This document provides an overview of bug bounty hunting. It discusses:
- What bug bounty programs are and how they work
- A brief history of major bug bounty programs from the 1990s to present day
- Reasons to participate in bug bounty hunting like money, career opportunities, and enjoyment
- Popular bug bounty platforms and programs
- How to get started with the process of bug hunting
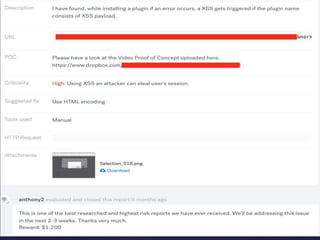
- Tips for writing bug reports that document the issue and steps to reproduce it
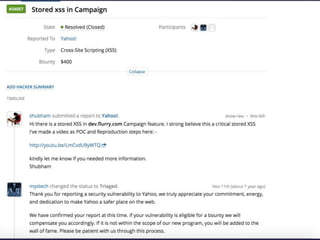
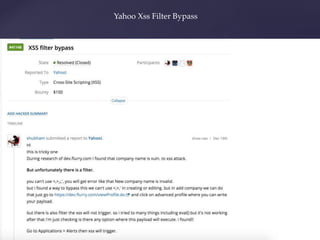
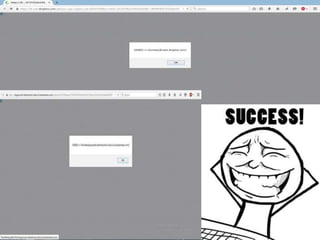
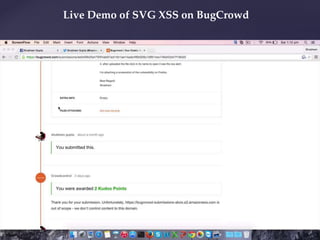
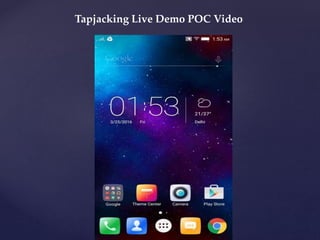
- Examples of past bug bounty finds, like an SVG XSS filter bypass and a tapjacking proof of concept