauthorized work use, software piracy, and viruses/worms. Risks to hardware include natural disasters, blackouts, and vandalism. Major defense strategies are encryption, authentication, firewalls, email monitoring, antivirus software, backup files, security monitors, and biometric controls. The document also discusses disaster recovery, business recovery plans, and general controls to minimize errors and disasters.
Computer Security

Computer security aims to protect computing systems and data from threats. It operates on multiple layers including physical, network, system, application, and user security. The key objectives of computer security are confidentiality, integrity, and availability of systems and data. To be secured, computer security addresses hardware, software, communications, and data. It emphasizes precaution, maintenance, and timely reaction to incidents. Risks to computer security include malware, email, and network attacks as well as identity theft. Computer security faces challenges due to complex algorithms, counterintuitive procedures, and need to consider potential attacks. Awareness of computer security helps minimize attacks and protect information and resources.
internet securityand cyber law Unit2

This document discusses security investigations and the need for information security in organizations. It outlines four main functions of information security: 1) protecting organizational functionality, 2) enabling safe application operations, 3) protecting collected data, and 4) safeguarding technology assets. It then discusses threats to information security such as human error, espionage, software attacks, and natural disasters. Specific threats include viruses, worms, Trojan horses, backdoors, and denial of service attacks. The document also covers categories of attacks like malicious code, IP scanning, and social engineering.
Chapter1 intro network_security_sunorganised

The document provides an overview of network security concepts. It begins by defining various types of malware like viruses, worms, spyware, ransomware, and trojans. It then discusses security policies, information security, aspects of information security including threats and vulnerabilities. It defines network security and its goals of confidentiality, integrity and availability. It describes aspects of network security including privacy, message integrity, authentication and non-repudiation. It then discusses cyber security and its main categories. It defines the different levels of impact from security breaches and types of attacks like passive, active, interruption, fabrication and modification. Finally, it provides an overview of networking devices and protocols at different layers of the OSI model as well as firewall
Lec 1- Intro to cyber security and recommendations

This document provides an overview of cyber security. It defines security, cyber security, and computer security. It discusses why security is important for businesses and lists common cyber security domains like network security, endpoint security, cloud security, and mobile security. It also covers ethical hacking, skills required to be an ethical hacker, common vulnerabilities they identify, and examples of famous ethical and malicious hackers like Kevin Mitnick. Finally, it briefly summarizes some major cyber security incidents like attacks on Iran and the largest DDoS attack.
DATA SECURITY AND CONTROL.ppt

There are three core principles of data security: confidentiality, integrity, and availability. Confidentiality means that sensitive data should not be accessed by unauthorized individuals. Integrity refers to ensuring data is not modified without permission. Availability means information must be accessible on demand. Data security controls aim to protect data from threats like unauthorized access, alteration, and destruction. Common threats include malware, hacking, and data loss from system failures. Organizations implement measures like encryption, firewalls, and monitoring to prevent threats and ensure the security of their data and IT systems.
Cyber-Security-Unit-1.pptx

The document provides an overview of cyber security, including its importance, key domains and types. It discusses network security, application security, information security, identity management, operational security and other areas. It defines cyber security as protecting networks, devices, programs and data from threats. The document also covers cyber threats, vulnerabilities, cyber warfare, cyber terrorism and the need for critical infrastructure security. It provides examples and details for concepts like the CIA triad of confidentiality, integrity and availability.
Cybersecurity_Issues and challenges.pptx

Cybersecurity involves defending computers and networks from malicious attacks. Key issues include unprecedented attacks, cyber espionage, data theft, ransomware targeting IoT devices, mobile device attacks, and phishing. Challenges to cybersecurity are staying ahead of threats through cloud security, addressing how AI enables attacks and prevention, and risks from social engineering, deep fakes, and smart contract hacking. Regular security audits, awareness training, strong unique passwords, antivirus software, backups, and encryption can help brace against cyberthreats as criminals pursue new exploits.
Computer security overview

COMPUTER SECURITY
KEY SECURITY CONCEPTS
SECURITY TERMINOLOGY
VULNERABILITY
THREATS
ATTACKS
ATTACK SURFACES
THREAT CONSEQUENCES
COUNTERMEASURES
CYBER CRIME INCIDENTS IN OMAN
SECURITY TECHNOLOGIES IN USE - GLOBAL
Network security

