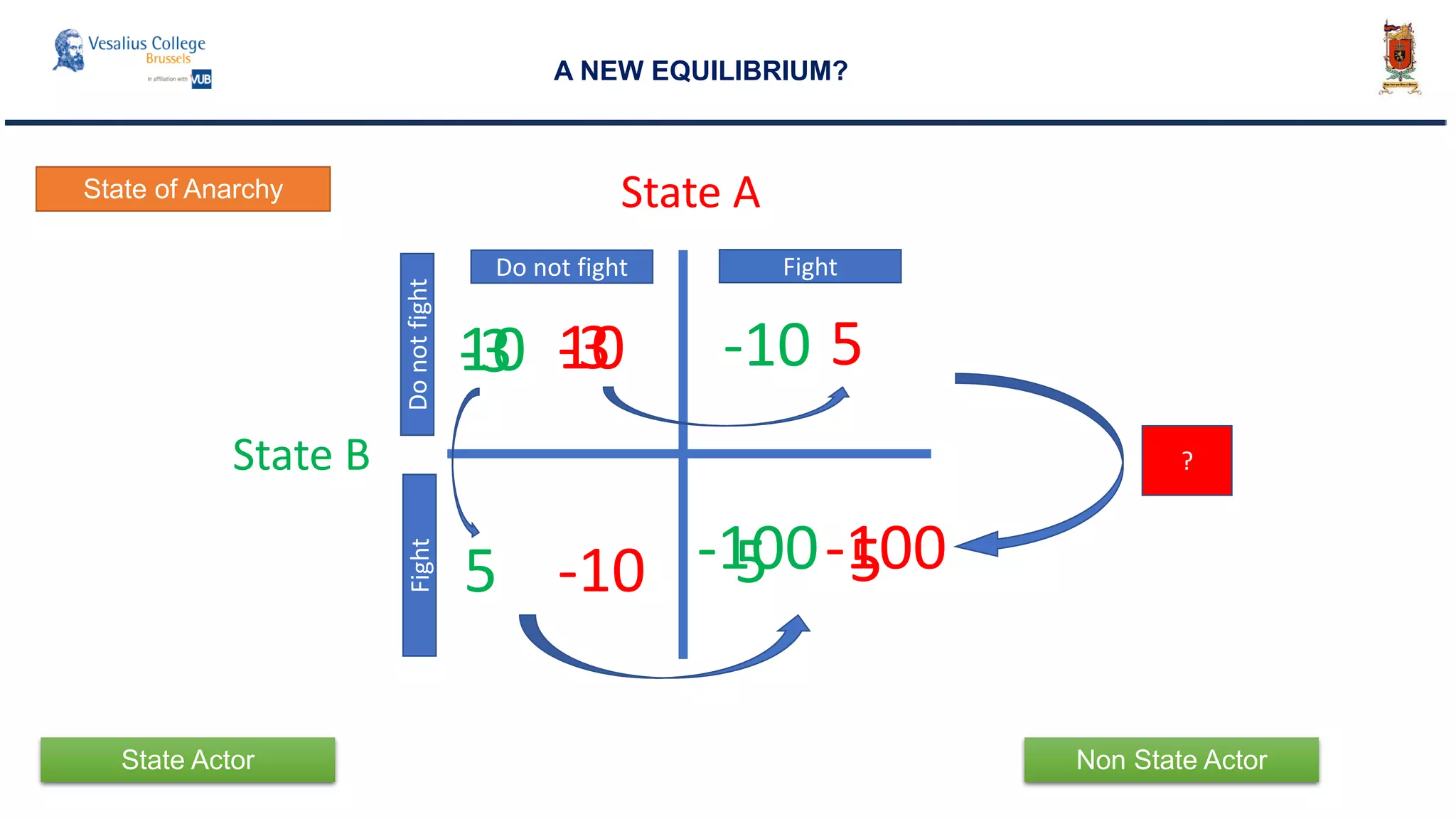
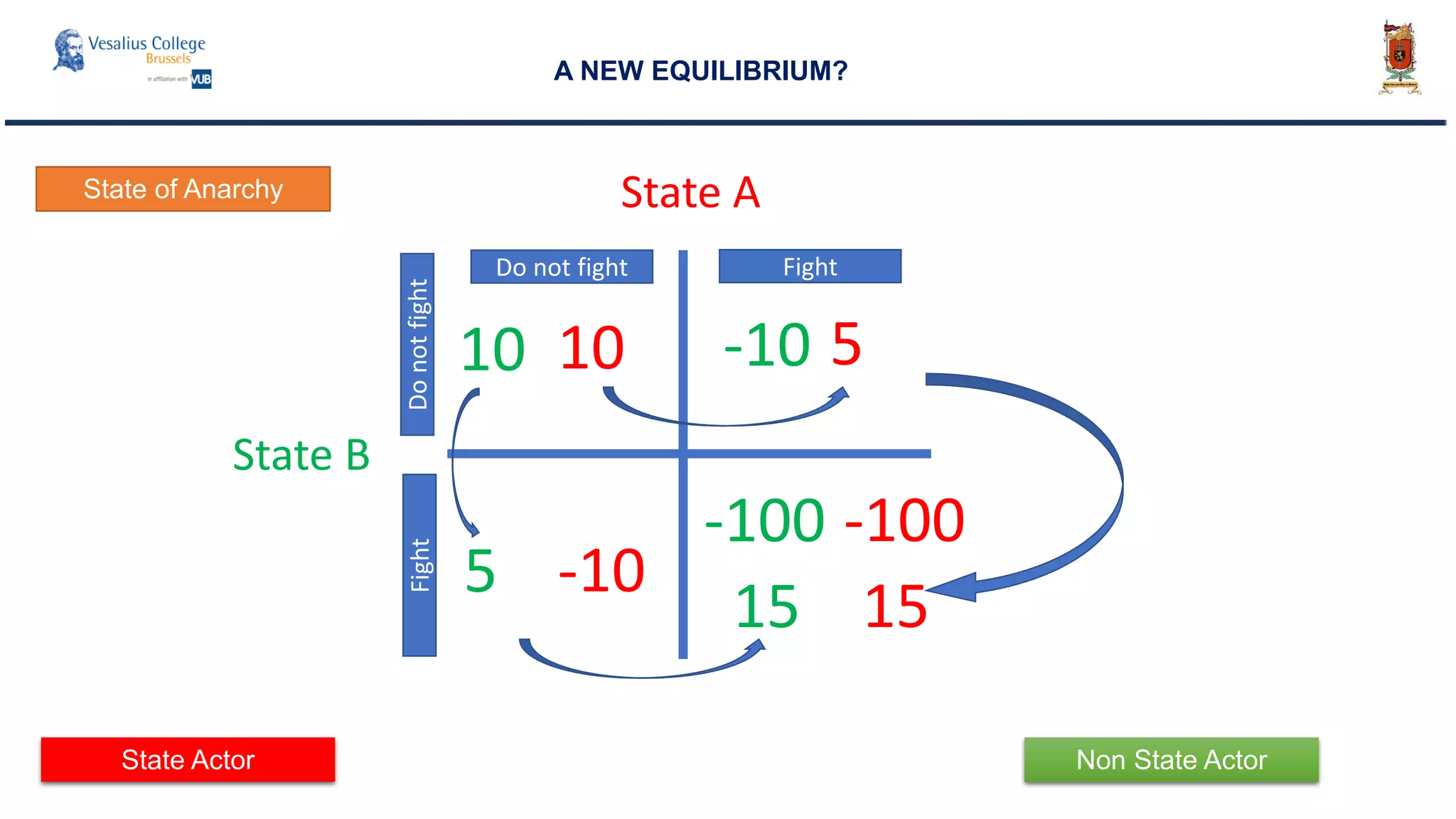
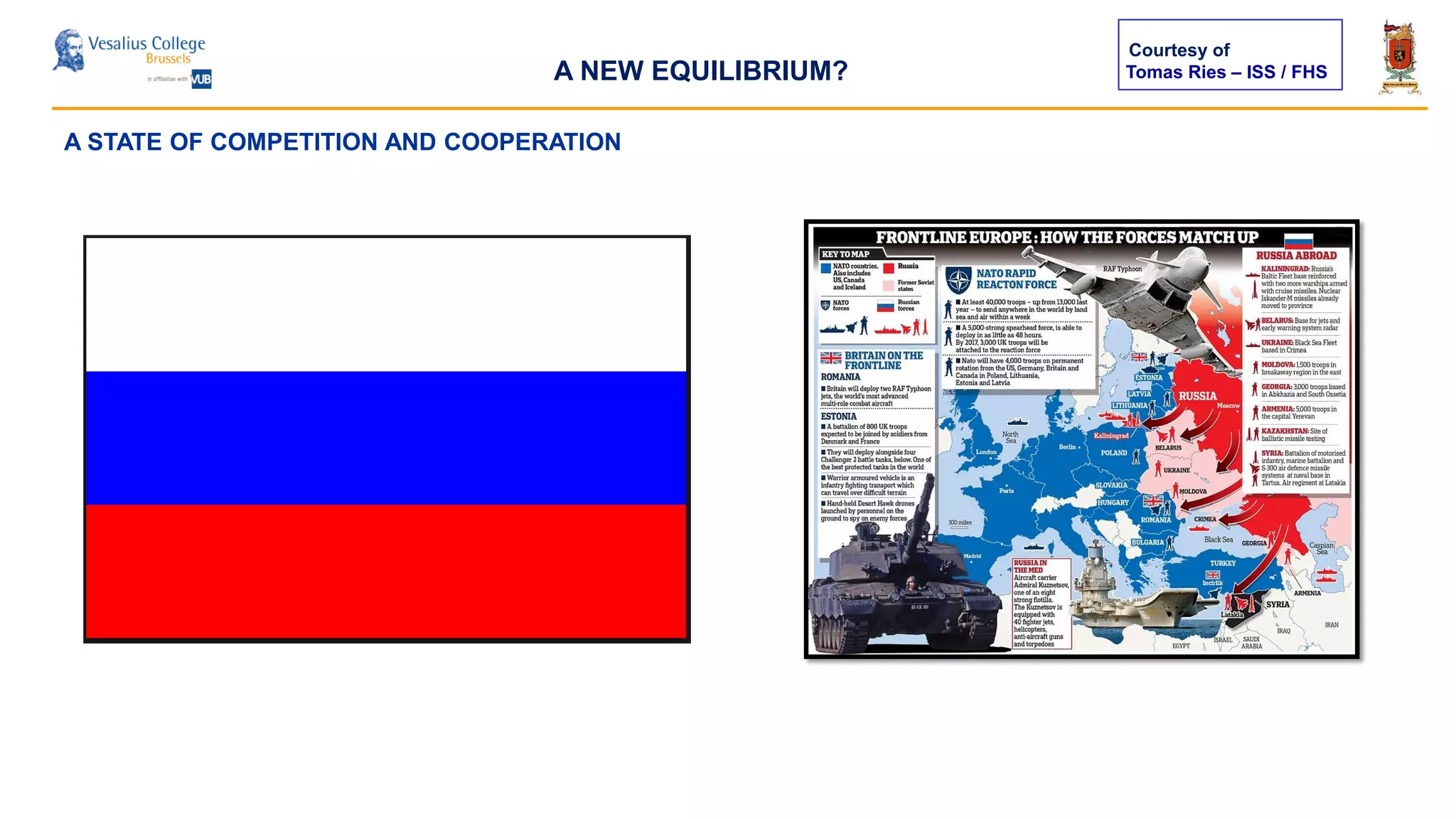
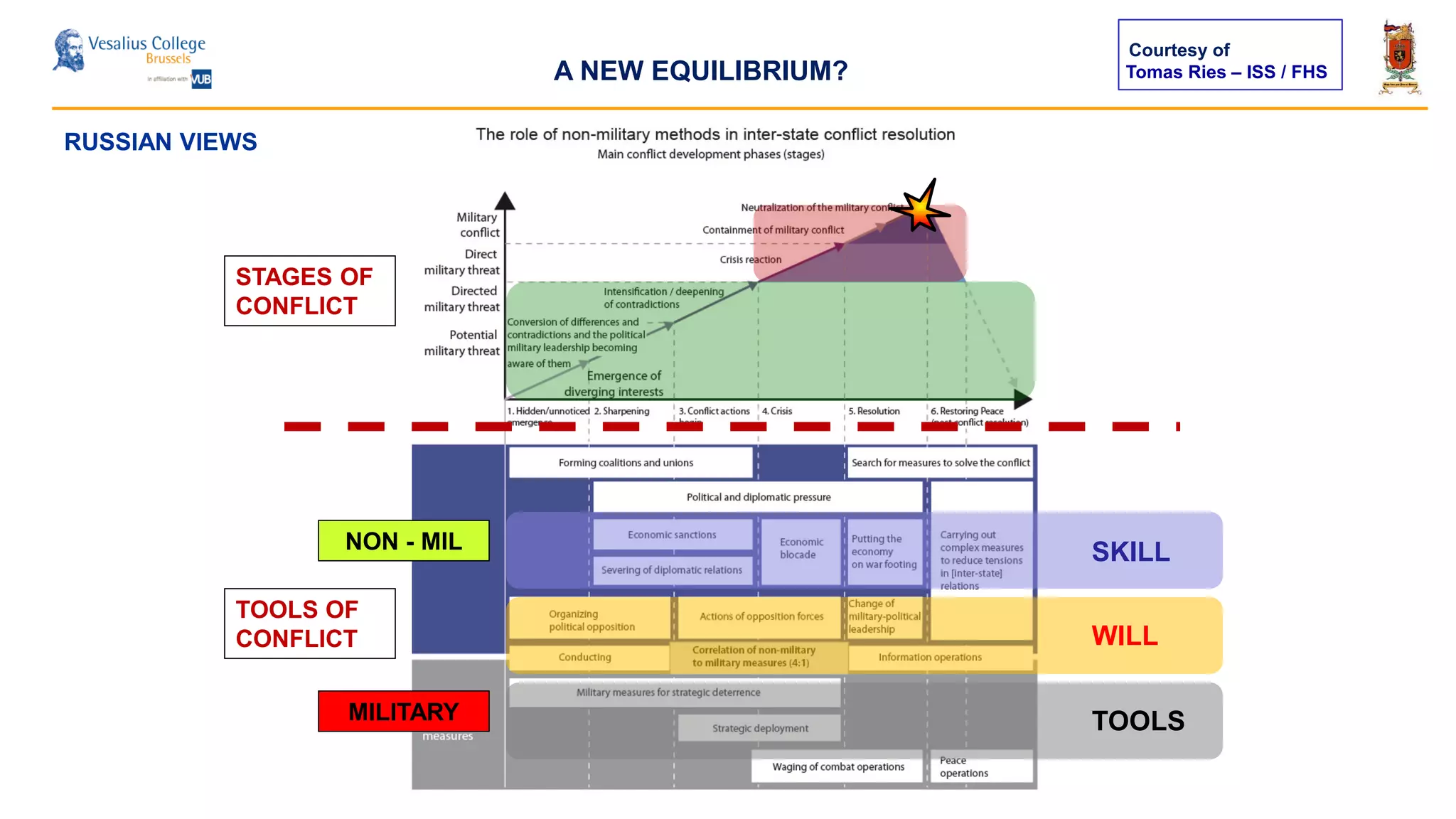
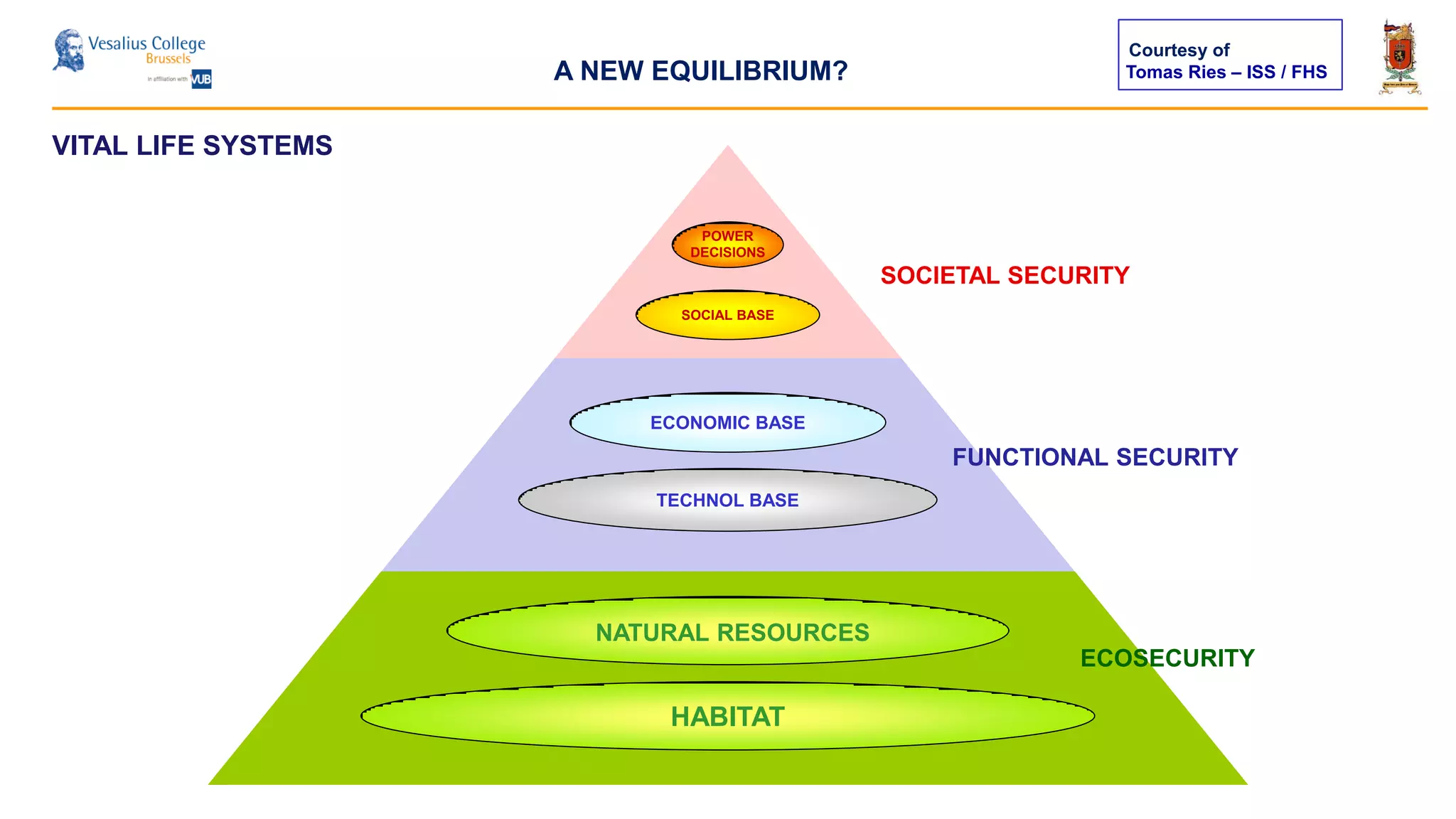
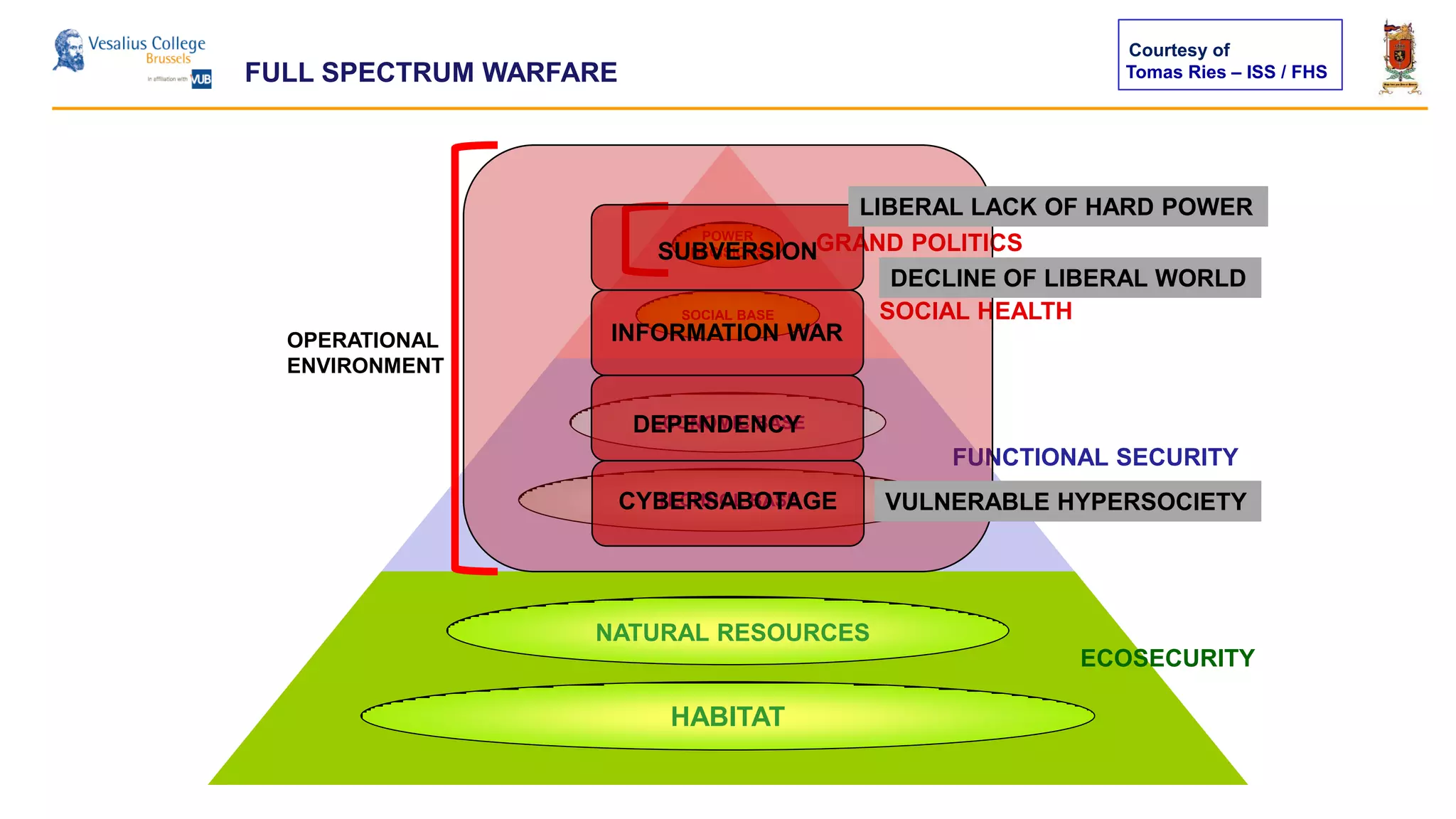
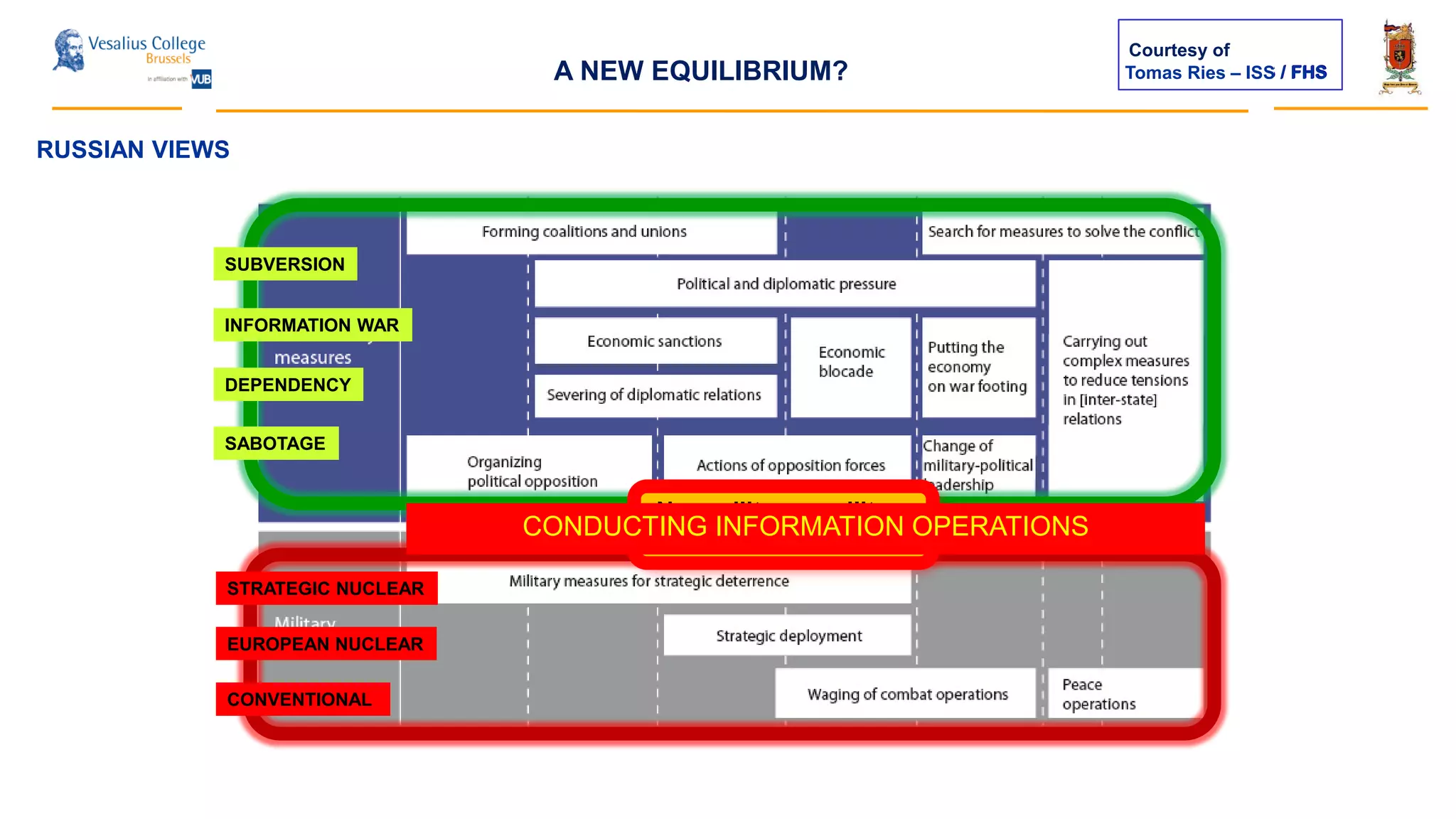
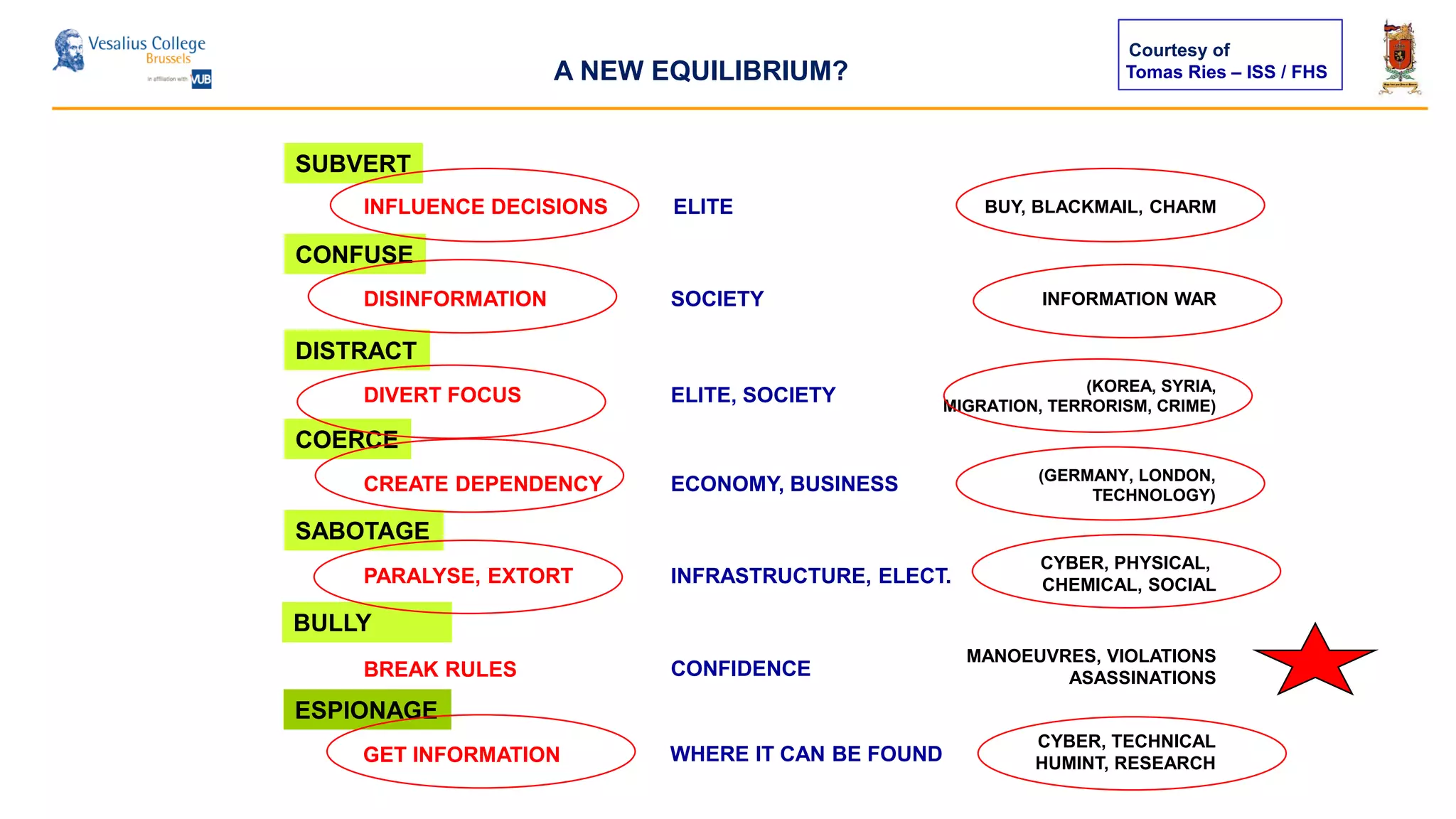
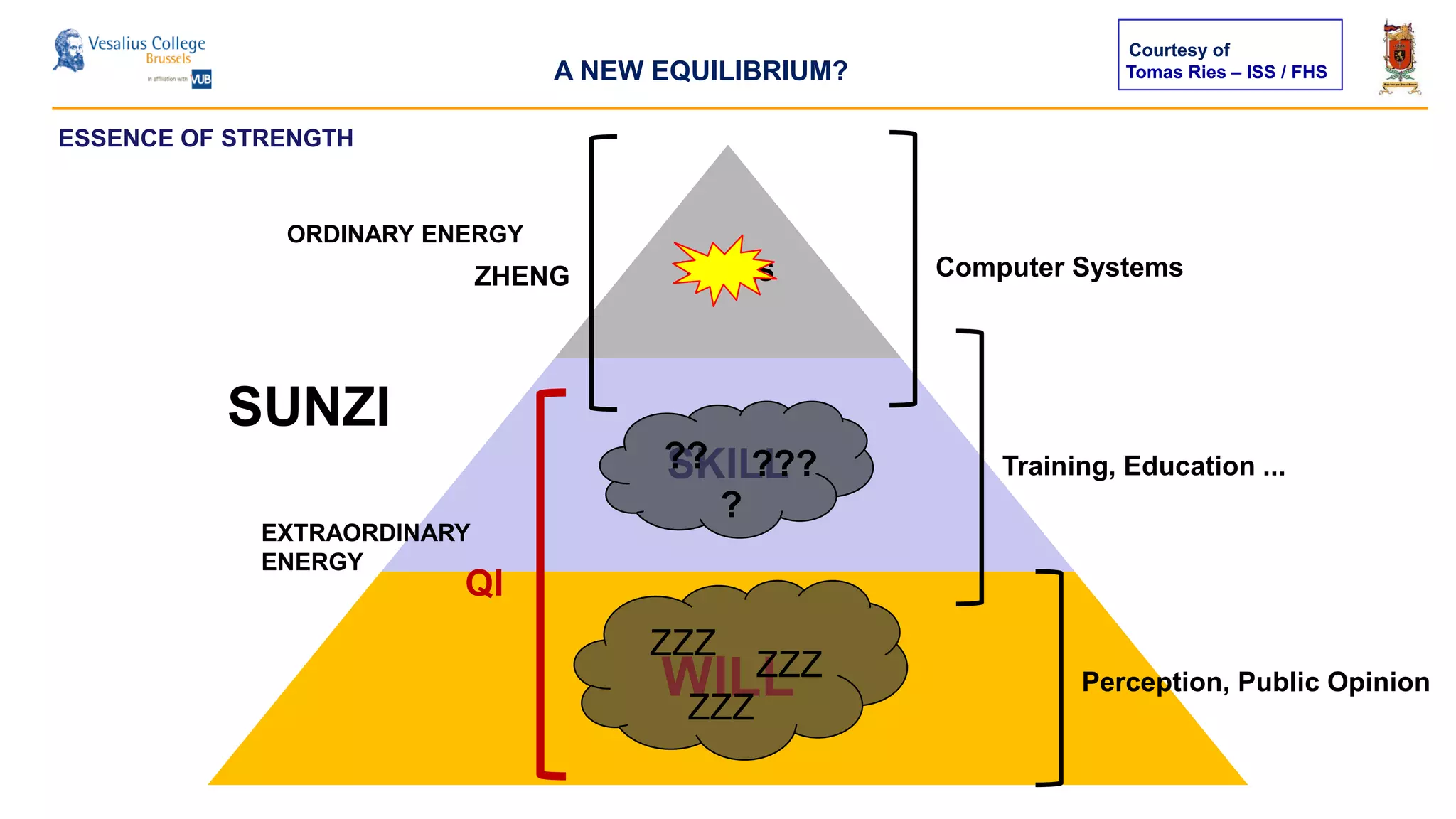
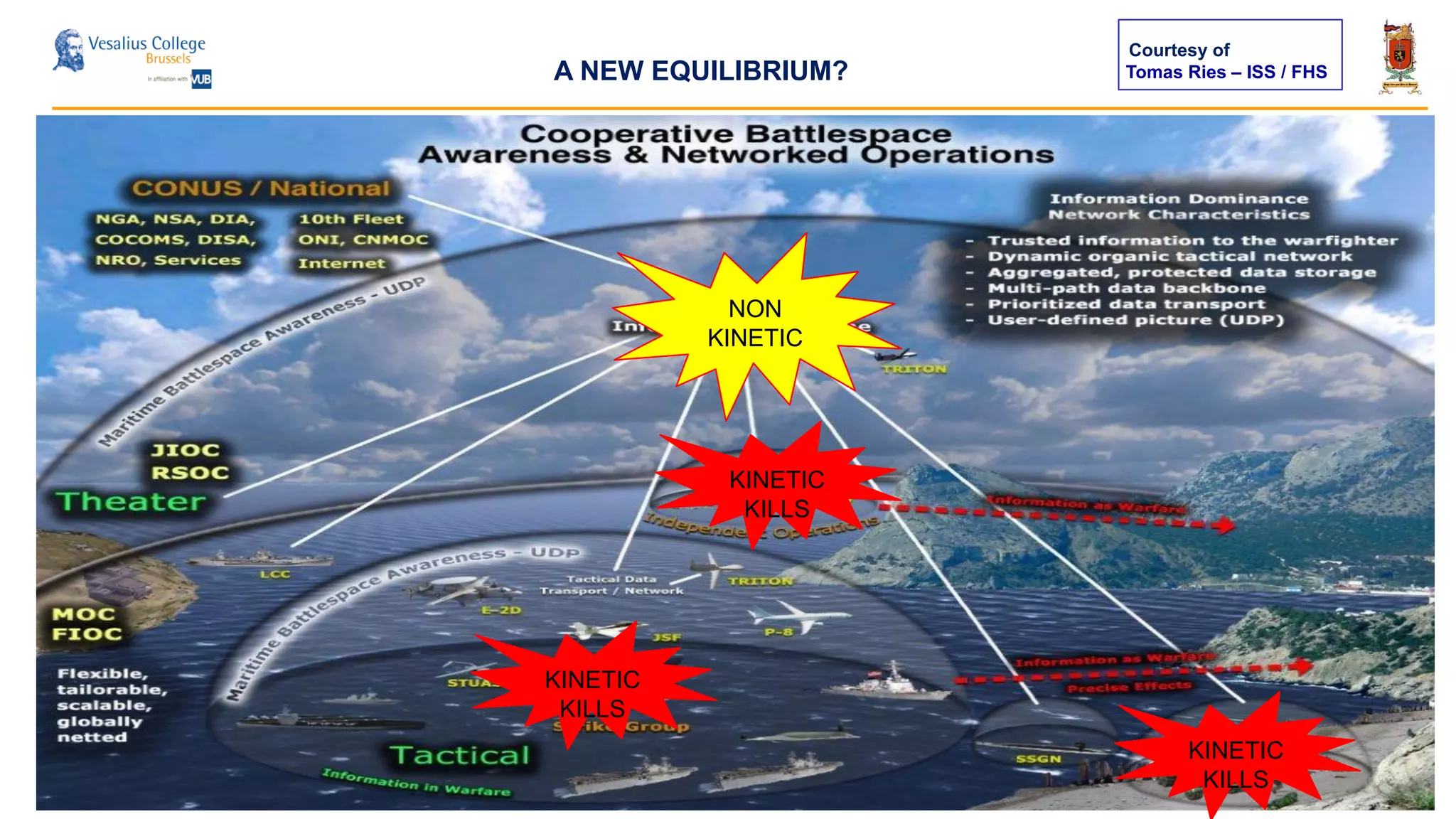
