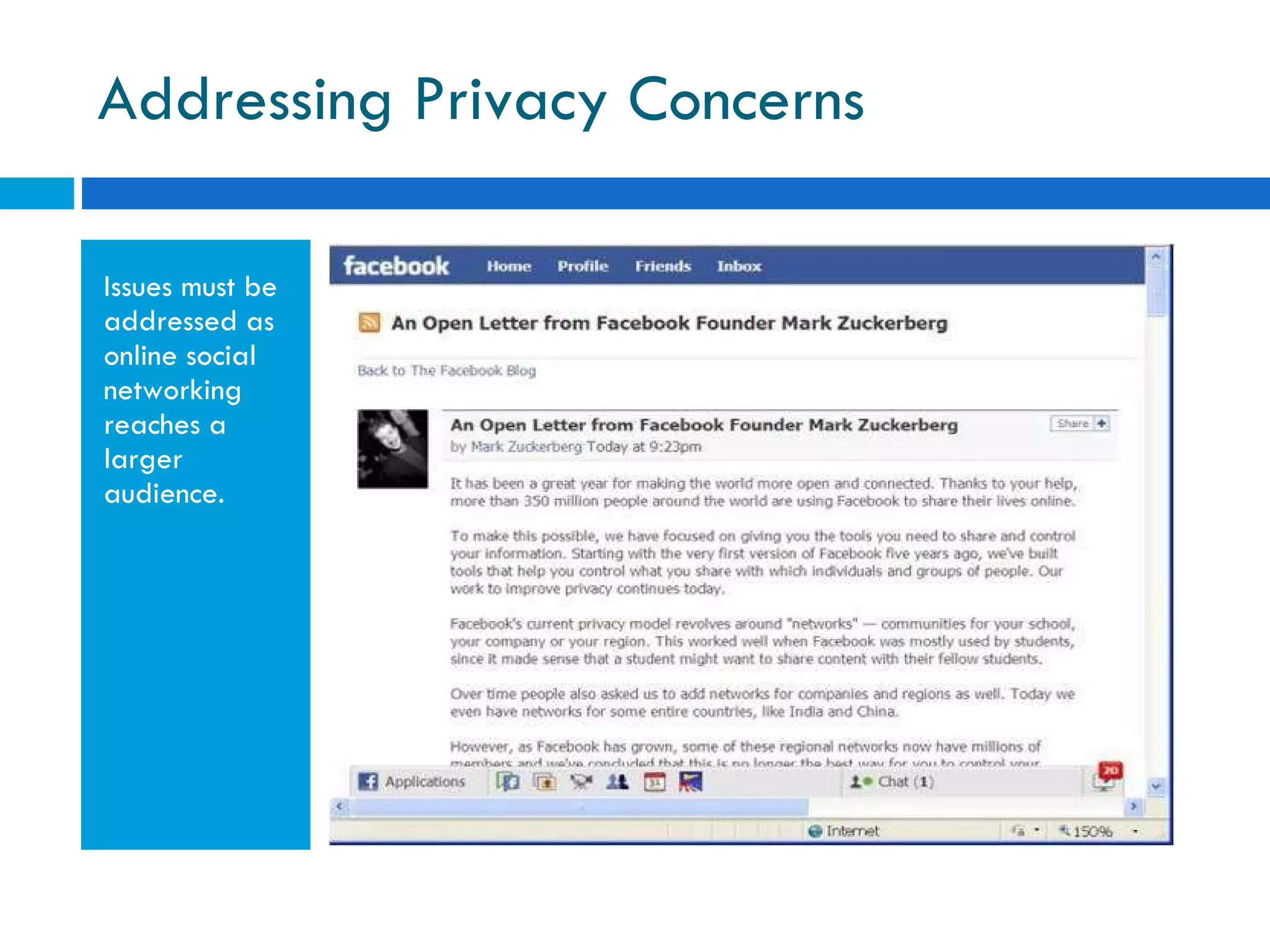
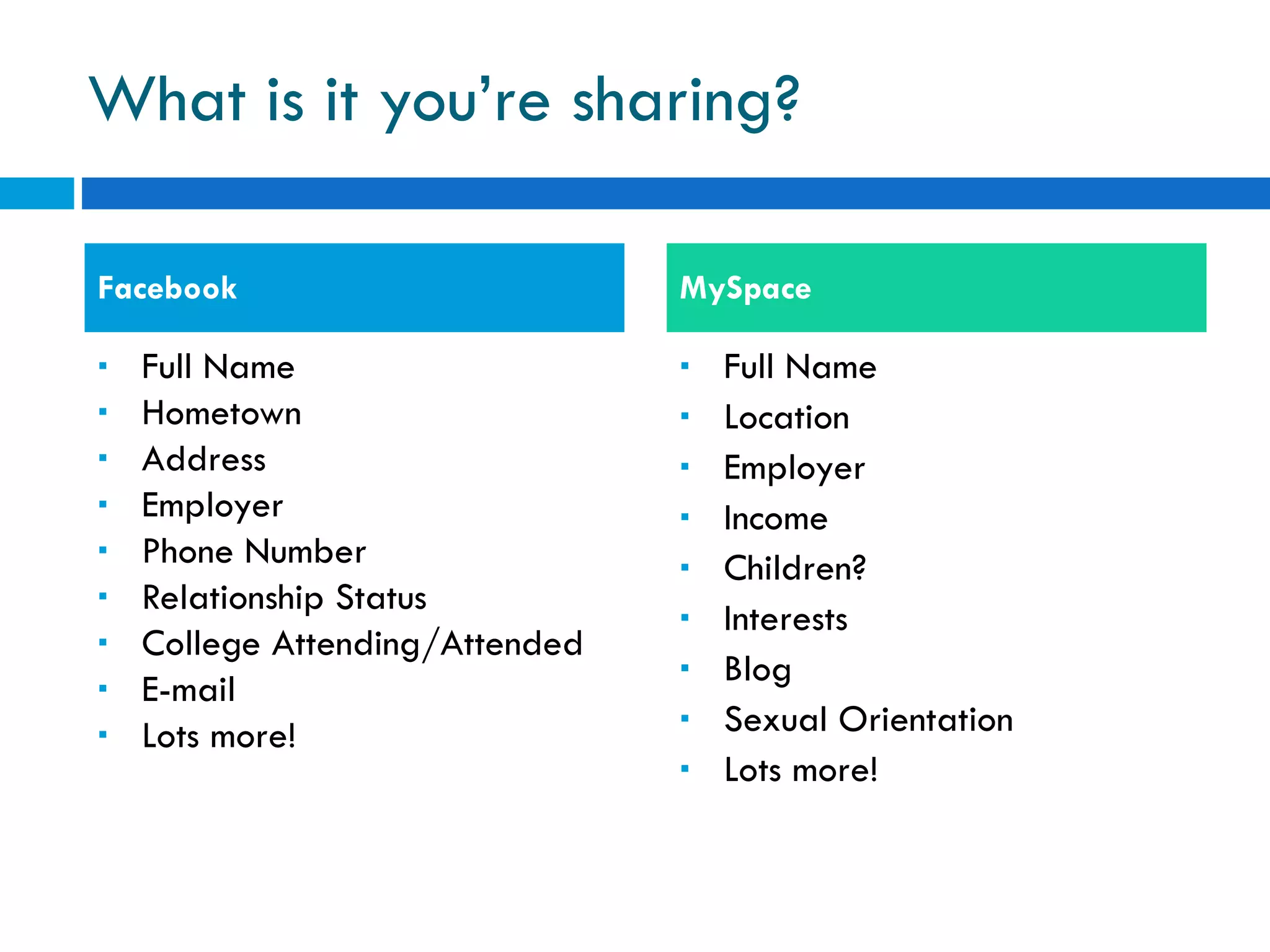
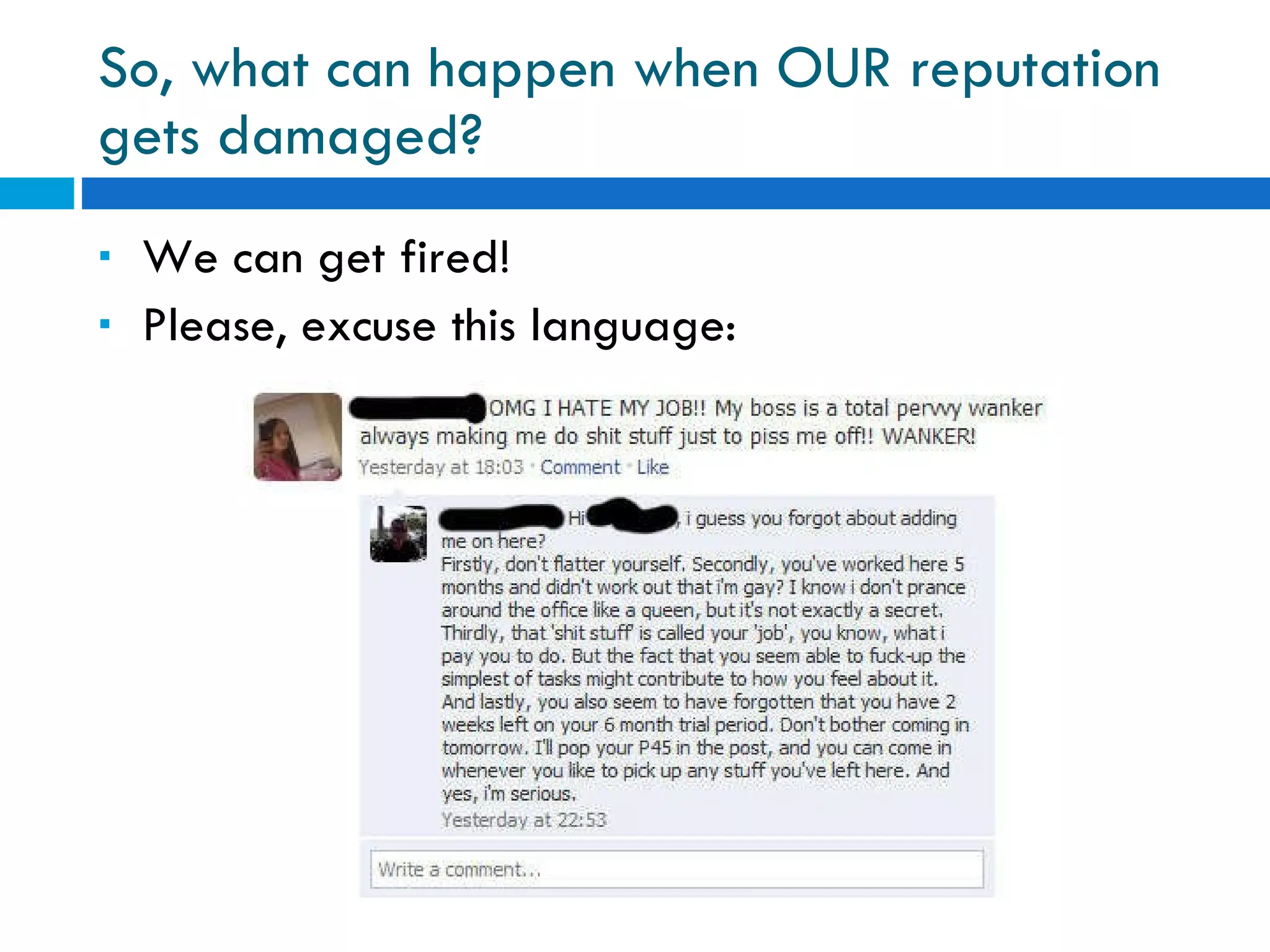