This document provides an introduction to network security. It discusses the history of network security, including early networks in universities and government and the Morris Worm in 1988. The document outlines common security threats like intrusion, interception, and modification and their countermeasures such as firewalls, intrusion detection systems, encryption, and education. It defines network security objectives including identification, authentication, and access controls. Finally, the document lists elements of a comprehensive security program and advantages of network security like protecting data, information, and physical computers from external attacks.
Network Security

Network security is important to protect vital information while allowing authorized access. Key aspects of network security include identifying vulnerabilities, threats like hackers and methods of attack, and implementing appropriate countermeasures. Common attacks include password attacks, viruses, and packet sniffing. Effective countermeasures include firewalls to control access, intrusion detection systems to monitor for exploits, IPsec and encryption to secure communications, and user education to address social engineering vulnerabilities. Comprehensive security requires backups, encryption, virus protection, firewalls, monitoring, training, and testing defenses.
Information Technology Security Basics

The document discusses various topics related to IT security basics. It begins by providing two examples of security breaches to illustrate why security is important. It then discusses the four virtues of security and the nine rules of security. The document also defines information security, its goal of ensuring confidentiality, integrity and availability of systems, and the potential impacts of security failures. Additionally, it outlines common security definitions, 10 security domains, and provides an overview of access control and application security.
SumitSingh51.pptx

Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
· Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
· Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed.
· Information security protects the integrity and privacy of data, both in storage and in transit.
· Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
· Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources.
· End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
The scale of the cyber threat
The global cyber threat continues to evolve at a rapid pace, with a rising number of data breaches each year. A report by RiskBased Security revealed that a shocking 7.9 billion records have been exposed by data breaches in the first nine months of 2019 alone. This figure is more than double (112%) the number of records exposed in the same period in 2018.
Medical services, retailers and public entities experienced the most breaches, with malicious criminals responsible for most incidents. Some of these sectors are more appealing to cybercriminals because they collect financial and medical data, but all businesses that use networks can be targeted for customer data, corporate espionage, or customer attacks.
With the scale of the cyber threat set to continue to rise, the International Data Corporation predicts that worldwide spending on cyber-security solutions will reach a massive $133.7 billion by 2022. Governments across the globe have responded to the rising cyber threat w
Cloud Security.pptx

The document discusses key concepts in cloud security including confidentiality, integrity, and availability (CIA triad). It also covers vulnerabilities, threats, attacks, and countermeasures. The objectives of cloud security are to protect systems, data, information, and build trust by preventing attacks, detecting breaches, defending against threats, and deterring attackers through appropriate security measures.
IS Unit II.pptx

This document discusses legal, ethical, and professional issues in information security. It begins by outlining the objectives and outcomes of the lesson, which are to understand these issues. It then provides an overview of security needs like ensuring business continuity, threats like human error and cyber attacks, and how businesses rely on information security to protect functionality, applications, data, and technology assets. Examples of common attacks are also described like malware, backdoors, password cracking, and spoofing. The document emphasizes understanding security needs and threats to make informed decisions about protecting an organization's information.
Computer-Security.pptx

This document discusses computer security and various cyber threats. It begins by explaining how computer security became increasingly important with the development of modems and personal computers in the late 20th century. It then discusses different methods used to protect computer systems and information, including serial numbers, locks, alarms, and various security strategies to address threats like data theft, vandalism, fraud, and privacy invasion. The document also provides definitions and examples of cryptography, encryption, malware, and other cyber attacks like phishing, watering hole attacks, and cybercrime. It concludes by listing some common reasons for web threats and tips to protect against web service attacks, such as backups, multi-factor authentication, malware scanning, and keeping software updated.
Chapter 13

This document discusses electronic security in computer networks. It covers securing network information through confidentiality, availability, and integrity. It describes authentication of users, acceptable use policies, and information integrity. It also discusses threats to security like hackers, viruses, and malicious insiders. Finally, it outlines security tools like firewalls, proxy servers, and intrusion detection systems that can help secure networks.
Information Systems.pptx

This document provides an overview of information systems and security topics including computer security, authentication mechanisms, firewalls, computer crimes, social impacts of computers, computer viruses, worms, digital signatures and certificates. It discusses information security principles of confidentiality, integrity and availability. It also covers specific authentication mechanisms like passwords, multi-factor authentication, certificates, tokens and biometrics. Additionally, it defines what a firewall is and how it works to inspect and block unauthorized network traffic based on packet rules.
Similar to Cs tations-pps xversion (20)
Lecture 01 Information Security BS computer Science