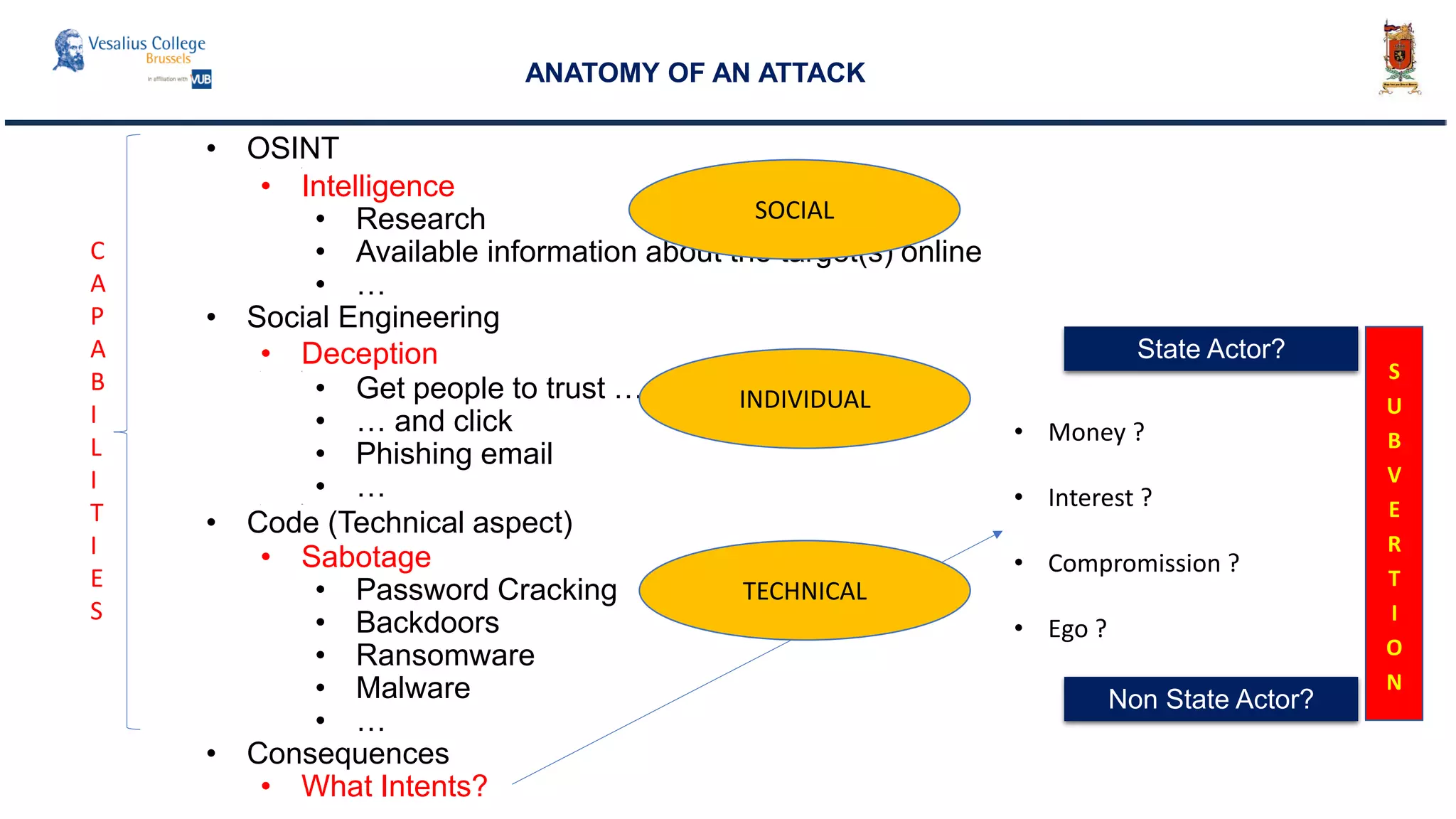
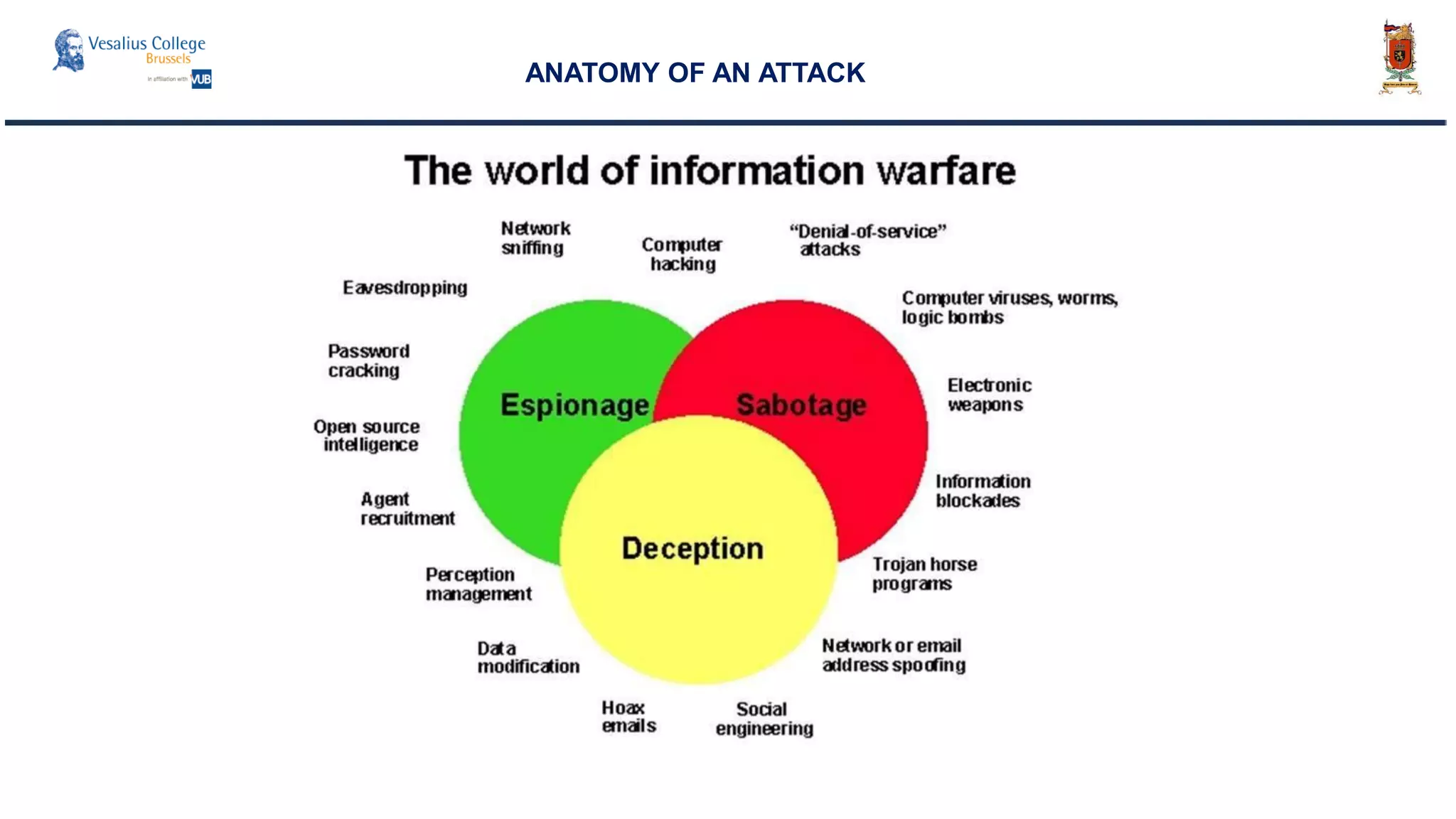
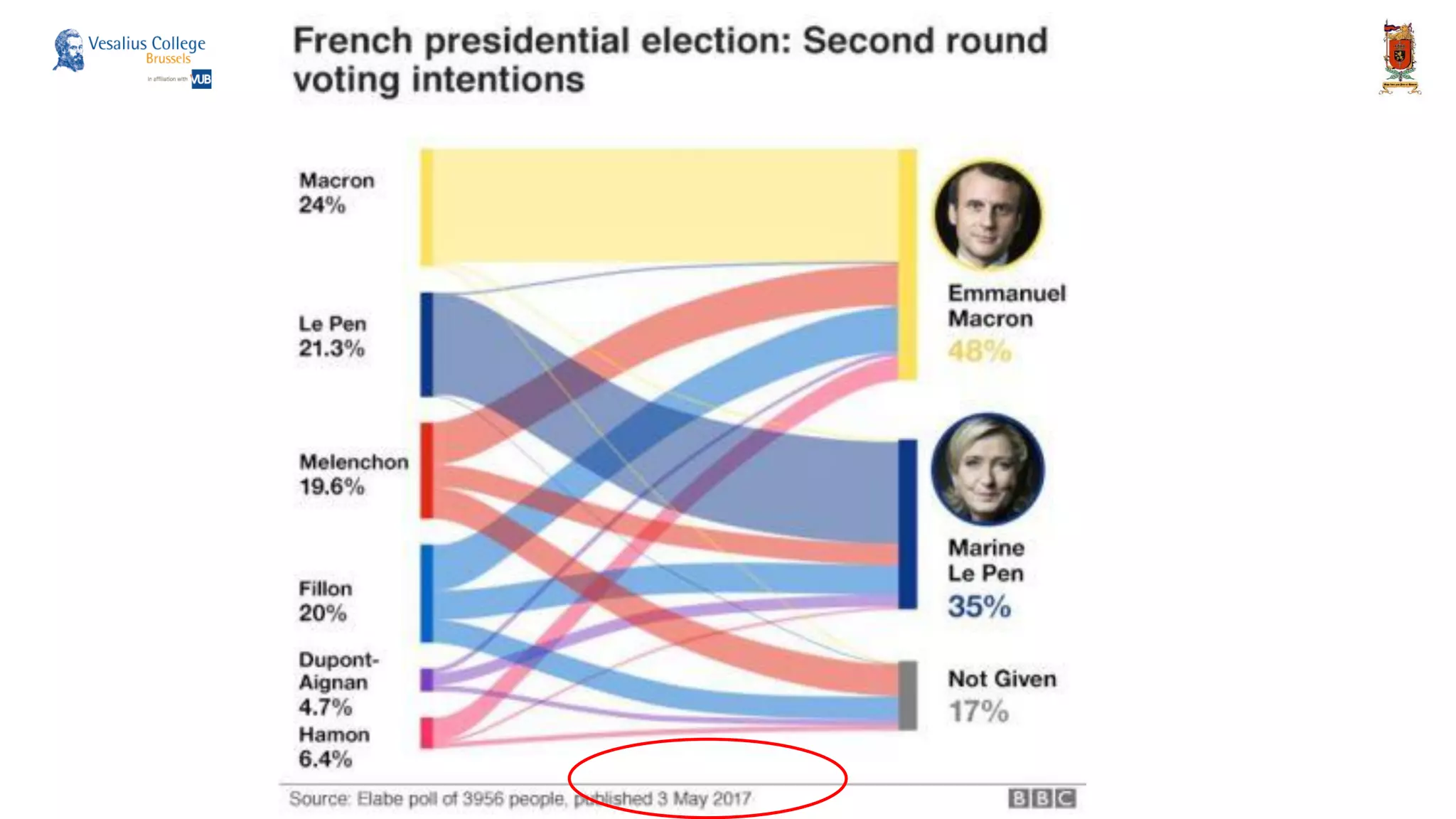
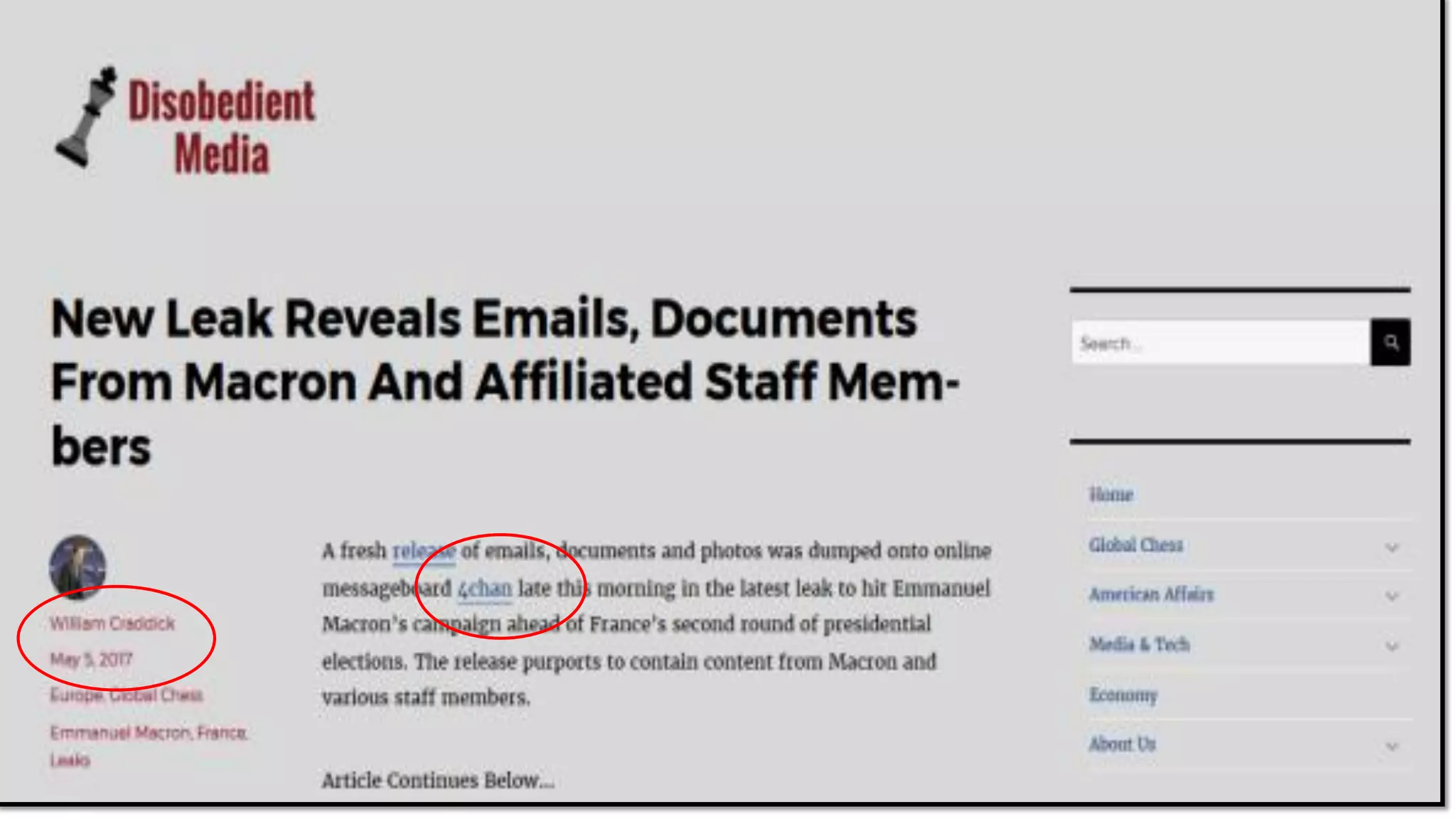
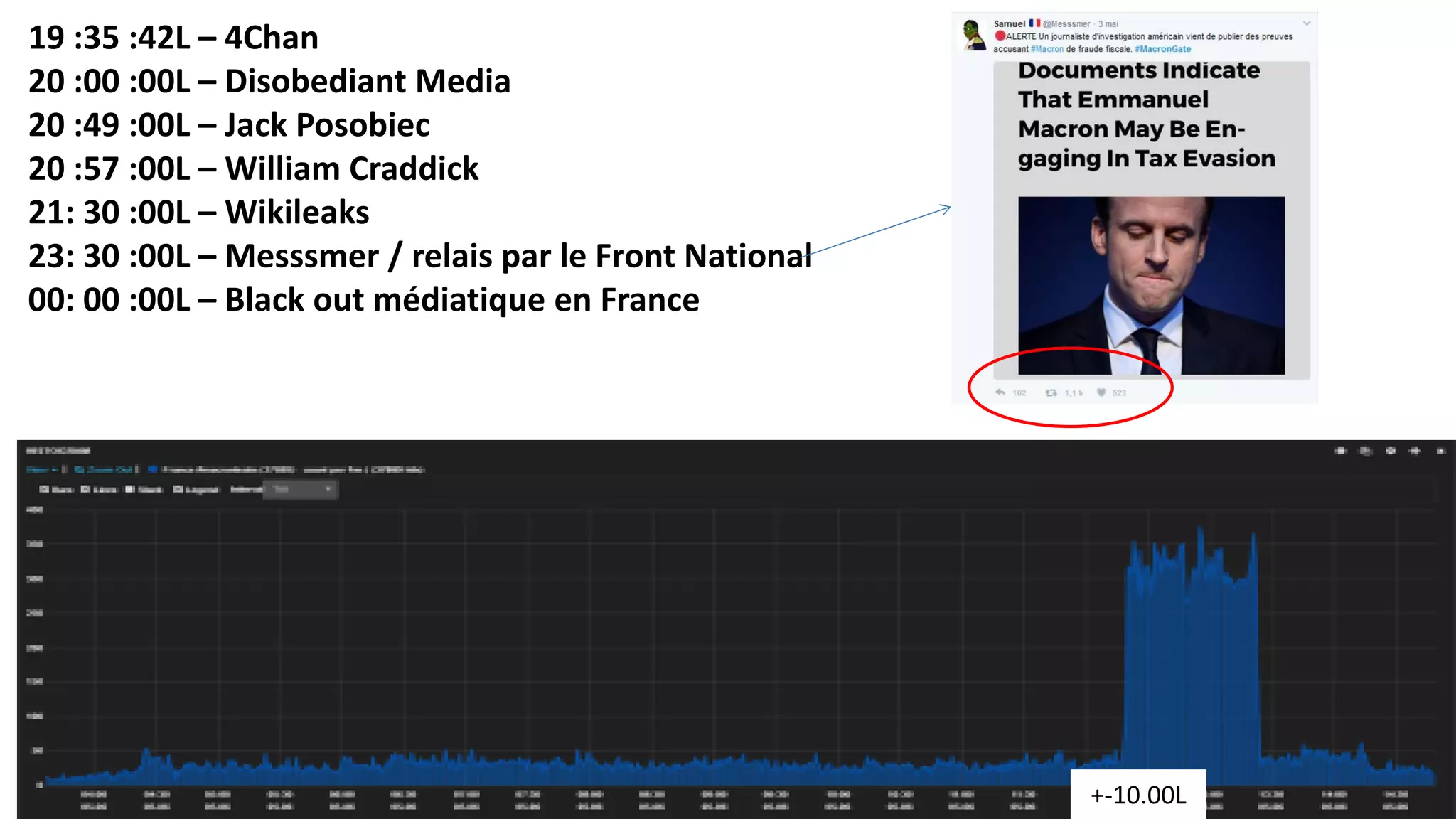
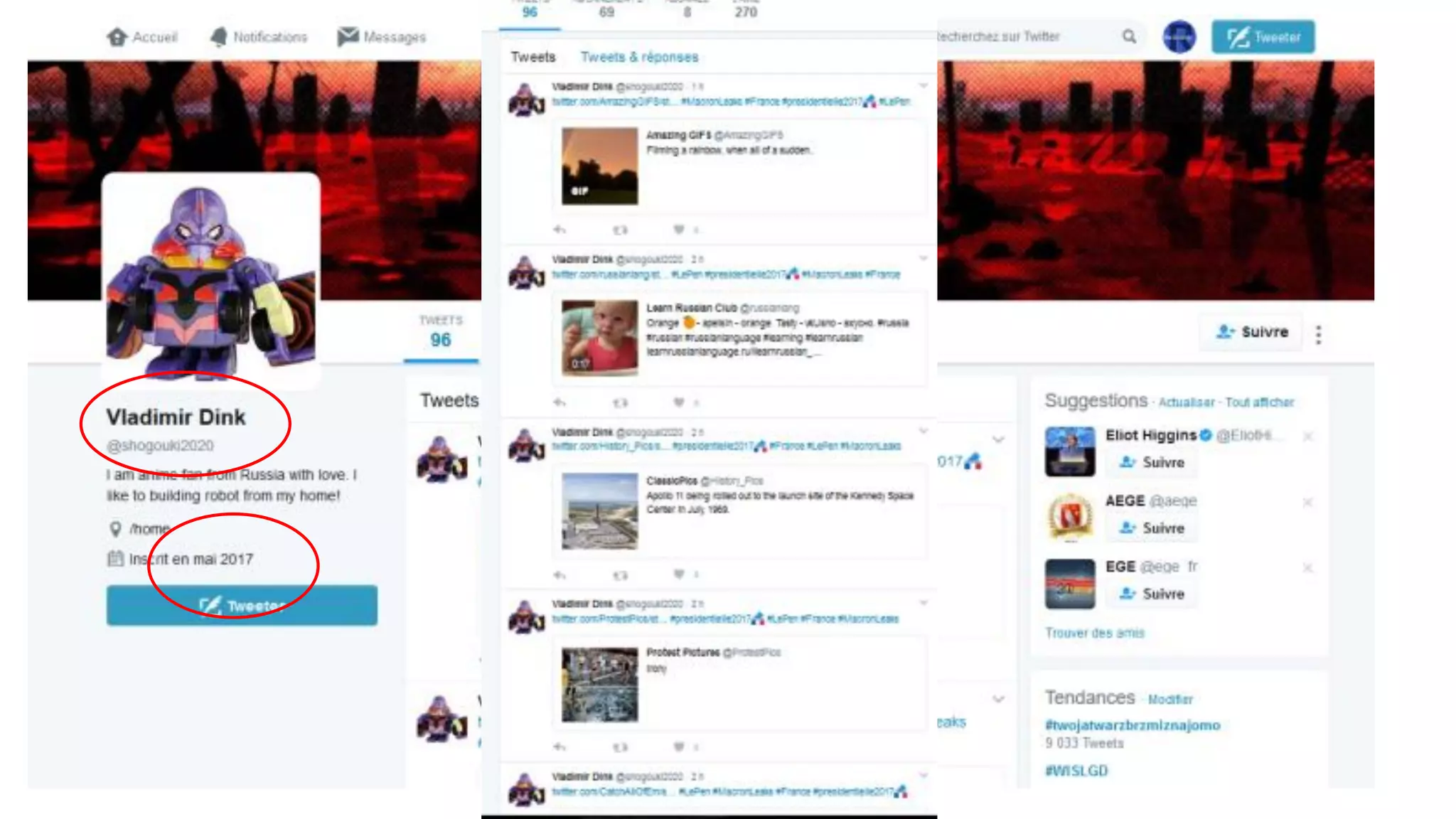
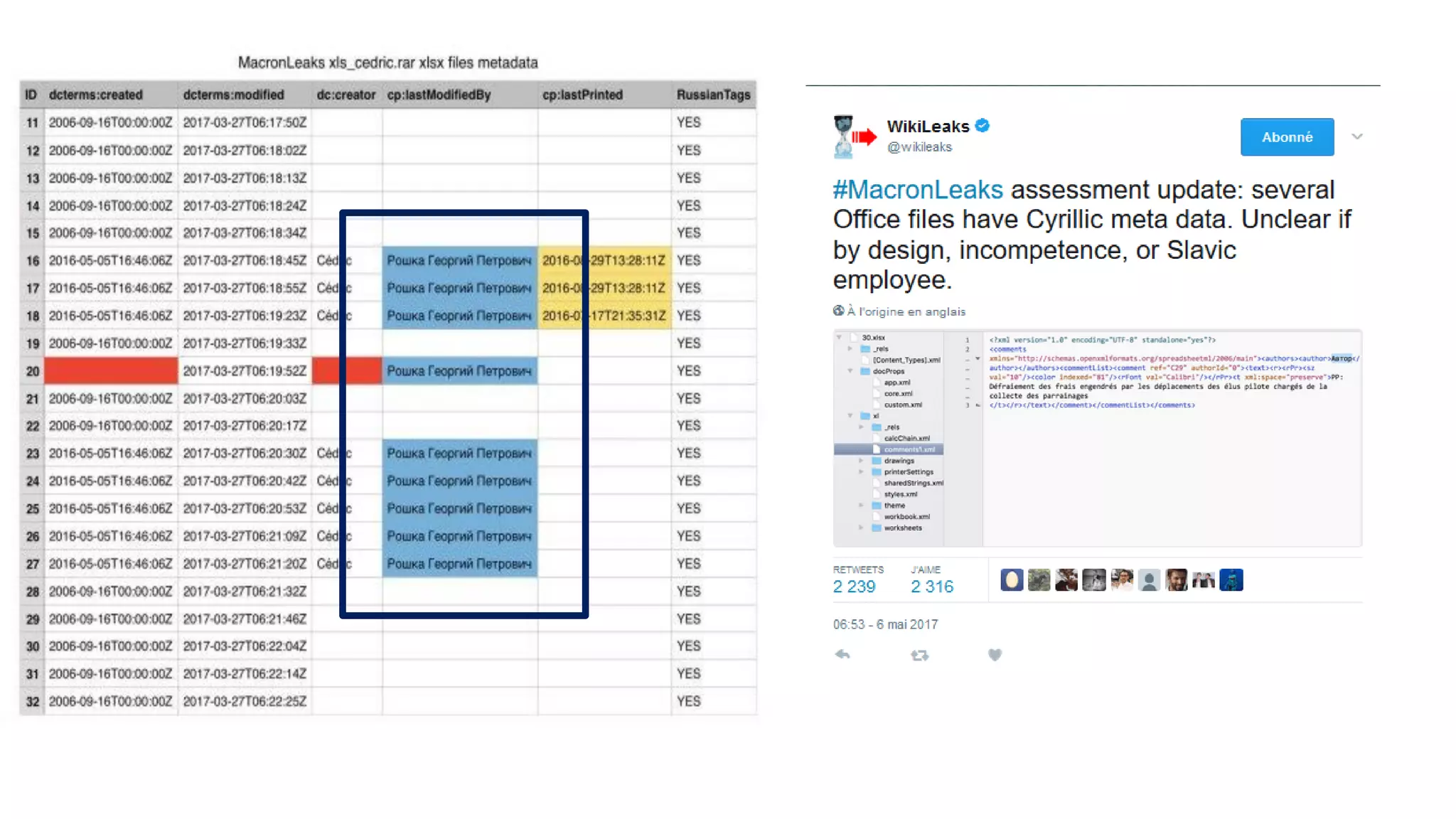
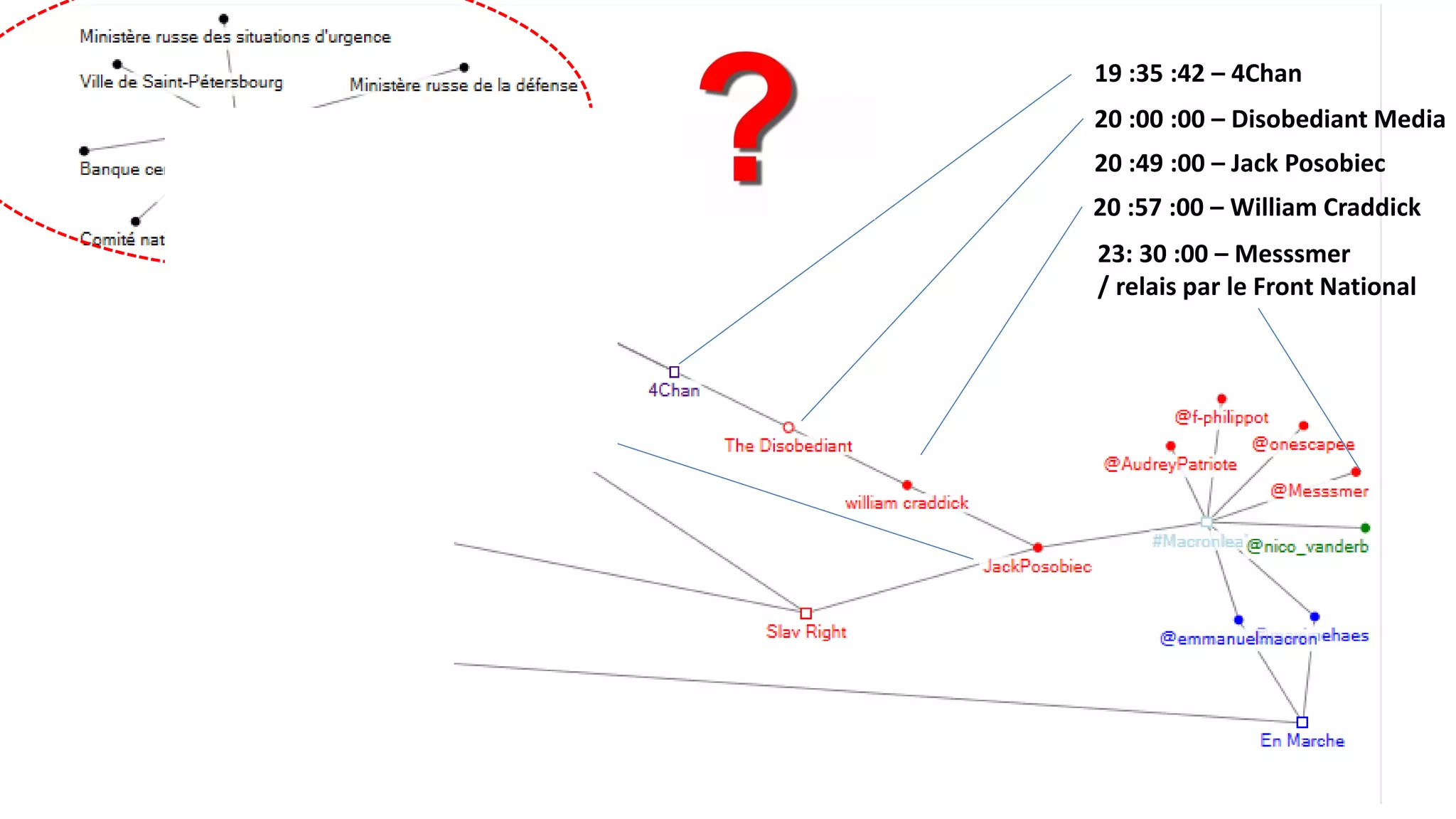
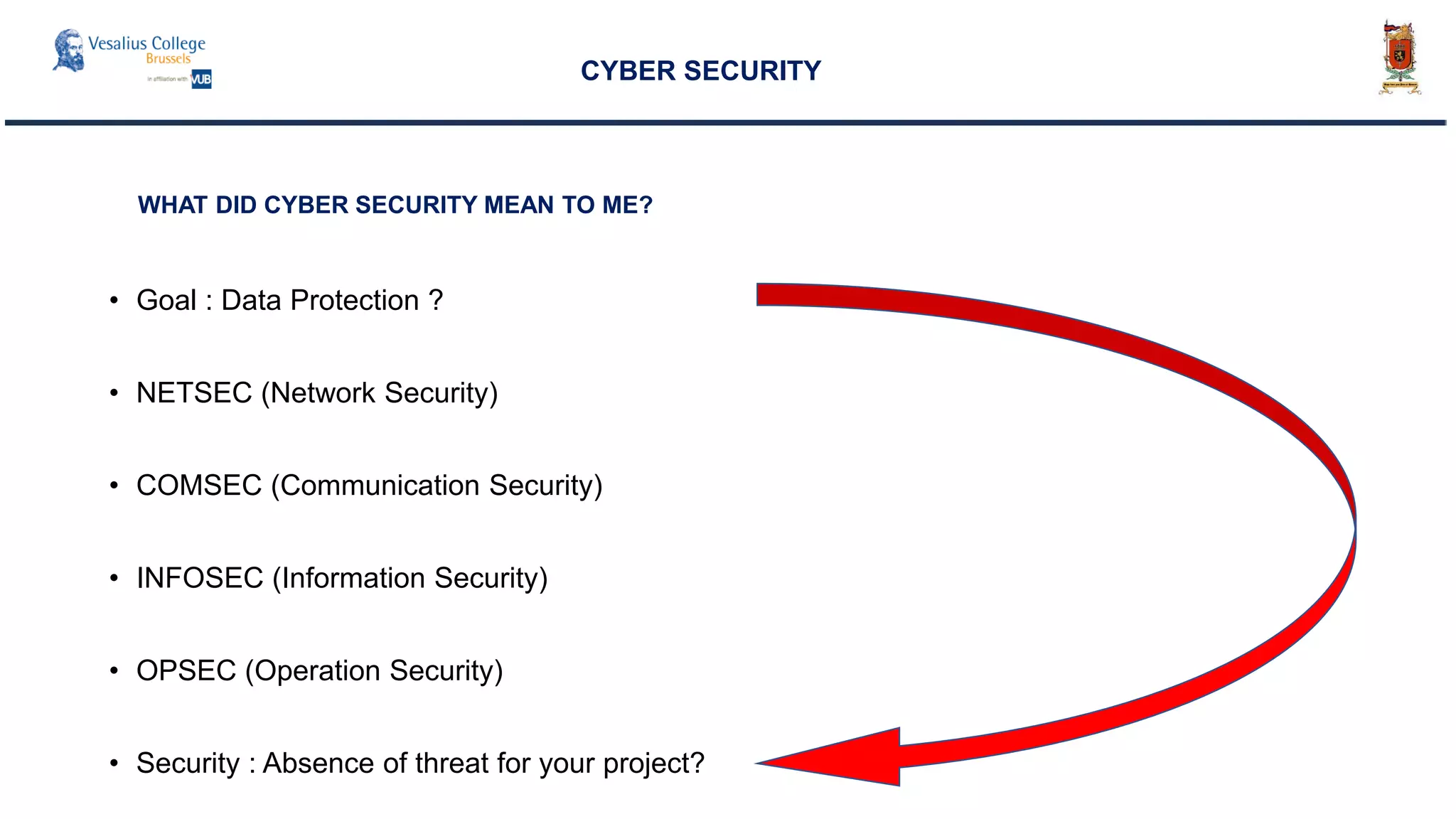
