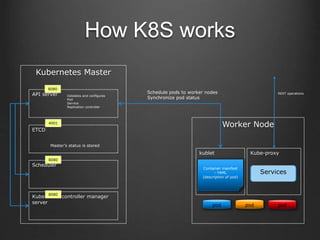
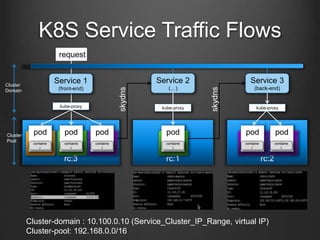
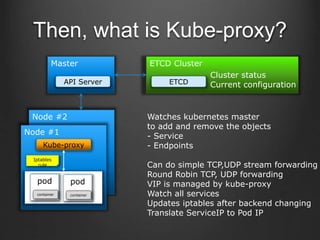
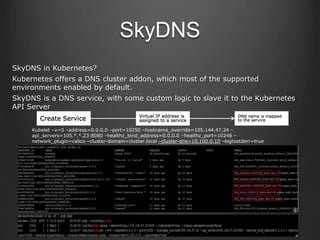
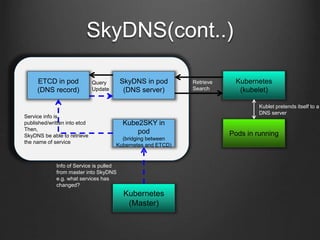
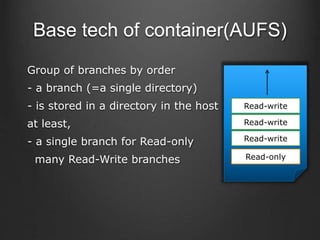
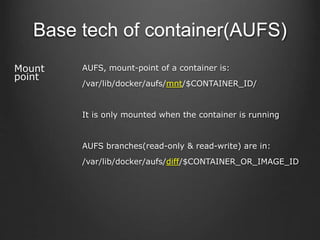
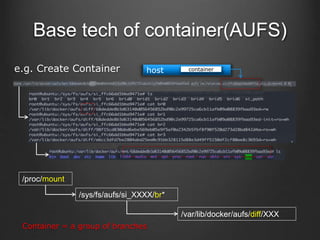
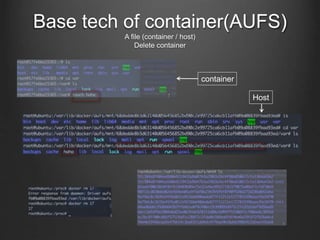
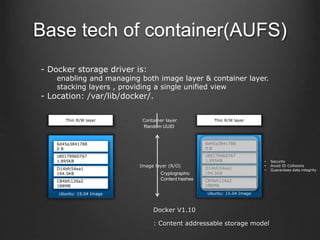
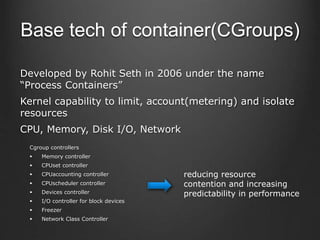
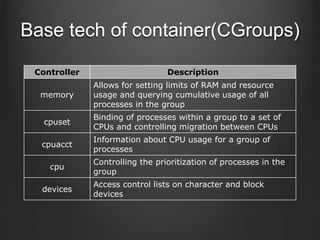
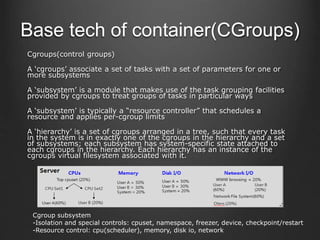
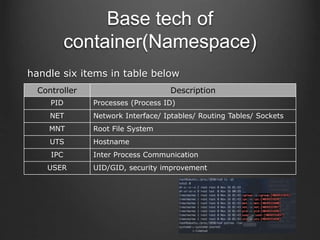
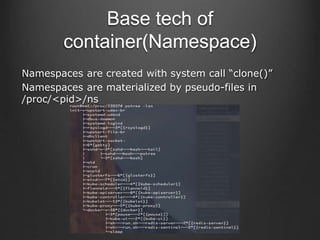
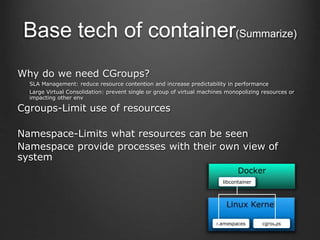
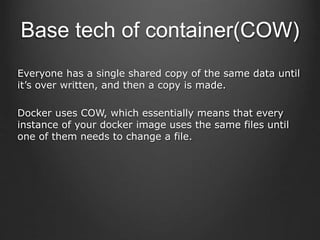
Container technologies use namespaces and cgroups to provide isolation between processes and limit resource usage. Docker builds on these technologies using a client-server model and additional features like images, containers, and volumes to package and run applications reliably and at scale. Kubernetes builds on Docker to provide a platform for automating deployment, scaling, and operations of containerized applications across clusters of hosts. It uses labels and pods to group related containers together and services to provide discovery and load balancing for pods.







![endpoints
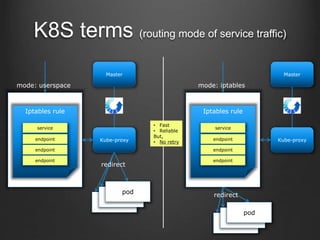
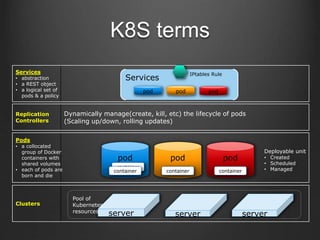
K8S terms
{
“kind”: ”Service”,
“apiVersion”:”v1”,
“metadata”:{
“name”: ”my-service”
},
“spec”:{
“selector”: {
“app”: ”MyApp”
},
“ports”:[{
“protocol”: ”TCP”,
“port”:”80”,
“targetPort”:9376”
}]
}
}
service
pod pod
endpoint
Selector = “app: MyApp”
Cluster IP my-service
targetPort:9376
Service
proxy](https://image.slidesharecdn.com/containerkubernetes-161129223929/85/Container-kubernetes-23-320.jpg)