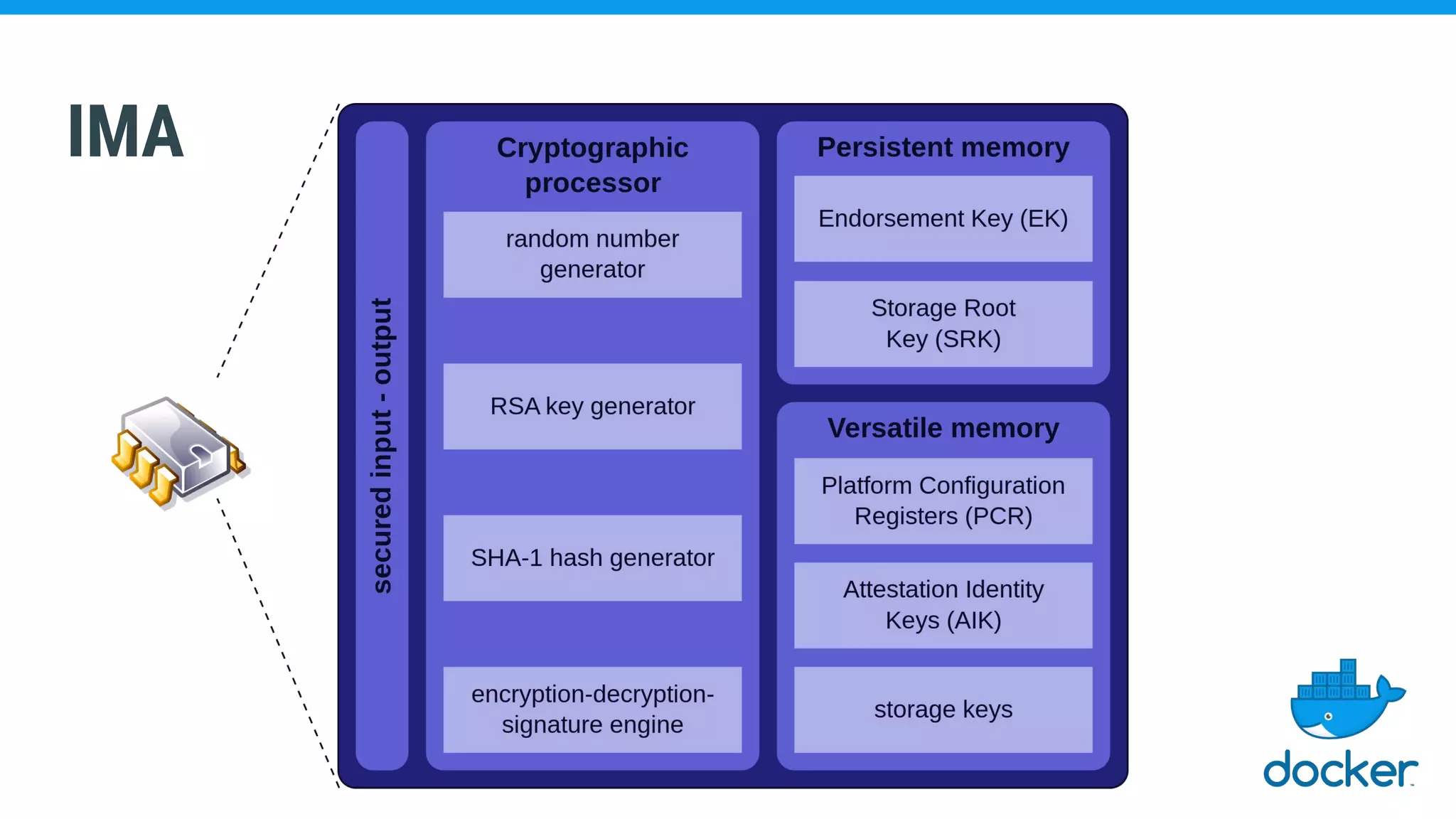
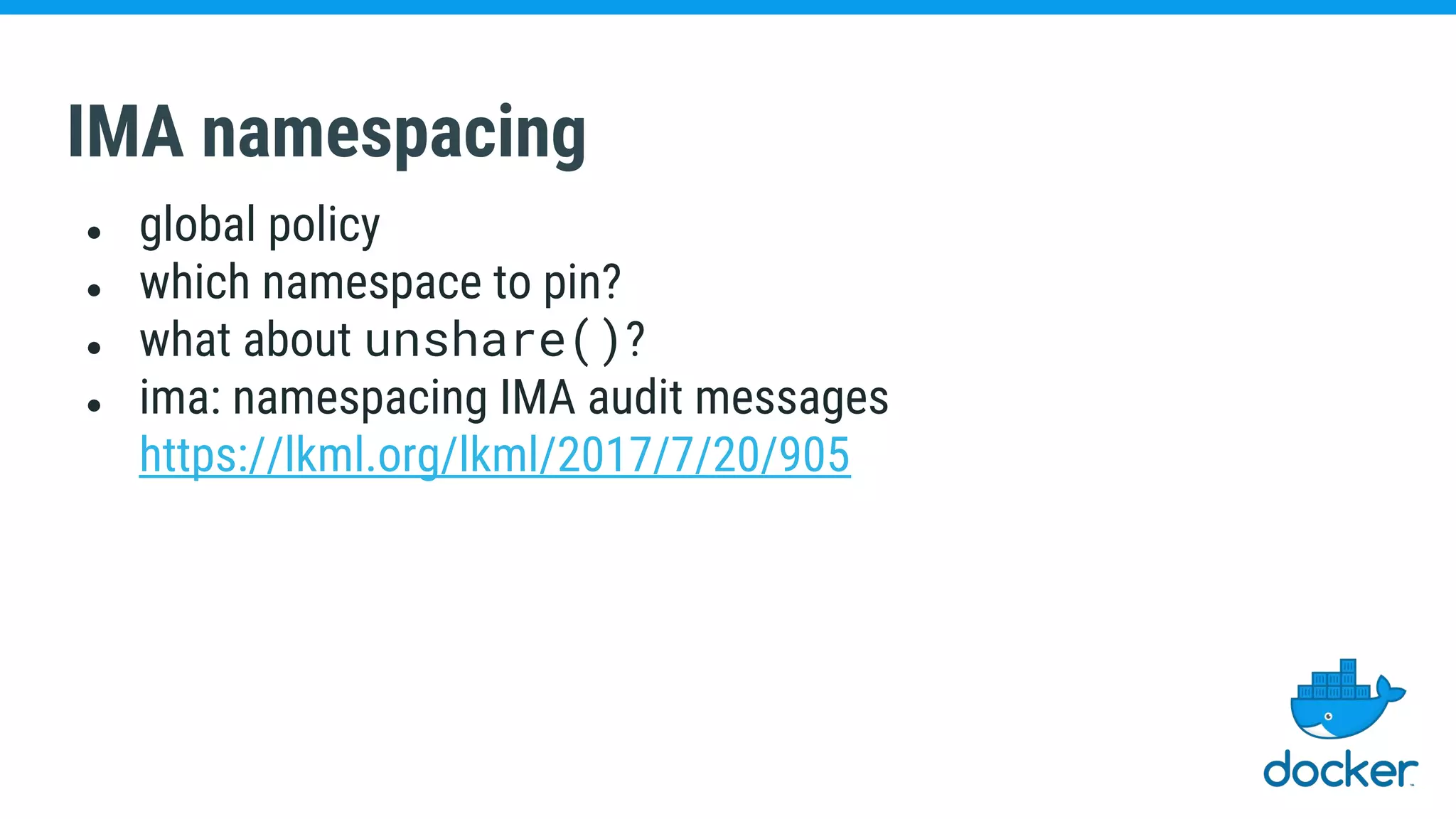
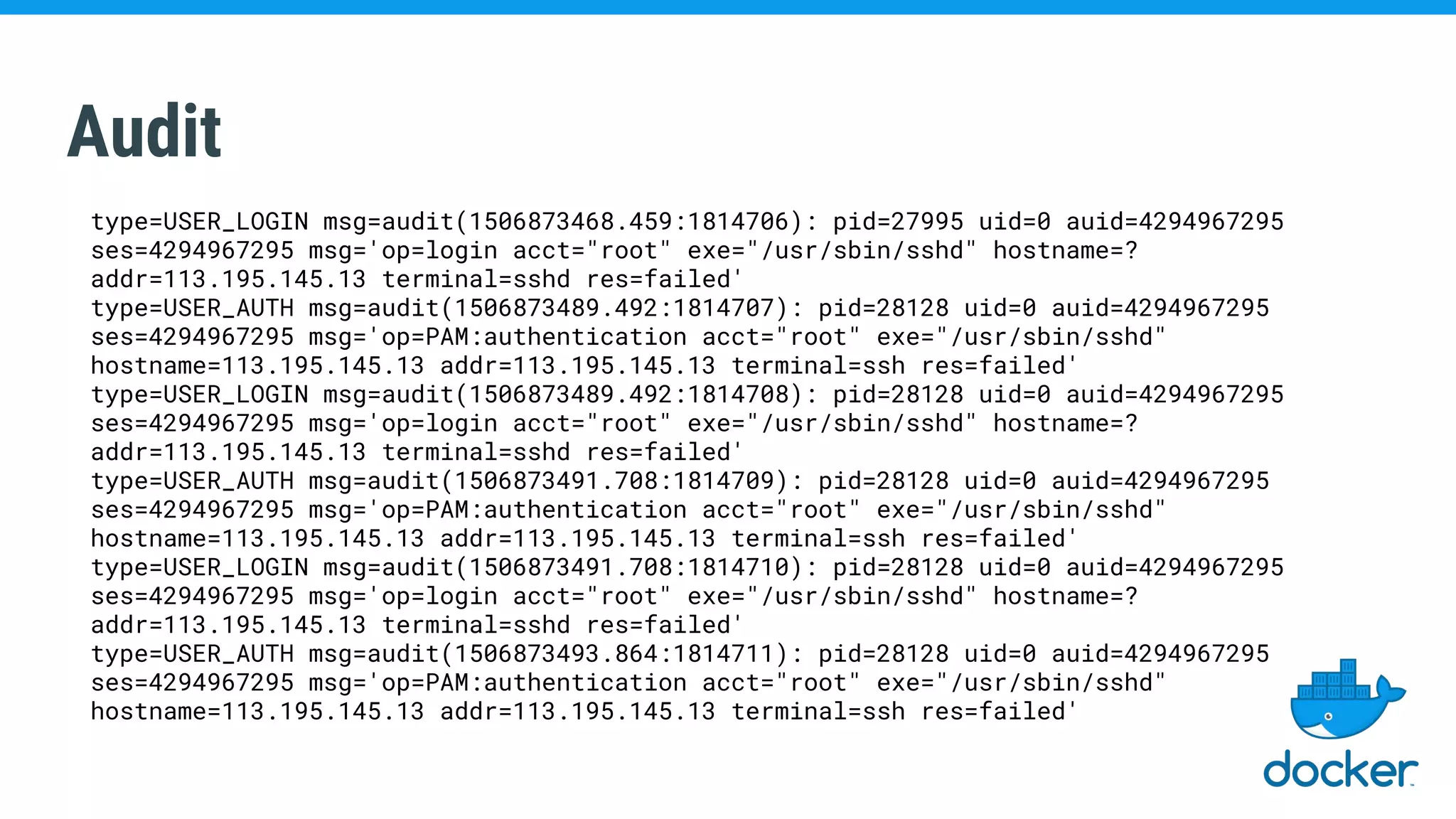
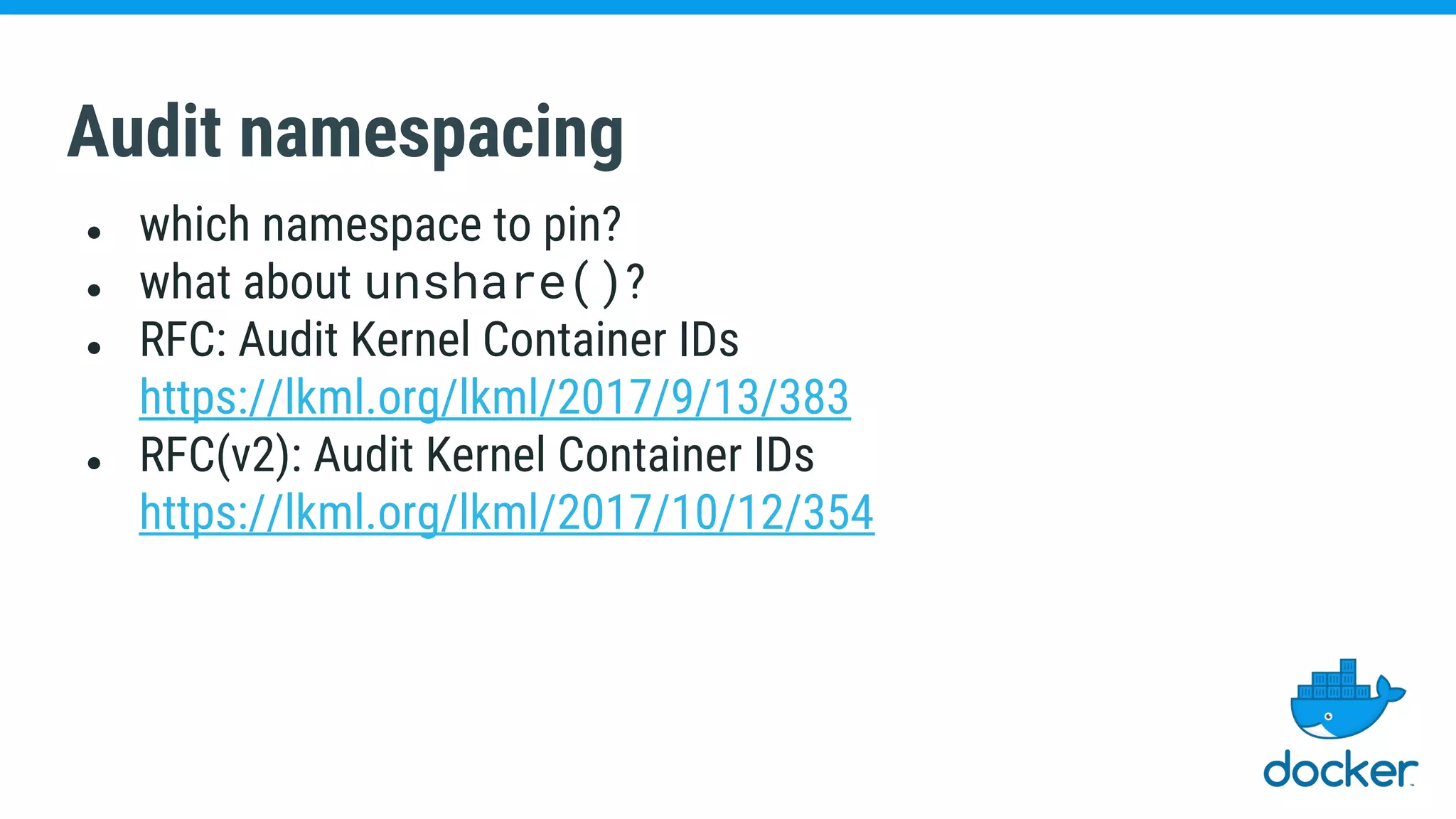
