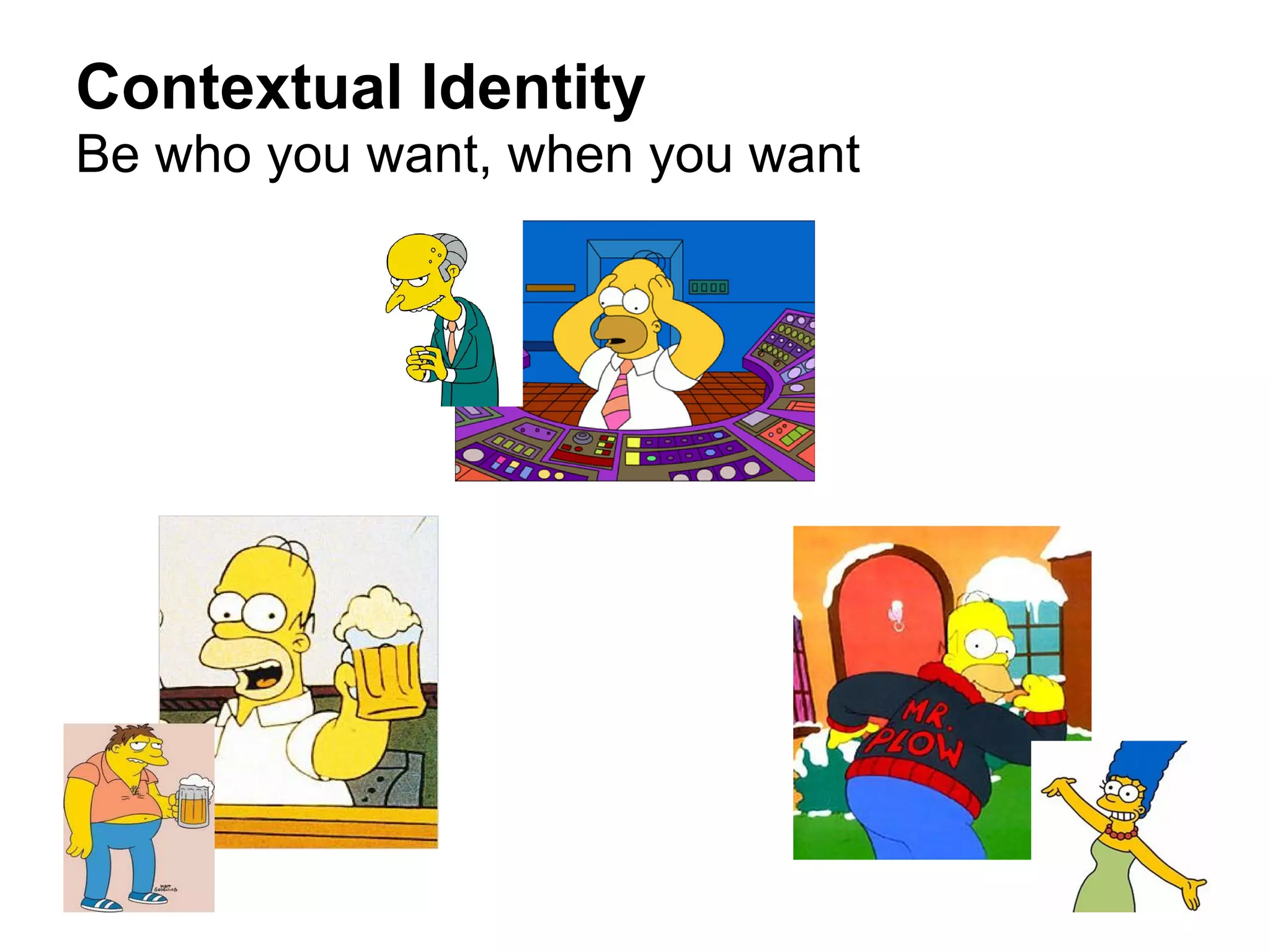
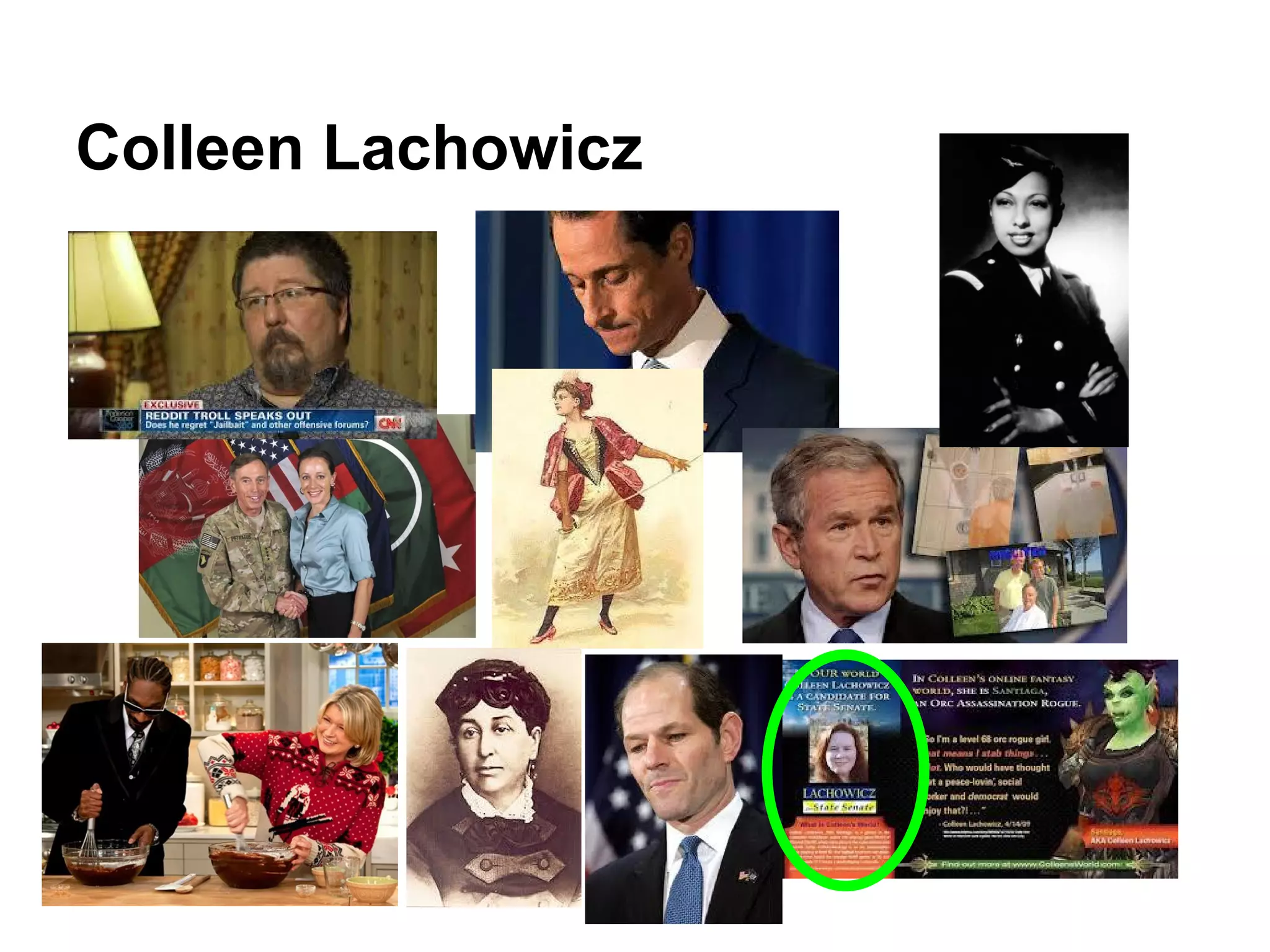
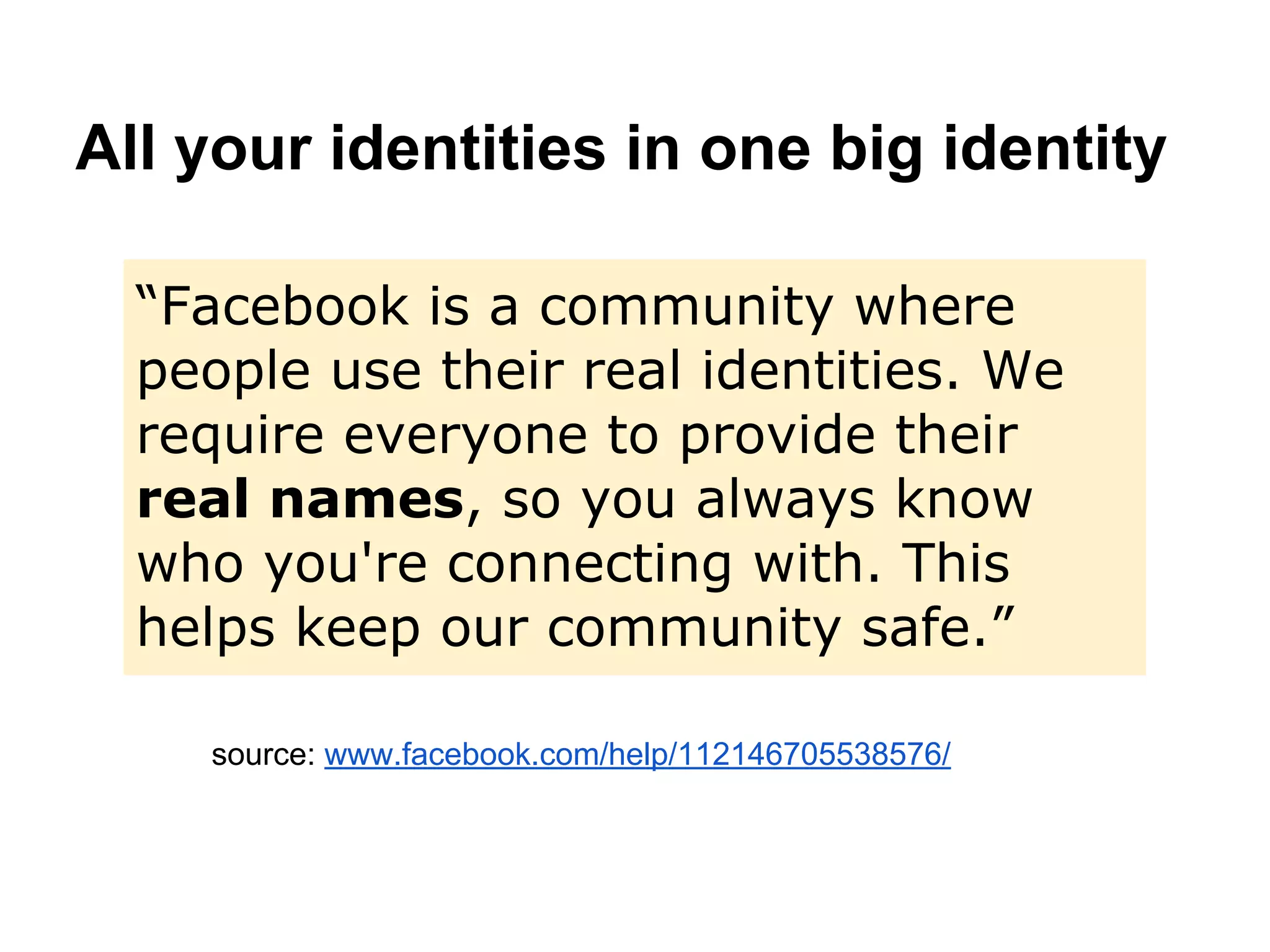
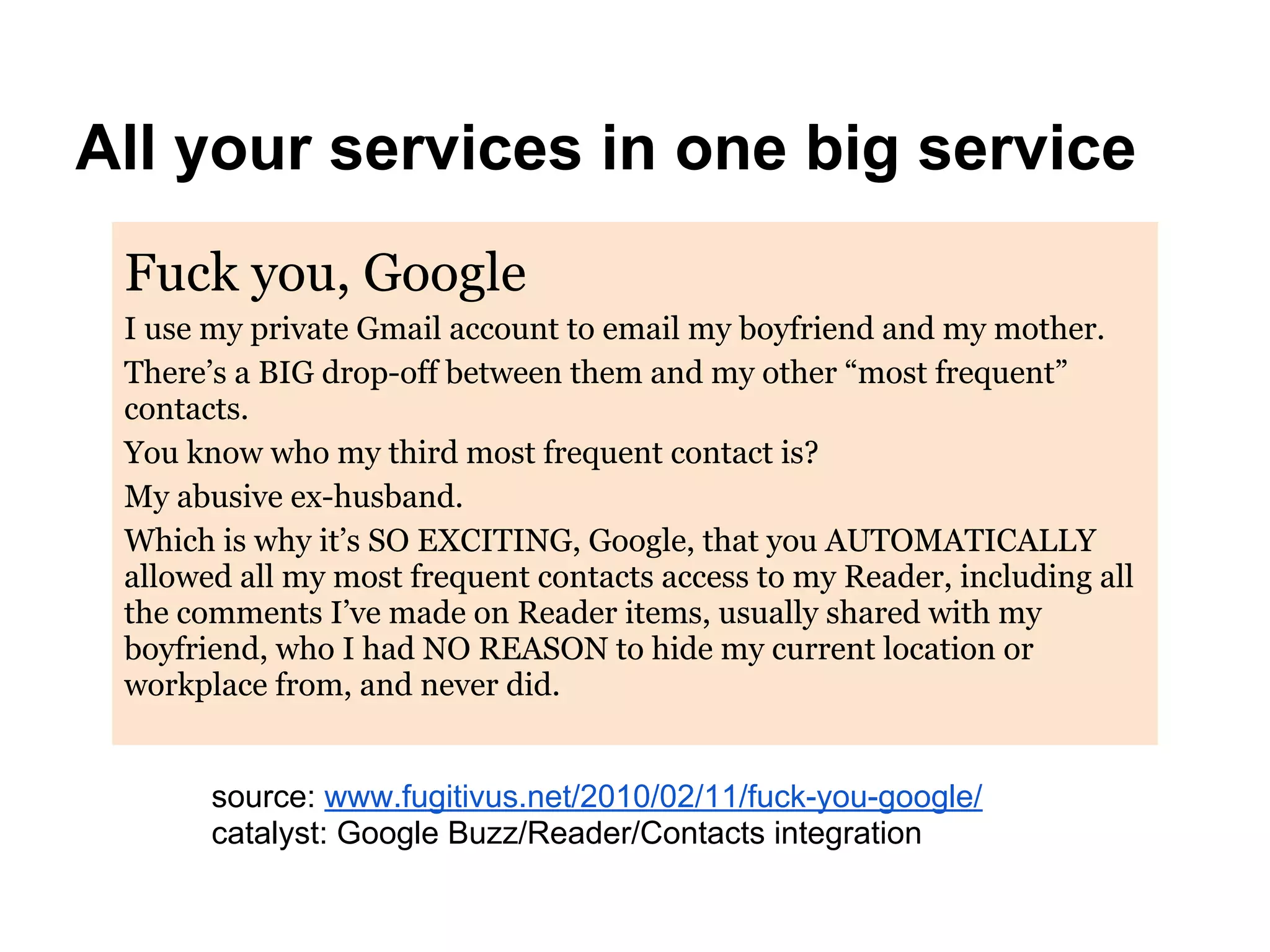
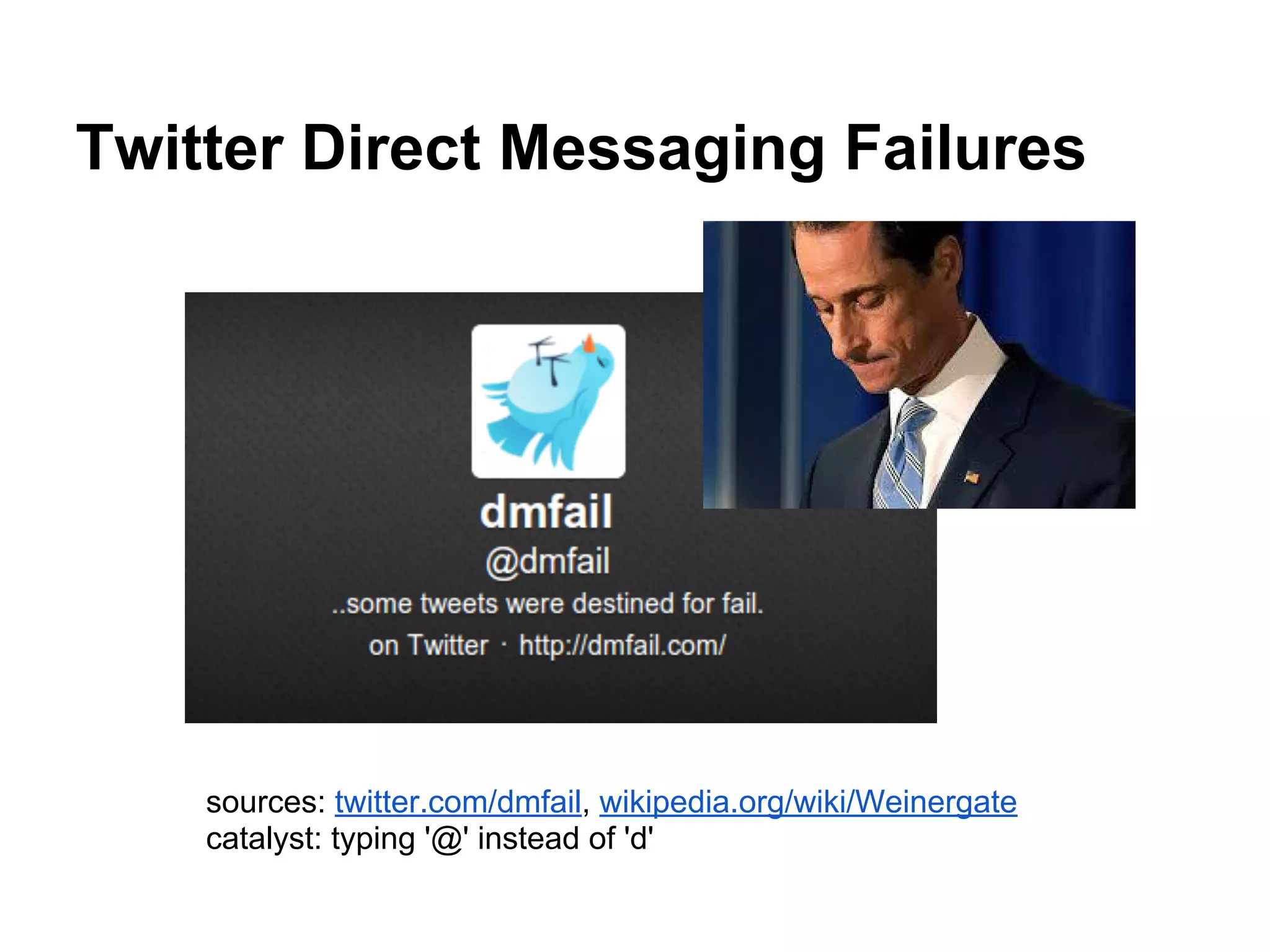