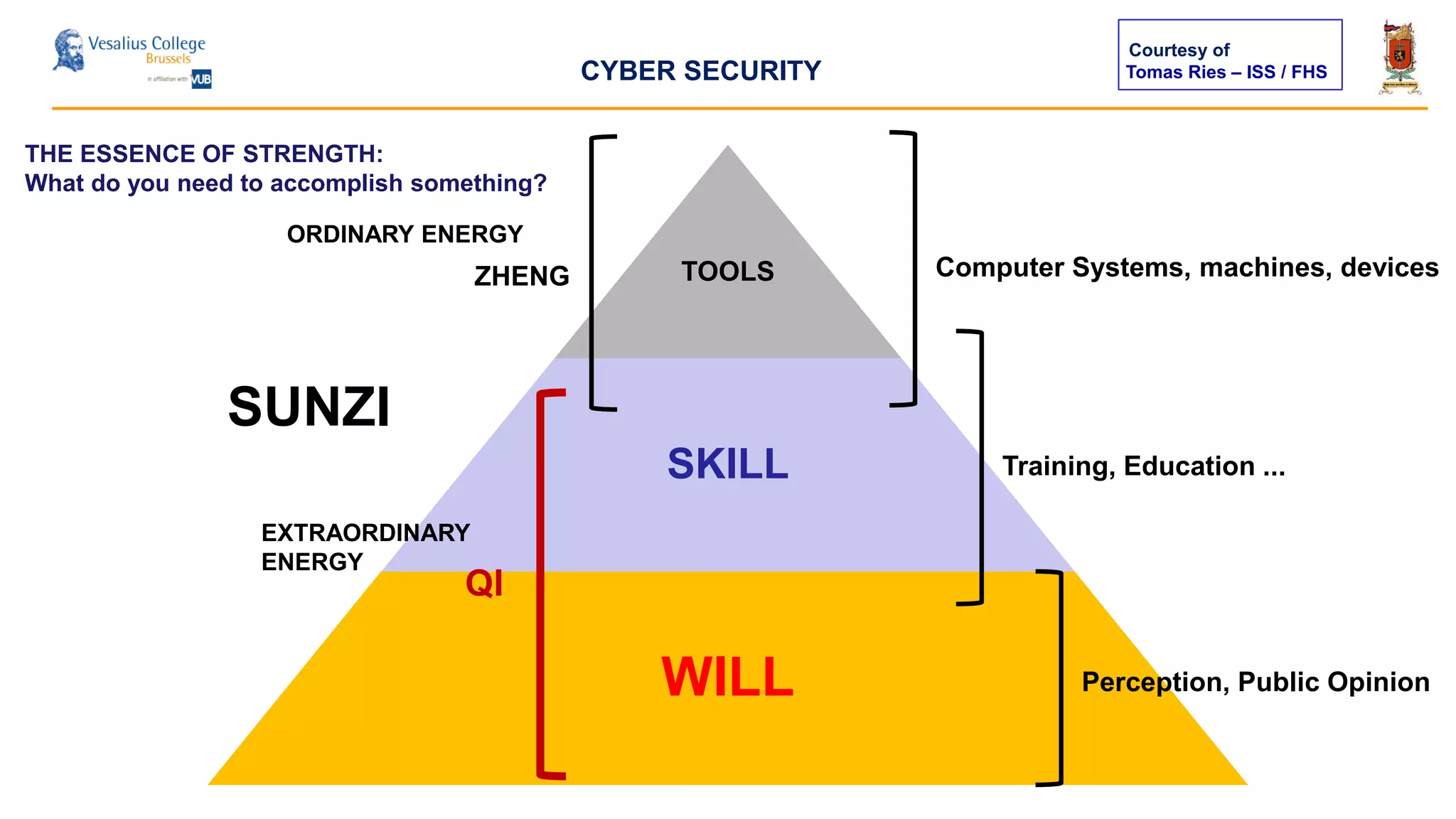
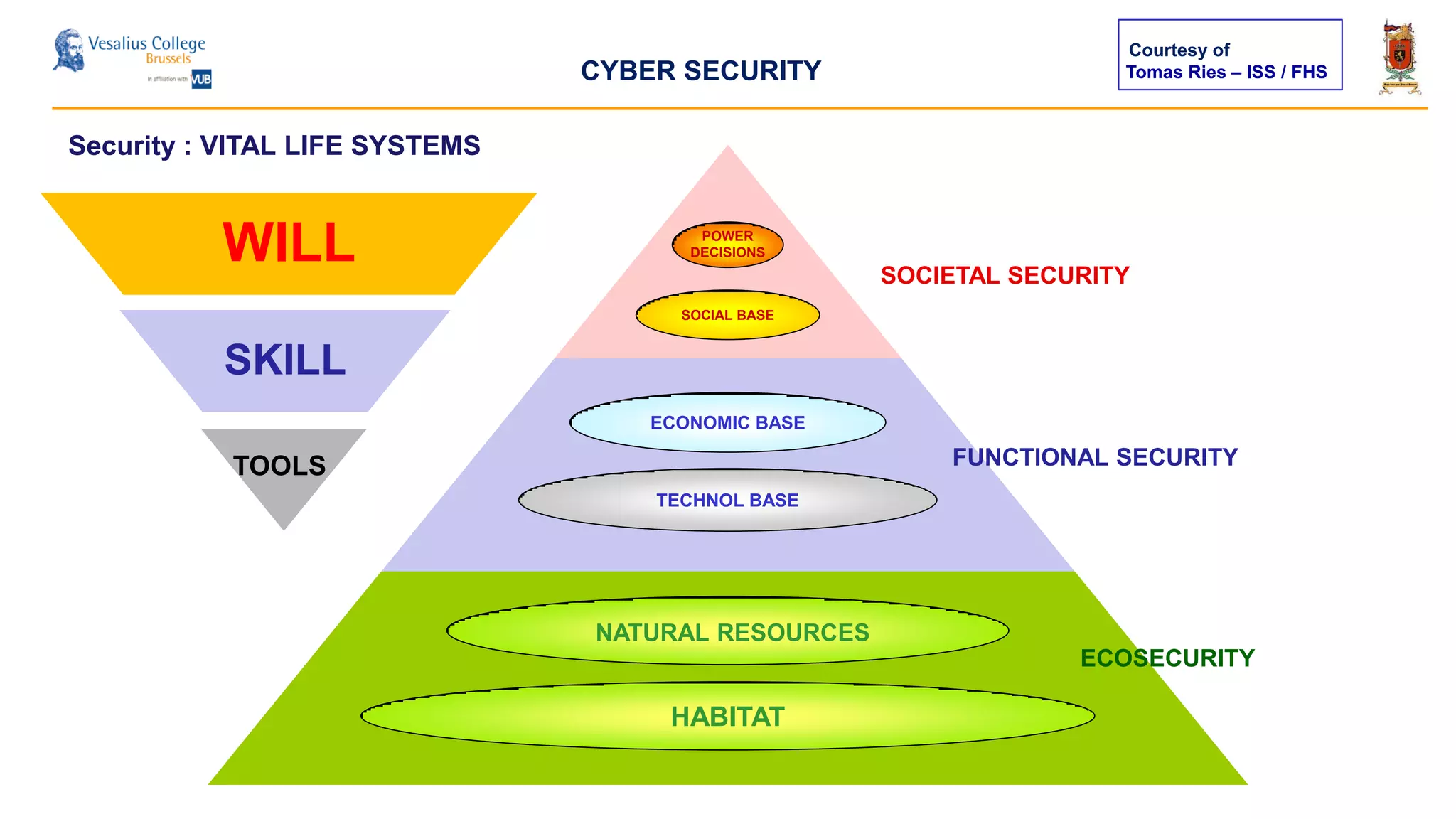
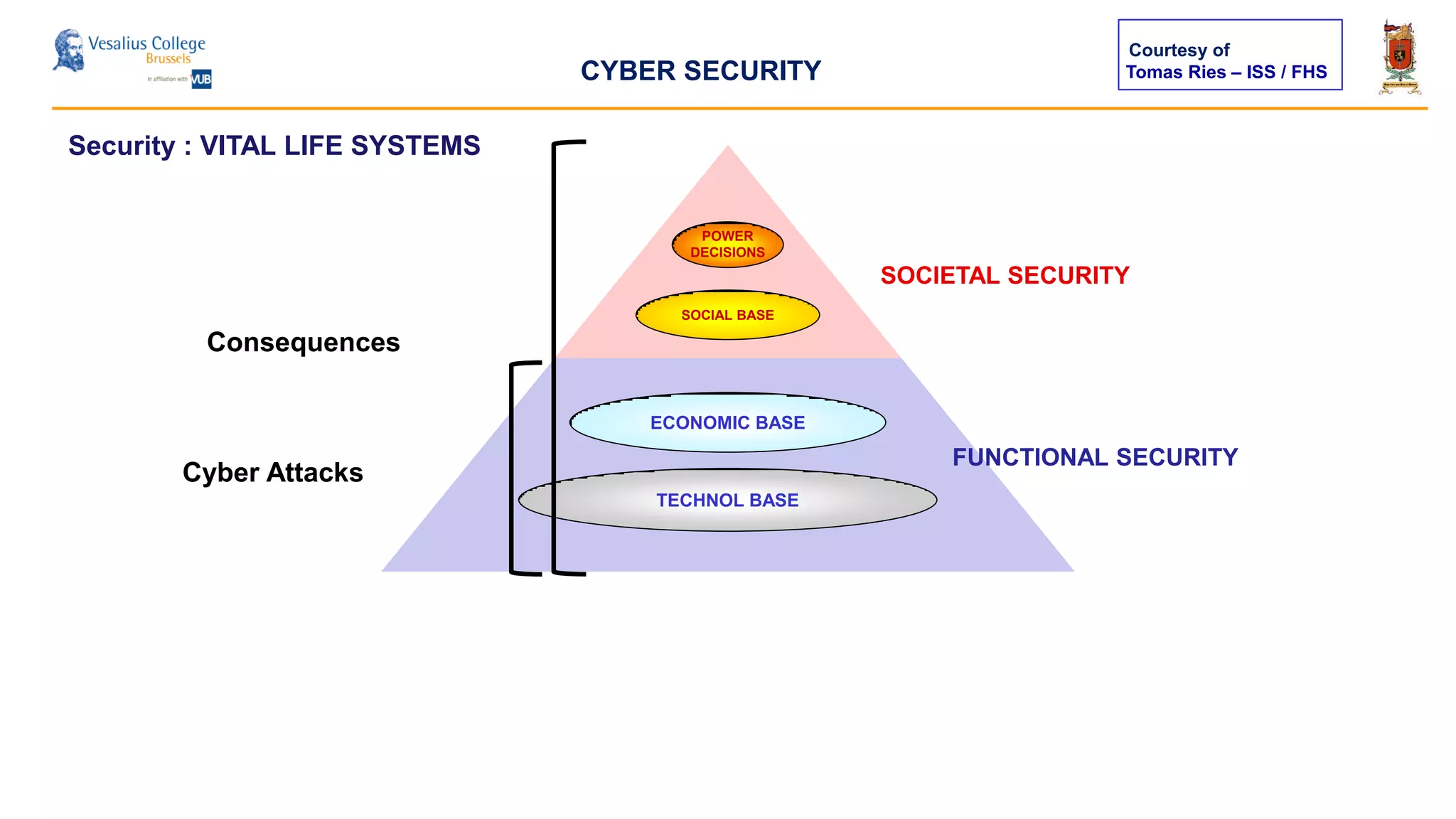
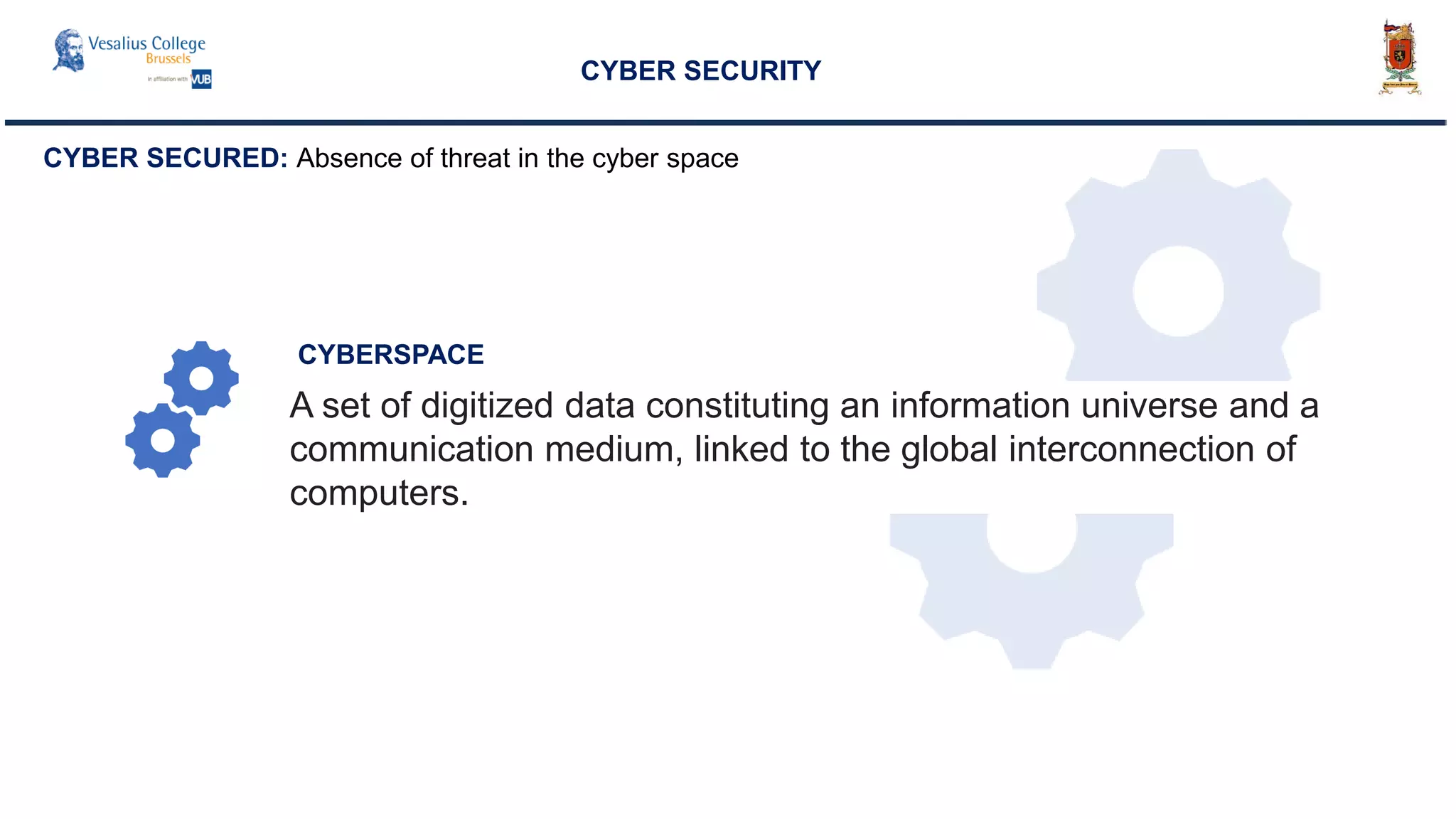
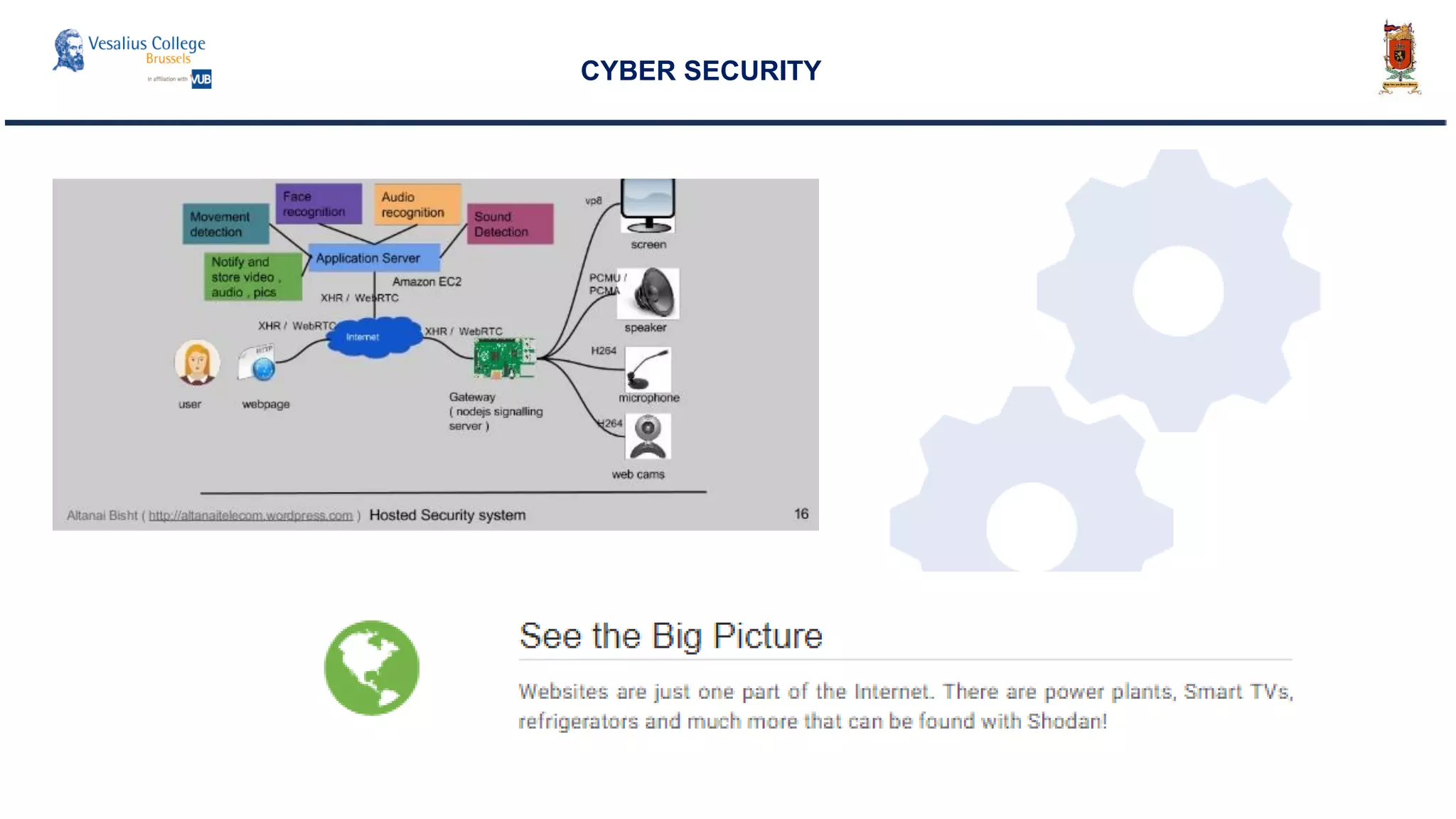
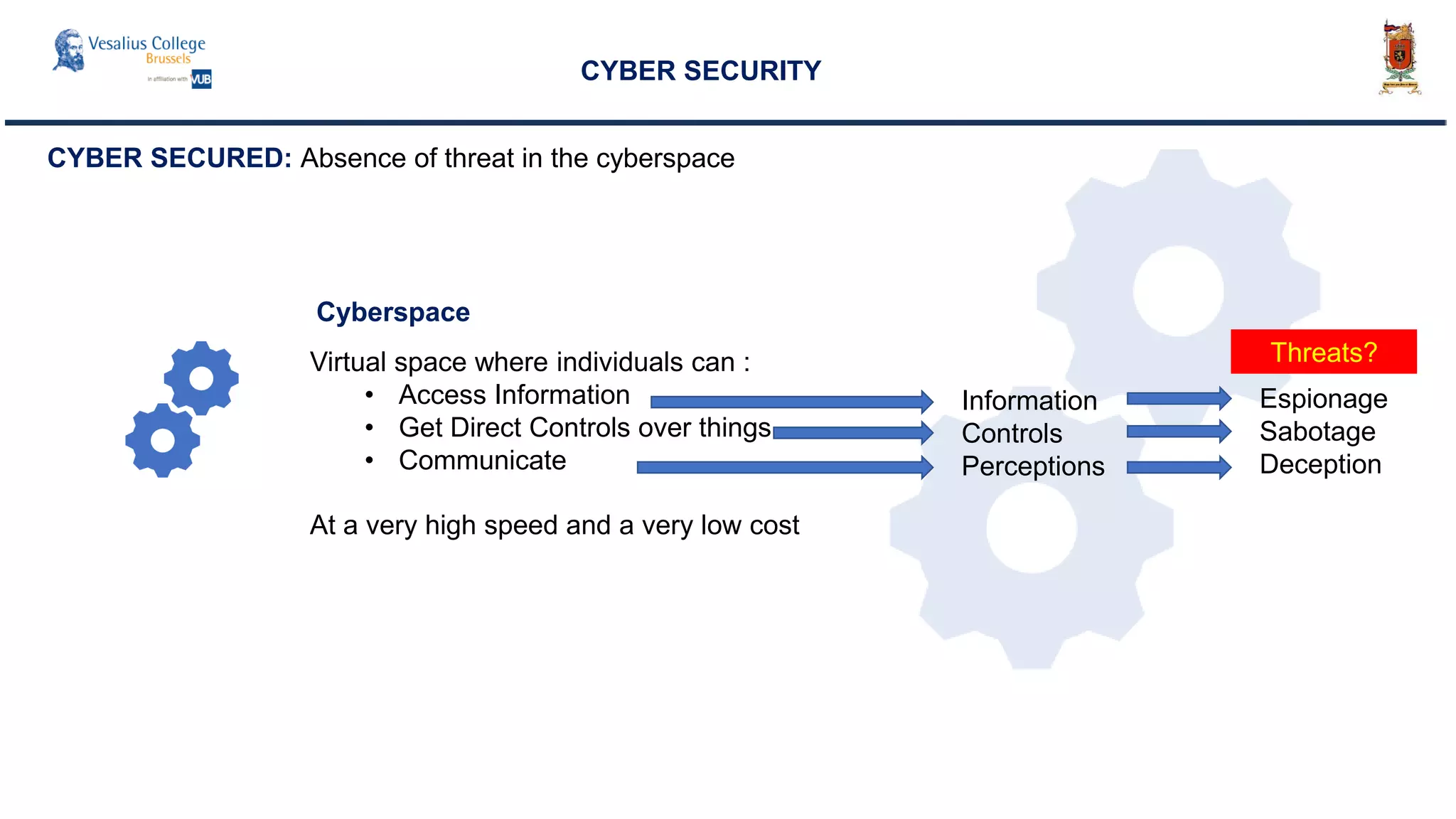
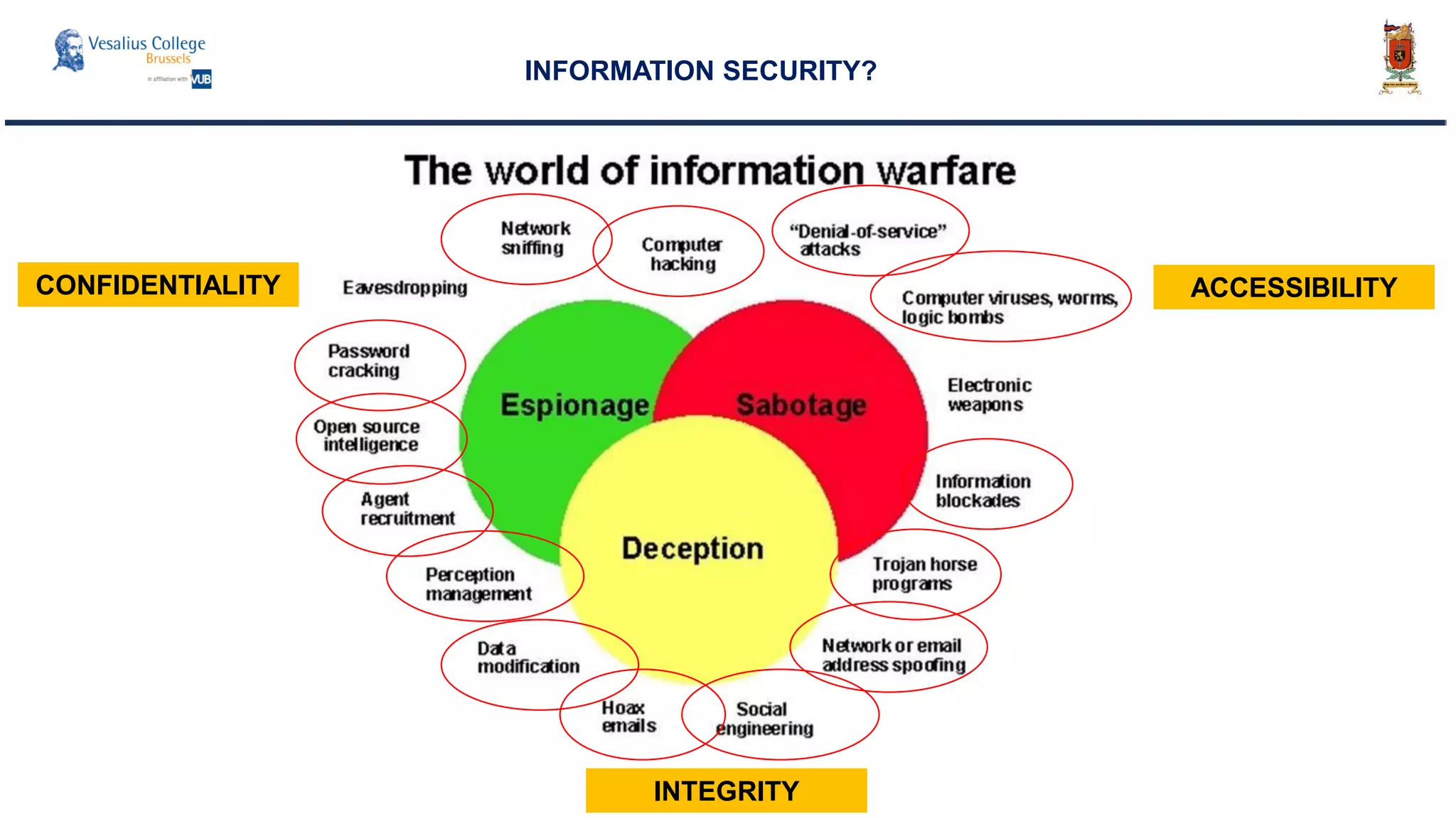
The document discusses the significance of cyber security as a global social issue, encompassing definitions, international relations, and the complexities of information warfare. It emphasizes the necessity for a holistic approach to protect systems and data from cyber attacks, considering both technical and social factors. Additionally, it highlights the implications of cyber threats on international stability and the necessity for collaborative efforts in developing effective security strategies.