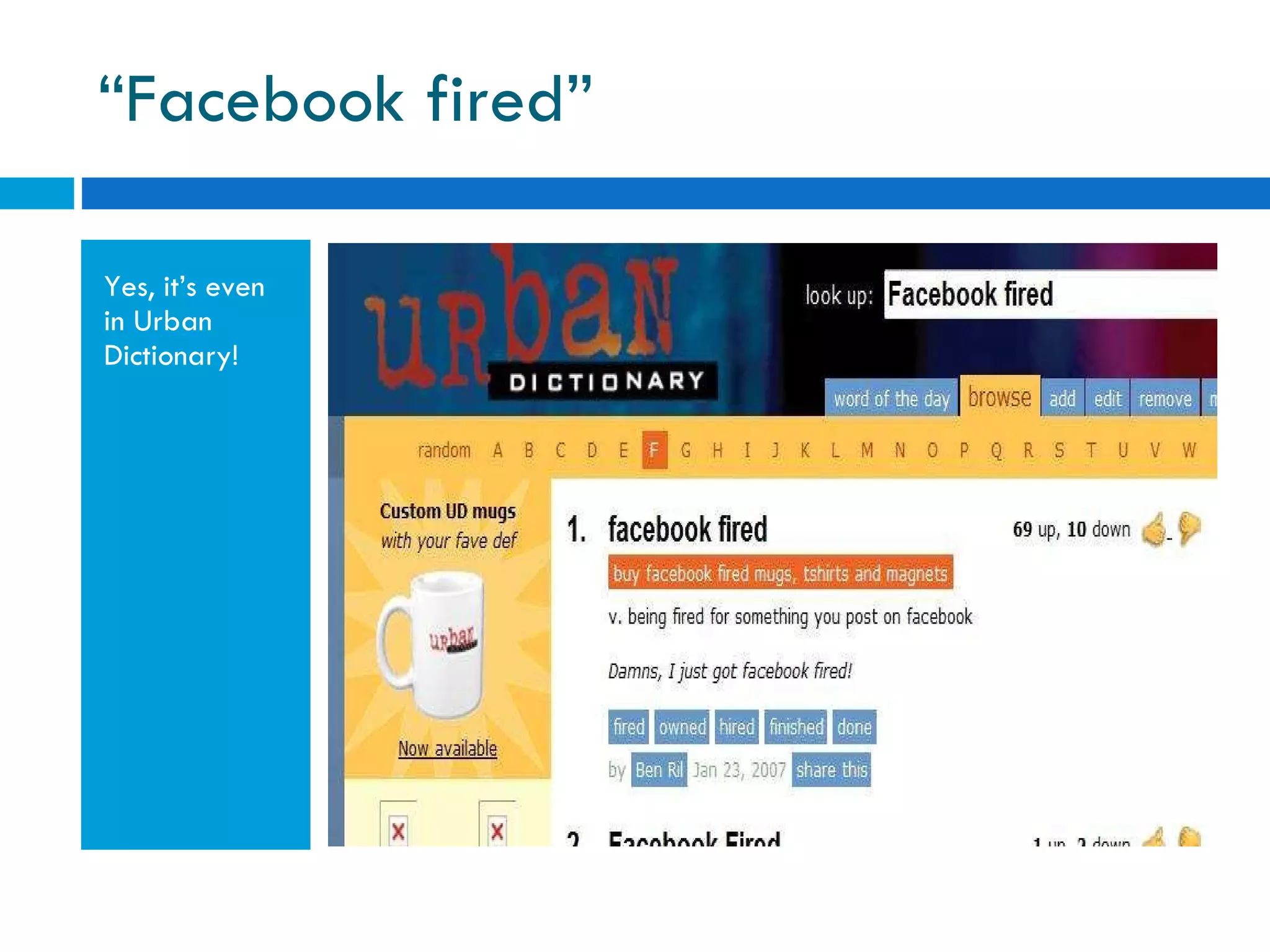
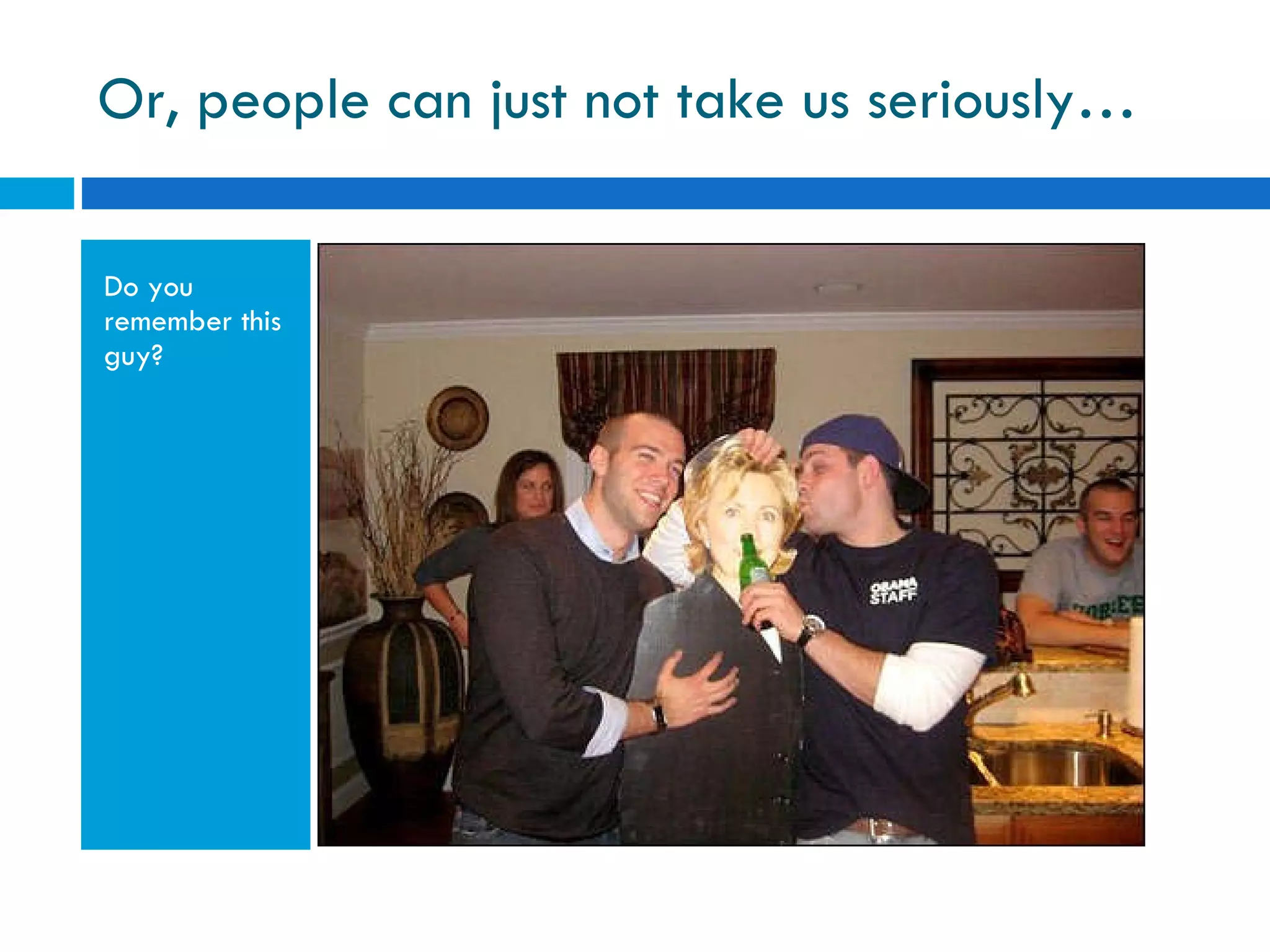
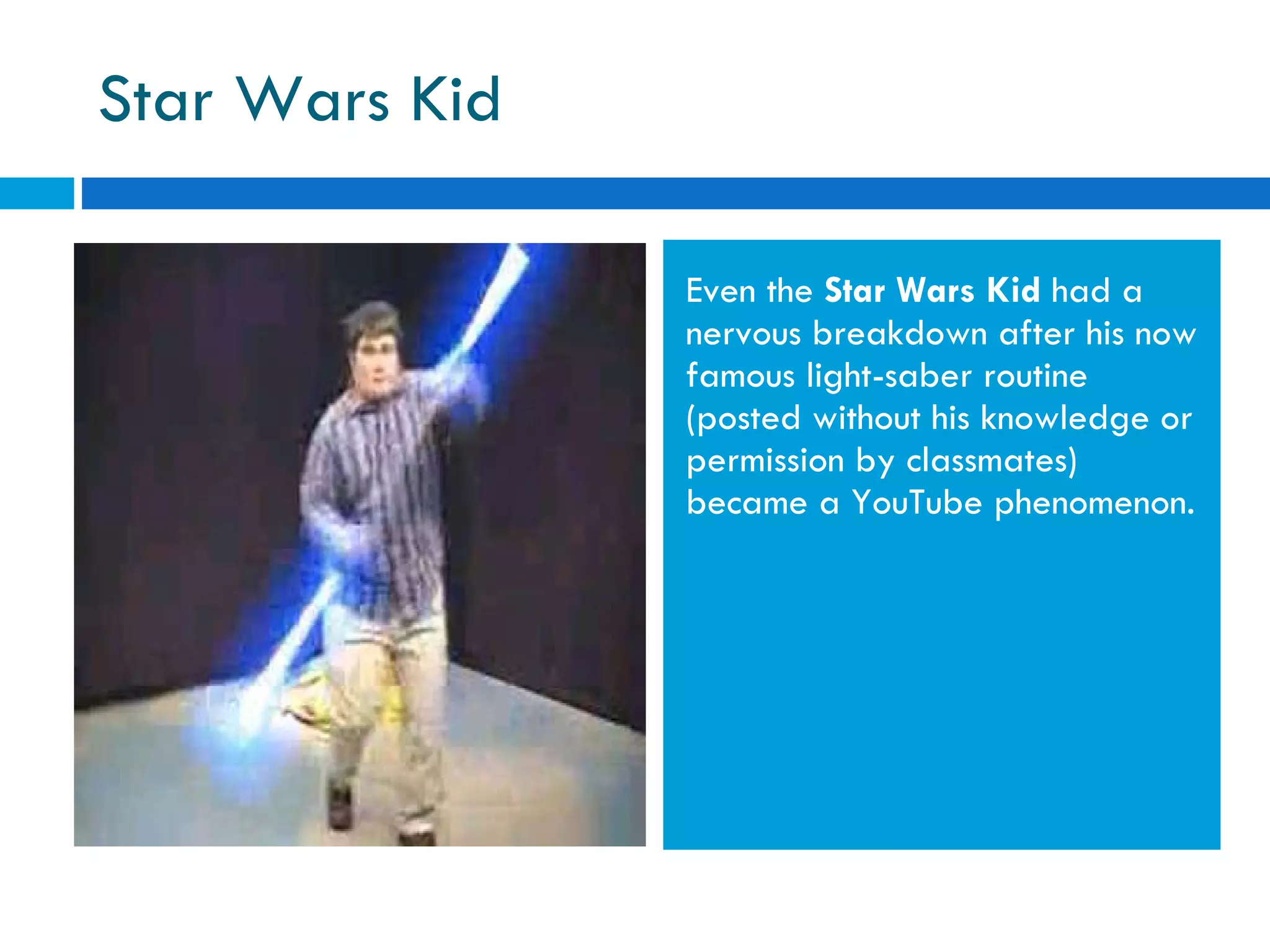
The document discusses the history of online social networking and privacy concerns. It outlines the evolution of technologies from early computer networks and email to modern social media sites. It then examines perceptions of privacy and the risks of oversharing personal information online. Tools for teaching privacy and managing online profiles are presented. Users are encouraged to be aware of what they post and who may have access to their information to avoid potential issues like identity theft, embarrassment, or legal problems.