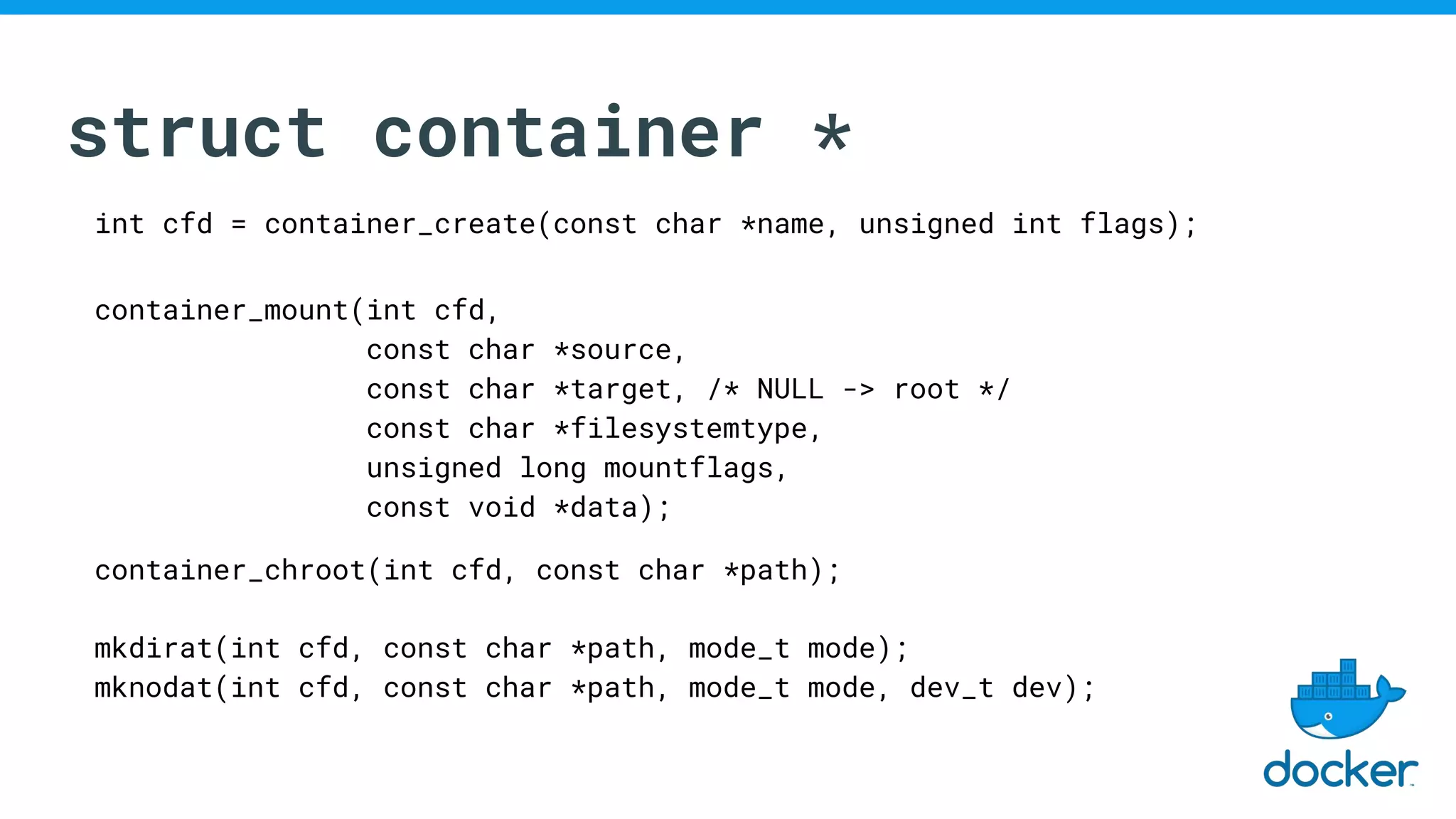
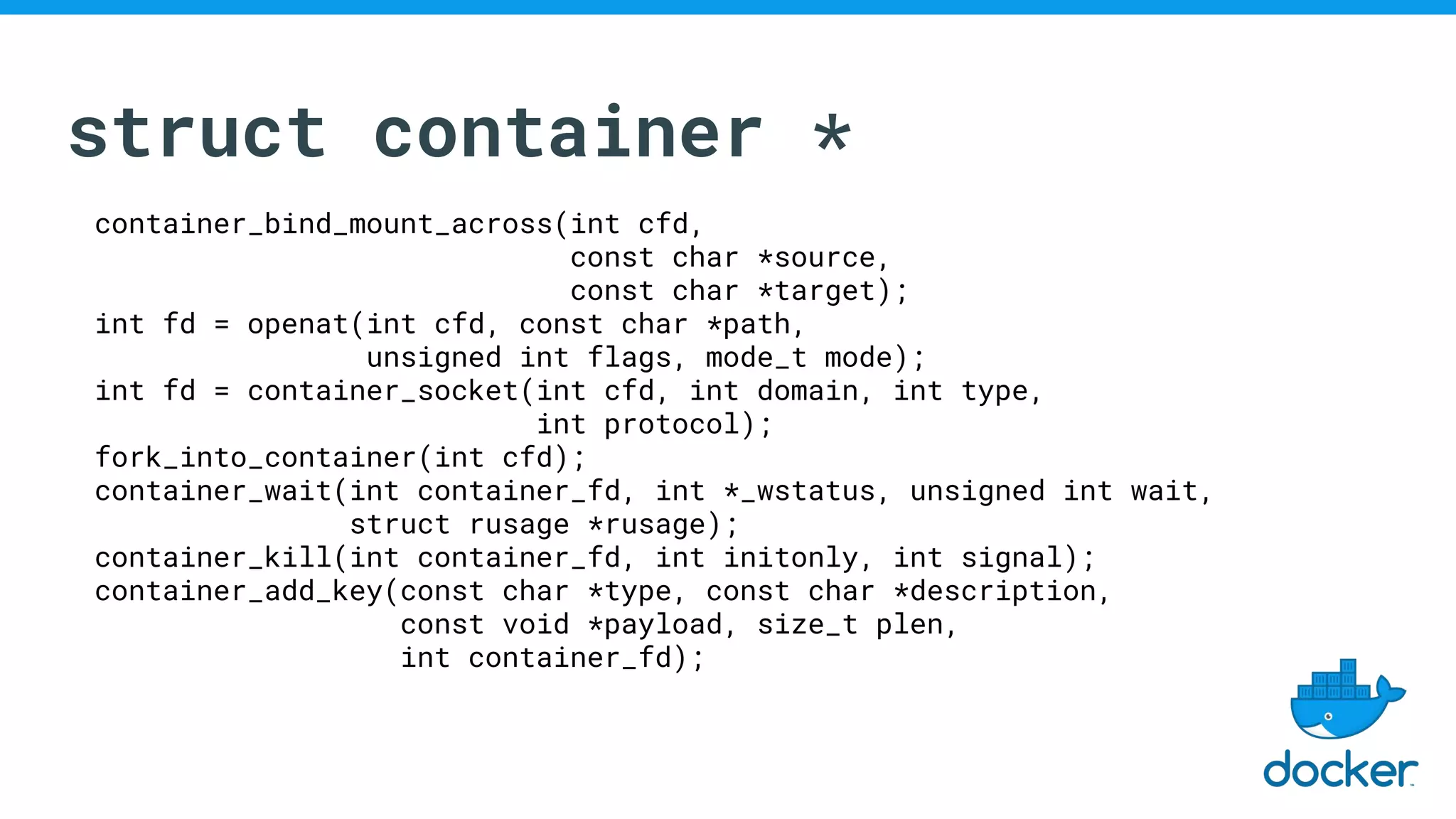
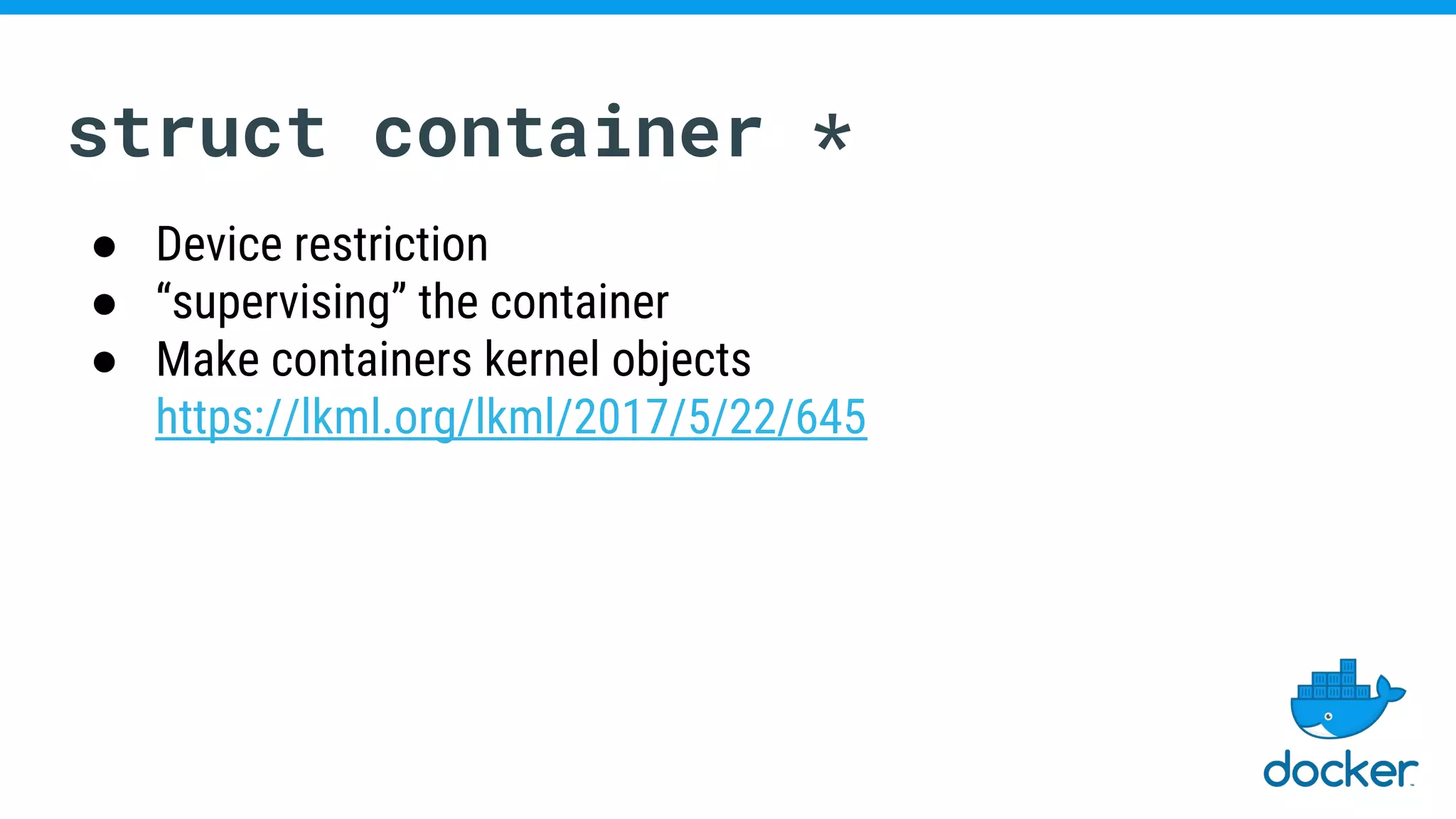
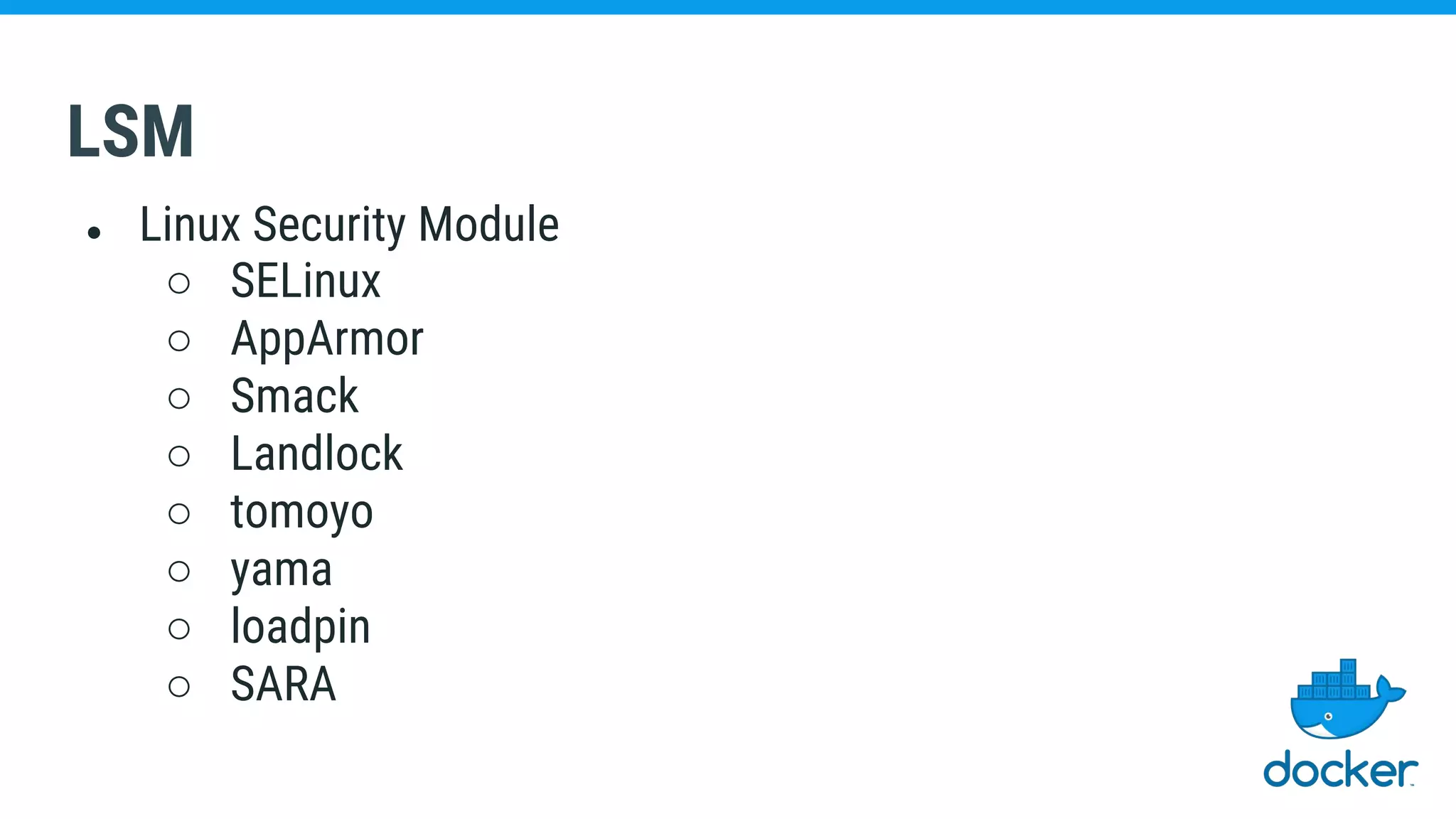