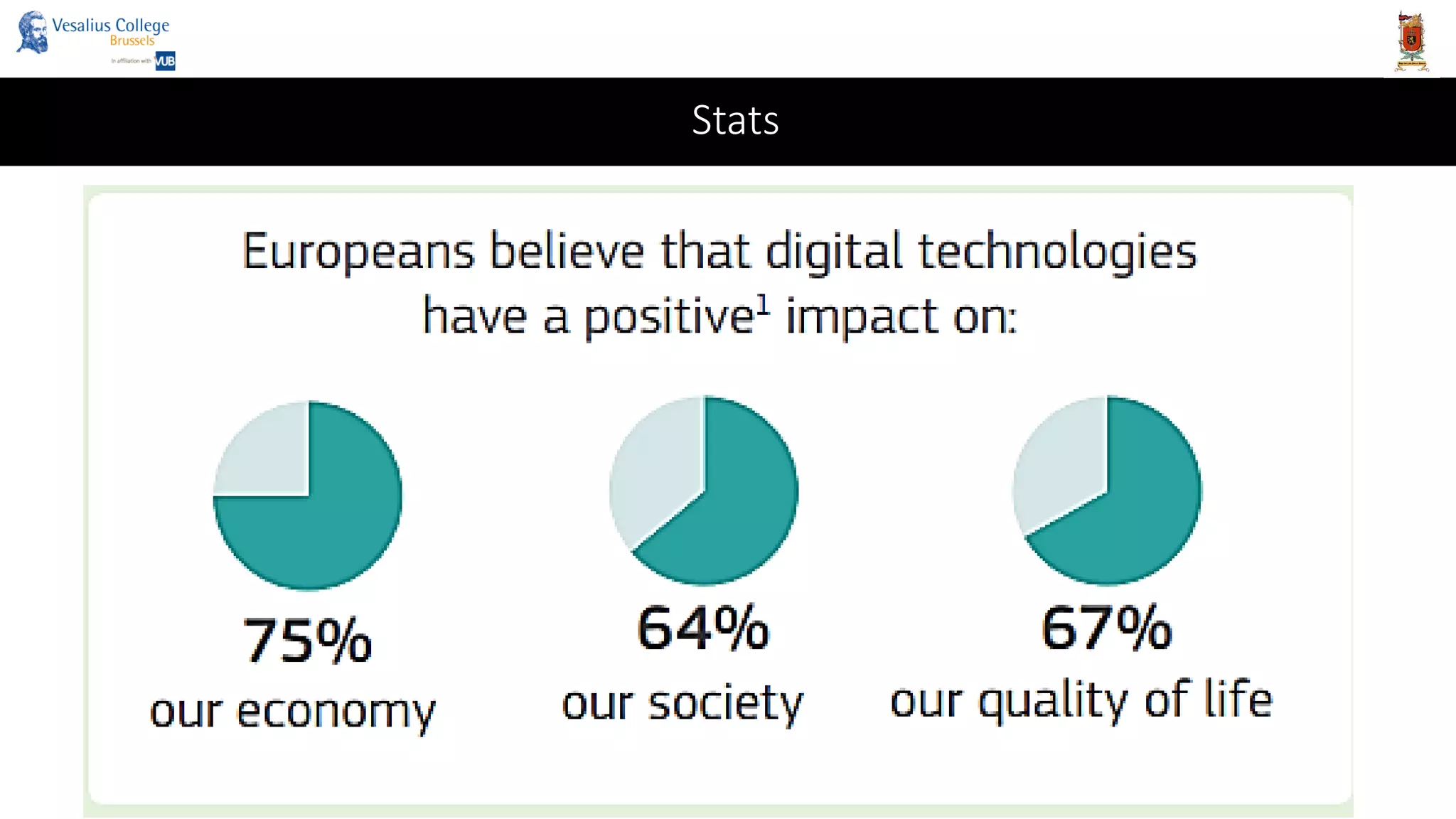
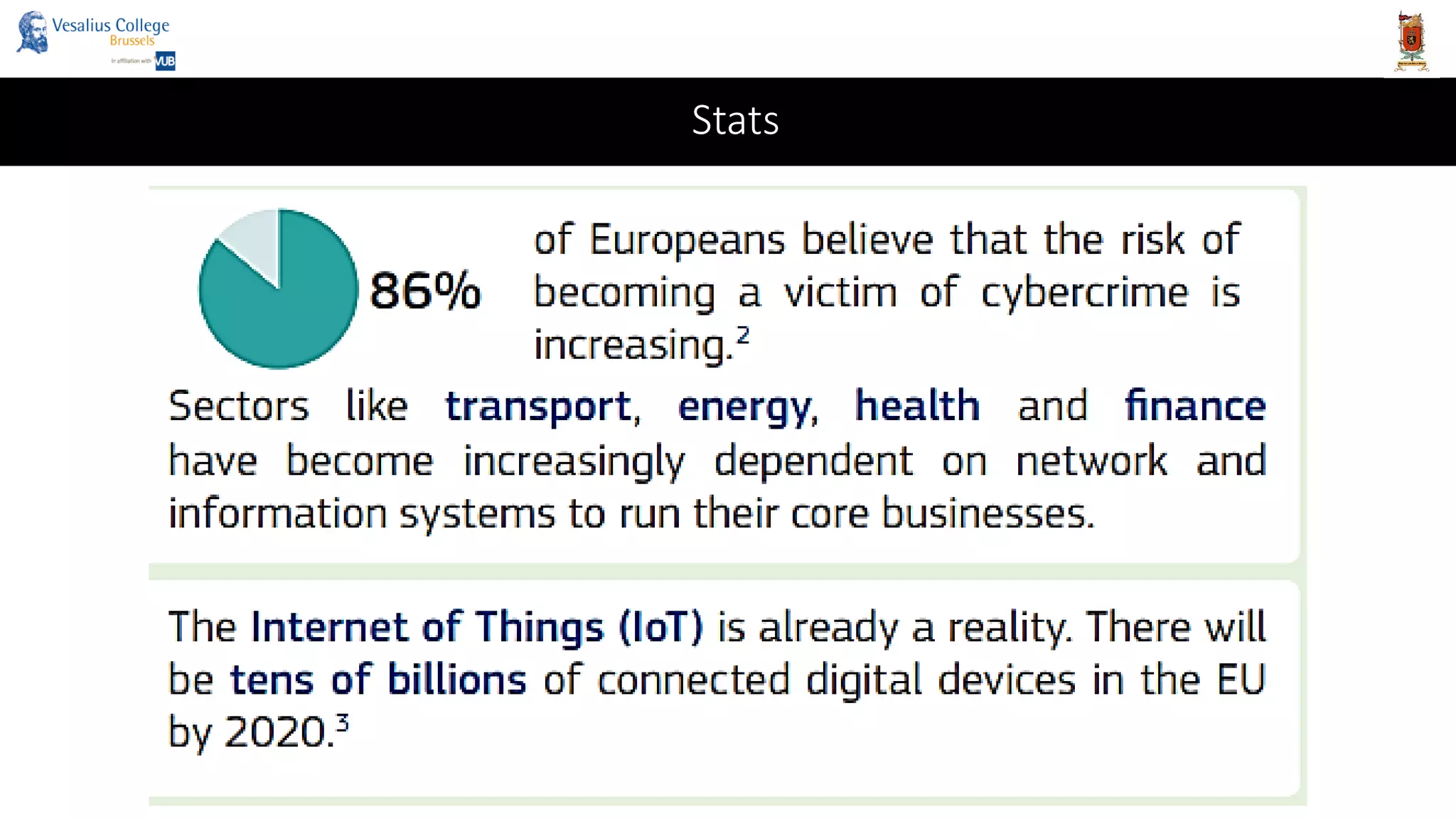











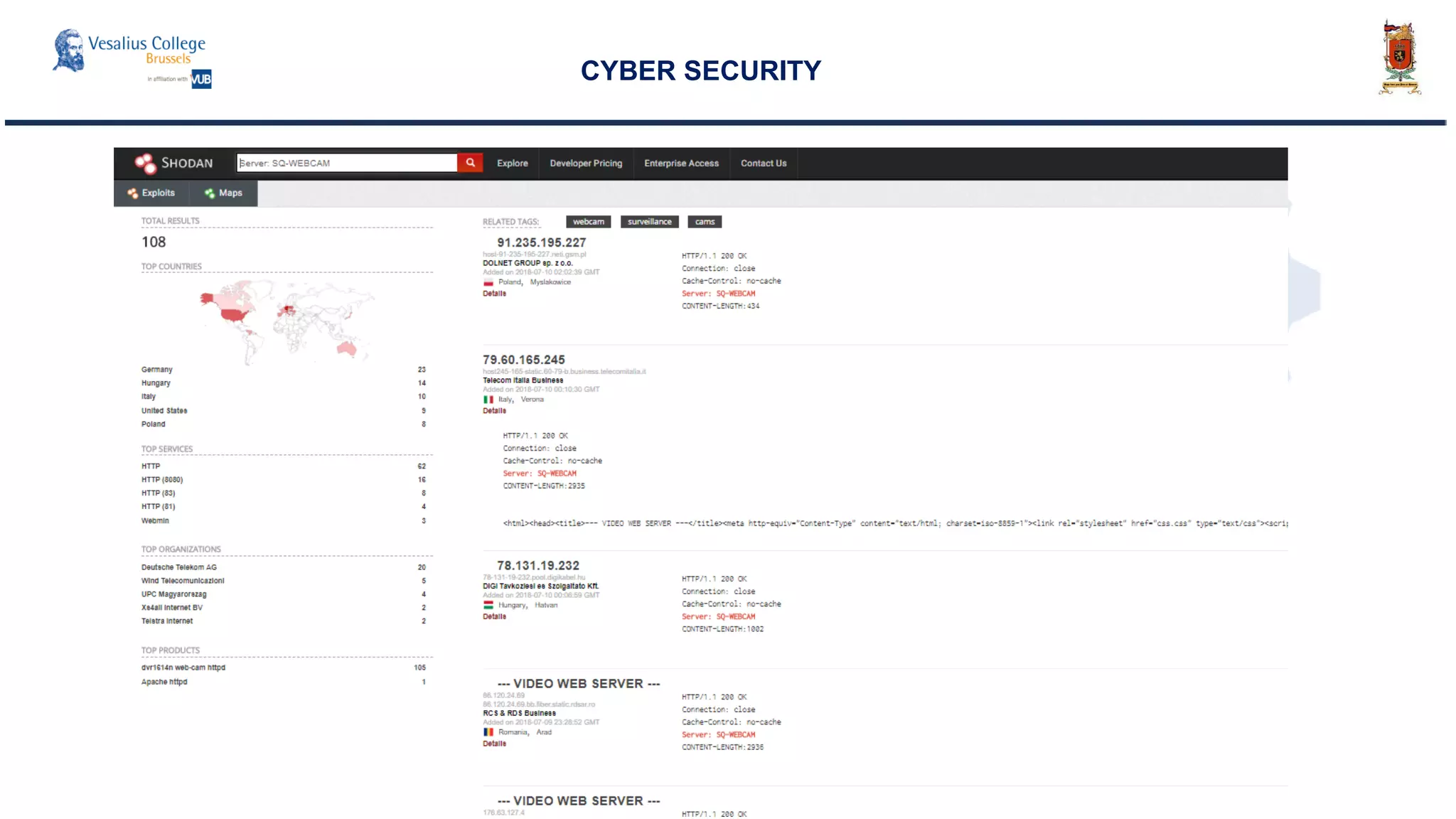
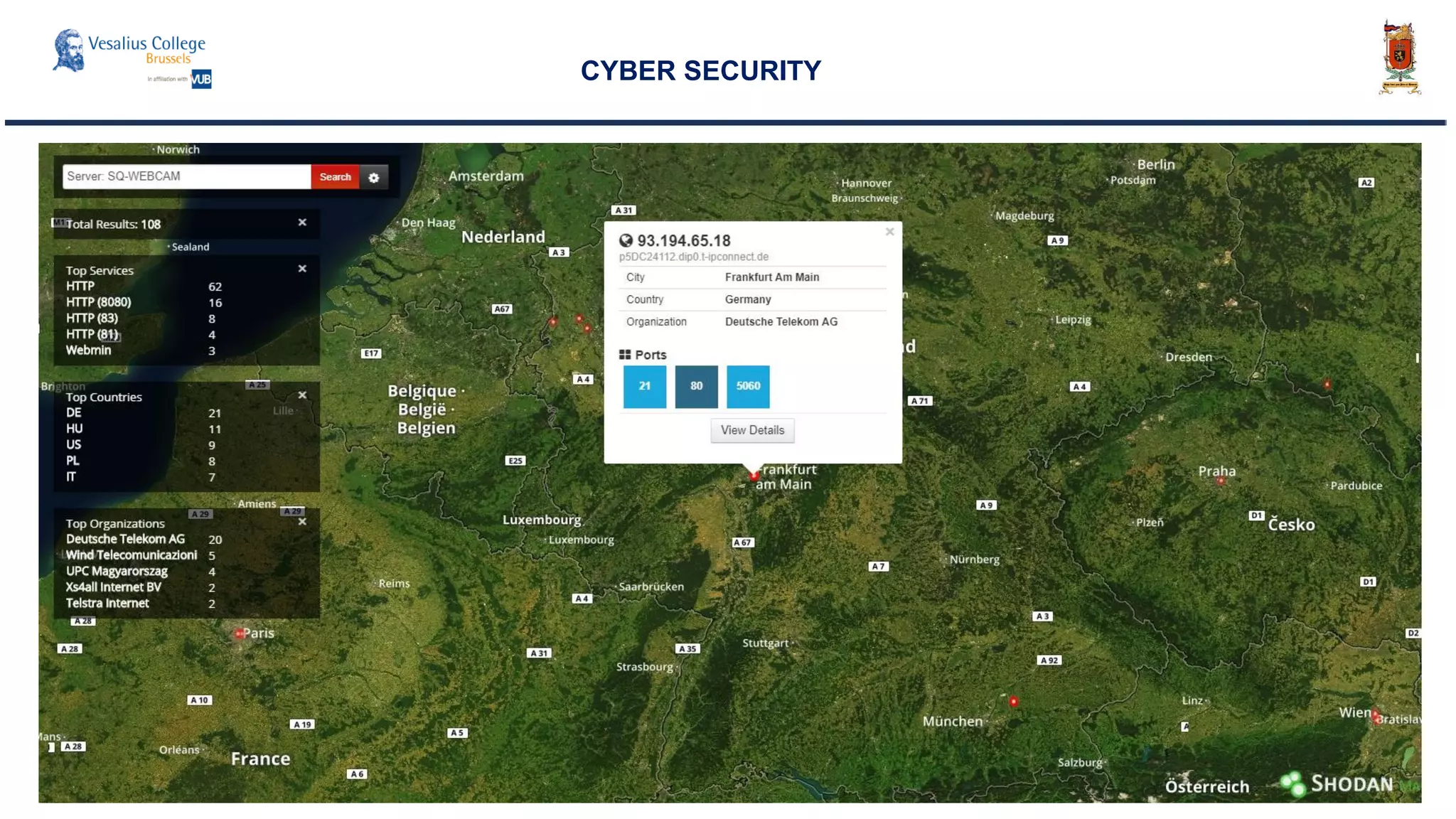


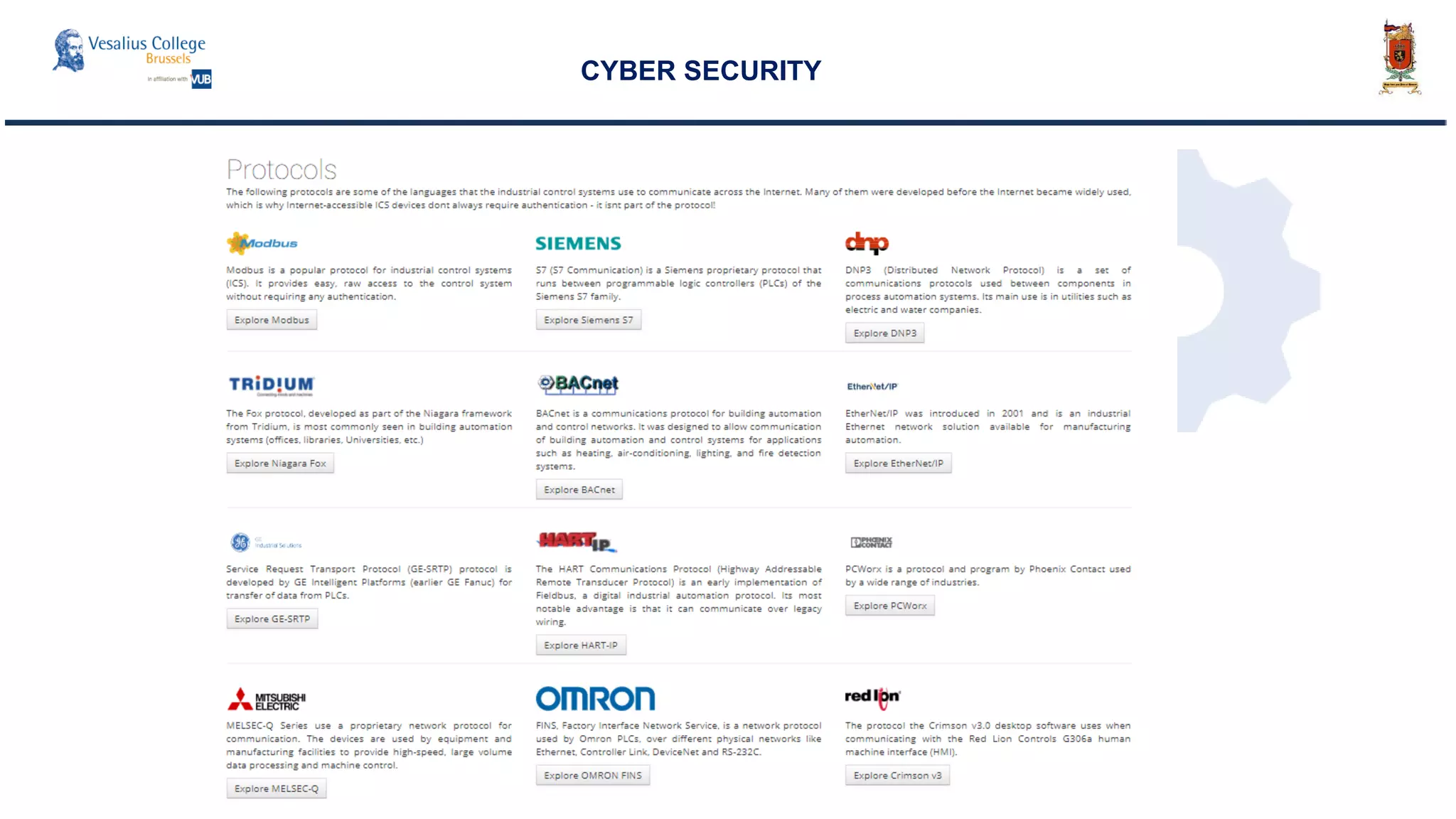



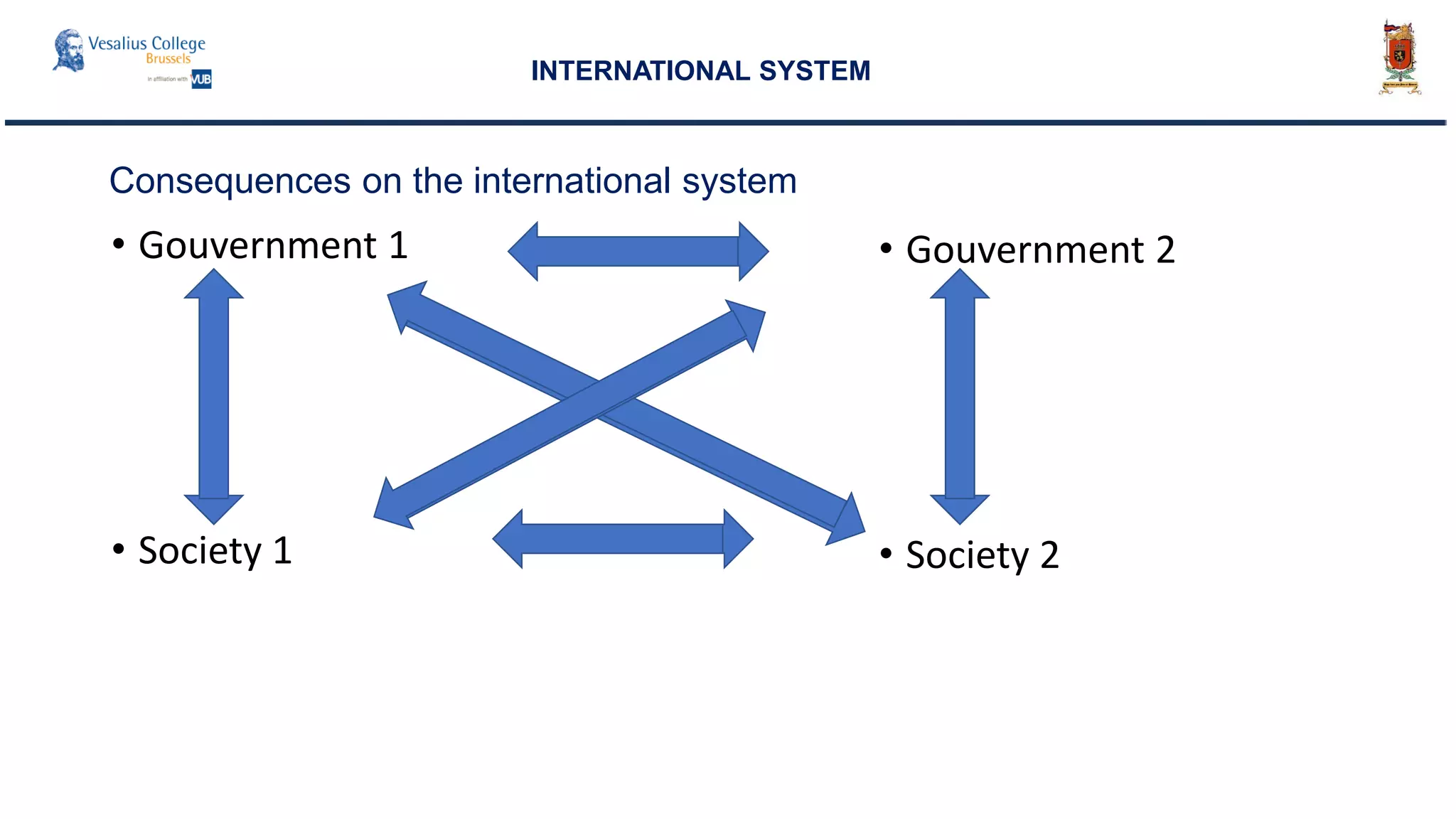
![Consequences on the international system
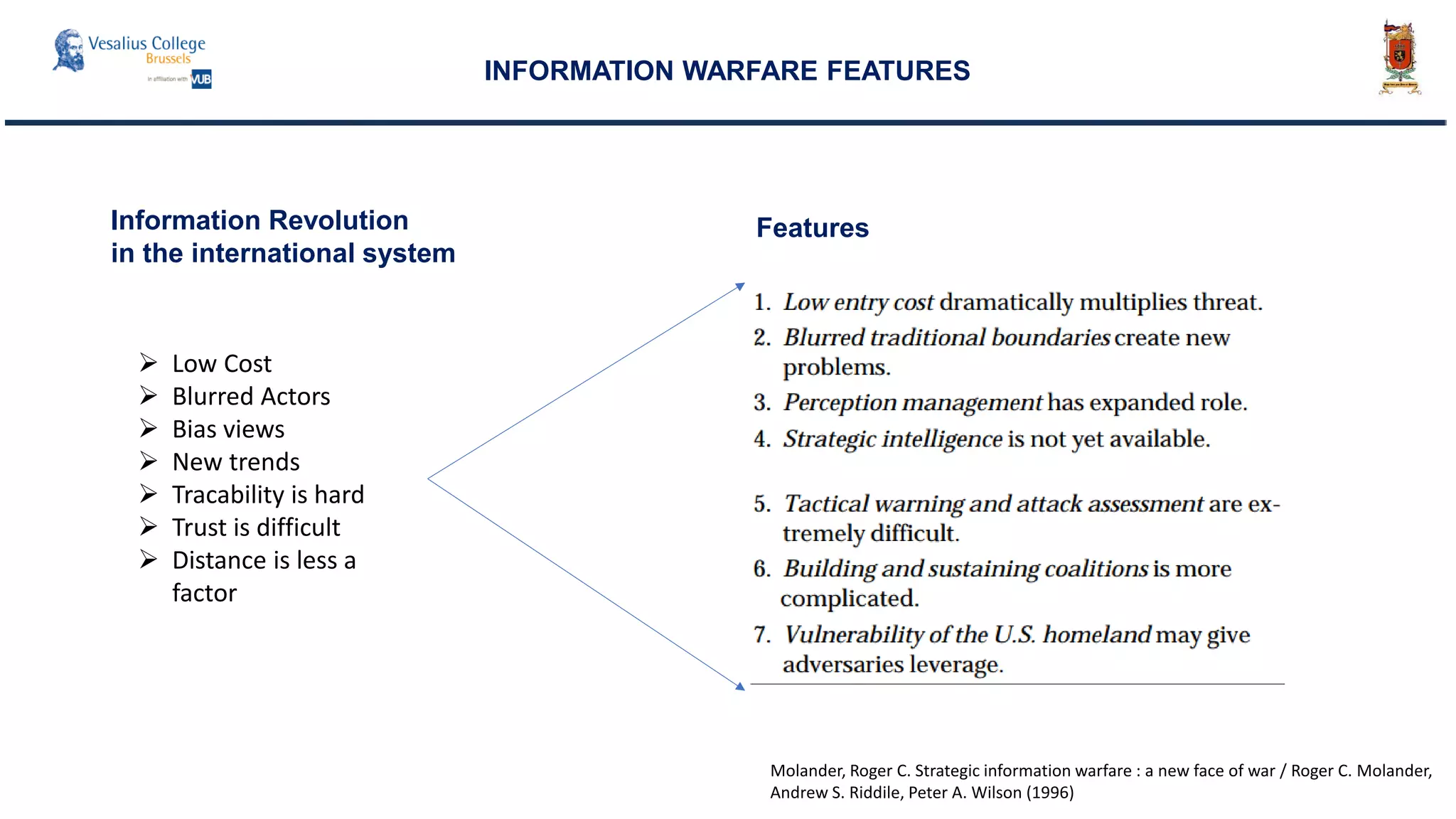
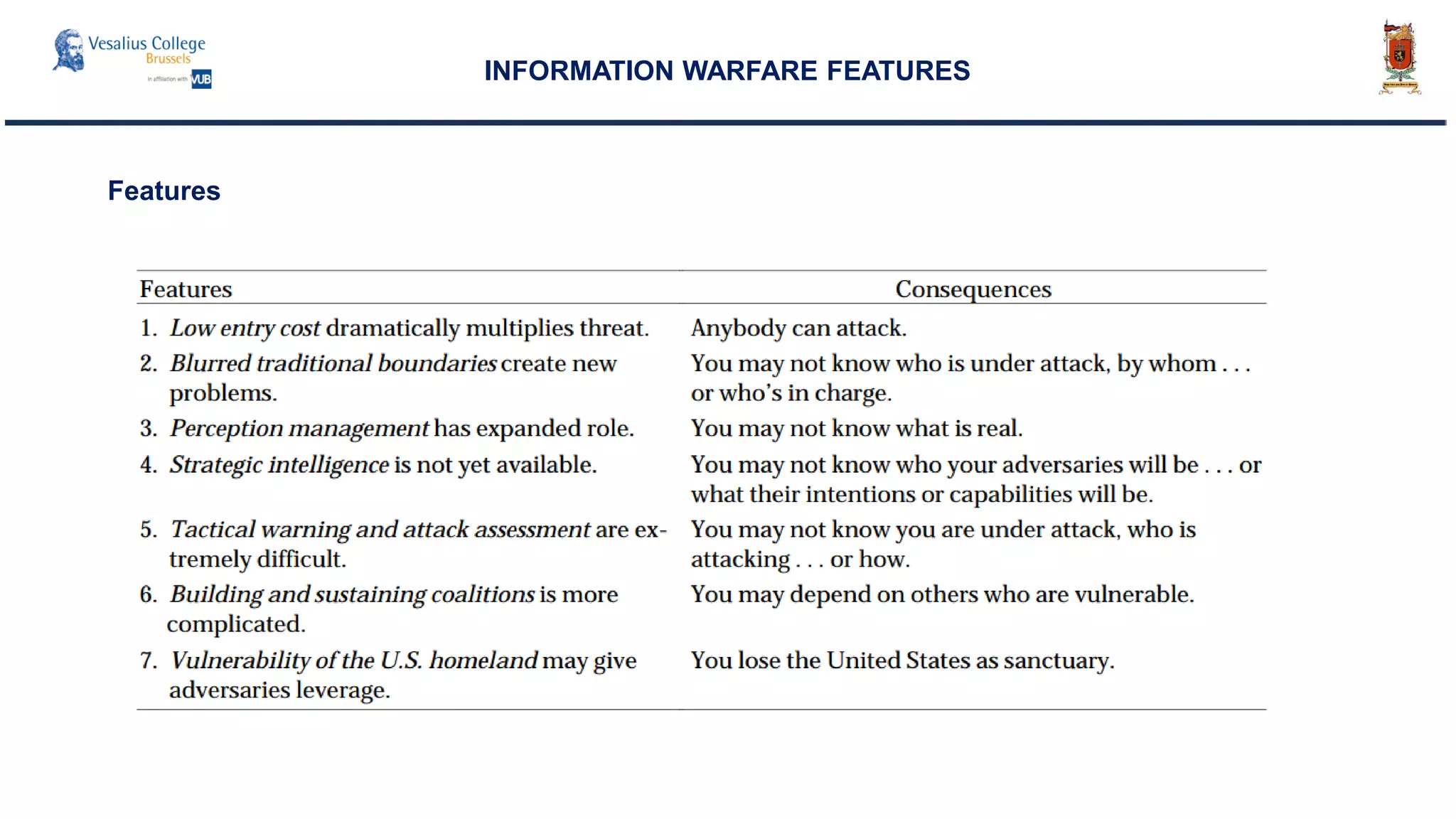