Lecture 01 Information Security BS computer Science
Security & control in management information system

Security & control in management information system
Lec 1- Intro to cyber security and recommendations

Lec 1- Intro to cyber security and recommendations
Recently uploaded
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

Imagine a world where machines not only perform tasks but also learn, adapt, and make decisions. This is the promise of Artificial Intelligence (AI), a technology that's not just enhancing our lives but revolutionizing entire industries.
Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on integration of Salesforce with Bonterra Impact Management.
Interested in deploying an integration with Salesforce for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
Columbus Data & Analytics Wednesdays - June 2024

Columbus Data & Analytics Wednesdays, June 2024 with Maria Copot 20
Digital Marketing Trends in 2024 | Guide for Staying Ahead

https://www.wask.co/ebooks/digital-marketing-trends-in-2024
Feeling lost in the digital marketing whirlwind of 2024? Technology is changing, consumer habits are evolving, and staying ahead of the curve feels like a never-ending pursuit. This e-book is your compass. Dive into actionable insights to handle the complexities of modern marketing. From hyper-personalization to the power of user-generated content, learn how to build long-term relationships with your audience and unlock the secrets to success in the ever-shifting digital landscape.
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Discover how MongoDB Atlas and vector search technology can revolutionize your application's search capabilities. This comprehensive presentation covers:
* What is Vector Search?
* Importance and benefits of vector search
* Practical use cases across various industries
* Step-by-step implementation guide
* Live demos with code snippets
* Enhancing LLM capabilities with vector search
* Best practices and optimization strategies
Perfect for developers, AI enthusiasts, and tech leaders. Learn how to leverage MongoDB Atlas to deliver highly relevant, context-aware search results, transforming your data retrieval process. Stay ahead in tech innovation and maximize the potential of your applications.
#MongoDB #VectorSearch #AI #SemanticSearch #TechInnovation #DataScience #LLM #MachineLearning #SearchTechnology
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
Webinar: Designing a schema for a Data Warehouse

Are you new to data warehouses (DWH)? Do you need to check whether your data warehouse follows the best practices for a good design? In both cases, this webinar is for you.
A data warehouse is a central relational database that contains all measurements about a business or an organisation. This data comes from a variety of heterogeneous data sources, which includes databases of any type that back the applications used by the company, data files exported by some applications, or APIs provided by internal or external services.
But designing a data warehouse correctly is a hard task, which requires gathering information about the business processes that need to be analysed in the first place. These processes must be translated into so-called star schemas, which means, denormalised databases where each table represents a dimension or facts.
We will discuss these topics:
- How to gather information about a business;
- Understanding dictionaries and how to identify business entities;
- Dimensions and facts;
- Setting a table granularity;
- Types of facts;
- Types of dimensions;
- Snowflakes and how to avoid them;
- Expanding existing dimensions and facts.
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
HCL Notes and Domino License Cost Reduction in the World of DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-and-domino-license-cost-reduction-in-the-world-of-dlau/
The introduction of DLAU and the CCB & CCX licensing model caused quite a stir in the HCL community. As a Notes and Domino customer, you may have faced challenges with unexpected user counts and license costs. You probably have questions on how this new licensing approach works and how to benefit from it. Most importantly, you likely have budget constraints and want to save money where possible. Don’t worry, we can help with all of this!
We’ll show you how to fix common misconfigurations that cause higher-than-expected user counts, and how to identify accounts which you can deactivate to save money. There are also frequent patterns that can cause unnecessary cost, like using a person document instead of a mail-in for shared mailboxes. We’ll provide examples and solutions for those as well. And naturally we’ll explain the new licensing model.
Join HCL Ambassador Marc Thomas in this webinar with a special guest appearance from Franz Walder. It will give you the tools and know-how to stay on top of what is going on with Domino licensing. You will be able lower your cost through an optimized configuration and keep it low going forward.
These topics will be covered
- Reducing license cost by finding and fixing misconfigurations and superfluous accounts
- How do CCB and CCX licenses really work?
- Understanding the DLAU tool and how to best utilize it
- Tips for common problem areas, like team mailboxes, functional/test users, etc
- Practical examples and best practices to implement right away
Recently uploaded (20)
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
AI 101: An Introduction to the Basics and Impact of Artificial Intelligence

AI 101: An Introduction to the Basics and Impact of Artificial Intelligence
Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...