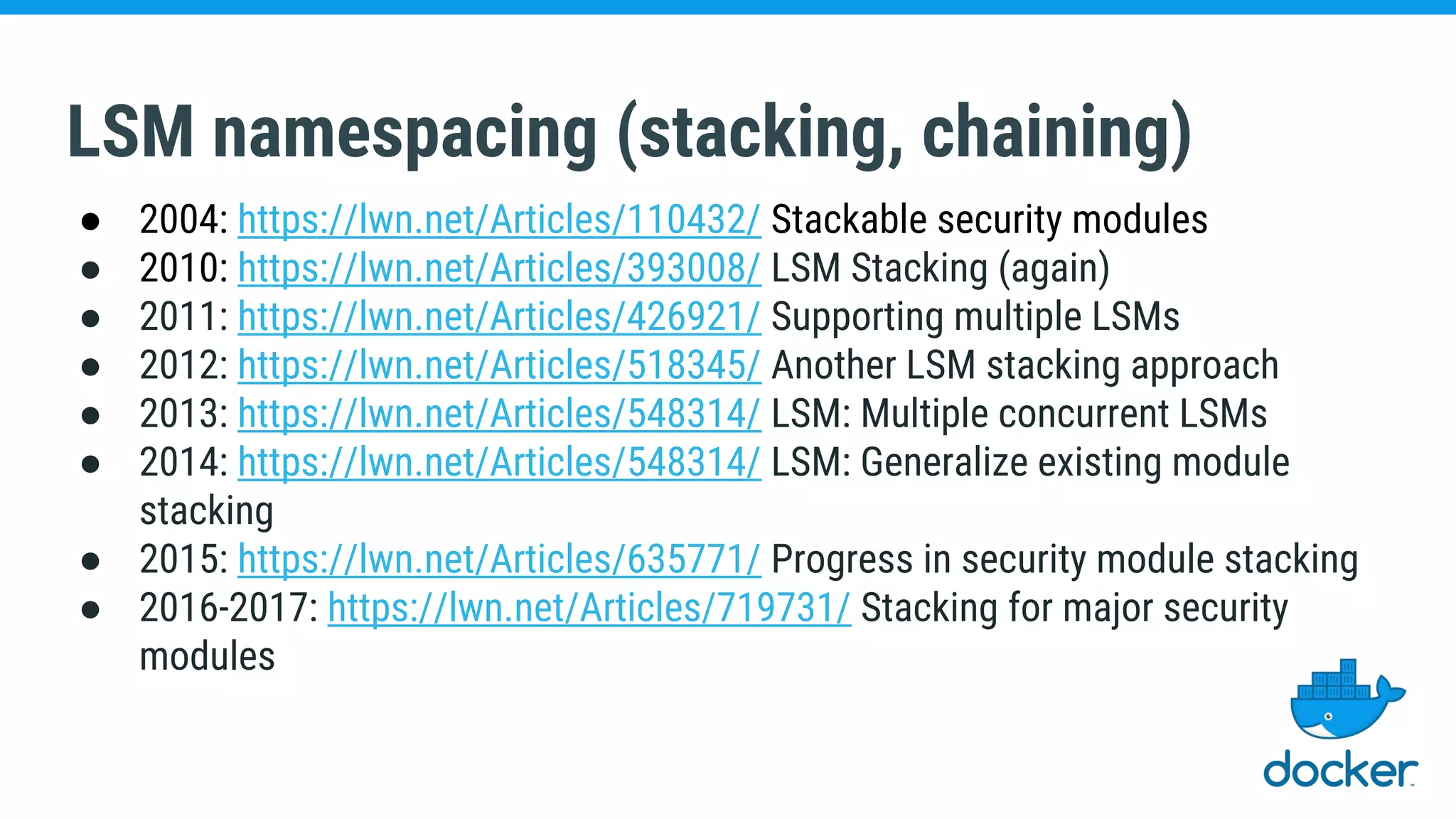
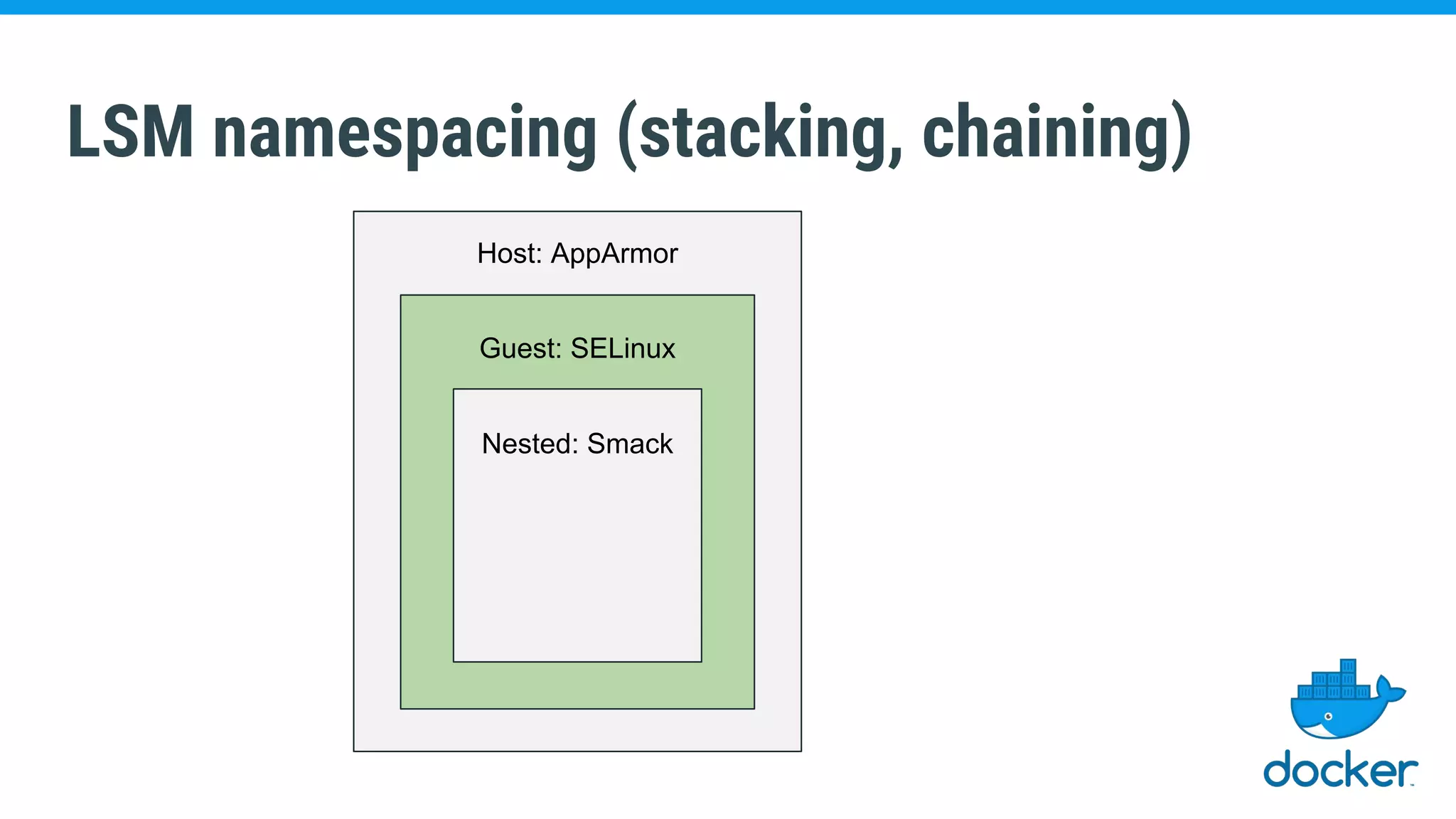
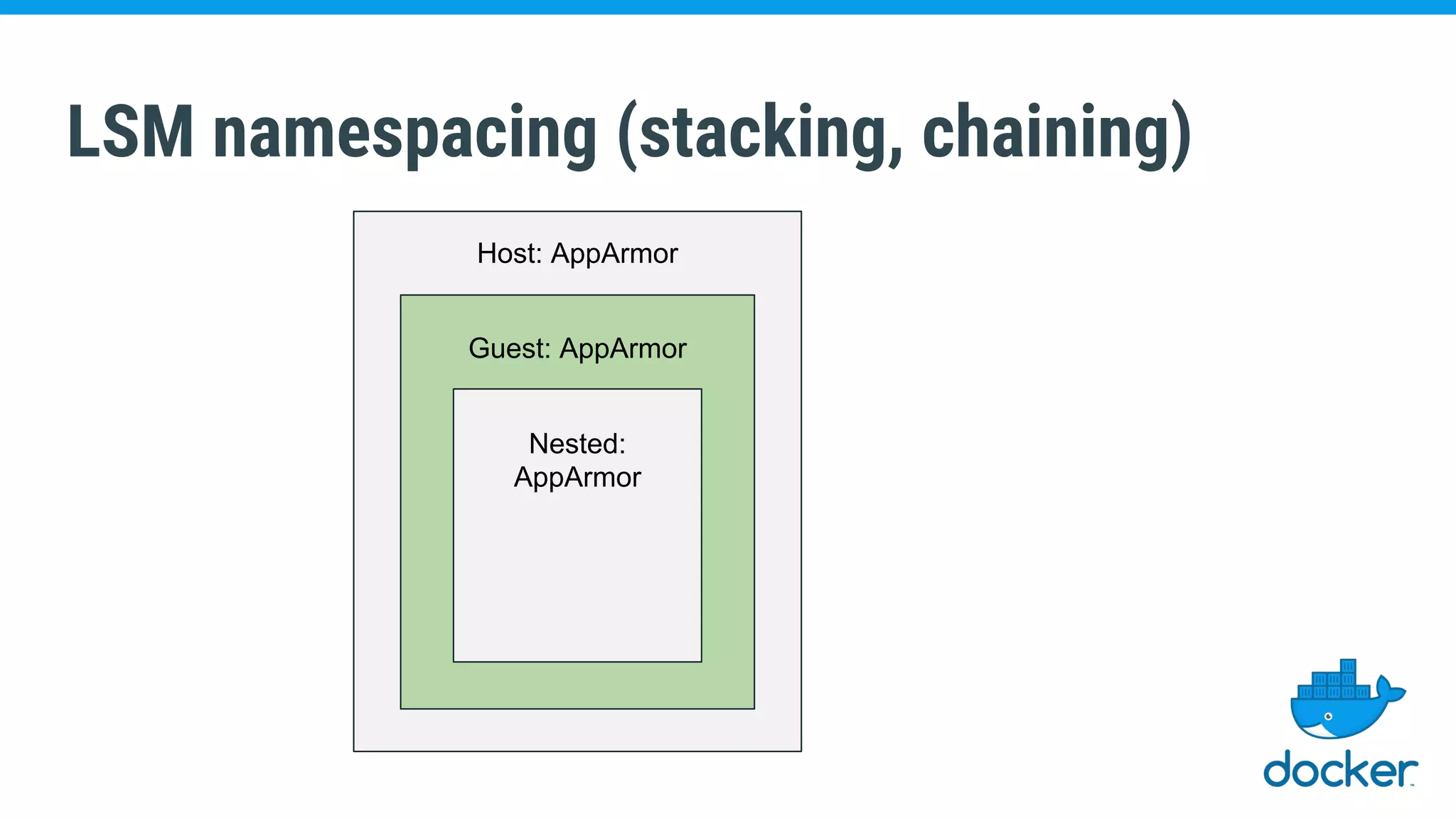
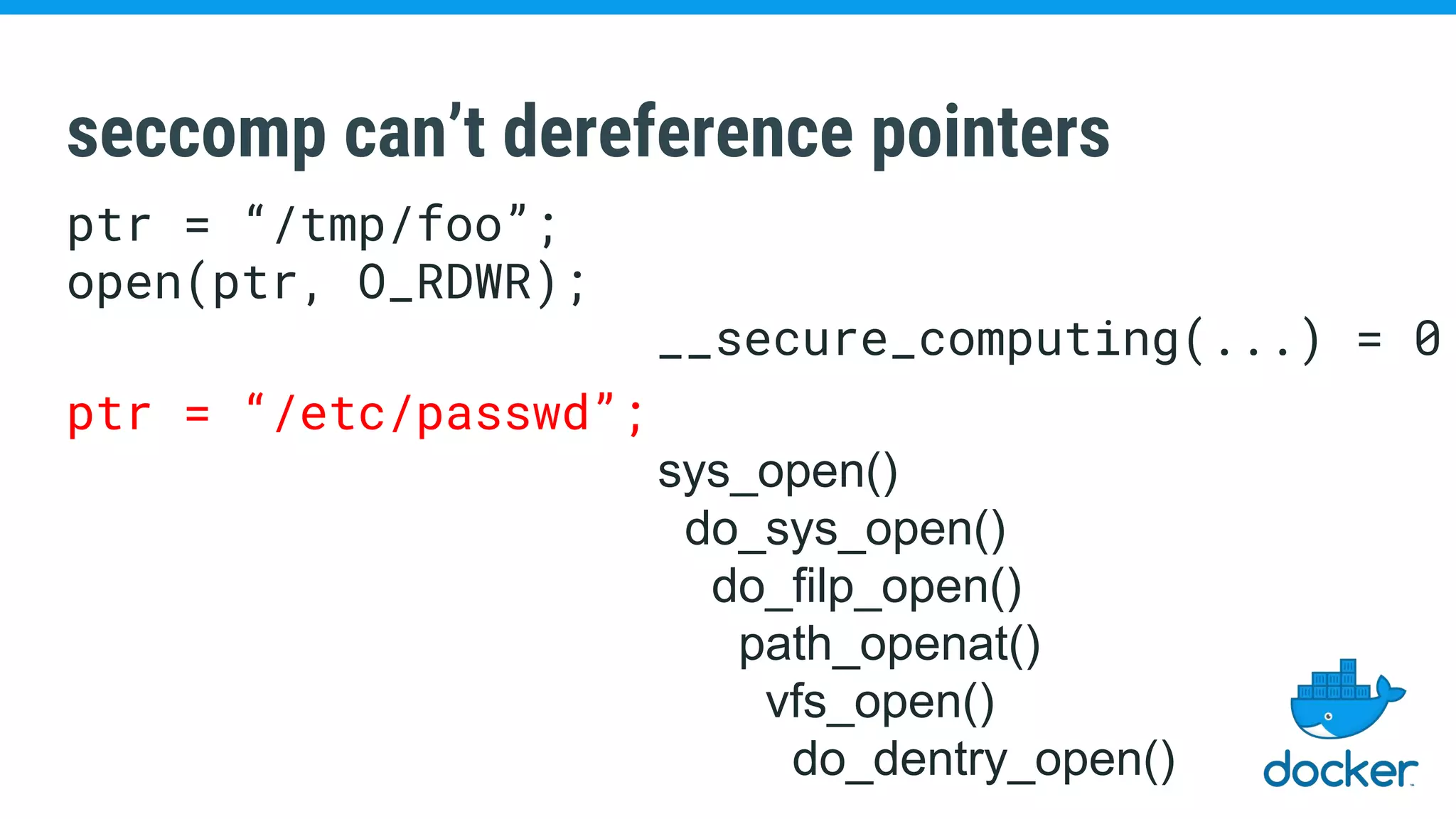
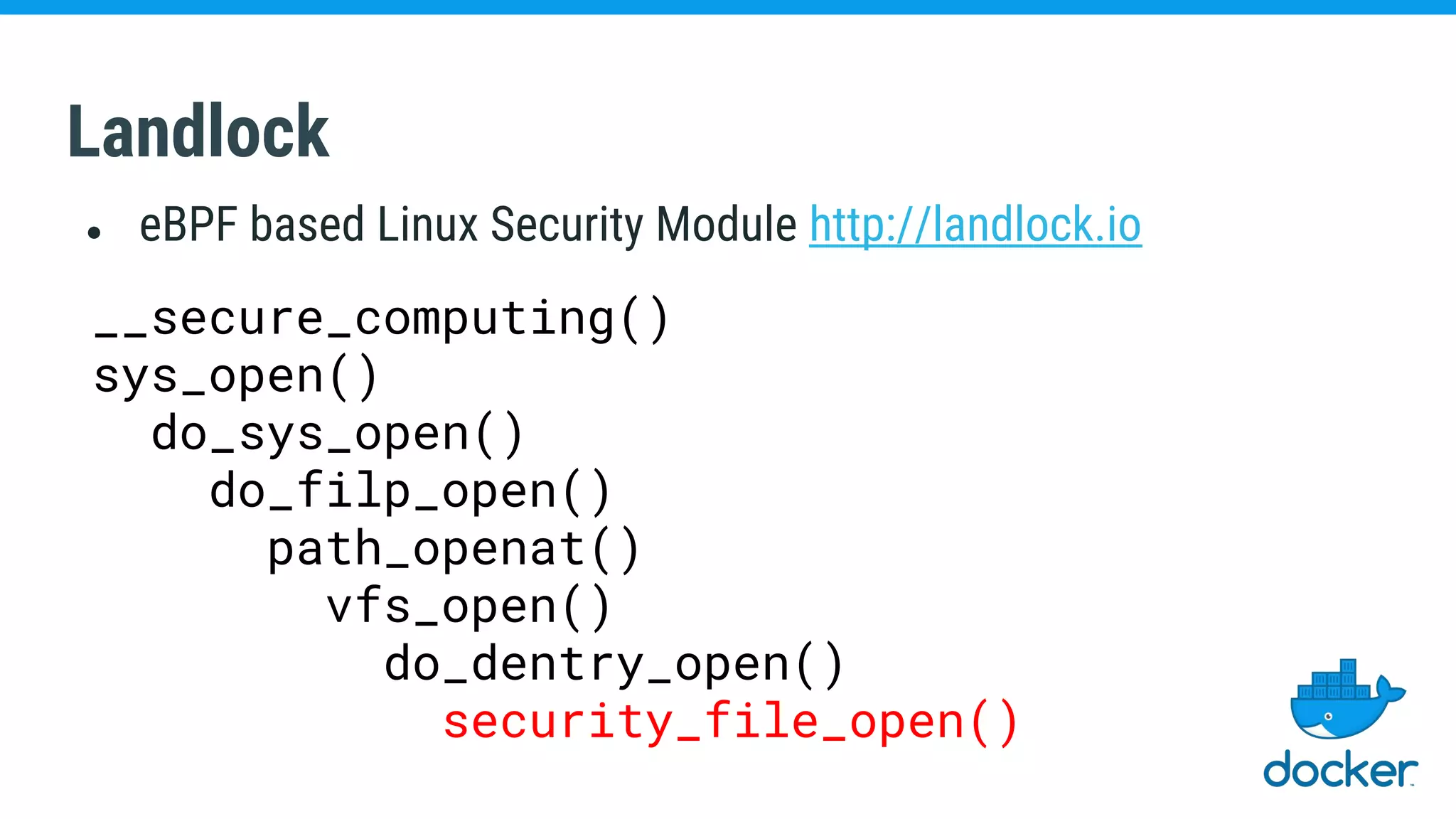