This document discusses contextual identity and the need for multiple identities. It notes that many public figures like Josephine Baker and Snoop Dogg have used different identities for different contexts. However, some social media platforms require a single verified identity. The document also discusses examples of privacy issues that can occur when all of one's online activities and contacts are connected, such as when an abusive ex is revealed. It calls for better tools and models to support contextual identity and privacy across different online contexts and services.







![What's in our privacy toolbox?
● Cryptography [RSA, AES, Diffie-Hellman]
● Contextual integrity [Barth et al.]
● Access control [Bell, LaPadula]
● Anonymizers [Dingledine, Marlinspike]
● Blockers [AdBlockPlus, Disconnect.me]
Our tools are necessary but not sufficient.](https://image.slidesharecdn.com/contextualidentity-w2sp-130716113944-phpapp02/75/Contextual-identity-w2sp-13-2048.jpg)
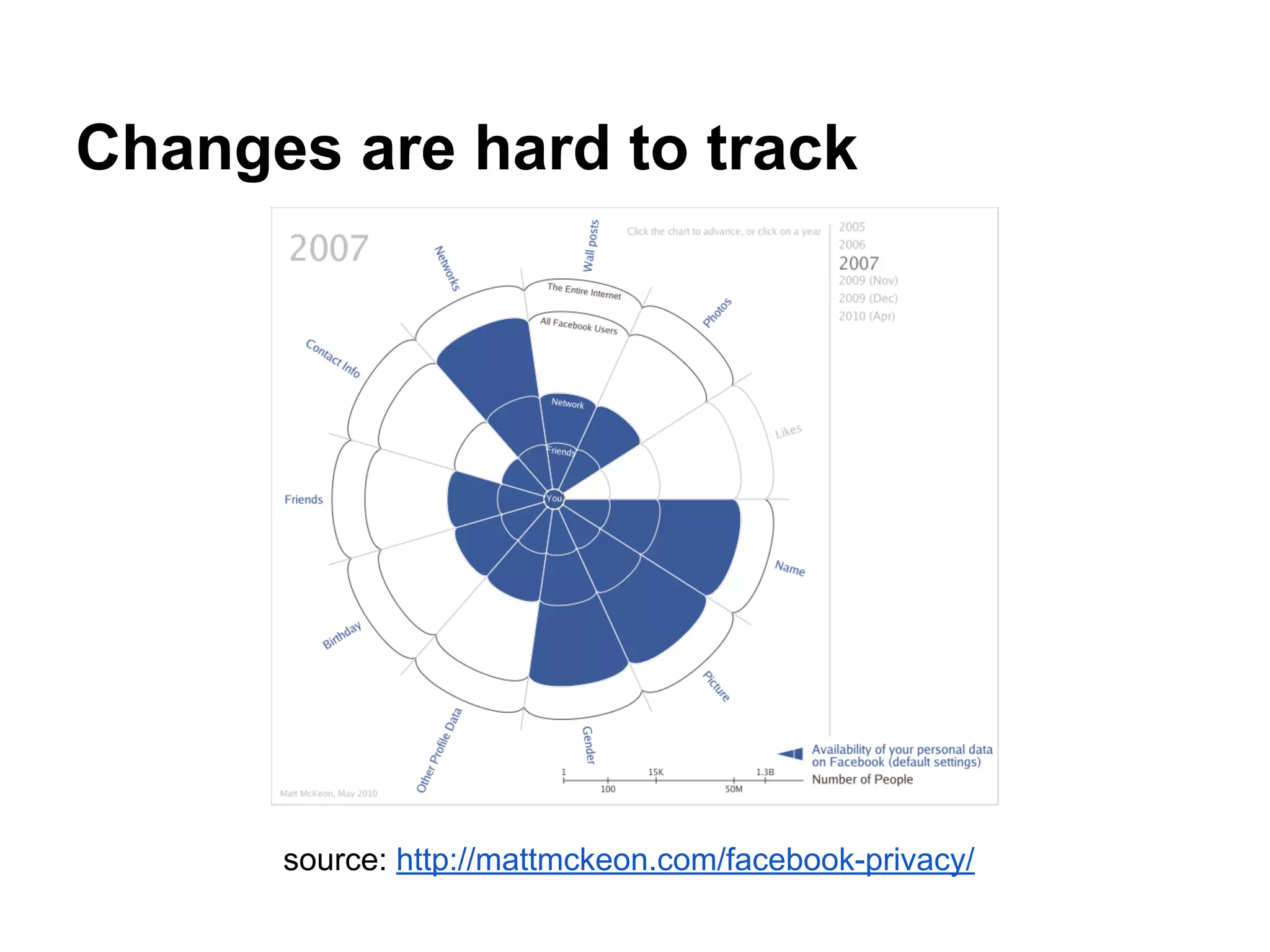
