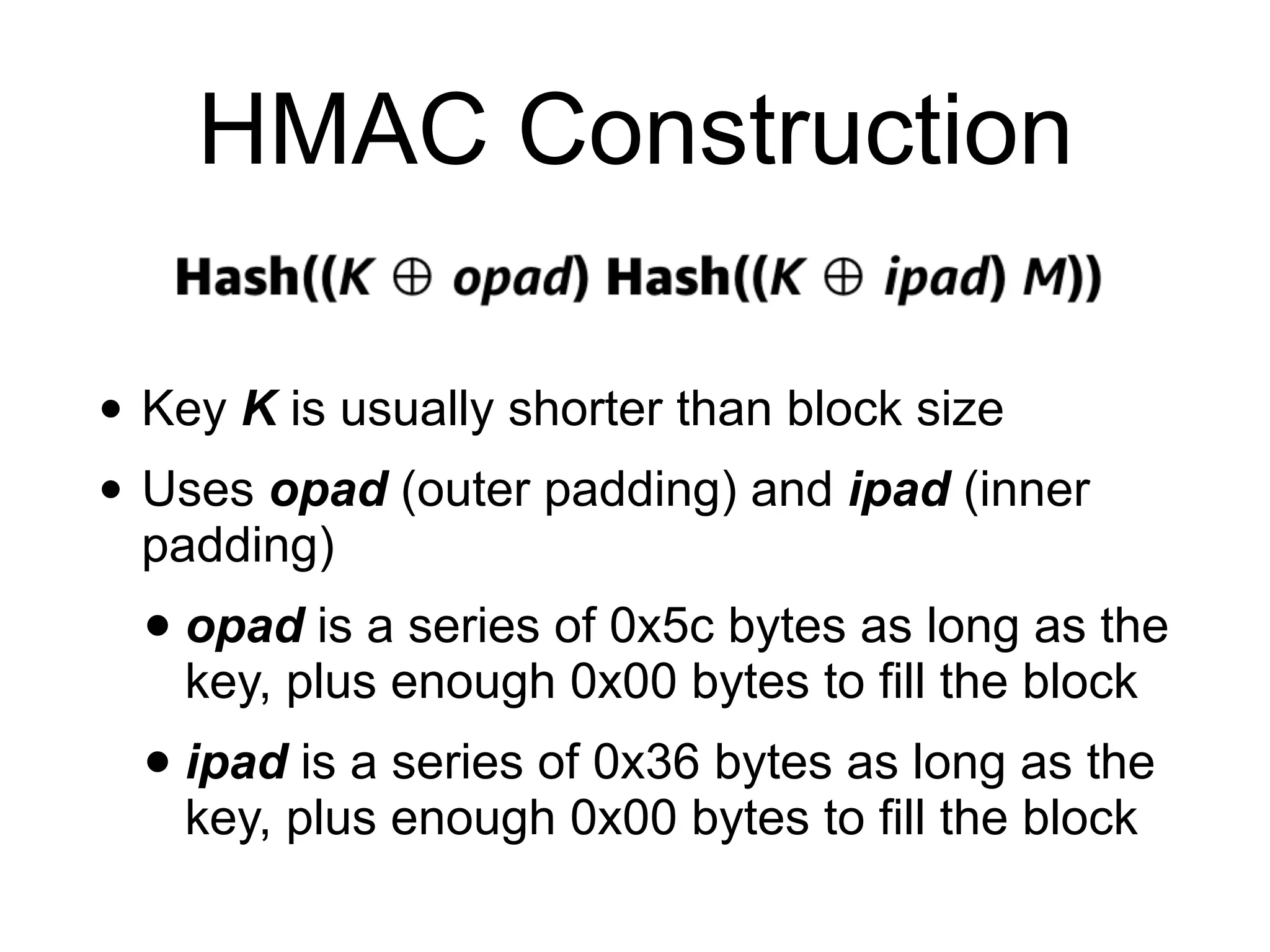
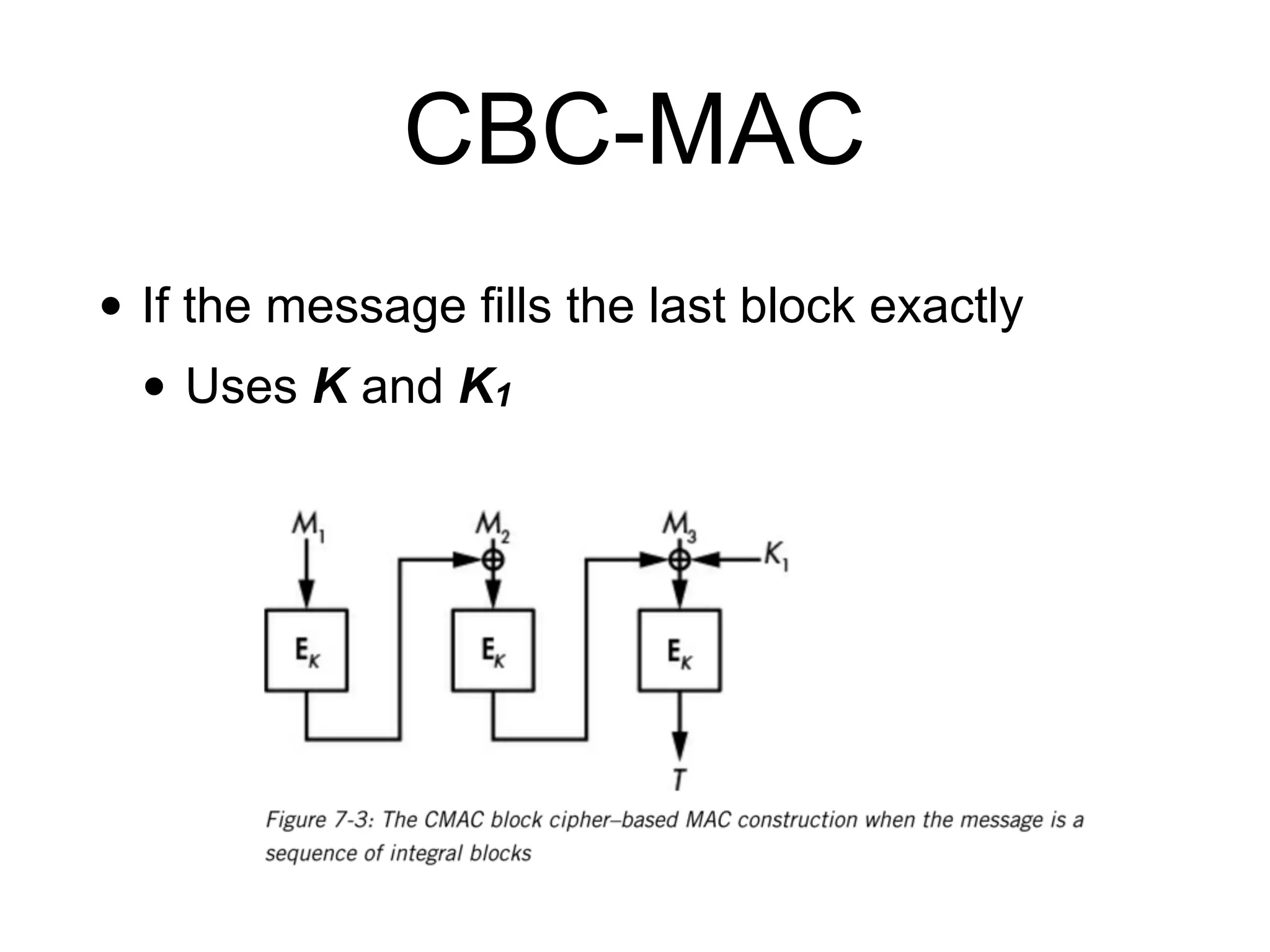
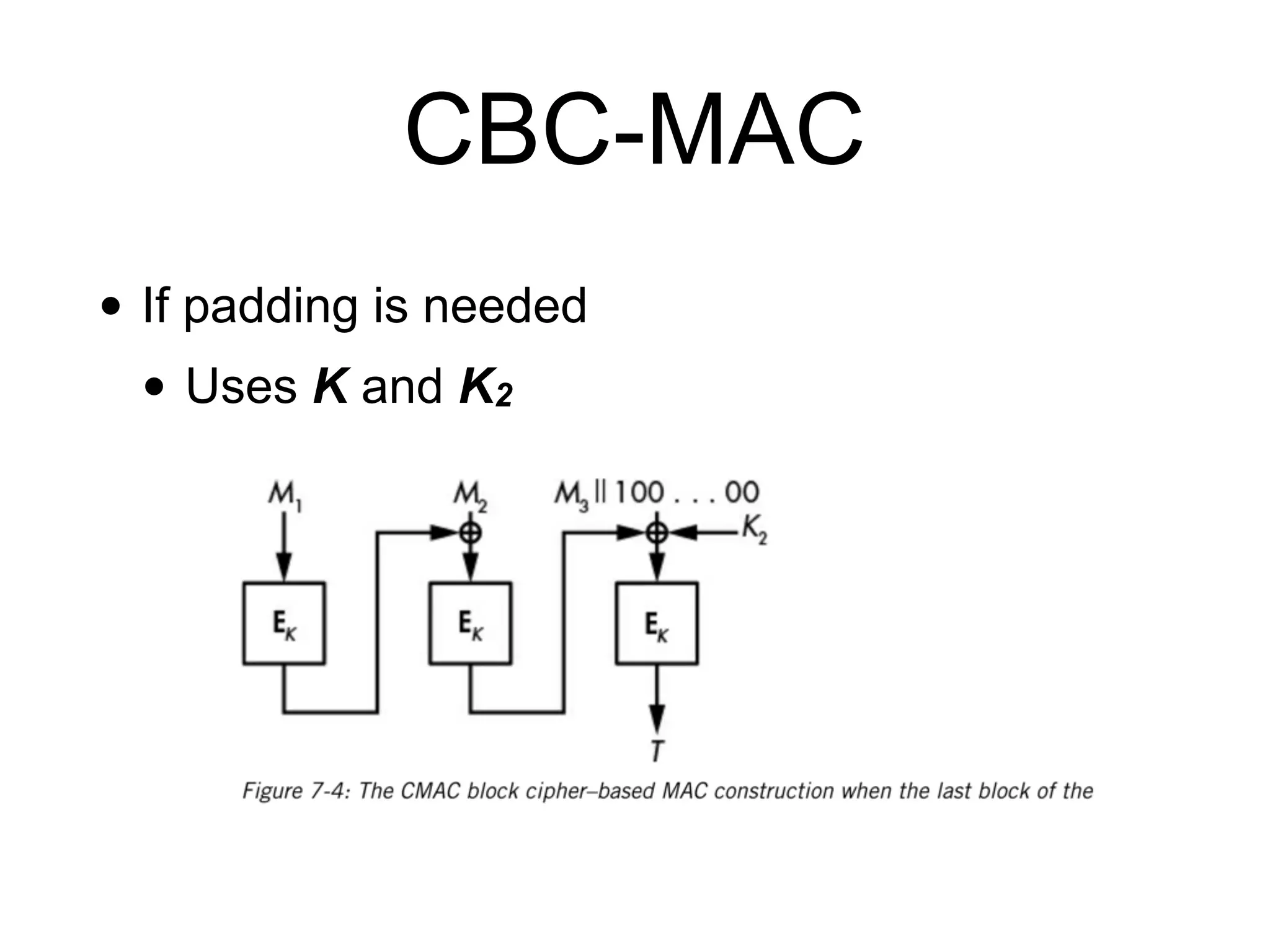