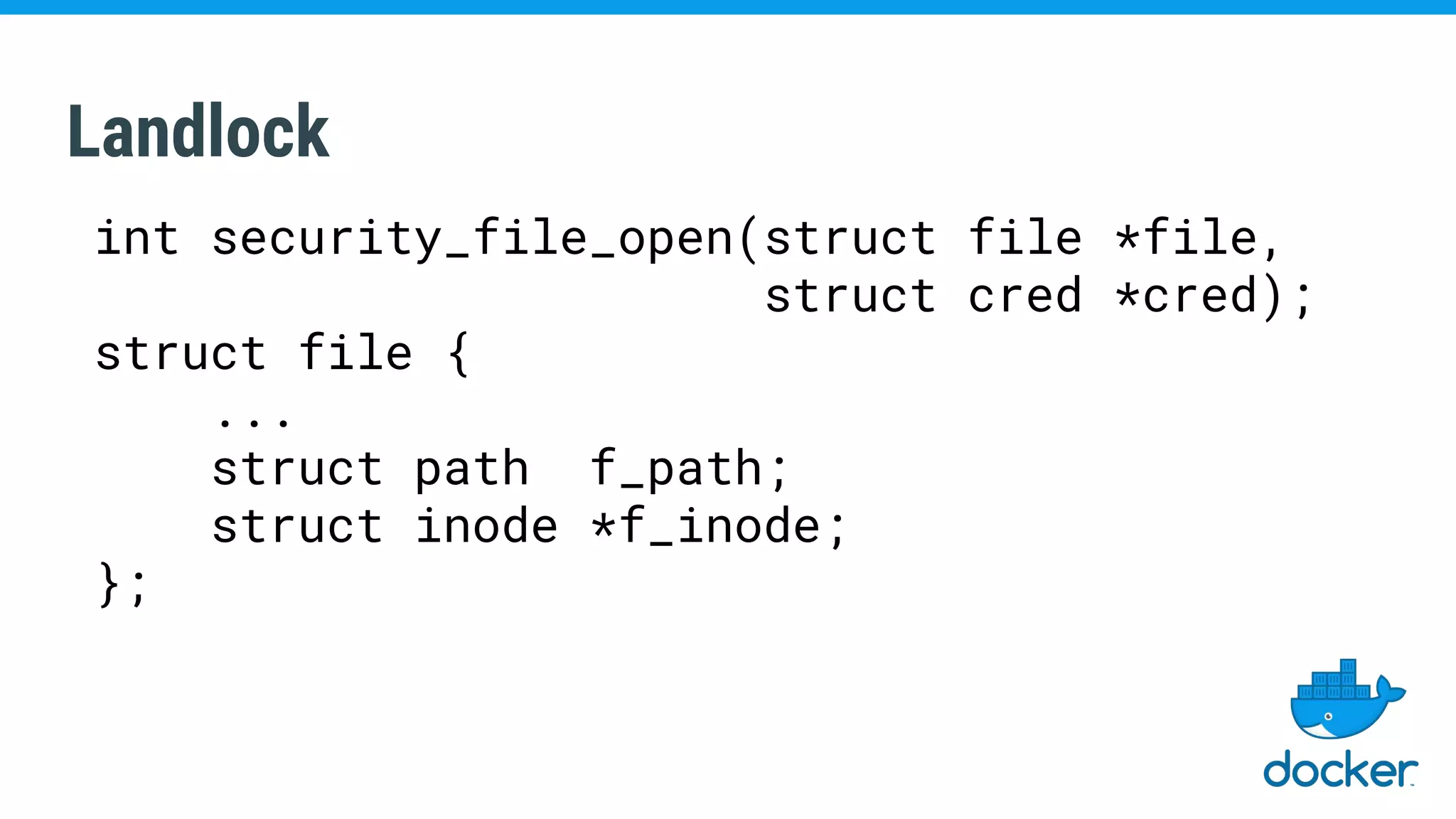
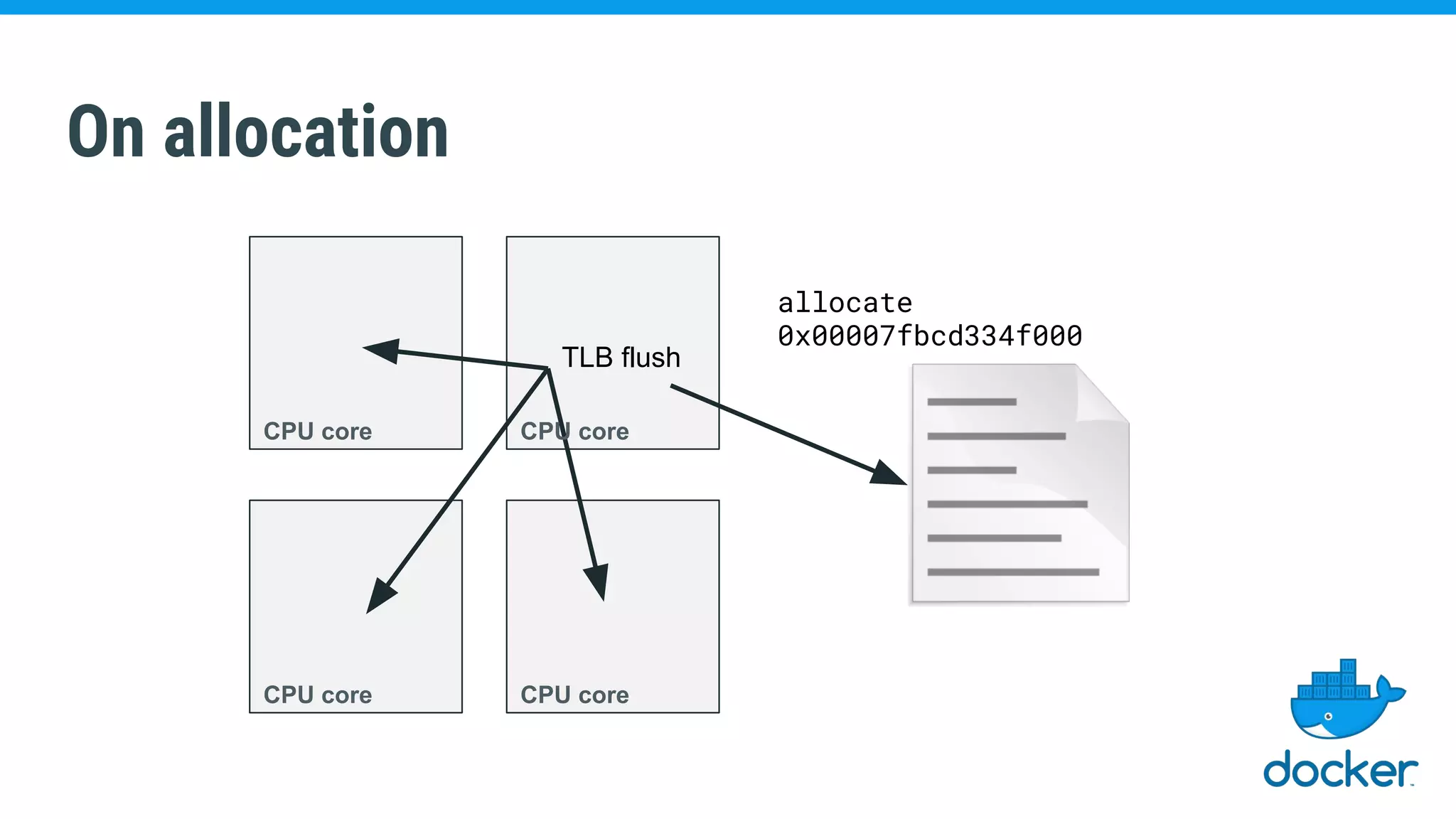
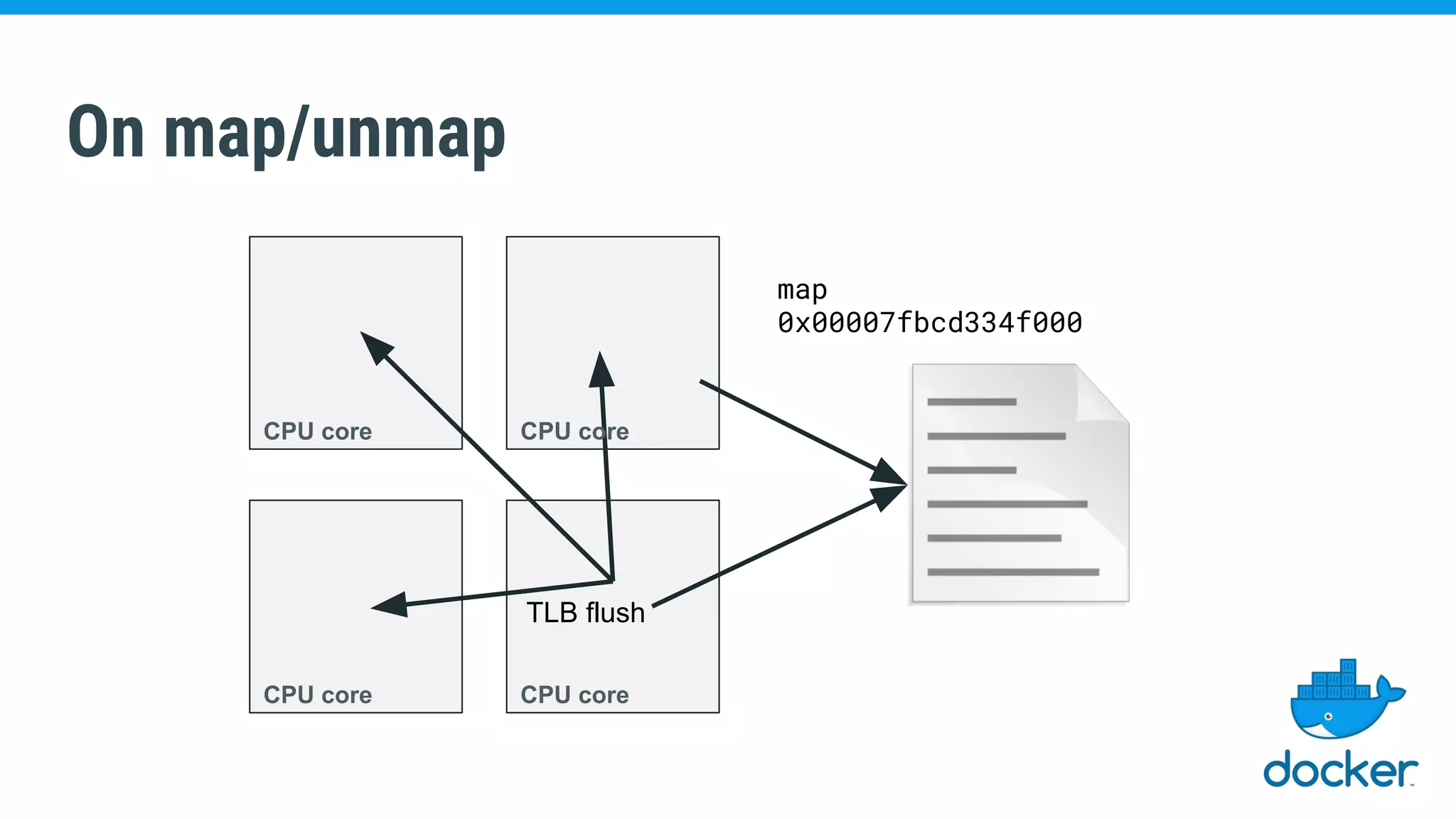
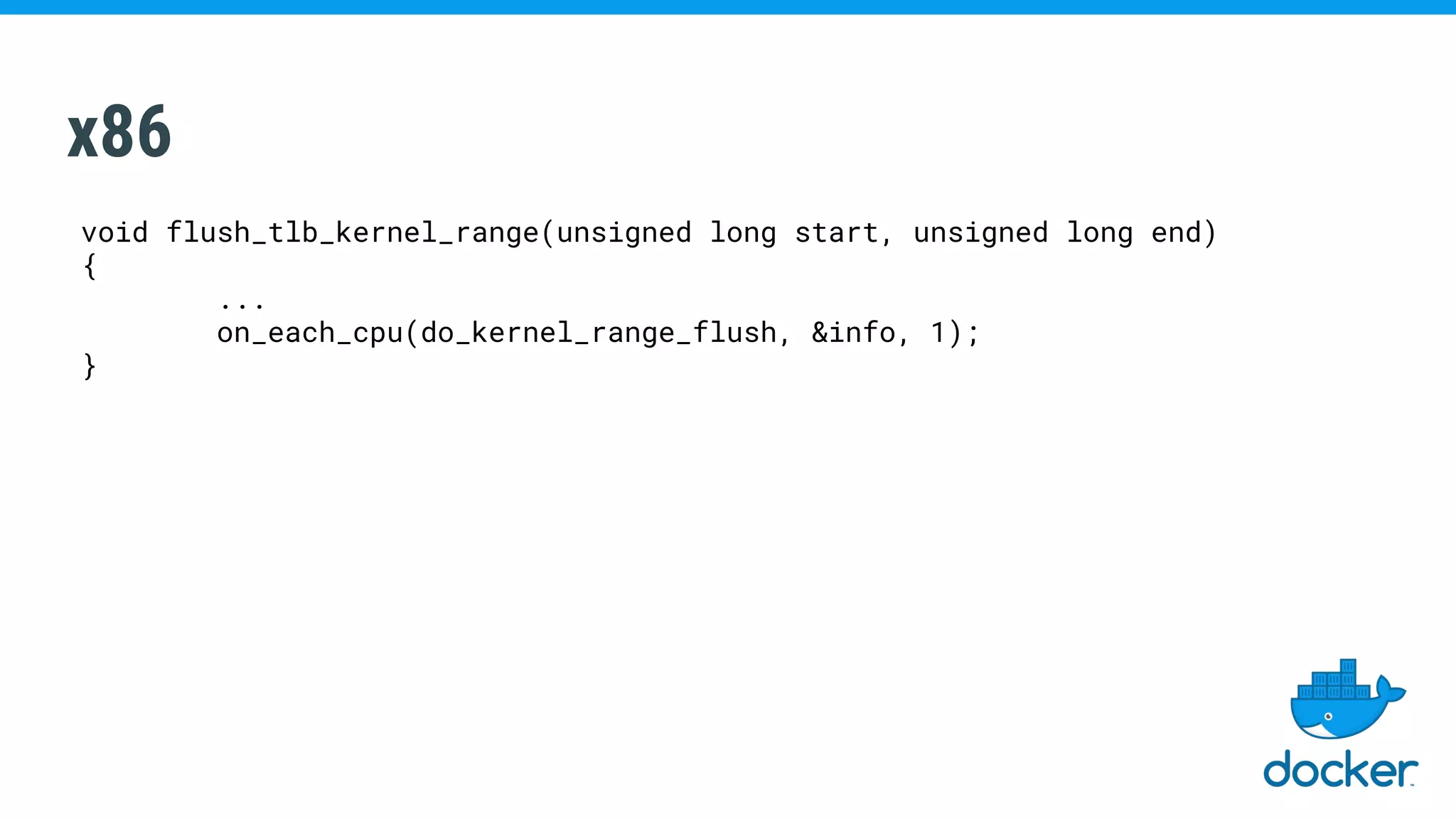