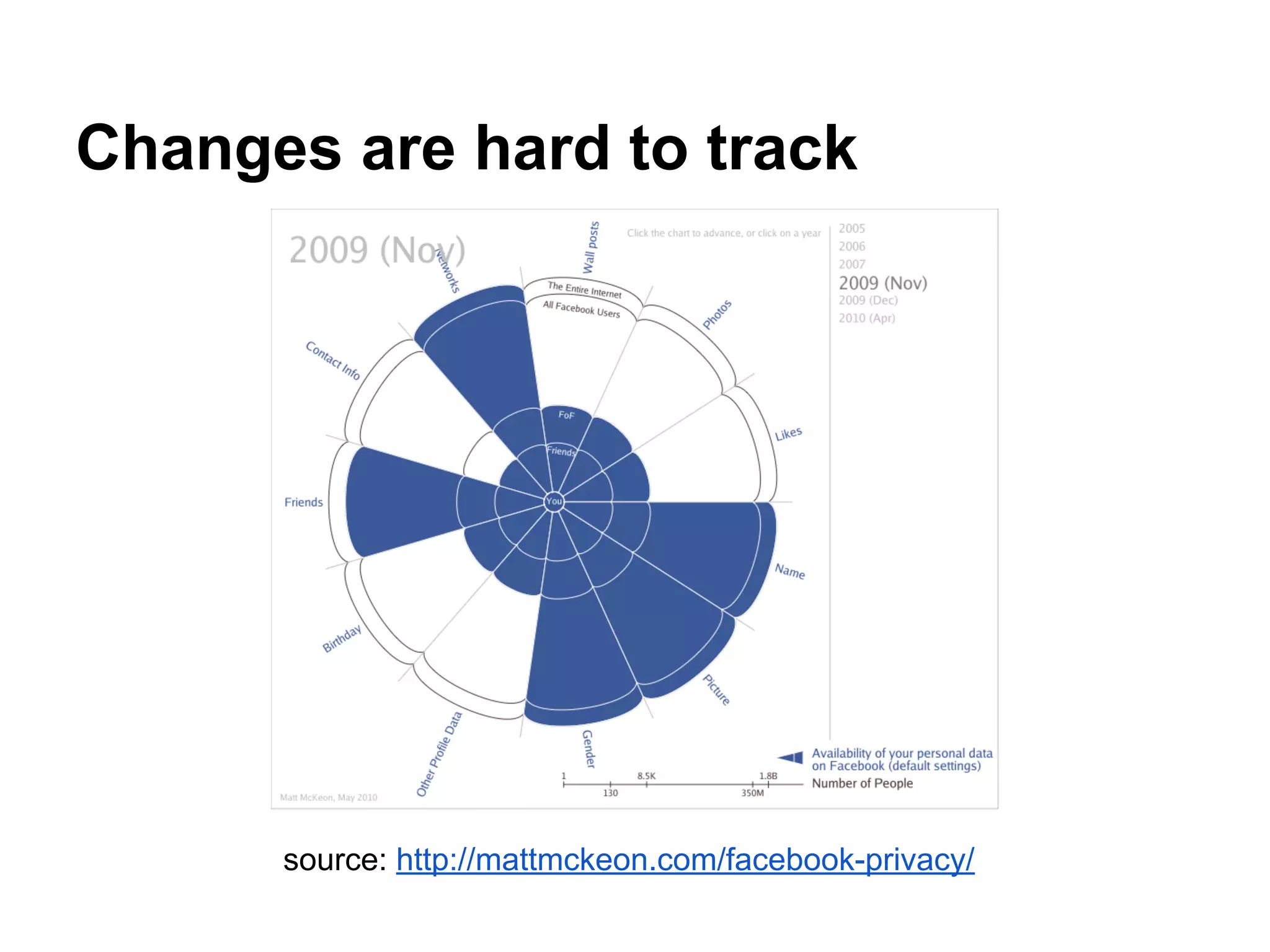
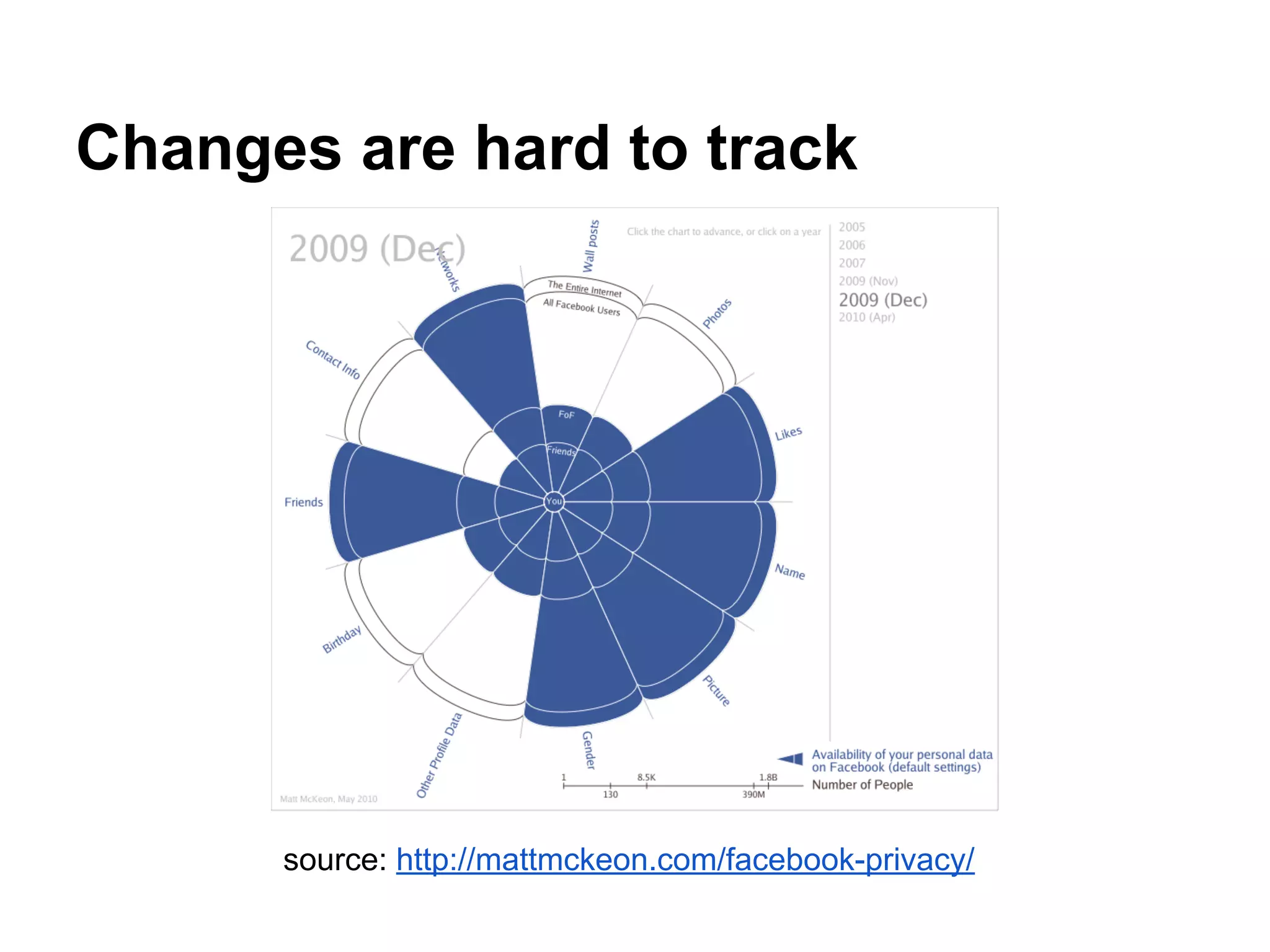
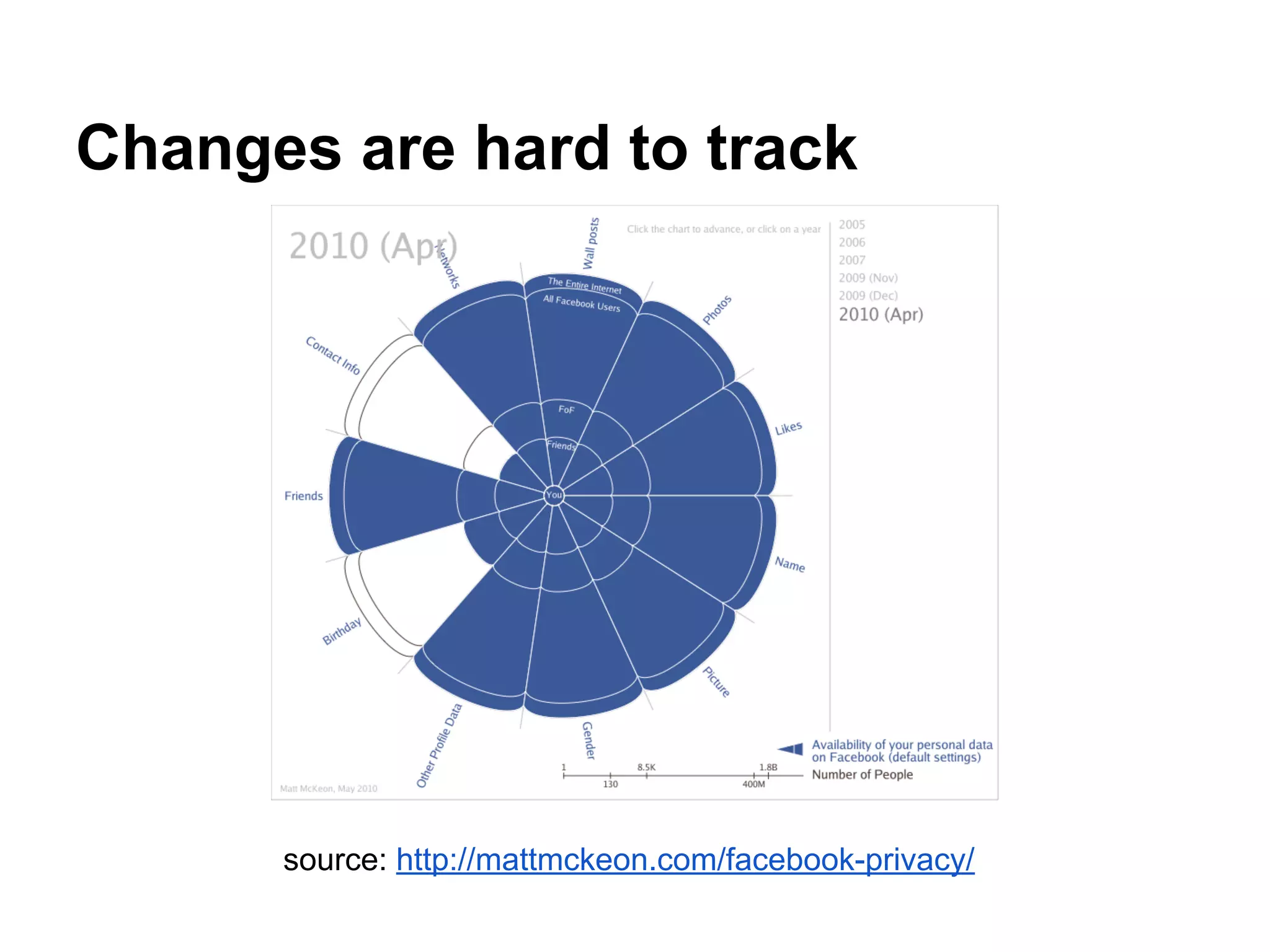













![Works in progress
● Blushproof [with David Keeler]
● Cookiemonster [with David Dahl]
● Behavioral segmentation [Mozilla UR]](https://image.slidesharecdn.com/contextualidentity-w2sp-130716113944-phpapp02/75/Contextual-identity-w2sp-37-2048.jpg)
