This document provides an introduction to bug bounty programs. It defines what a bug bounty program is, provides a brief history of major programs, and discusses reasons they are beneficial for both security researchers and companies. Key points covered include popular programs like Google and Facebook, tools used in bug hunting like Burp Suite, and lessons for researchers such as writing quality reports and following each program's rules.



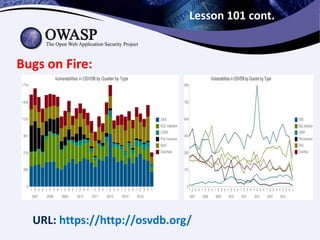
![History of Bug Bounty
At October 1995 by Netscape.
At August 2002 by iDefense [VCP].
At August 2004 by Mozilla.
2007 CanSecWest……ZDI…$10k..
March 24, 2010…pwn2own..big money.
Days before 2008 was Tough for Security
Researchers.
2009, the year of revolution.](https://image.slidesharecdn.com/owasp-bd-bug-bounty-101-150212130003-conversion-gate01/85/Bug-Bounty-101-4-320.jpg)






















![Lesson 101 cont.
Please DO NOT:
Don’t be a Shit.
Don’t Lie.
Don’t cry for SWAG /Money /HOF if it’s out of rules.
Don’t disrespect other researchers.
Don’t Copy-Paste from other reports.
Please, Don’t share your payouts. [amounts]](https://image.slidesharecdn.com/owasp-bd-bug-bounty-101-150212130003-conversion-gate01/85/Bug-Bounty-101-28-320.jpg)