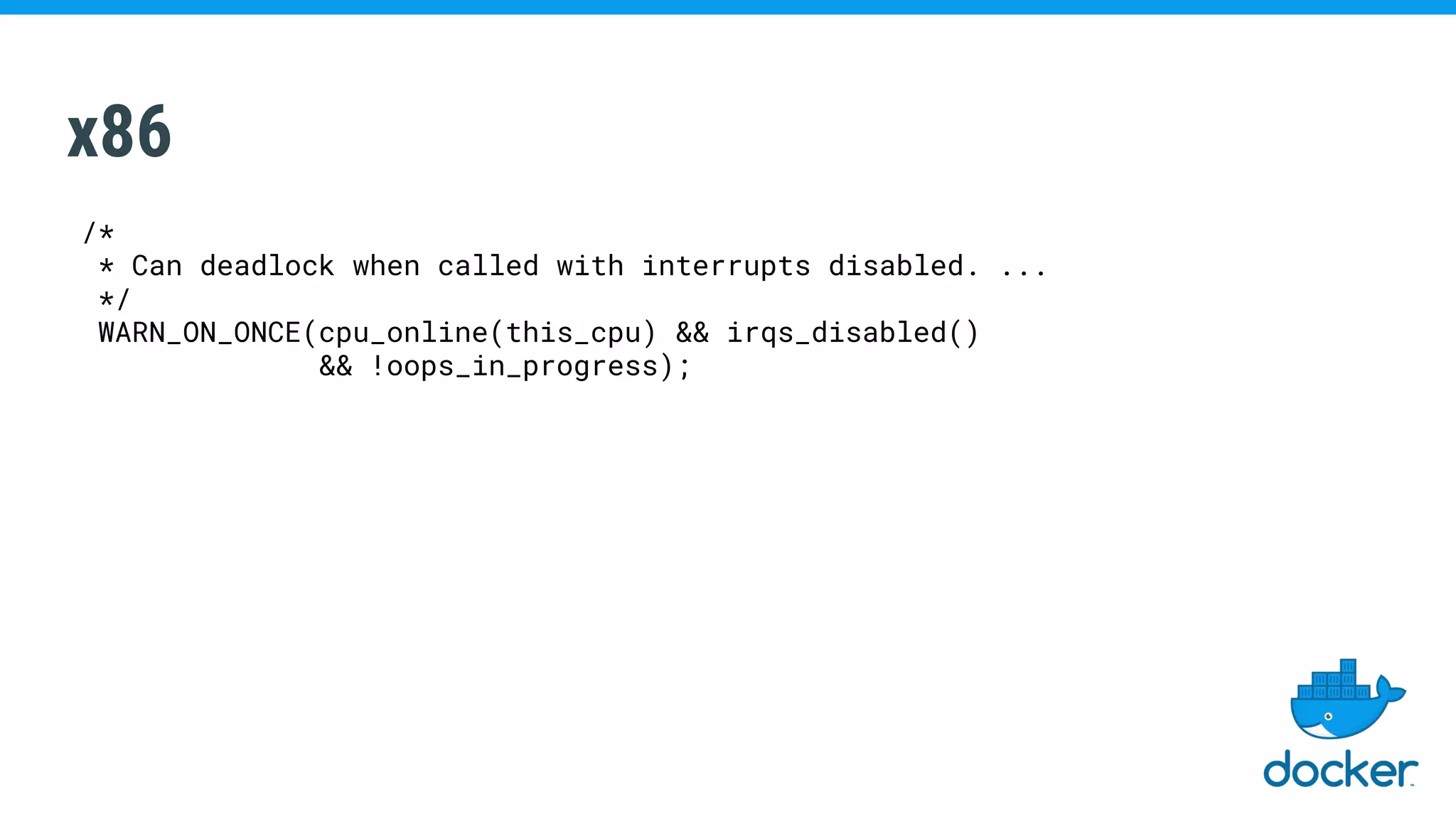
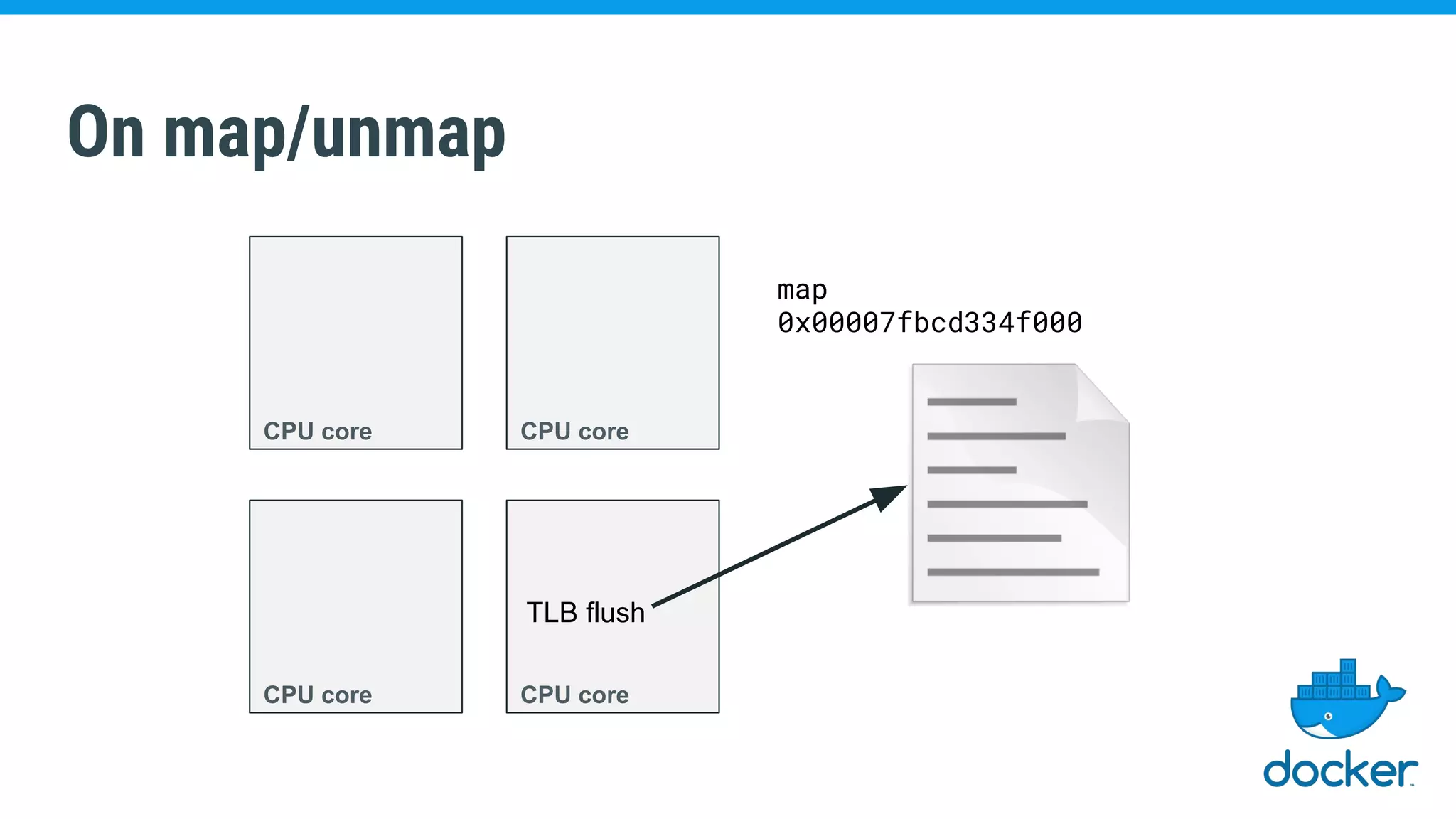
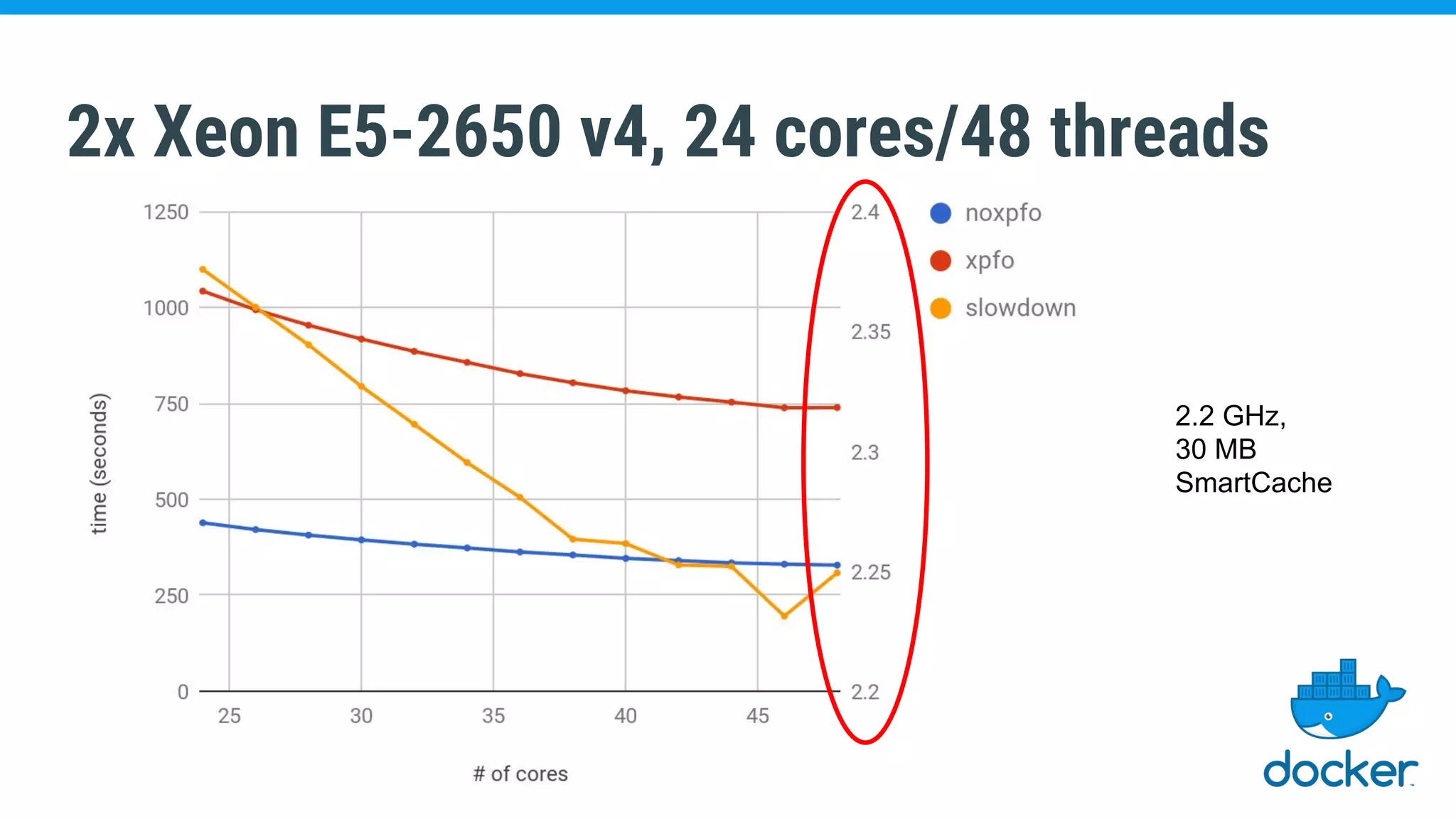
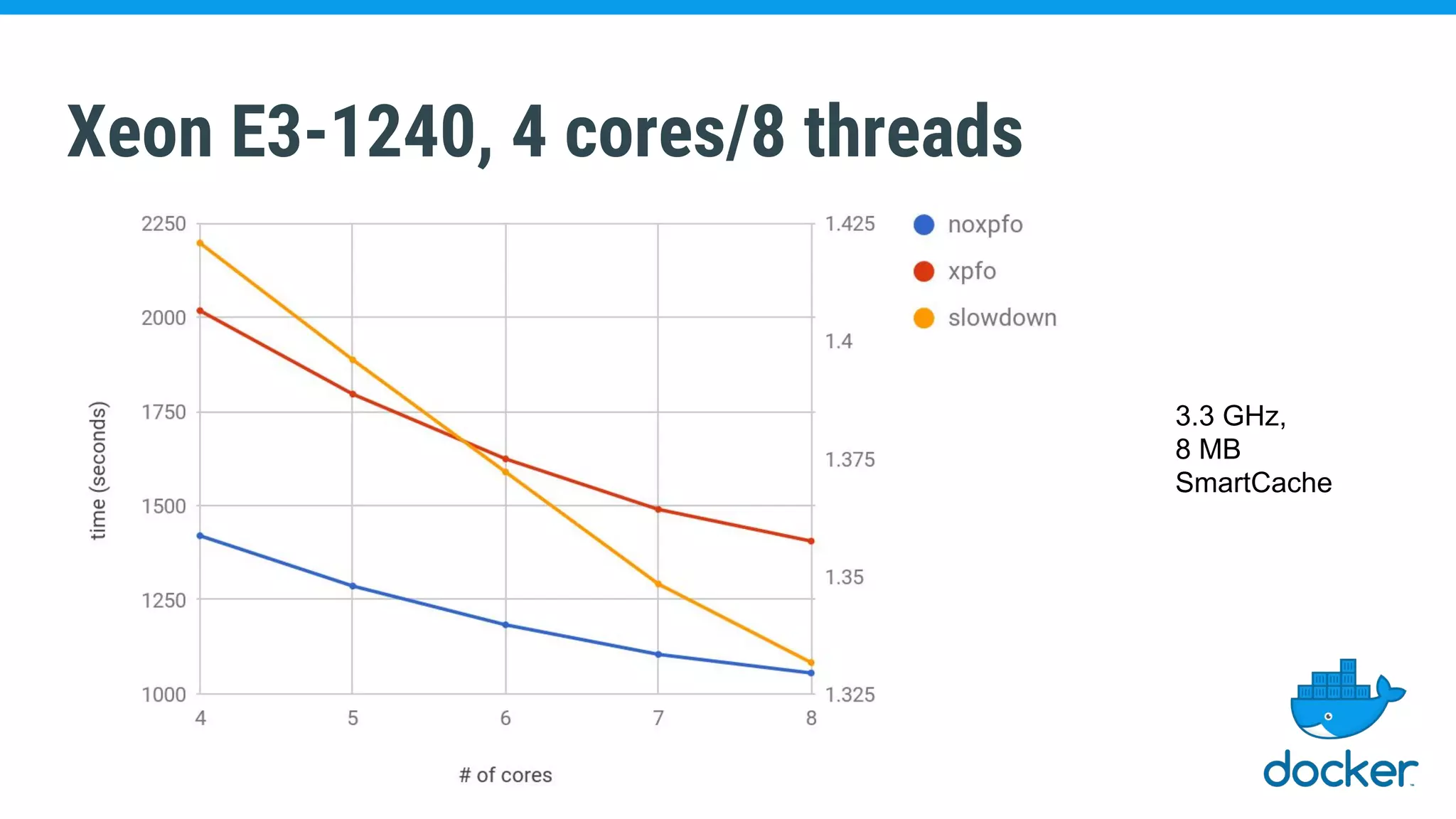