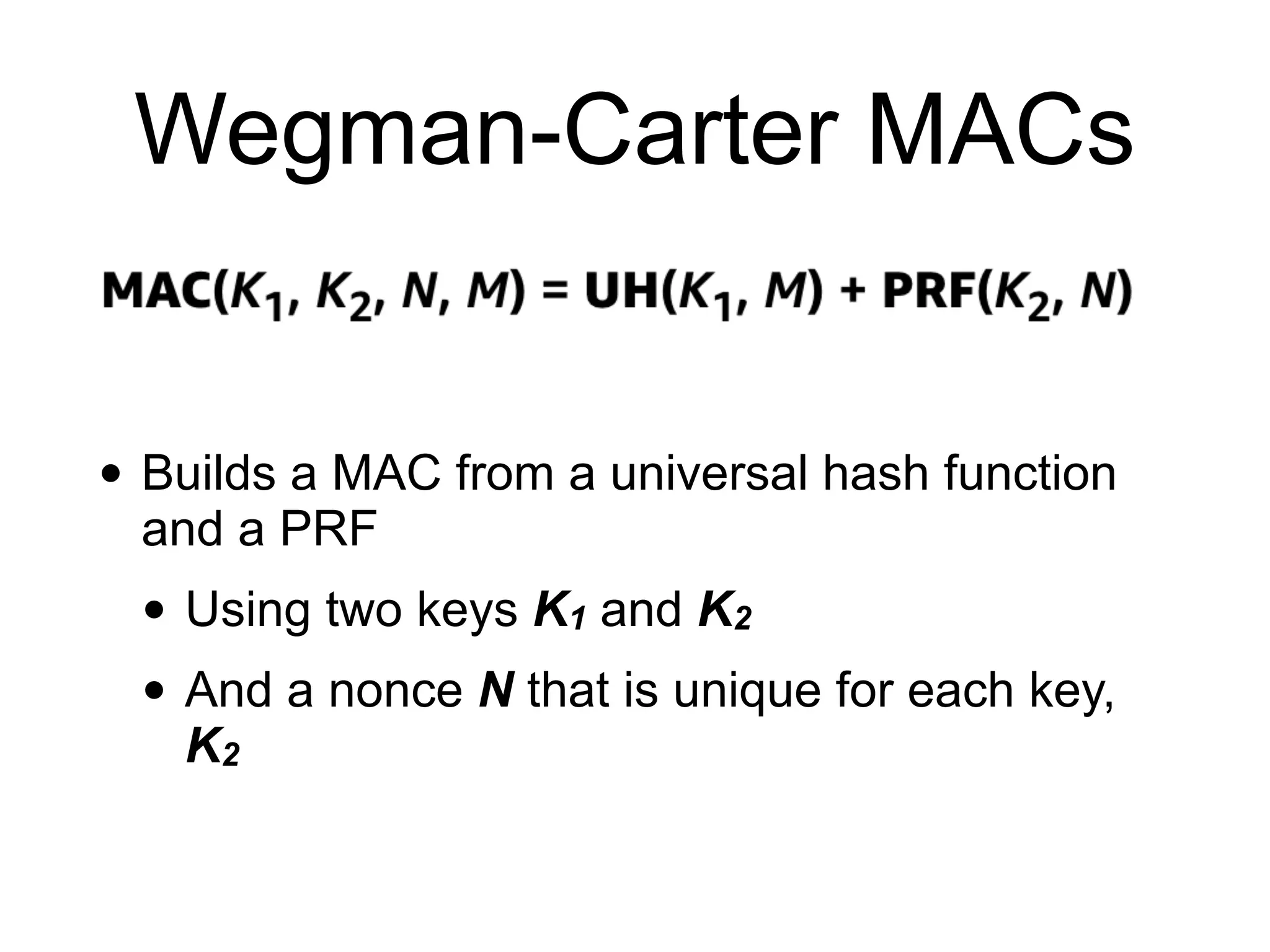
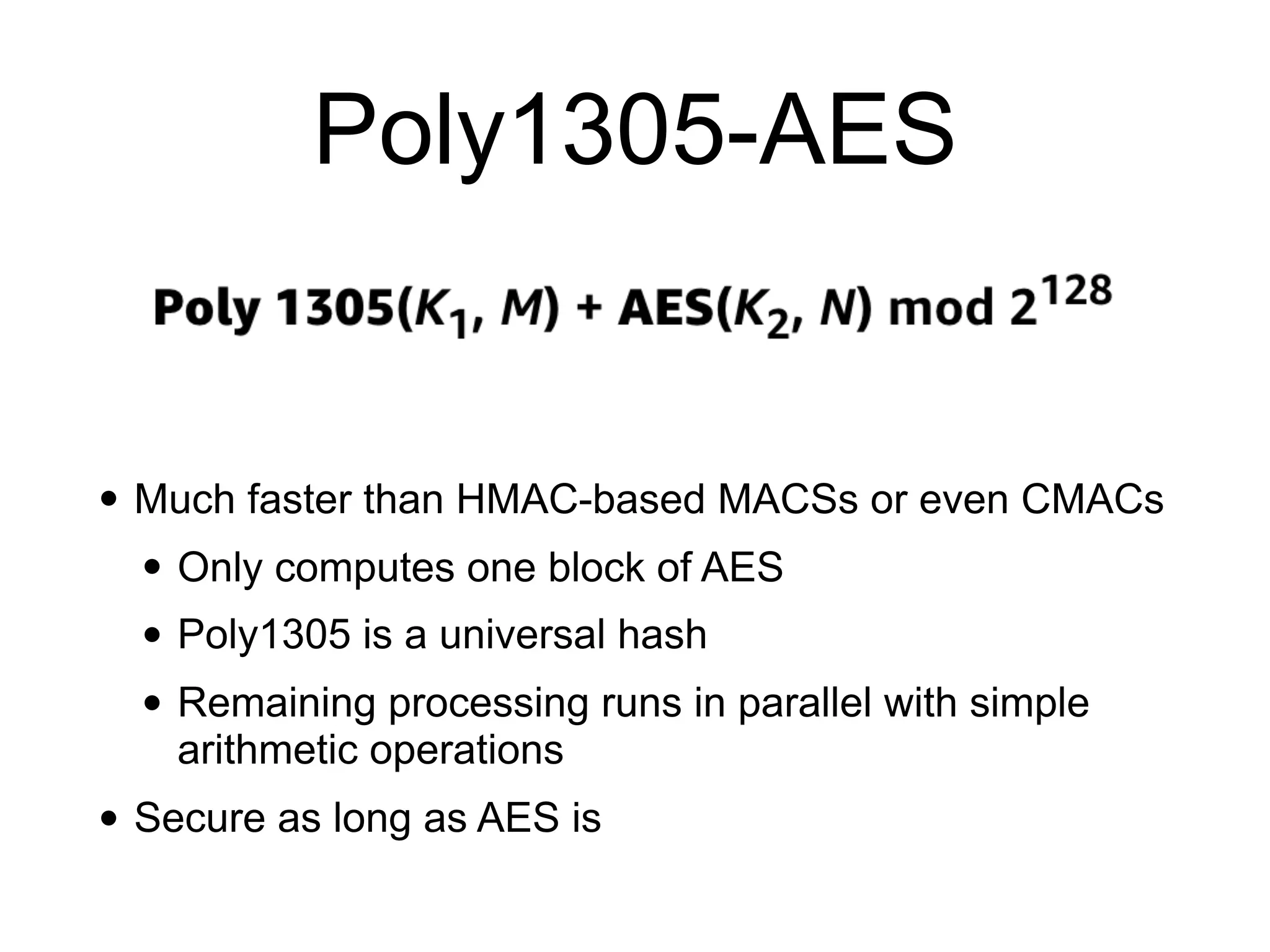
The document covers keyed hashing in cryptography, detailing Message Authentication Codes (MACs) and Pseudorandom Functions (PRFs) for securing message integrity and authenticity. It describes various constructions for keyed hashes, including secret-prefix and secret-suffix, and suggests improvements using HMAC and CMAC methods. Additionally, it highlights potential security vulnerabilities, such as replay attacks and timing attacks, stressing the importance of constant-time implementations.