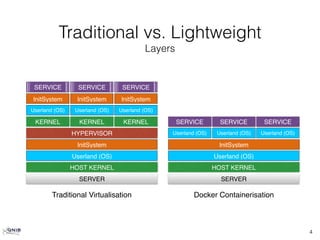
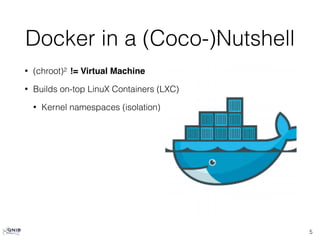
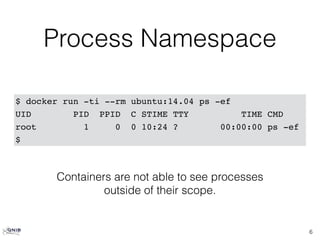
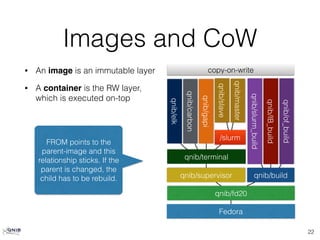
The document provides an overview of Docker, highlighting its differences from traditional virtual machines by emphasizing its use of Linux containers, kernel namespaces for isolation, and cgroups for resource management. It discusses the intuitive build system with Dockerfiles, caching of build steps, and the concept of images and layers in Docker. Additionally, it touches on the integration of Docker with Ansible for configuration management, orchestration, and validation in a containerized environment.


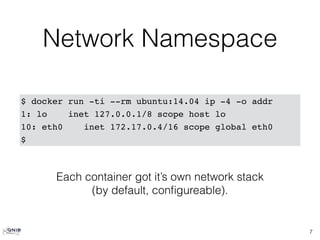
![Dockerfile
10
$ cat Dockerfile
# From which image to start from
FROM fedora:20
# Who is in charge
MAINTAINER "Christian Kniep <christian@qnib.org>"
# Execute bash command
RUN yum install -y stress
# if no command is given, this command will be
# executed at runtime (within a bash).
CMD ["stress", "-c", "4"]](https://image.slidesharecdn.com/ansibledocker-141215141812-conversion-gate02/85/Ansible-docker-10-320.jpg)


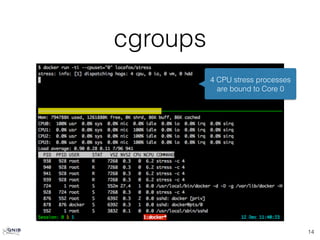
![cgroups [cont]
15
4 CPU stress processes
are bound to Core 0 & 3](https://image.slidesharecdn.com/ansibledocker-141215141812-conversion-gate02/85/Ansible-docker-15-320.jpg)




![Config Mgmt
• Provisioning
• Bootstrap DOCKER_HOST
• Dockerfile vs. playbooks?
• Orchestration
• Multiple other project in the woods
(Docker Swarm, Kubernetes, Apache Mesos[?], …)
• Validation
• Is the configuration within still valid?
28](https://image.slidesharecdn.com/ansibledocker-141215141812-conversion-gate02/85/Ansible-docker-28-320.jpg)


![Thoughts
• Containers mostly do not provide an SSH daemon
• Connecting via
• Docker is a nice way to check out playbook
• Otherwise playbooks shouldn’t be used inside of Dockerfiles [IMHO]
• Use Ansible to check configuration within container?
• Setup SELinux rules using Ansible
• Vagrant vs. Docker
31
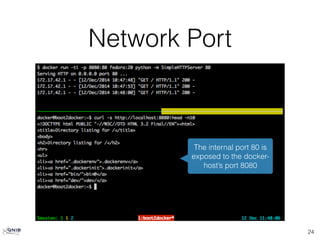
docker exec <container> bash](https://image.slidesharecdn.com/ansibledocker-141215141812-conversion-gate02/85/Ansible-docker-31-320.jpg)