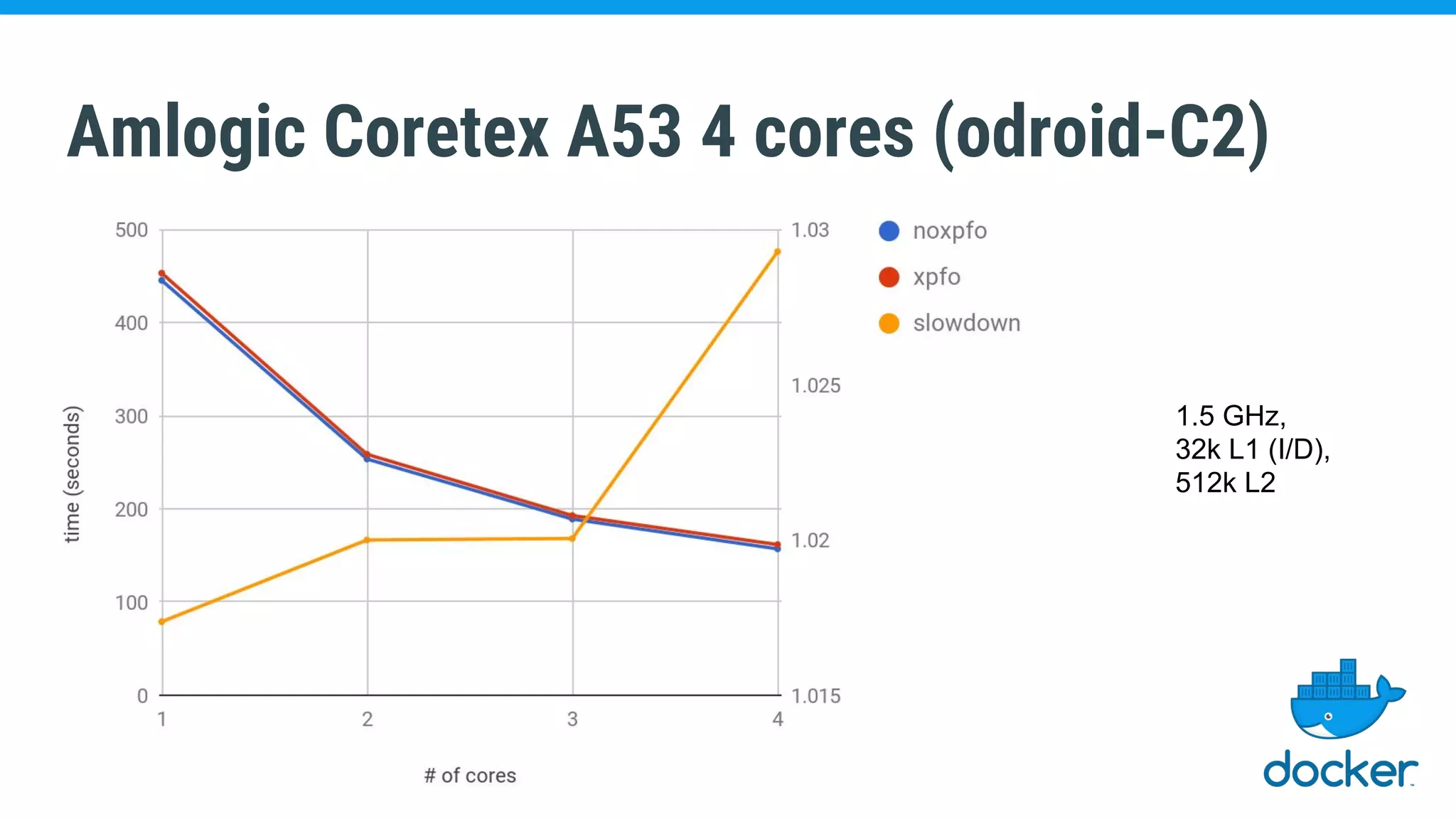
The document discusses various kernel developments related to container security, focusing on modules like Integrity Management Architecture (IMA), auditing capabilities, and security policies for namespaces. It examines the integration of security modules such as SELinux, AppArmor, and others, as well as advancements in protecting the kernel from attacks. Additionally, it highlights the Kernel Self Protection Project (KSPP) and technologies like WireGuard for secure communications.