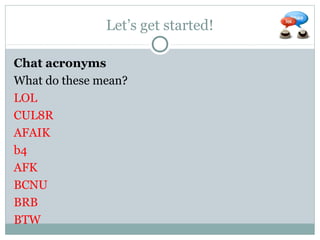
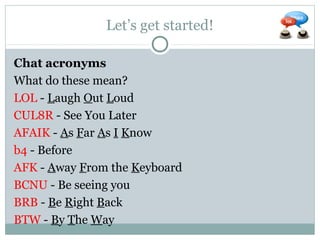
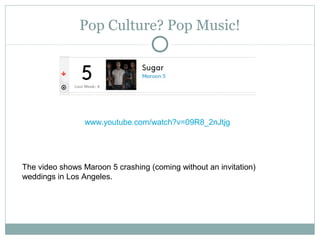
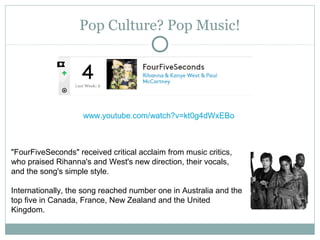
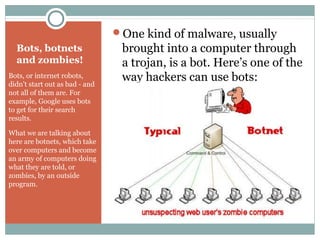
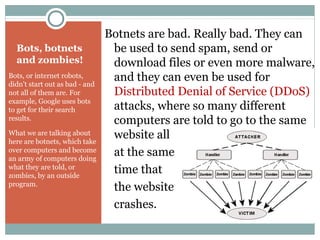
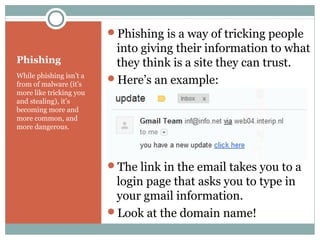
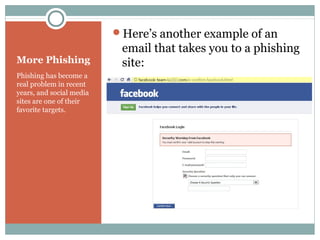
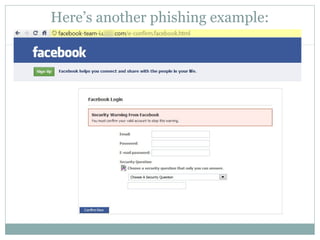
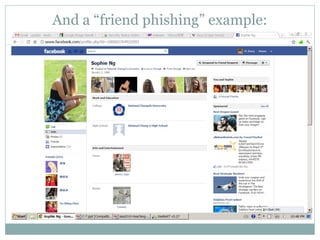
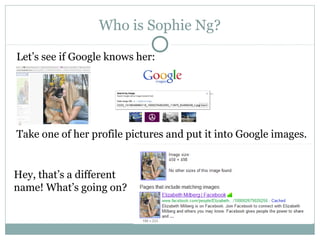
The document outlines a course on multimedia English. Students will study pop culture, media messaging, using the internet for information, and online software/social networks. Grades are based on quizzes, exams, presentations, assignments, and participation. The class website is media.jadekite.com and students must register. Some topics covered are information literacy, advertising techniques, memes, social media, music genres, and slang. The document then provides examples of chat acronyms and discusses a popular pop song and artist.