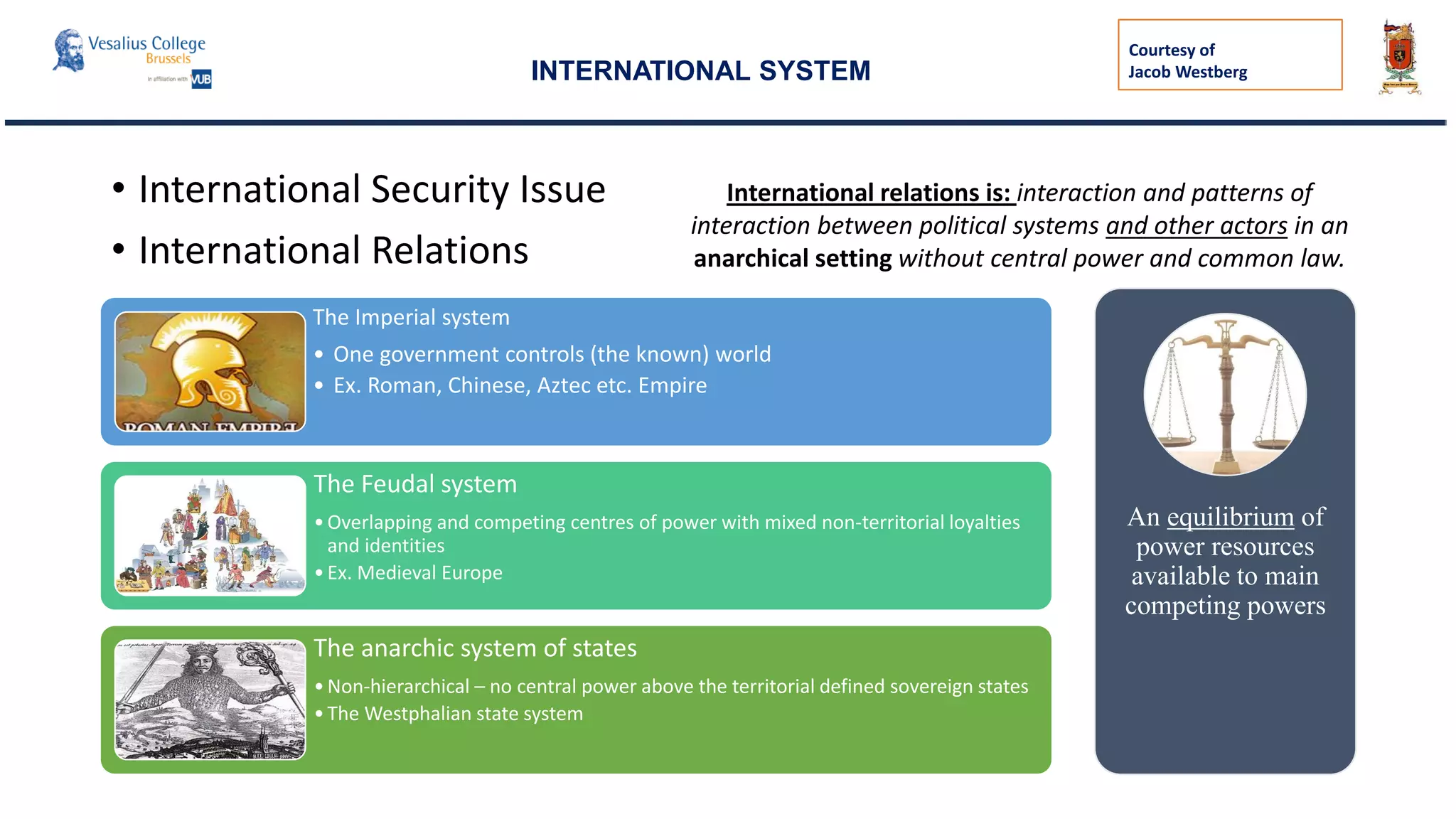
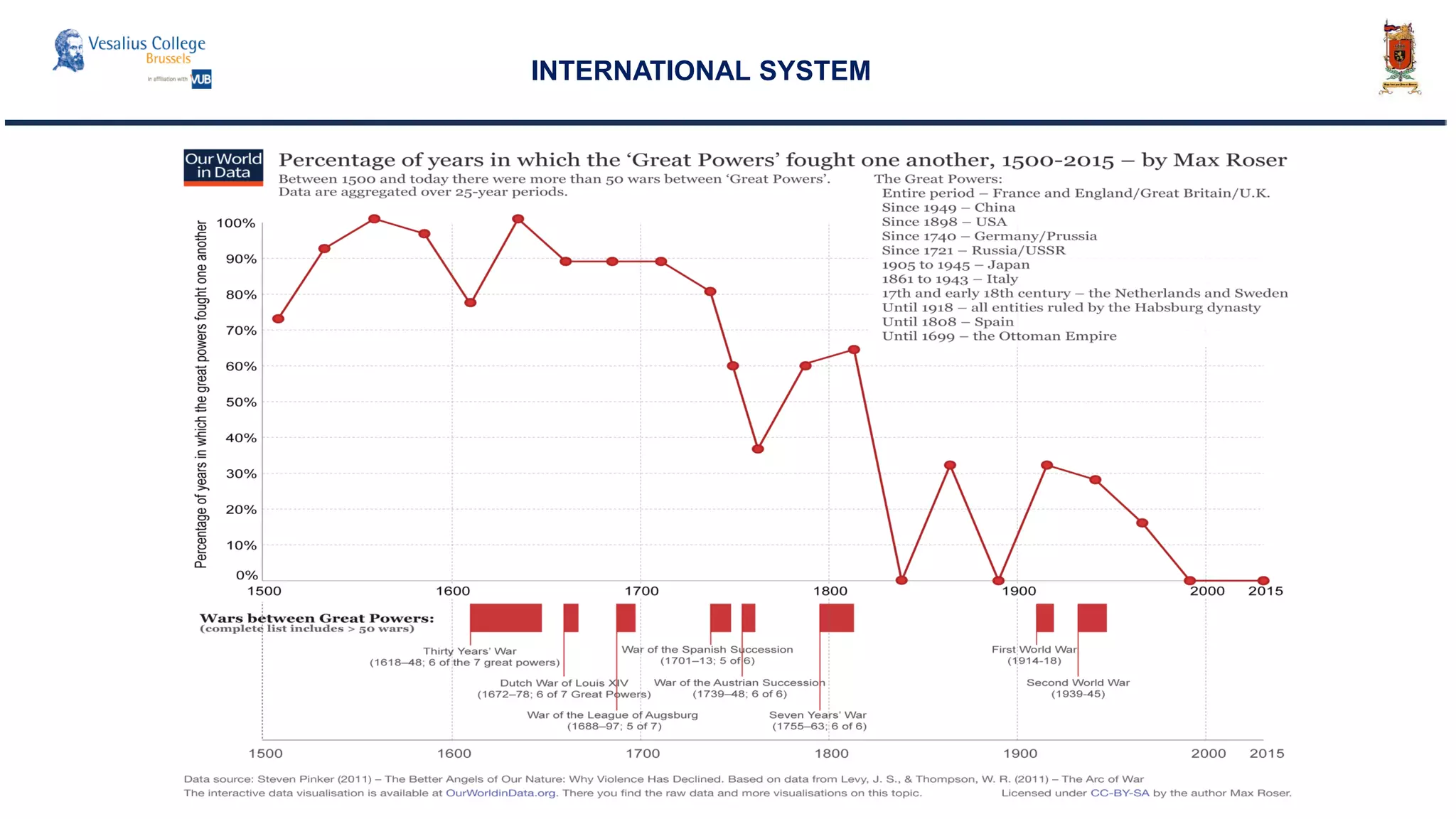
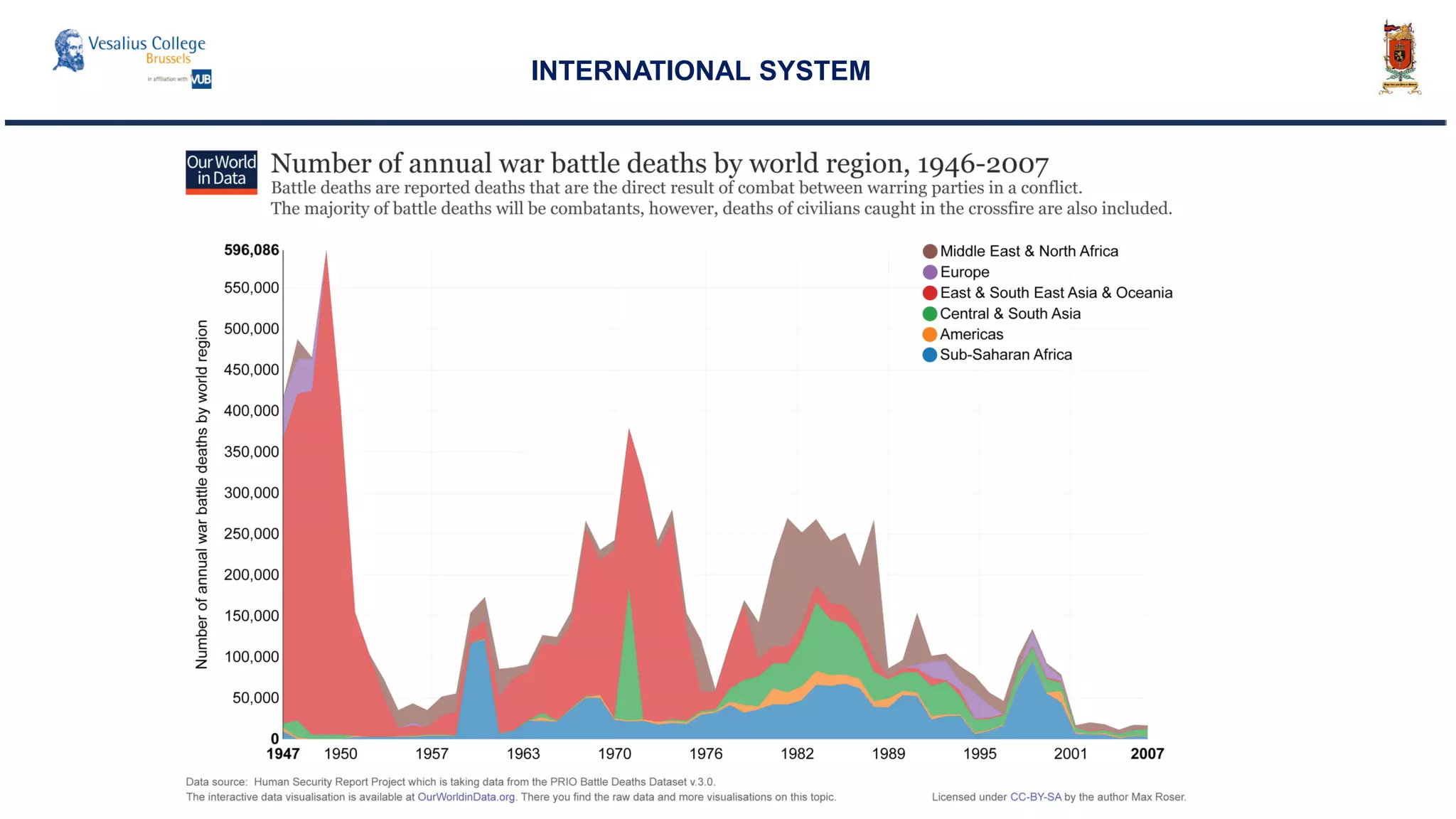
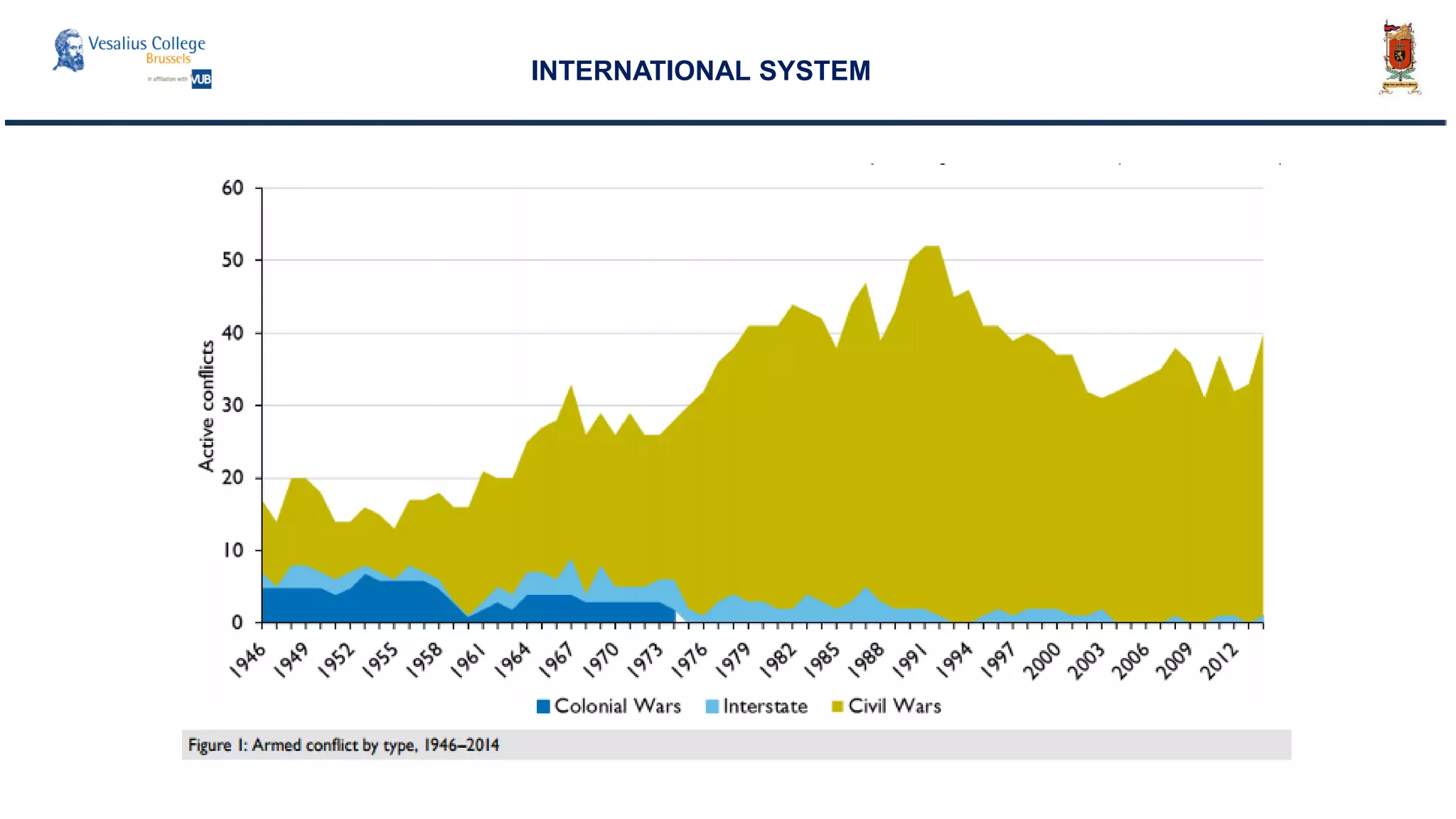
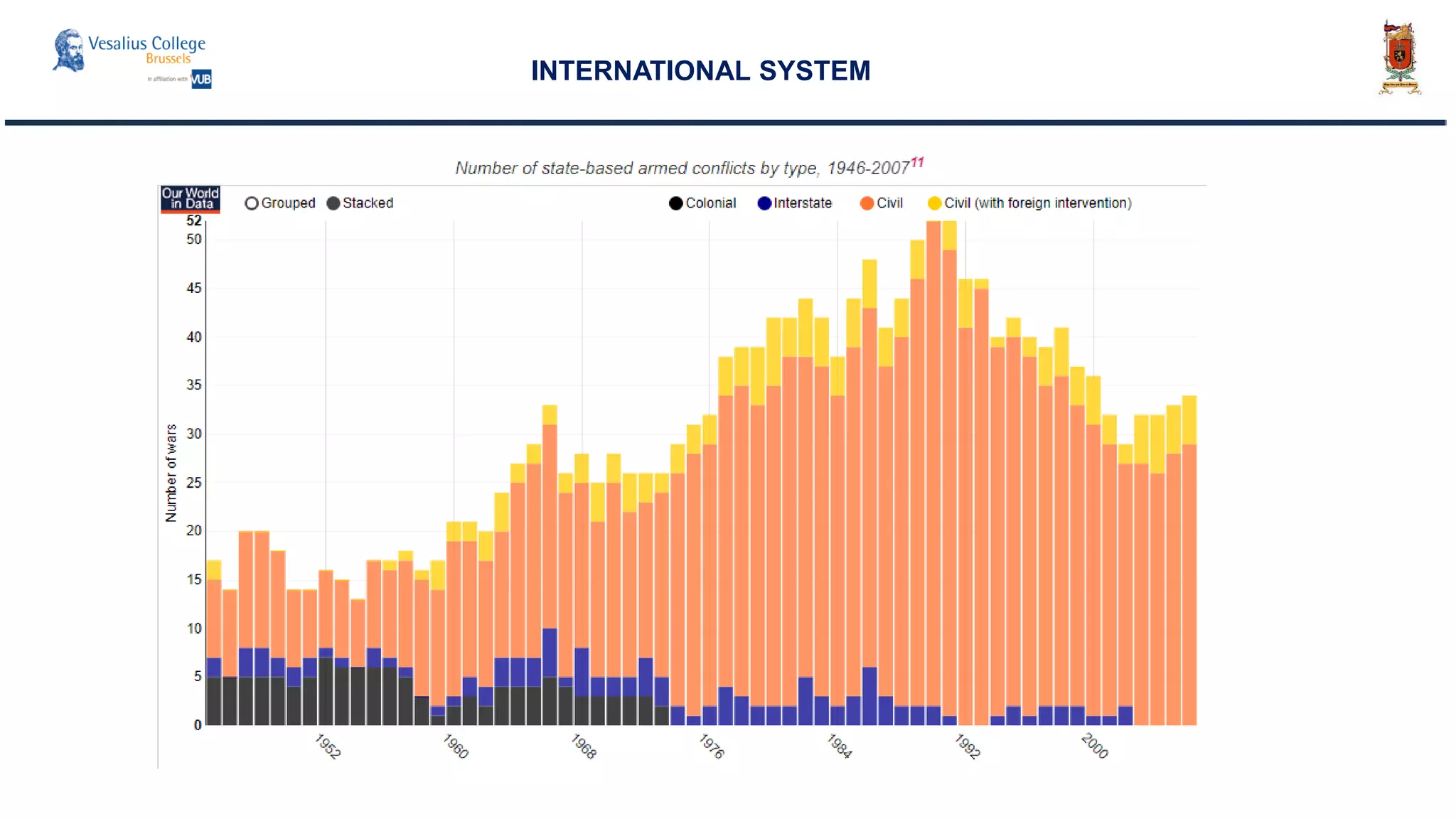
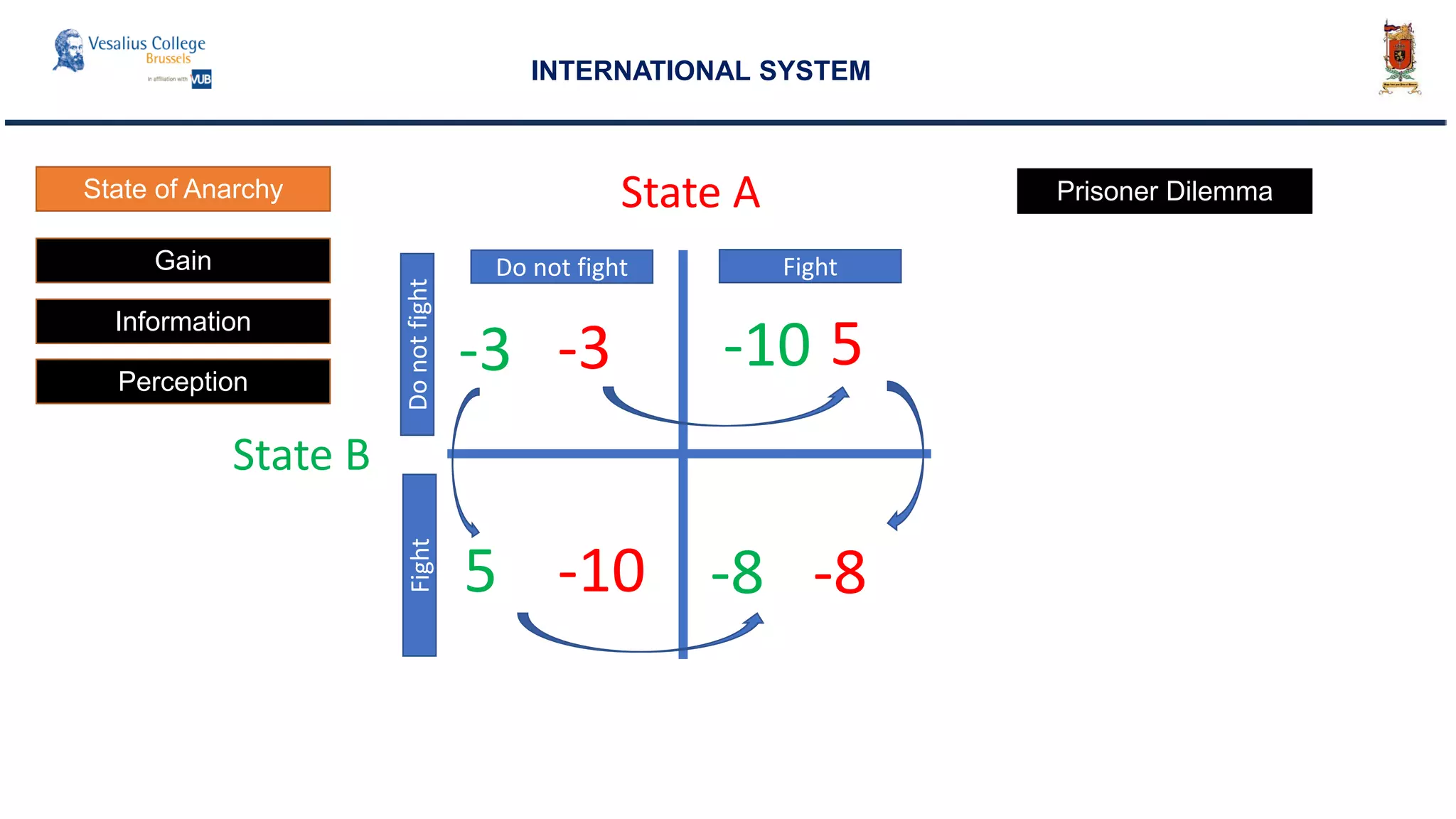
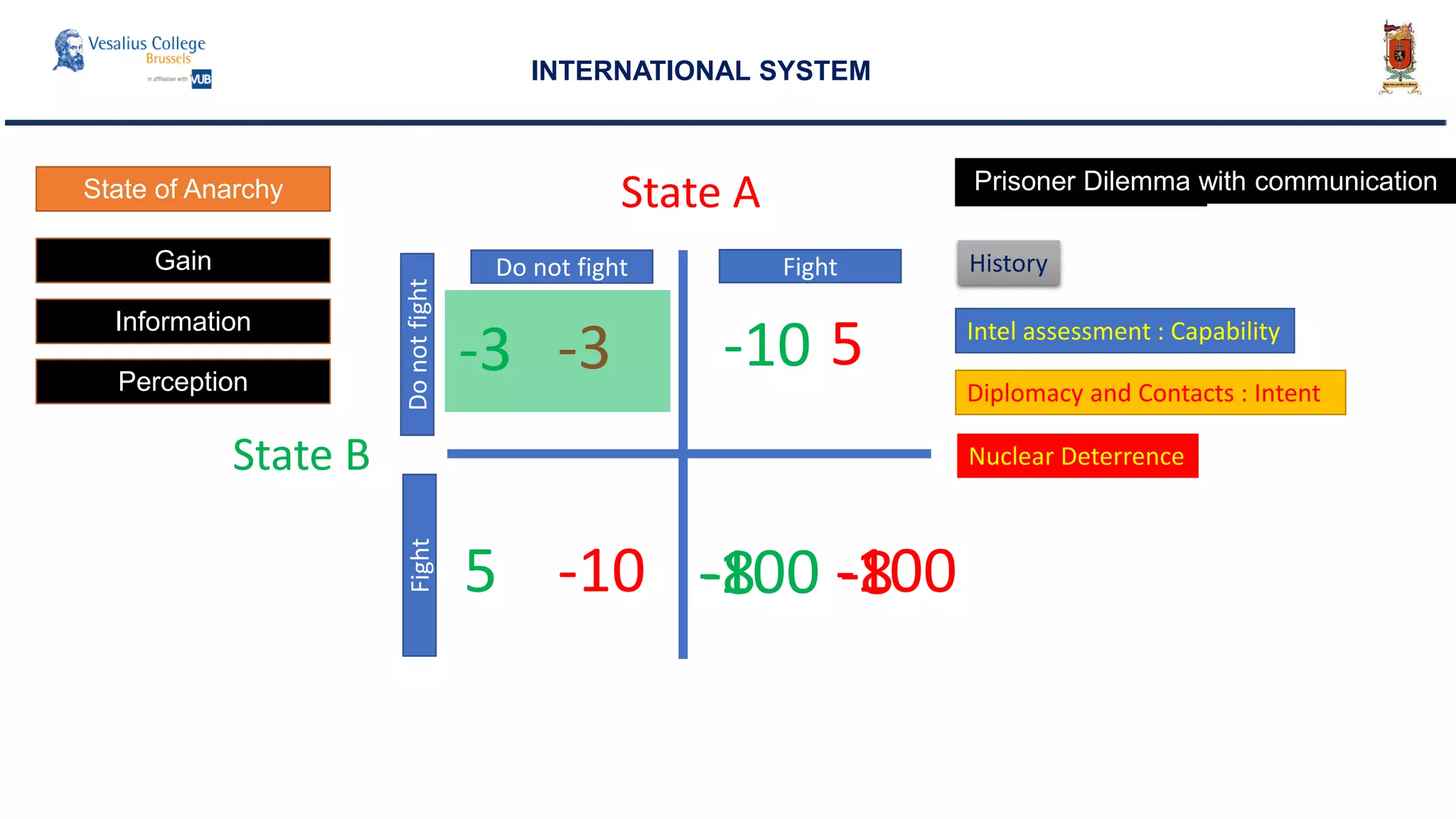
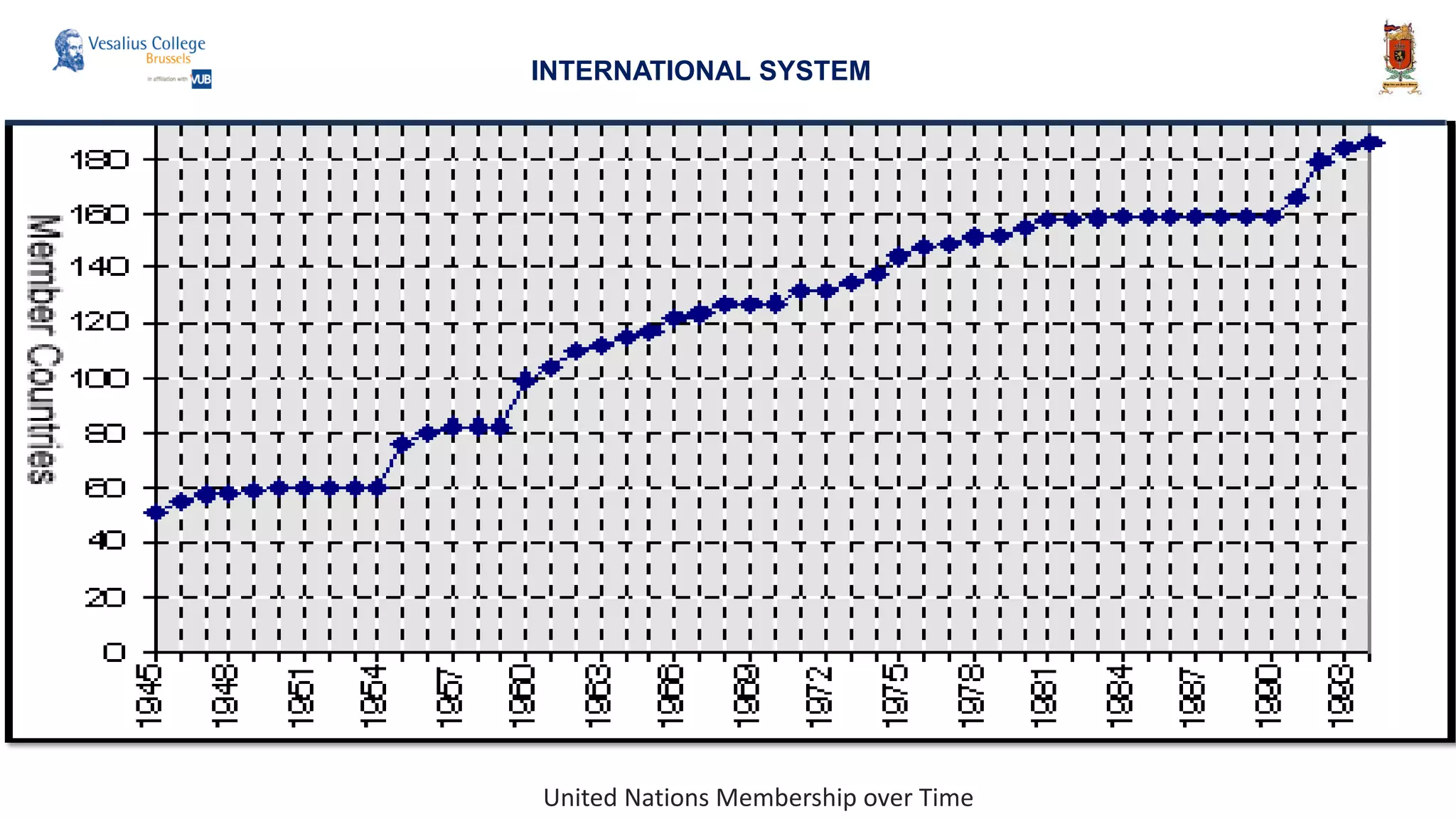
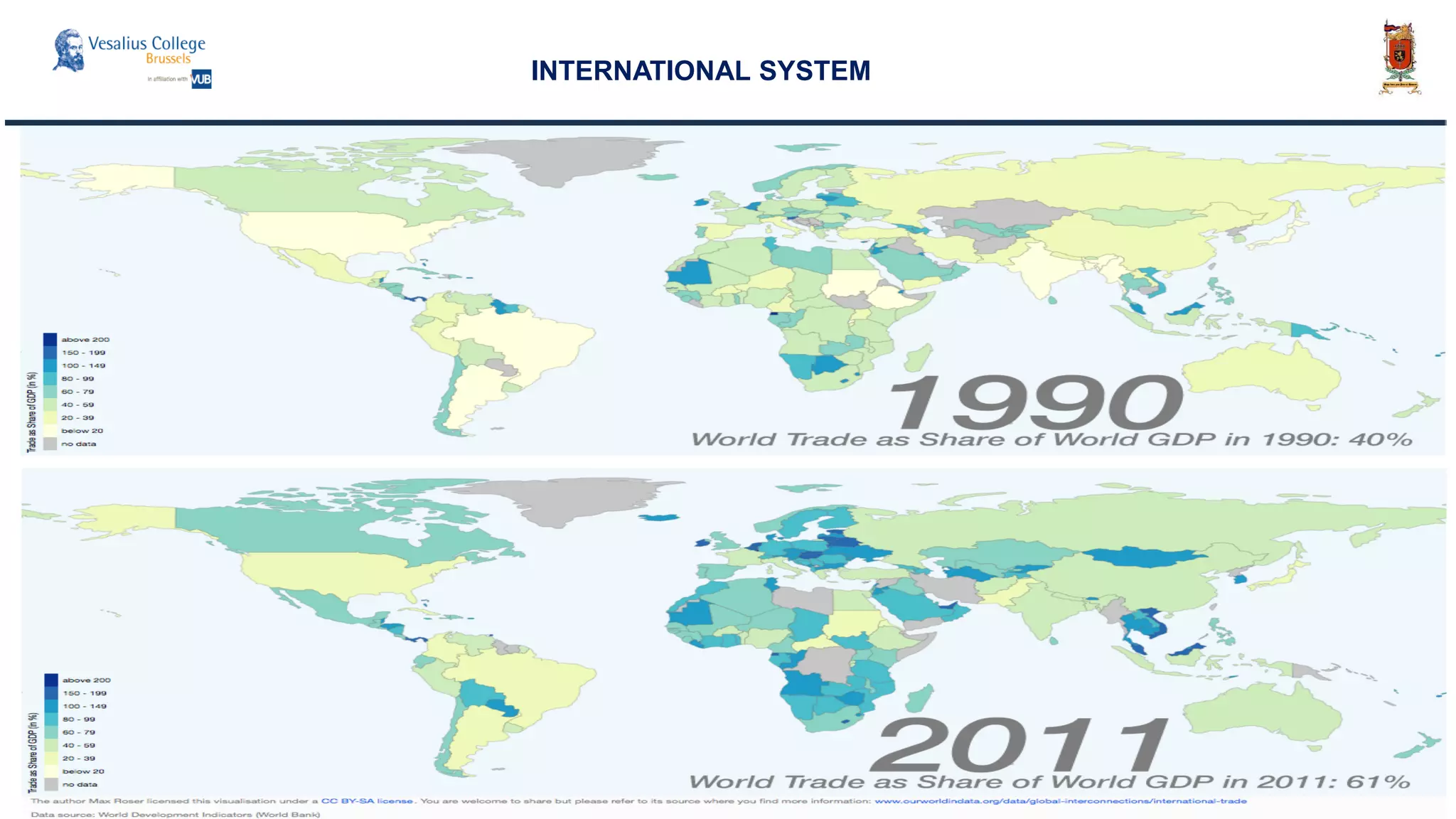
