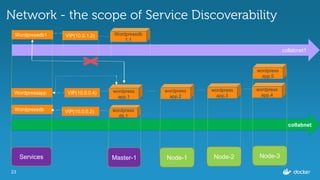
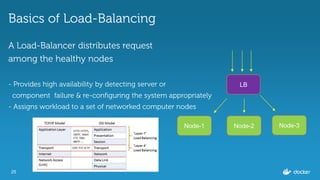
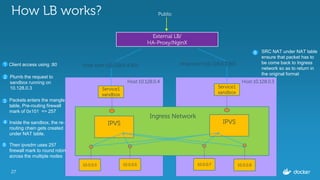
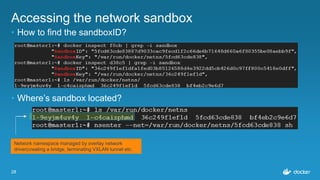
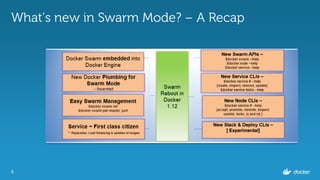
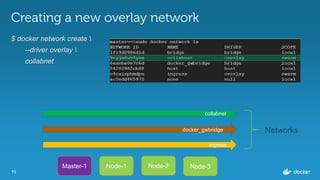
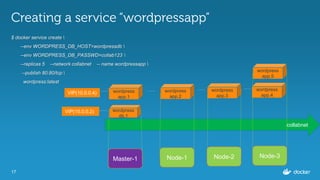
Ajeet Singh Raina presented at the Docker Bangalore Meetup on August 20, 2016, discussing service discovery and load-balancing in Docker 1.12. Key topics included the evolution of service discovery, the new Docker Swarm features, and practical examples of creating and inspecting services. The presentation highlighted the benefits of embedded DNS for service discovery and decentralized load balancing in container management.


![6
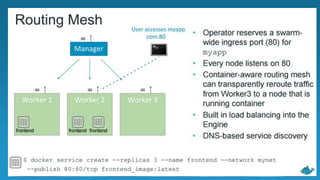
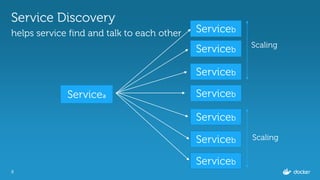
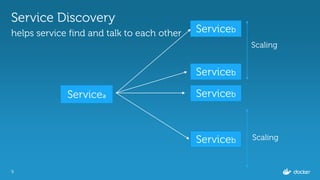
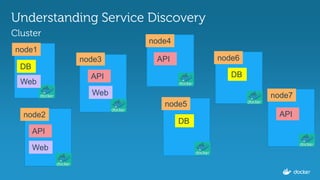
Evolution of Service Discovery
Docker 1.9
/etc/hosts and
/etc/resolv.conf
~ for the cluster service.
Cons:
- Corrupted /etc/hosts
- Lacking of Load-
Balancing Feature
- Complex way of Service
Discovery
Docker 1.10/1.11
- Embedded DNS
--network-alias=ALIAS
--link=CONTAINER_NAME:ALIAS
--dns=[IP_ADDRESS...]
--dns-search=DOMAIN
Cons:
- Service Discovery through
External Discovery backend
like Consul, zookeeper etc.
Docker 1.12
- No External Service Discovery
Backend Required
- Service Discovery plumbed
directly into $docker service
- Service Discovery by Unqualified
names.(Un-FQDN)
- Provided by Embedded DNS
- Highly Available
- Ability to discover both the
services and tasks
-.](https://image.slidesharecdn.com/dockerbangaloremeetup22-160820175928/85/Service-Discovery-Load-Balancing-under-Docker-1-12-0-Docker-Meetup-22-6-320.jpg)


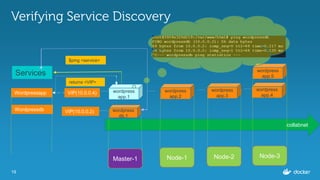
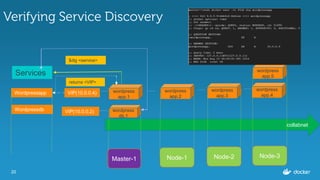
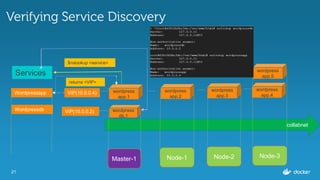
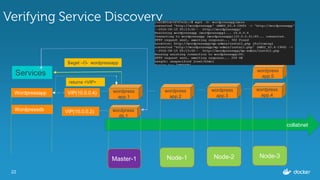
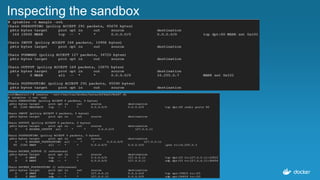
![18
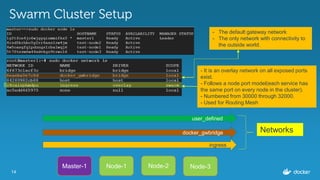
Inspecting the services
$ docker service inspect
--format=='{{json .Endpoint.VirtualIPs}}'
wordpressapp
[{"NetworkID":"c4caizphmdpuhm1gjdle8eaal","Addr":"10.255.0.7/16"},
{"NetworkID":"9eyjm4uv4ynmz0aubfqxise29","Addr":"10.0.0.4/24"}]
$ docker service inspect
--format=='{{json .Endpoint.VirtualIPs}}'
wordpressdb
[{"NetworkID":"9eyjm4uv4ynmz0aubfqxise29","Addr":"10.0.0.2/24"}]](https://image.slidesharecdn.com/dockerbangaloremeetup22-160820175928/85/Service-Discovery-Load-Balancing-under-Docker-1-12-0-Docker-Meetup-22-18-320.jpg)