Salesforce Integration for Bonterra Impact Management (fka Social Solutions A...
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Digital Marketing Trends in 2024 | Guide for Staying Ahead

Digital Marketing Trends in 2024 | Guide for Staying Ahead
Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf

Unlock the Future of Search with MongoDB Atlas_ Vector Search Unleashed.pdf
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
HCL Notes and Domino License Cost Reduction in the World of DLAU

HCL Notes and Domino License Cost Reduction in the World of DLAU
Cs tations-pps xversion
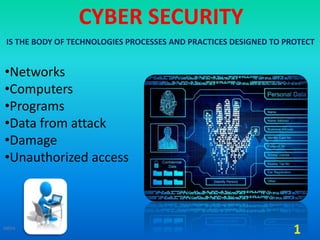
- 1. •Networks •Computers •Programs •Data from attack •Damage •Unauthorized access CYBER SECURITY 1 IS THE BODY OF TECHNOLOGIES PROCESSES AND PRACTICES DESIGNED TO PROTECT Jatins
- 2. •Loss or damage to computer hardware •Software •Data • Information Some breaches to computer security are accidental, but some are planned. Any illegal act involving a computer is generally referred to as a computer crime. RISKS OF COMPUTER SECURITY 2Jatins
- 3. Information systems security is INFOSEC, refers to the processes and methodologies involved with keeping : •Information confidential •Available •Assuring its integrity It also refers to: Access controls, which prevent unauthorized personnel from entering or accessing a system. SECURITY SYSTEM 3Jatins
- 4. CYBER TECHNOLOGY 4 Field of technology that deals with the development of: •Artificial devices •Machines •Techniques •Intelligence •Components Jatins
- 5. 5Jatins
- 6. Virus protection software is designed to prevent viruses, worms and Trojan horses from getting onto a computer as well as remove any malicious software code that has already infected computer. COMPUTER PROTECTION 6Jatins
- 7. Governments, military, corporations, financial institutions, hospitals and other businesses collect, process and store a great deal of confidential information on computers and transmit that data across networks to other computers. With the growing volume and sophistication of cyber attacks, ongoing attention is required to protect sensitive business and personal information, as well as safeguard national security. 7Jatins
- 8. AREAS OF CYBER SECURITY 8 Data in a database or on the file system or a system resource unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability Disaster recovery is the area of security planning that deals with protecting an organization from the effects of significant negative events. policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Application Security Information Security Disaster recovery Network Security Jatins
- 9. 9Jatins Weakness Exploitation of Weakness Protections on Weakness Plan to reduce Threats Identify Threats Cyber Securities
- 10. 10 SECURE COMPUTER FROM ONLINE THREATS WHILE SURFING INTERNET 1. Enable windows automatic updates feature 2. Install antivirus software 3. Activate windows firewall 4. Enable pop up blocker of your browser 5. Clean cookies and session data after using internet 6. Be aware from email spam 7. Be aware from phishing and internet frauds Jatins
- 11. 11Jatins
- 12. COMPUTER SECURITY - THREATS • Intrusions – Any attempt to gain unauthorized access to a system – Cracking – Hacking – Social Engineering – War-driving
- 13. WHAT IS CYBERCRIME? • Using the Internet to commit a crime. – Identity Theft – Hacking – Virus • Facilitation of traditional criminal activity – Stalking – Stealing information – Child Pornography
- 14. CYBERCRIME COMPONENTS • Computers • Cell Phones • PDA’s • Game Consoles
- 15. COMPUTER SECURITY - TERMINOLOGY • Script Kiddies – Someone that calls themselves a ‘hacker’ but really isn’t • Ethical Hacker – Someone hired to hack a system to find vulnerabilities and report on them. – Also called a ‘sneaker’
- 16. Jatins 16
- 17. Allow a program or feature through window Firewall
- 18. 18Jatins Setting for each type of Network
- 19. 19Jatins
- 20. 20Jatins
- 21. 21Jatins
- 22. 22Jatins
- 23. 23Jatins
- 24. 24Jatins
- 25. 25Jatins
- 26. 26Jatins