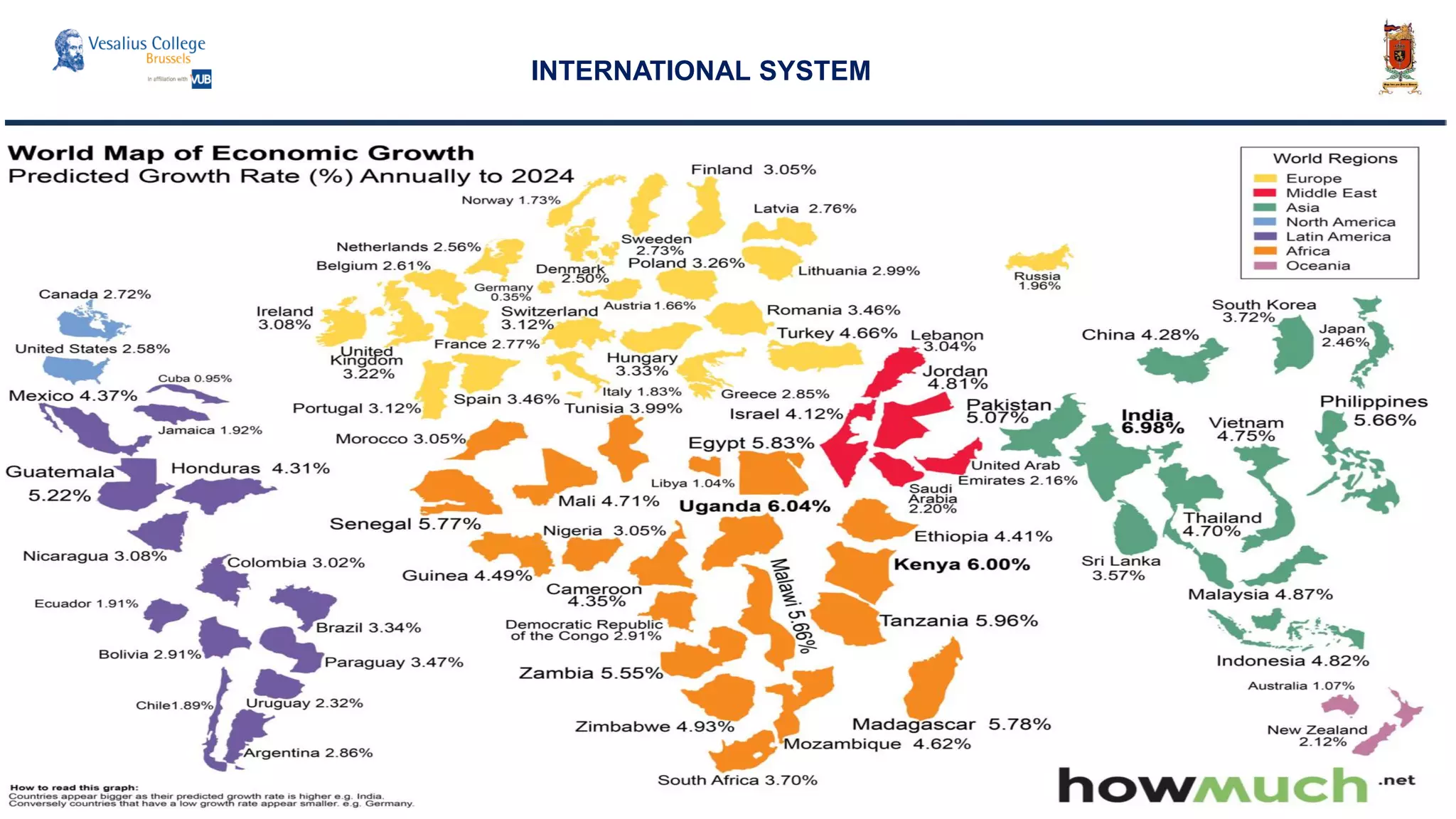
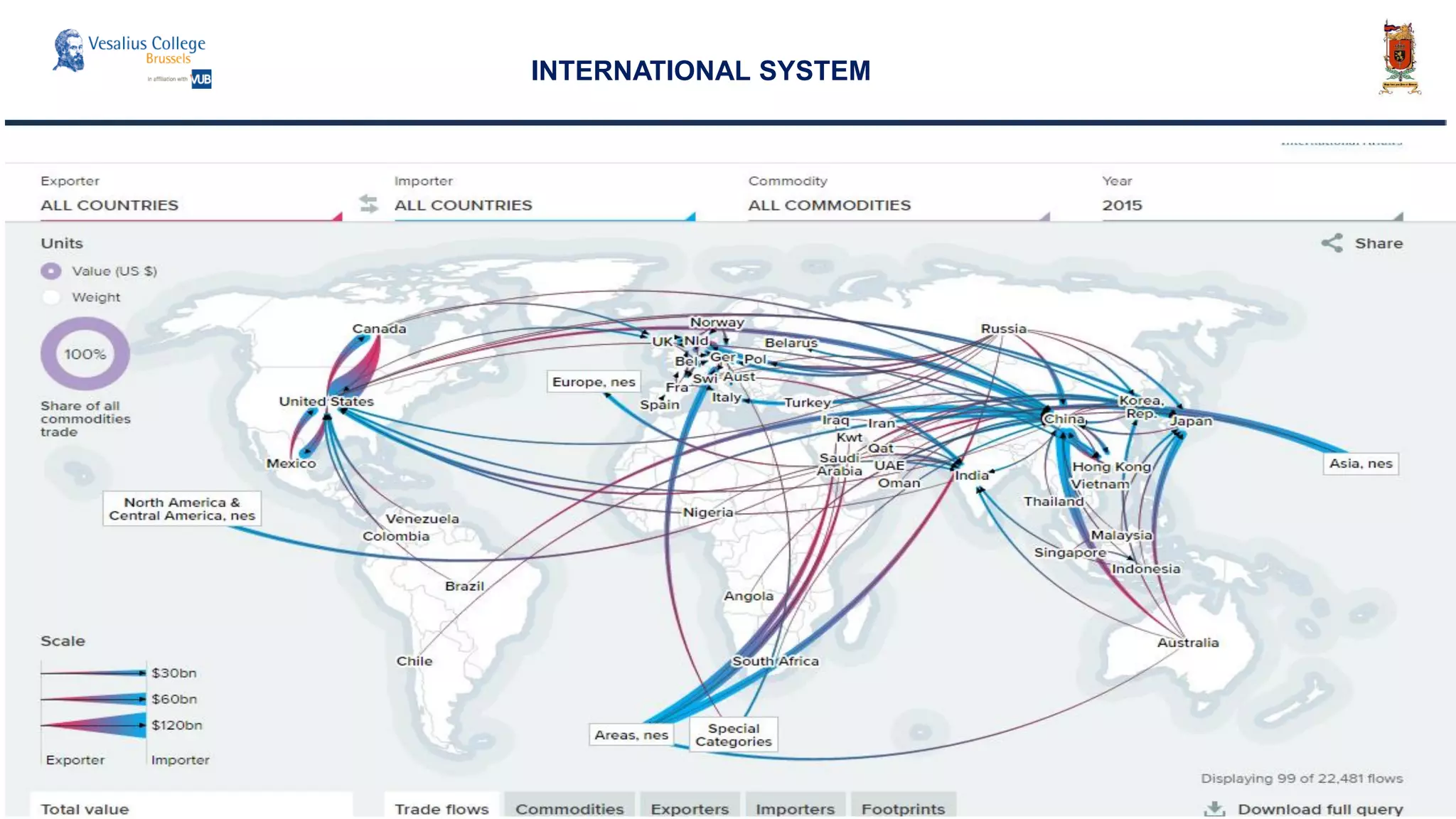
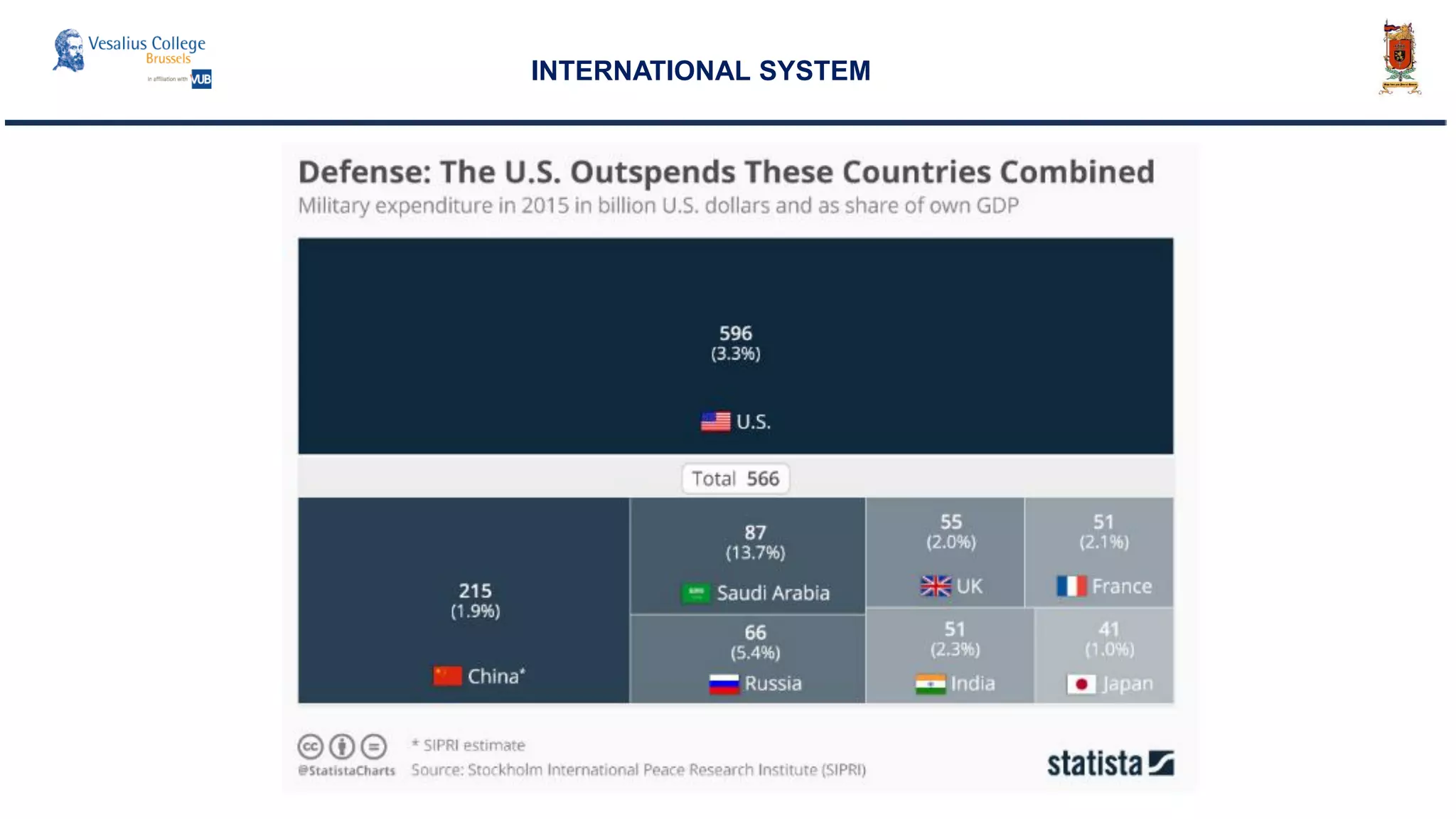
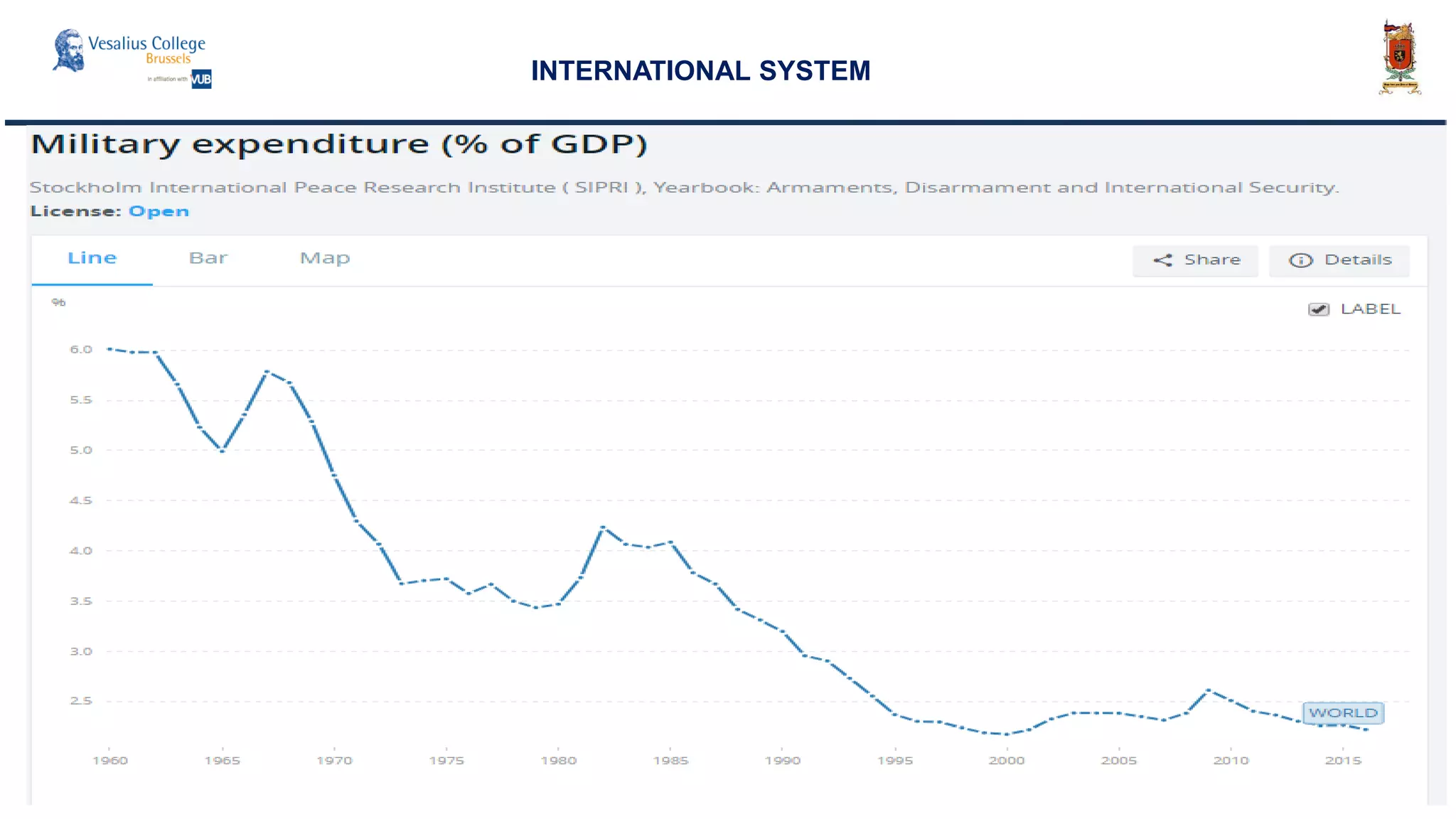
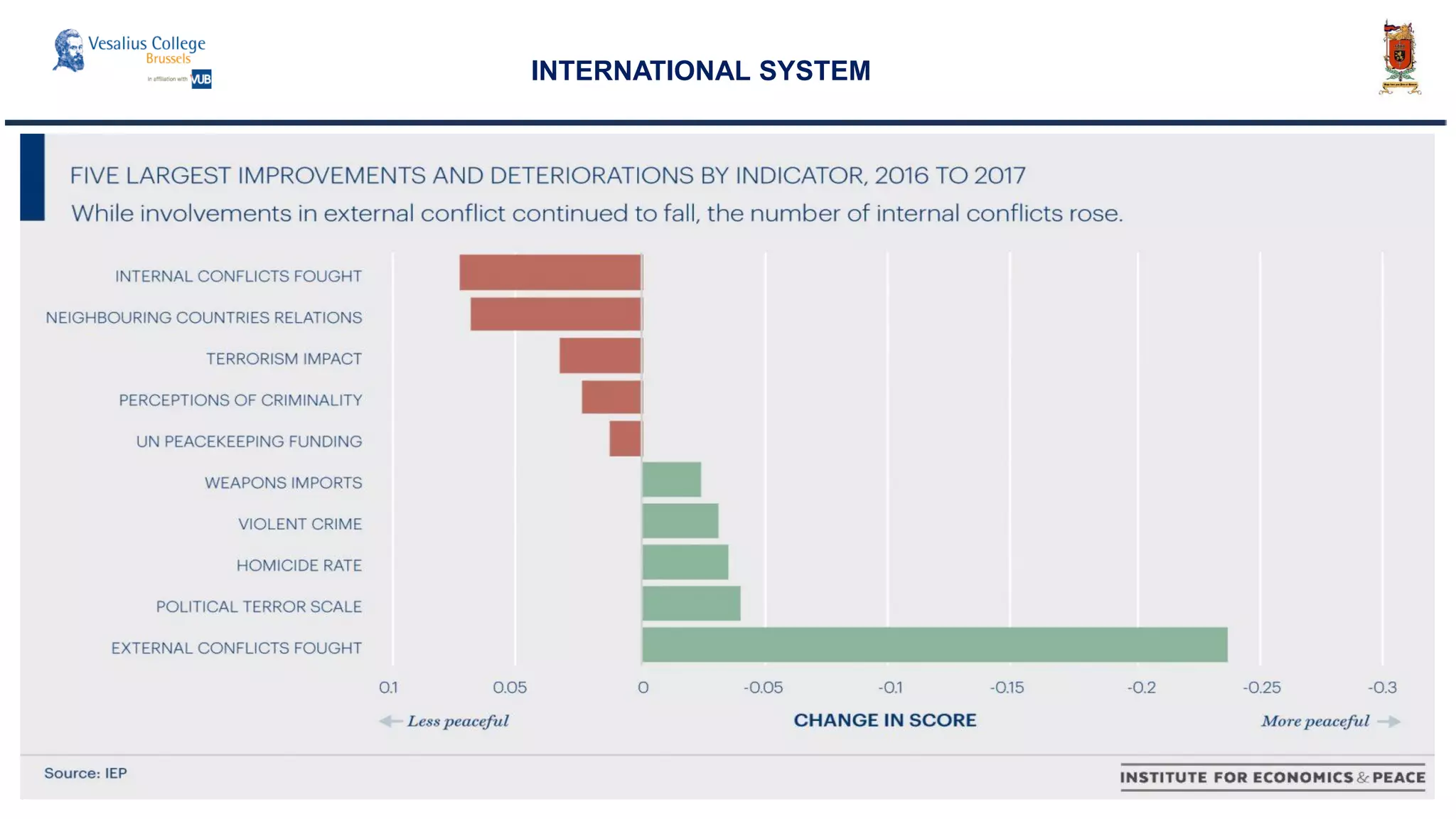
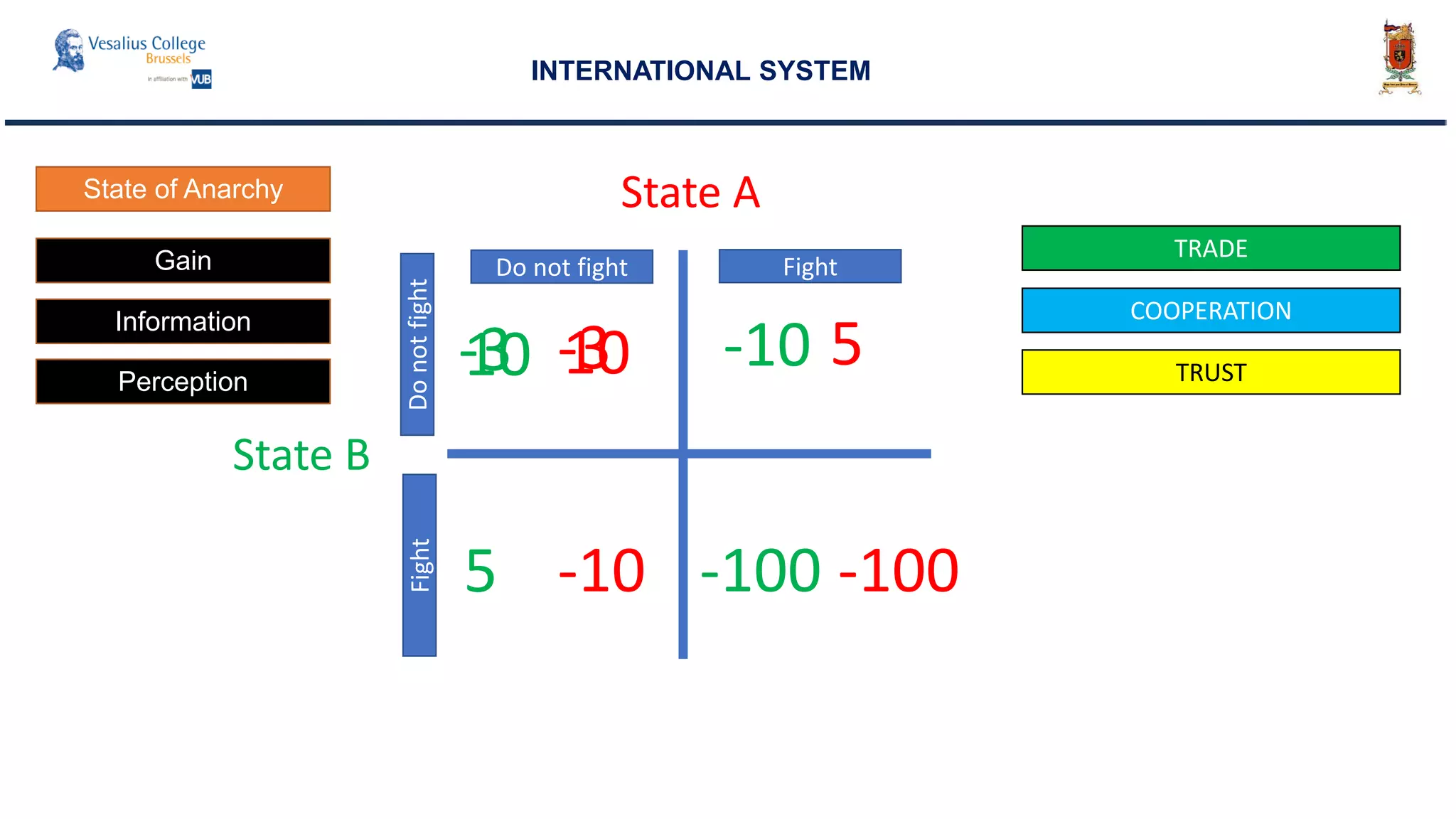
INTERNATIONAL SYSTEM
• Information is power : Information as a good
• Information is a nonrival good. [...]
• One person’s consumption does not diminish that of another.
• If I give you a light, it does not diminish my light.
• But in a competitive situation, it makes a big difference if I have the
light first and see things before you do.
Joseph S. Nye](https://image.slidesharecdn.com/cybersecurity-aglobalsecurityissue-180718141348/75/Cyber-Security-Information-Warfare-A-global-security-issue-55-2048.jpg)